
In the field of information technology, understanding key concepts is crucial for mastering essential skills. This section focuses on core areas that are fundamental for building a solid foundation in the subject. By thoroughly reviewing various technical concepts, you can enhance your ability to apply knowledge in real-world scenarios.
The material covered includes important topics related to networking, hardware configuration, and system security. It is designed to equip learners with the tools needed to navigate the complexities of IT infrastructure and troubleshooting. With a strong grasp of these principles, you can solve problems more efficiently and improve your technical proficiency.
By reviewing the major points and reinforcing key terms, you will be better prepared to tackle any related challenges. Whether you are revisiting the material or exploring it for the first time, a structured approach to studying ensures success. Focus on comprehension and application to master the concepts and develop your technical expertise.
IT Knowledge Review and Key Concepts
Understanding fundamental concepts in information technology is critical to mastering the subject and applying it effectively in various scenarios. In this section, we explore the key areas that are frequently tested, offering insights and techniques to navigate through the material efficiently. A solid grasp of these topics allows you to tackle challenges and deepen your technical expertise.
Networking and Communication Fundamentals
Networking principles form the backbone of modern IT infrastructure. Being familiar with the core concepts of data transmission, IP addressing, and connectivity protocols will significantly enhance your problem-solving abilities. Below are some of the crucial points to remember:
- Understanding the OSI model and its layers
- Configuring network devices and troubleshooting connectivity issues
- Knowledge of common network topologies
- Identifying and solving network-related problems
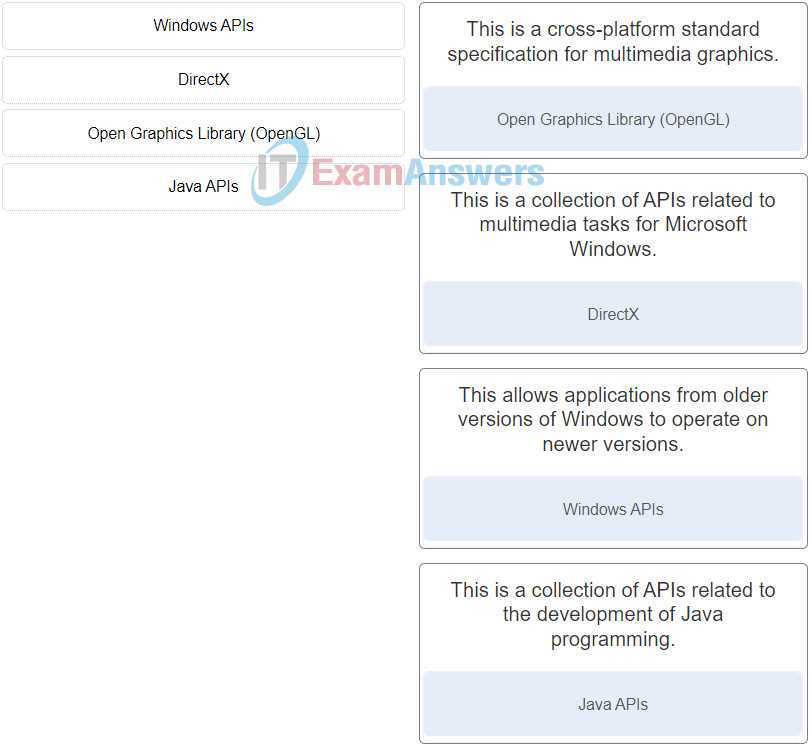
Hardware Configuration and System Maintenance
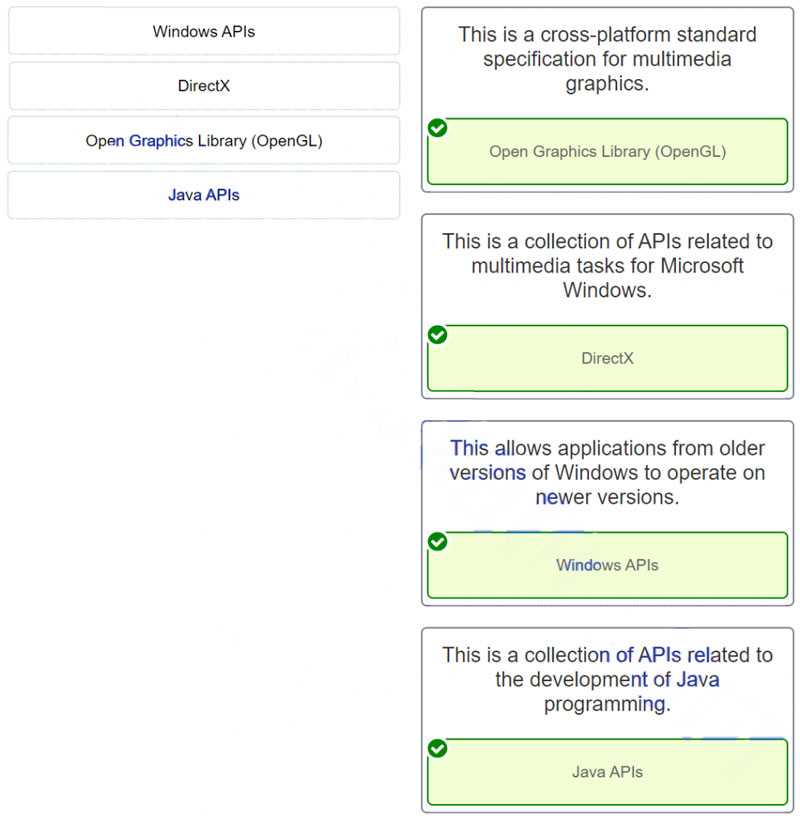
Hardware is the foundation of any IT system, and knowing how to set up and maintain various components is essential. In this section, focus on understanding the key hardware devices, how they interact, and how to troubleshoot common issues. Important points include:
- Setting up and configuring computer components
- Identifying and replacing faulty parts
- System upgrades and performance optimization
- Performing regular system maintenance and updates
By reinforcing these core concepts, you ensure a comprehensive understanding that will serve you well in practical applications. Mastery of these topics equips you with the skills to excel in the IT field and overcome the most common challenges encountered in the industry.
Key Topics Covered in Chapters 10-14
In this section, we focus on several crucial concepts that are central to understanding the broader field of information technology. These topics provide a foundation for the various tasks and challenges you will encounter in a professional IT environment. Mastering these concepts will enhance your ability to configure, troubleshoot, and maintain complex systems with confidence.
The material touches upon fundamental areas such as networking principles, system security, hardware components, and troubleshooting strategies. These key areas are vital for anyone working in IT, as they address the technical aspects of daily operations and provide the knowledge needed to resolve issues effectively. Each topic builds upon the previous one, allowing for a comprehensive understanding of the IT landscape.
Whether you are learning these topics for the first time or reviewing them for deeper understanding, these areas will ensure a well-rounded grasp of IT principles and best practices.
Study Tips for IT Knowledge Mastery
Preparing for an IT assessment requires a structured approach that focuses on understanding core principles and applying them to practical situations. Effective study techniques not only help in recalling important information but also in mastering the skills required for real-world problem-solving. By organizing your study routine and utilizing the right resources, you can ensure success and gain confidence in the subject matter.
Effective Study Strategies

To optimize your preparation, follow these key strategies:
- Break down the material into manageable sections
- Review each topic thoroughly and focus on key terms
- Practice applying concepts to real-world scenarios
- Use study guides and online resources for additional practice
- Join study groups to discuss difficult concepts
Time Management Tips

Managing your time effectively is crucial to covering all topics efficiently. Consider the following tips to make the most of your study sessions:
- Set specific, measurable goals for each study session
- Create a schedule that allocates time for each topic
- Take regular breaks to maintain focus and avoid burnout
- Start with the most challenging topics when your energy is highest
By following these strategies, you can ensure a thorough understanding of key IT topics and improve your chances of success in the assessment.
Understanding Networking Basics for Success
Networking is a foundational element of modern technology, connecting devices and enabling the flow of information across systems. A clear understanding of networking principles is essential for troubleshooting, configuration, and optimization of IT systems. In this section, we will explore the core concepts that make up the network infrastructure, focusing on how to apply this knowledge in practical scenarios.
Key Networking Components
To effectively manage and troubleshoot networks, it’s important to understand the main components that make up any network. These include devices, protocols, and configurations that allow seamless communication between systems. Below is a table outlining the key components:
| Component | Description |
|---|---|
| Router | Directs data packets between different networks, enabling communication across devices. |
| Switch | Connects devices within the same network, forwarding data to the correct destination based on MAC addresses. |
| IP Address | Unique identifier assigned to each device on a network, used for routing data to and from the device. |
| Firewall | Monitors and controls incoming and outgoing network traffic based on security rules. |
Network Troubleshooting Techniques
Once you understand the components, you can begin applying troubleshooting techniques to resolve common network issues. Effective troubleshooting requires knowledge of how devices communicate, how to interpret error messages, and the steps to identify and resolve connectivity problems. Some key troubleshooting steps include:
- Verify physical connections and ensure cables are intact.
- Check IP configurations and ensure devices are properly assigned.
- Test network speed and identify potential bottlenecks.
- Use diagnostic tools like ping and traceroute to identify issues.
By mastering these basics, you can ensure reliable communication across networks and address common connectivity problems efficiently.
Common Mistakes to Avoid in IT Assessment
When preparing for an IT assessment, certain mistakes can hinder your performance and reduce your chances of success. It’s essential to be aware of these common errors so you can avoid them and approach the material with a clear and focused mindset. By recognizing and addressing these pitfalls, you can maximize your effectiveness during the evaluation process.
One of the most frequent mistakes is failing to manage time properly. Many students rush through questions without fully reading them, leading to missed details or incorrect answers. Additionally, relying too heavily on memorization without truly understanding the underlying concepts can lead to confusion when faced with more complex questions.
Here are some other common mistakes to be aware of:
- Skipping Practice Questions: Not completing enough practice questions limits your ability to apply what you’ve learned in realistic scenarios.
- Ignoring Key Concepts: Neglecting foundational topics can lead to gaps in knowledge, which are often tested in more difficult sections.
- Mismanaging Study Time: Procrastination and last-minute cramming can leave you unprepared and stressed.
- Overlooking Instructions: Failing to follow the specific guidelines or instructions on a question can lead to avoidable mistakes.
By avoiding these common errors and taking a more structured and thoughtful approach to your preparation, you can improve your chances of performing well and mastering the material.
Hardware Troubleshooting Techniques Explained
Hardware issues are one of the most common challenges in IT environments, and knowing how to diagnose and resolve them efficiently is essential for maintaining system stability. Understanding the various techniques and tools available for troubleshooting can help identify problems, fix faults, and prevent future complications. In this section, we will explore effective methods to tackle hardware-related issues and optimize performance.
Identifying Common Hardware Failures
Hardware failures can stem from a variety of sources, including physical damage, power issues, or component malfunctions. The first step in troubleshooting is recognizing the symptoms and narrowing down the root cause. Some common signs of hardware failure include:
- Unusual noises (e.g., clicking or grinding from hard drives)
- System not powering on or shutting down unexpectedly
- Frequent crashes or freezes during operation
- Overheating or failure to boot up
Once you’ve identified these issues, you can begin addressing them systematically by checking connections, replacing faulty parts, or testing individual components to isolate the problem.
Effective Troubleshooting Steps
To effectively troubleshoot hardware problems, follow these proven steps:
- Check Power Supply: Ensure that power cables are securely connected and the power supply is functioning correctly. If the system does not turn on, test with a different power source.
- Inspect Internal Connections: Verify that all internal cables, memory modules, and components like hard drives and graphics cards are properly seated in their slots.
- Run Diagnostic Tools: Use built-in or third-party diagnostic tools to check the status of components like RAM, CPU, and storage devices.
- Replace Suspect Parts: If a specific component is identified as faulty, such as a hard drive or RAM stick, replace it with a known working part to see if the problem is resolved.
By following these steps and understanding the nature of common hardware issues, you can efficiently troubleshoot and restore system functionality, minimizing downtime and ensuring smooth operation.
Key Security Concepts You Must Know
Understanding fundamental security principles is essential for protecting systems and sensitive information in any IT environment. As technology evolves, so do the tactics employed by cybercriminals, making it crucial to stay informed about the best practices and strategies for safeguarding data. In this section, we will explore the most important security concepts that every IT professional should know to defend against potential threats.
Security encompasses a wide range of measures, from protecting hardware and software to ensuring the privacy and integrity of data. Understanding the various layers of protection and how they work together will help you design and implement secure systems. The key security concepts outlined below will provide the foundation for a comprehensive security strategy.
| Security Concept | Description |
|---|---|
| Authentication | Verifying the identity of users, devices, or systems to ensure only authorized entities have access to resources. |
| Encryption | Transforming data into a secure format that can only be read or decrypted by authorized parties. |
| Firewalls | Monitoring and controlling incoming and outgoing network traffic based on security rules to prevent unauthorized access. |
| Intrusion Detection Systems (IDS) | Monitoring network traffic for suspicious activity or known threats and alerting administrators when an intrusion is detected. |
| Access Control | Setting policies and permissions to restrict access to sensitive information or systems to authorized users only. |
By mastering these fundamental security concepts, you can better understand how to protect systems and data from various security risks. These principles form the backbone of any robust cybersecurity strategy and are crucial for maintaining the confidentiality, integrity, and availability of information.
Preparing for the Final Assessment Effectively
Effective preparation for any major assessment requires a well-structured approach that includes understanding the material, managing your time efficiently, and practicing problem-solving. To achieve success, it’s important to go beyond mere memorization and focus on mastering key concepts and applying them in real-world scenarios. In this section, we will explore strategies and tips to ensure you are fully prepared for your upcoming evaluation.
Time Management and Study Planning
One of the most critical aspects of preparation is effective time management. Spreading out your study sessions over several weeks, rather than cramming all at once, allows you to absorb and retain information more effectively. Start by creating a study plan that outlines specific topics to review each day. Be sure to allocate more time for areas where you feel less confident. Additionally, don’t forget to schedule breaks to avoid burnout.
- Start early and break the material into smaller sections.
- Set realistic goals for each study session.
- Review your progress regularly and adjust your plan as needed.
Active Learning Techniques
Merely reading through your notes is often insufficient. Active learning involves engaging with the material in a way that encourages deeper understanding and retention. Practice problems, quizzes, and mock scenarios are all excellent ways to actively engage with the content and test your knowledge. Working through examples allows you to apply what you’ve learned and better prepare for the types of questions you’ll encounter.
- Use flashcards to reinforce key concepts and terminology.
- Collaborate with peers for study sessions and discussions.
- Test yourself using practice exams or simulated challenges.
By combining time management with active learning techniques, you can maximize your preparation and approach the assessment with confidence and clarity.
Critical Software Knowledge for IT Assessment
In the world of information technology, understanding key software tools and their functionalities is essential for success in any technical assessment. Mastery of software applications not only helps in solving problems but also enables individuals to streamline tasks, improve system performance, and troubleshoot efficiently. This section covers the critical software knowledge that IT professionals must be familiar with to excel in technical assessments.
Operating Systems and Utilities
Proficiency in different operating systems (OS) is a fundamental skill for IT professionals. Whether working with Windows, macOS, or Linux, knowing how to navigate and configure these environments is vital. Additionally, understanding system utilities such as task managers, file explorers, and disk management tools will aid in troubleshooting and system optimization.
- Windows OS: Knowledge of control panel settings, device manager, and command-line tools such as cmd and PowerShell.
- Linux/Unix OS: Familiarity with terminal commands and system configuration files.
- macOS: Understanding system preferences and tools like Activity Monitor.
Networking and Security Tools
Networking software and security tools are another key area to focus on. These include network diagnostic tools, firewalls, antivirus software, and encryption methods. Knowing how to configure and troubleshoot network connections, apply security patches, and ensure data privacy will help in safeguarding systems against vulnerabilities.
- Network Tools: Proficiency with utilities like ipconfig, tracert, and ping for troubleshooting connectivity issues.
- Security Software: Familiarity with antivirus programs, encryption software, and firewall configurations.
- Backup Solutions: Knowledge of tools used for system backups and disaster recovery strategies.
By mastering these critical software tools and concepts, you will be well-equipped to tackle challenges in both real-world scenarios and technical assessments, ensuring a high level of competence in IT operations.
Exam Strategies to Boost Your Score
Maximizing your performance in any assessment requires more than just reviewing material; it involves applying effective strategies during the test itself. Being well-prepared is key, but knowing how to approach the questions and manage your time efficiently can make a significant difference in your final score. In this section, we will explore several strategies that can help you perform at your best and boost your results.
Time Management and Question Strategy
One of the most important factors in achieving a high score is managing your time effectively during the test. It’s easy to get stuck on challenging questions, but wasting time on one problem can limit the time you have for others. Here’s how you can stay on track:
- Read through all the questions first: Get an overview of the entire test before starting to answer. This helps you identify easy questions to answer first.
- Allocate time for each section: Based on the number of questions, set a time limit for each section to avoid spending too much time on any one area.
- Skip and return: If you encounter a difficult question, move on and come back to it later. This ensures that easier questions are answered first.
Answering Techniques
How you approach each question is just as important as your preparation. Proper answering techniques can help you gain more points, even in tricky scenarios:
- Read questions carefully: Pay close attention to what is being asked and make sure you understand before answering. Often, questions contain hints or important details.
- Eliminate incorrect choices: For multiple-choice questions, eliminate obviously incorrect answers to increase your chances of selecting the right one.
- Use process of elimination: If unsure, eliminate the least likely answers and make an educated guess based on what you know.
Review and Check Your Work

After completing all the questions, always leave time for a final review. Checking your work can help you catch mistakes and ensure you haven’t overlooked any details:
- Review answers: Go through your answers to make sure you didn’t miss anything. Often, the first impression might not be the best one.
- Check for consistency: Ensure that your answers align with the questions and the overall content you’ve studied.
- Look for careless errors: Check your spelling, numbers, and calculations to avoid simple mistakes that could cost points.
By applying these strategies, you can maximize your performance and improve your chances of scoring higher in any technical assessment. With the right mindset and approach, you’ll be better prepared to tackle any challenge that comes your way.
Important Definitions from Chapters 10-14
Understanding key terms and concepts is essential when preparing for any technical assessment. These foundational definitions not only help clarify complex topics but also provide the necessary knowledge to solve practical problems effectively. Below, we cover some of the most important terms and their meanings that are crucial for mastering the subject matter.
Key Networking Concepts
Networking is a fundamental aspect of IT, and understanding the associated terminology is critical. Here are some core networking terms you should be familiar with:
- IP Address: A unique identifier assigned to each device on a network, enabling it to communicate with other devices.
- DNS (Domain Name System): A system that translates domain names into IP addresses, allowing users to access websites using human-readable names instead of numerical addresses.
- Router: A device that forwards data packets between computer networks, directing traffic to its destination.
Security and Protection Terminology
Security is another crucial area, and understanding the terminology related to system protection is vital. Here are some definitions you need to grasp:
- Firewall: A network security system that monitors and controls incoming and outgoing network traffic based on predetermined security rules.
- Encryption: The process of converting information into a code to prevent unauthorized access.
- Malware: Malicious software designed to damage or disrupt systems, including viruses, trojans, and ransomware.
These terms represent just a small portion of the essential vocabulary that will help you succeed. Understanding these definitions and their practical applications will give you a solid foundation for tackling technical challenges and assessments effectively.
How to Master Chapter 10 Questions
When preparing for any assessment, mastering individual sections or topics is key to gaining a comprehensive understanding of the subject. Focusing on specific areas of study will help you approach questions with confidence and clarity. In this section, we will discuss effective strategies to tackle the most common questions that arise in technical assessments, focusing on one specific area at a time.
Break Down Complex Topics
It’s important to break down complex concepts into manageable parts. By focusing on individual elements, you can more easily digest the material and address each part when answering questions.
- Identify key concepts: Make a list of essential terms and their definitions. Knowing these will allow you to understand and recall information more effectively.
- Understand the application: Look at how each concept applies in real-world scenarios. Practical examples help solidify your understanding and make it easier to answer related questions.
- Practice with problems: Solve related problems to get familiar with how these concepts are tested. The more you practice, the more intuitive the process will become.
Focus on Troubleshooting Skills
For many technical subjects, troubleshooting is a critical skill. Being able to quickly diagnose issues and apply the correct solutions will greatly improve your ability to handle related questions. Here’s how you can improve your troubleshooting skills:
- Learn step-by-step processes: Troubleshooting often involves a series of logical steps. Make sure you understand the sequence of actions that lead to a solution.
- Familiarize yourself with common errors: Knowing the most common issues and their solutions will give you an edge when similar problems appear on assessments.
- Simulate real scenarios: Create hypothetical problems and solve them as if you were dealing with an actual technical issue. This will help reinforce your problem-solving skills.
By mastering these strategies, you will not only improve your ability to answer questions accurately but also enhance your overall understanding of the material. Focusing on problem-solving and key concepts will make complex questions feel more approachable and manageable.
Understanding IP Addressing for the Exam
In any technical assessment, understanding the fundamentals of network addressing is crucial. IP addressing forms the backbone of network communication, ensuring devices can send and receive data across various networks. To master this concept, it is essential to grasp the structure, types, and allocation methods used in modern networking systems.
When studying for an assessment, focus on the two primary types of IP addresses: IPv4 and IPv6. Knowing how to identify and differentiate these addressing schemes is key to understanding how networks are configured. Additionally, understanding subnetting, private vs. public addresses, and how routing decisions are made based on IP addresses will improve your ability to answer related questions effectively.
IPv4 Addressing Overview
IPv4 is the most widely used version of the Internet Protocol. It is a 32-bit address that is typically represented in four octets, written in decimal format. The structure and classification of IPv4 addresses are fundamental to any networking course.
| Class | Address Range | Subnet Mask |
|---|---|---|
| A | 1.0.0.0 – 127.255.255.255 | 255.0.0.0 |
| B | 128.0.0.0 – 191.255.255.255 | 255.255.0.0 |
| C | 192.0.0.0 – 223.255.255.255 | 255.255.255.0 |
Subnetting Basics
Subnetting allows network administrators to break a large network into smaller, more manageable sub-networks. Understanding subnetting is crucial for network design and troubleshooting. It helps in optimizing the use of available IP addresses and in managing traffic more effectively.
- IP Class: Recognize which IP class an address belongs to. This helps determine the network’s size and the number of hosts it can accommodate.
- Subnet Masks: Learn how subnet masks define the network and host portions of an IP address. A subnet mask is essential for routing data to the correct destination.
- CIDR Notation: Familiarize yourself with CIDR (Classless Inter-Domain Routing) notation, which is used to represent IP addresses and their associated subnet masks.
Understanding the structure and rules behind IP addressing is a vital step in mastering networking concepts. Whether dealing with IPv4 or IPv6, knowing how to correctly assign, subnet, and troubleshoot IP addresses will enhance your ability to succeed in technical assessments.
Effective Time Management During the Test
Time management is a crucial skill to master during any technical assessment. With a limited amount of time, it is essential to allocate your efforts efficiently to ensure you complete all sections within the allowed timeframe. By planning and pacing yourself properly, you can increase your chances of success while reducing stress and avoiding rushed decisions.
The first step in managing your time effectively is to quickly assess the structure of the test. Understanding how many sections there are, how much time you have for each part, and the difficulty level of each question will help you prioritize. A clear strategy for tackling the test can make a significant difference in your performance.
Strategies for Time Allocation
Here are some useful strategies to help manage your time during the assessment:
- Skim the Entire Test: Take a few minutes to quickly review all the questions at the beginning. This will give you an overview of what to expect and allow you to gauge how long you might need for each section.
- Prioritize Easy Questions: Start with the questions that you find easiest. This helps build confidence and ensures that you are making the most of your time on the simpler tasks.
- Set Time Limits for Each Section: Break the test into sections and set a specific time limit for each one. Stick to these limits to avoid spending too much time on any single question or section.
- Leave Difficult Questions for Later: If you encounter particularly challenging questions, don’t get stuck on them. Move on and return to them if time permits.
- Review Your Work: Allocate a few minutes at the end to go back over your answers. This will allow you to catch any mistakes and ensure your answers are complete.
By following these strategies and maintaining a steady pace throughout the assessment, you can manage your time effectively and ensure that you finish with a solid understanding of all the material presented. Time management during a test is not only about speed but also about making thoughtful decisions and using your time wisely to maximize your success.
Reviewing Key Terms and Their Applications
Understanding key terminology and its practical use is essential for success in any technical assessment. Mastery of these terms not only improves your comprehension of the material but also helps you apply them effectively in real-world scenarios. By familiarizing yourself with these concepts, you can tackle questions more confidently and accurately.
In this section, we will review some of the most important terms and their applications in the context of IT and networking. Knowing how these terms relate to each other and how they are used in practice will give you a strong foundation for solving problems and understanding the broader concepts presented in the test.
Essential Networking Terms
- IP Address: A unique identifier for a device on a network, used to route data between devices. Understanding both IPv4 and IPv6 addressing is crucial.
- Subnet Mask: A tool that helps divide an IP network into sub-networks, allowing more efficient use of IP addresses. It is critical for network management and troubleshooting.
- Router: A device that directs data traffic between different networks. Routers are essential for connecting local networks to the internet or other external networks.
- DNS (Domain Name System): The system that translates domain names into IP addresses. It plays a vital role in navigating the web and enabling communication between devices.
Key Security Terms and Their Use
- Firewall: A security system designed to prevent unauthorized access to or from a private network. Firewalls can be either hardware-based or software-based.
- Encryption: The process of converting data into a code to prevent unauthorized access. Encryption is critical for securing communications and protecting sensitive information.
- VPN (Virtual Private Network): A tool used to create a secure connection over the internet, allowing users to send and receive data as if they were directly connected to a private network.
- Malware: Software designed to harm or exploit any device or network. Understanding the different types of malware and their prevention methods is essential for maintaining security.
By reviewing and understanding these key terms and their practical applications, you will be better equipped to solve technical problems and answer questions effectively. Familiarity with these terms also allows for a deeper understanding of how systems and networks operate, giving you an edge in both theoretical and practical aspects of IT-related assessments.
Final Review Checklist for IT Essentials Exam
Before taking any assessment, it’s essential to have a comprehensive review plan to ensure that you’ve covered all the necessary topics and are well-prepared. This checklist will guide you through the key areas to focus on as you prepare for your IT-related evaluation. A systematic review will help you identify any areas where you may need to spend more time and will ensure that you’re confident in your knowledge on the day of the test.
Use the following checklist to confirm that you’ve covered all the critical areas and feel ready to tackle the test. This will not only boost your confidence but also increase your chances of success by ensuring that you have a strong grasp on both the theoretical and practical aspects of the subject matter.
Review Key Concepts
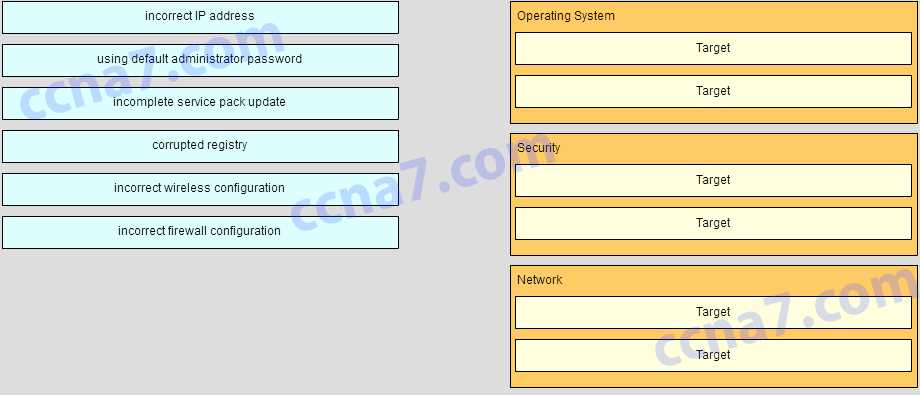
- Networking Fundamentals: Ensure you understand IP addressing, subnetting, and routing protocols. Be familiar with common network devices such as routers, switches, and hubs.
- Hardware Components: Review the main hardware components of computers, including processors, RAM, storage devices, and peripherals. Know their functions and how they interact within a system.
- Operating Systems: Be comfortable with both Windows and Linux operating systems. Focus on system commands, file management, and troubleshooting techniques.
- Security Basics: Revisit key security terms like firewalls, encryption, and malware protection. Understand common vulnerabilities and how to mitigate security risks.
Practice Troubleshooting
- Common Issues: Practice diagnosing common hardware and software problems. Understand how to identify symptoms and apply effective solutions.
- Tools and Techniques: Familiarize yourself with the use of diagnostic tools such as command-line utilities, disk management tools, and network diagnostic software.
- Systematic Troubleshooting Approach: Review the step-by-step approach to troubleshooting. This includes identifying the problem, isolating potential causes, and implementing solutions.
Test Taking Strategies
- Time Management: Allocate enough time to review all questions. Don’t spend too much time on a single question; move on if you’re unsure and return to it later.
- Read Carefully: Pay close attention to the wording of each question, especially when it comes to multiple-choice or true/false questions. Ensure you understand exactly what’s being asked.
- Prioritize High-Impact Areas: Focus on areas with higher point values or those that carry more weight in the assessment.
By following this checklist, you’ll be able to approach the test with confidence, knowing you’ve covered all the important topics and practiced critical skills. Take time to review, practice troubleshooting scenarios, and utilize effective test-taking strategies to maximize your performance.