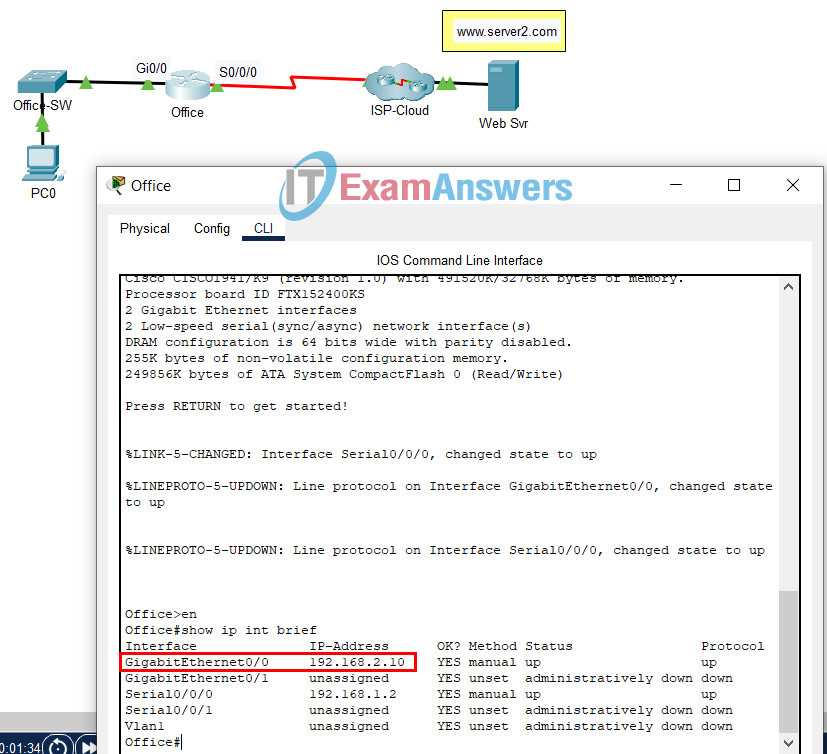
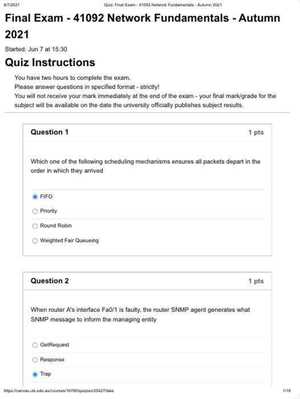
As technology continues to evolve, understanding the core principles that power modern communication systems is essential. Mastery of these concepts is crucial for those aiming to excel in the field of IT. The ability to confidently navigate through various protocols, devices, and configurations will not only help in academic assessments but also in real-world applications.
In this guide, we will explore the key topics that are commonly assessed in assessments related to communication systems. From addressing the basics of connectivity to diving deeper into advanced troubleshooting, this section will equip you with the knowledge needed to succeed. Preparation and a solid understanding of the material are vital to achieving great results in both theoretical and practical challenges.
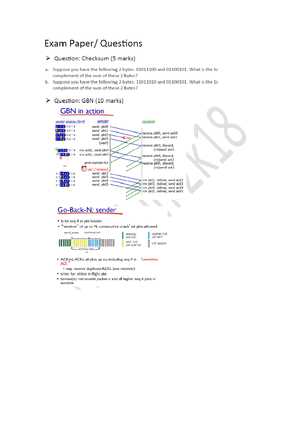
By focusing on the most critical areas and offering strategies for tackling complex scenarios, this article serves as a comprehensive resource to ensure readiness for any related challenges.
Key Concepts for Communication Systems Mastery
Understanding the core elements of digital communication is essential for anyone preparing for assessments in the IT domain. Success in this area requires a clear grasp of how various components interact to enable efficient data transfer. By focusing on the most important principles and configurations, one can build a strong foundation that applies to both theoretical and practical scenarios.
Students often encounter questions related to how information is transmitted across different mediums, the role of essential devices, and the setup of secure and reliable infrastructures. Mastering these topics ensures that individuals are well-prepared to handle a variety of practical challenges, from troubleshooting to configuration tasks.
Developing expertise in areas like protocol management, system configuration, and problem resolution is vital. With the right preparation, you can approach any question with confidence and clarity. Effective practice and understanding are the keys to excelling in this subject area.
Understanding Key Communication Concepts
To excel in the field of information technology, a strong grasp of the basic principles that govern data transmission is essential. These core ideas form the foundation of how devices exchange information, ensuring smooth and secure communication across various platforms. Whether it’s understanding the routing process, device roles, or the protocols that manage these tasks, mastering these topics is crucial for success in the IT domain.
Essential Components of Data Transmission

Data transmission relies on several key components, each playing a vital role in ensuring the smooth exchange of information. Devices such as routers, switches, and servers serve as the backbone of communication systems. Understanding how these elements work together helps to troubleshoot and optimize performance, ensuring that the system remains secure and efficient.
Protocols and Their Role
Protocols are the set of rules that govern how data is formatted, transmitted, and received. Key protocols like TCP/IP, HTTP, and DNS are fundamental for understanding how information flows through different systems. By mastering these rules, individuals can ensure seamless communication and address potential issues that may arise within a system.
Commonly Tested Communication Protocols
In the field of digital communications, understanding the protocols that govern data transfer is essential. These protocols define the rules and formats for transmitting information between devices, ensuring that data is exchanged in a secure and efficient manner. A solid grasp of these protocols is crucial for troubleshooting, configuring, and optimizing communication systems.
Some of the most commonly encountered protocols in assessments include TCP/IP, HTTP, FTP, and DNS. Each protocol serves a distinct function, whether it’s ensuring reliable delivery, supporting web browsing, or enabling file transfers. Familiarity with their structure and usage is key to understanding how information flows through the systems we rely on every day.
Essential Tools for Troubleshooting Communication Systems
When it comes to diagnosing and fixing issues in communication systems, having the right set of tools is crucial. These tools help identify problems, test connections, and ensure that everything is functioning as expected. Mastering their use can significantly reduce downtime and improve overall system reliability.
Key Diagnostic Tools
There are several tools commonly used to troubleshoot issues, ranging from simple command-line utilities to advanced software solutions. These tools help pinpoint the source of problems, whether they are related to connectivity, configuration, or device performance.
- Ping: Used to test the reachability of a device or server.
- Traceroute: Helps trace the path data takes from one device to another, identifying potential bottlenecks.
- NetFlow: Monitors traffic patterns and helps identify anomalies in data transmission.
- Wireshark: A packet analyzer that captures and inspects network traffic in detail.
Advanced Troubleshooting Tools
For more complex issues, advanced tools can offer deeper insights into system behavior and assist in pinpointing more subtle problems.
- Nessus: A vulnerability scanner that identifies security risks and weaknesses.
- SolarWinds: Provides comprehensive monitoring and diagnostics of network performance.
- Putty: A versatile SSH and telnet client used to access remote devices for configuration and troubleshooting.
Types of Communication Topologies Explained
Understanding the structure of a communication system is essential for ensuring efficient data transfer and reliable performance. The arrangement of devices and how they are interconnected significantly affects system behavior. Each topology offers unique advantages and challenges, depending on the requirements of the system.
Here are the most common types of communication topologies, each suited for different scenarios and use cases:
| Topology | Description | Advantages | Disadvantages |
|---|---|---|---|
| Bus | Devices are connected to a single central cable (bus). | Simple to implement, low cost. | Performance drops as more devices are added. |
| Star | All devices are connected to a central hub or switch. | Easy to manage, isolation of failures. | Central device failure leads to network downtime. |
| Ring | Devices form a circular loop, with each device connected to two others. | Efficient data transfer, organized flow of information. | Failure of one device can disrupt the entire network. |
| Mesh | Each device is connected to every other device in the system. | Highly resilient, multiple paths for data transmission. | Complex setup, higher cost. |
| Tree | Combines characteristics of bus and star topologies. | Scalable, hierarchical structure. | Failure in the backbone can disrupt multiple branches. |
Subnetting and IP Addressing Tips
Mastering IP addressing and subnetting is essential for efficient configuration and management of communication systems. These techniques allow for the effective division and allocation of address spaces, ensuring optimal performance and scalability. Understanding how to work with addresses and subnets is crucial for both system setup and troubleshooting.
Subnetting Strategies
Subnetting helps divide a larger address block into smaller, more manageable segments. Here are some tips to simplify the process:
- Start with the subnet mask: Identify the subnet mask for your network and determine how many bits you need to borrow from the host portion to create the required number of subnets.
- Use the 2^n rule: To calculate the number of subnets or hosts, use the formula 2^n, where n is the number of bits borrowed or left for the host portion.
- Determine network ranges: Calculate the valid address range for each subnet to ensure addresses are not duplicated.
IP Addressing Best Practices
When assigning IP addresses, it’s important to follow best practices for efficient address space management:
- Follow a structured allocation: Use a consistent scheme, such as assigning addresses by department or physical location, to avoid confusion and overlap.
- Plan for future growth: Leave room for expansion by reserving a few IP addresses in each subnet for future devices or services.
- Use private address spaces: For internal networks, use private IP address ranges (e.g., 10.x.x.x, 172.16.x.x, 192.168.x.x) to ensure security and avoid conflicts with public addresses.
How to Manage Communication Security Risks
Ensuring the security of information systems is a critical aspect of maintaining the integrity and confidentiality of data. With the increasing number of threats, managing risks effectively is essential for protecting sensitive information from unauthorized access, breaches, and other vulnerabilities. A well-structured approach helps minimize potential threats and enhances the overall security posture of the system.
By implementing a combination of preventive, detective, and corrective measures, one can create a secure environment for data exchange. Regular assessments, strong access controls, and the use of encryption technologies are fundamental in mitigating risks and safeguarding digital assets. Awareness of the latest security practices is key to staying ahead of evolving threats.
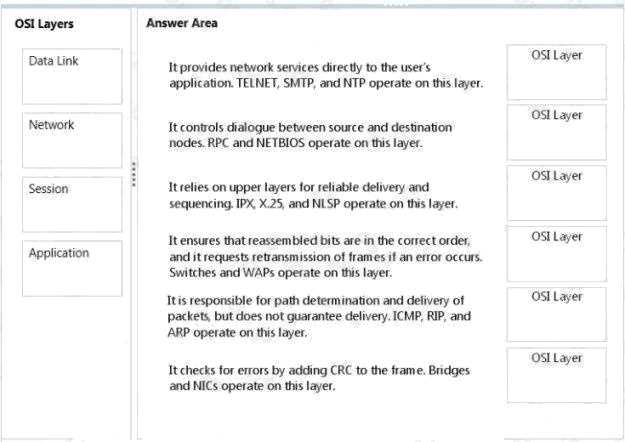
Exploring the OSI Model in Detail
The OSI model provides a structured approach to understanding how data travels from one device to another within a communication system. By breaking down the process into distinct layers, it helps clarify the functions and responsibilities of each stage in the transmission process. Each layer serves a unique role, from handling physical connections to ensuring data integrity and application functionality.
Understanding the OSI model is crucial for diagnosing issues, optimizing performance, and implementing efficient communication systems. By learning the individual layers and how they interact, professionals can better address challenges and ensure smooth, secure data exchanges across a variety of devices and platforms.
Common Communication Devices and Their Roles
In any communication setup, various devices play a critical role in facilitating the exchange of data. Each device has a specific function that contributes to the overall efficiency and security of the system. Understanding the roles of these devices helps ensure the proper configuration and troubleshooting when issues arise.
Some of the most commonly used devices include routers, switches, firewalls, and hubs. Each of these devices performs a distinct task, whether it’s directing traffic, managing data flow, or protecting against unauthorized access. Knowing their functions and how they work together can greatly enhance the performance and security of the entire system.
- Router: Directs data between different networks and manages traffic flow based on IP addresses.
- Switch: Connects devices within the same network, forwarding data packets based on MAC addresses.
- Firewall: Protects the system by monitoring and controlling incoming and outgoing traffic based on security rules.
- Hub: A basic device that connects multiple devices in a network, transmitting data to all connected devices.
Understanding the TCP/IP Protocol Suite
The TCP/IP protocol suite is a set of communication protocols used for interconnecting devices across different systems. It defines the rules and formats for data transmission and helps ensure that devices can exchange information smoothly, regardless of their underlying hardware or software. This suite is the backbone of most modern communication systems, facilitating reliable and efficient data transfer.
At the core of this suite are key protocols that handle different tasks, such as ensuring reliable delivery, addressing, and routing data. The suite is designed in layers, each responsible for specific functions, and works in tandem to ensure seamless communication across varied platforms and devices.
Key Protocols in the TCP/IP Suite
| Protocol | Purpose | Layer |
|---|---|---|
| Transmission Control Protocol (TCP) | Ensures reliable, ordered delivery of data between devices. | Transport Layer |
| Internet Protocol (IP) | Handles addressing and routing of data packets across networks. | Internet Layer |
| User Datagram Protocol (UDP) | Provides a faster, connectionless alternative to TCP for certain applications. | Transport Layer |
| Address Resolution Protocol (ARP) | Maps a device’s IP address to its physical MAC address on a local network. | Network Access Layer |
| Hypertext Transfer Protocol (HTTP) | Used for transferring web pages and other content on the World Wide Web. | Application Layer |
Key Differences Between IPv4 and IPv6
As technology evolves, so does the need for more efficient and scalable addressing schemes. Two of the most commonly used address types today are IPv4 and IPv6, each serving a distinct role in facilitating communication across devices. While both are used for identifying devices on a network, they differ significantly in terms of structure, capacity, and features, addressing the growing demand for more addresses as the internet expands.
IPv4 has been the primary protocol for assigning addresses since the early days of the internet. However, with the increase in devices connected to the internet, IPv4’s limited address space has become a bottleneck. IPv6, designed as the successor to IPv4, provides a much larger address space and additional improvements to meet the needs of a modern, connected world.
Differences in Addressing
| Feature | IPv4 | IPv6 |
|---|---|---|
| Address Length | 32-bit | 128-bit |
| Address Format | Decimal notation (e.g., 192.168.1.1) | Hexadecimal notation (e.g., 2001:0db8:85a3:0000:0000:8a2e:0370:7334) |
| Address Space | Approximately 4.3 billion addresses | Over 340 undecillion addresses |
| Address Allocation | Uses subnetting and private addresses | Auto-configuration with stateless address auto-configuration (SLAAC) |
Other Key Differences
In addition to address length and format, IPv6 brings several other improvements over IPv4:
- Improved Routing: IPv6 simplifies routing by reducing the size of routing tables and improving the efficiency of routing decisions.
- Better Security: IPv6 has built-in security features such as IPsec, offering better encryption and integrity protection for data transmission.
- Address Configuration: IPv6 supports auto-configuration, making device setup simpler and reducing the need for manual configuration or DHCP servers.
- No Need for NAT: IPv6 eliminates the need for Network Address Translation (NAT), simplifying the process of end-to-end communication between devices.
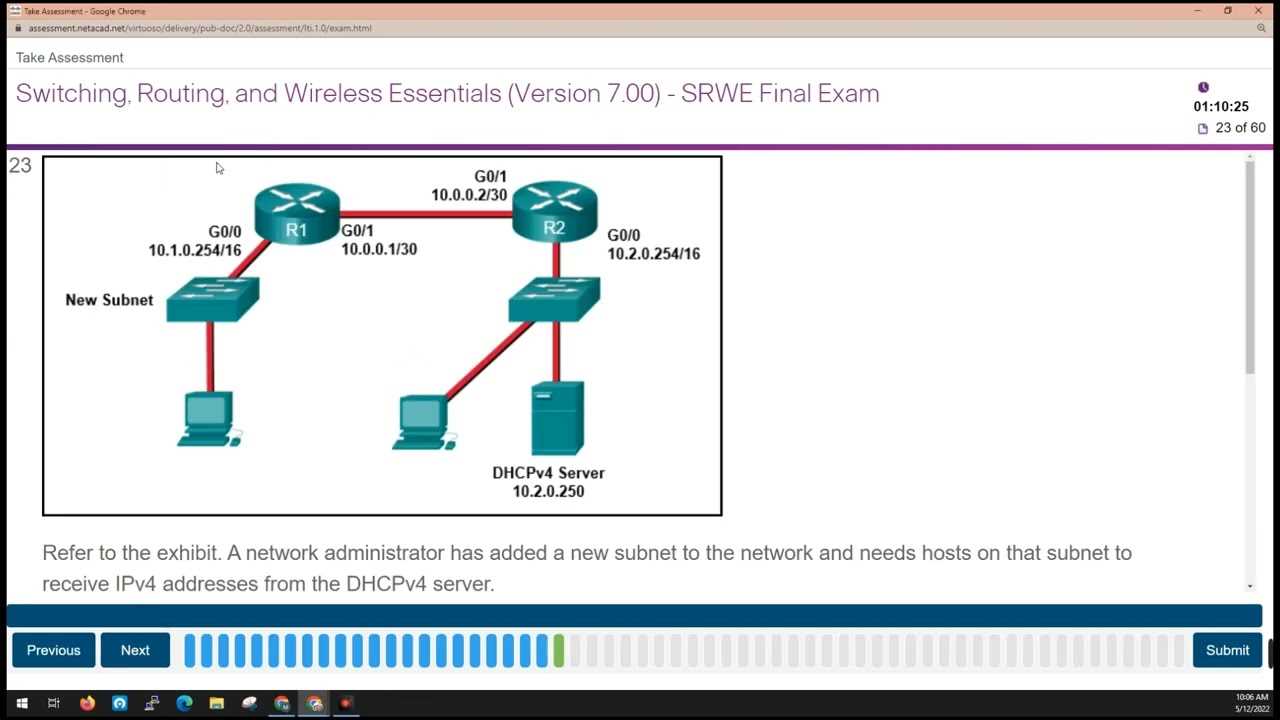
Configuring and Troubleshooting Routers
Routers are critical devices that manage the flow of data between different segments of a communication system. Configuring and maintaining these devices effectively is essential for ensuring smooth and efficient data transfer. Proper configuration enables routers to route traffic based on destination addresses, while troubleshooting helps address any issues that may arise, ensuring that traffic flows seamlessly and securely between devices.
While routers are designed to automatically handle most tasks, proper setup and ongoing troubleshooting are necessary to avoid disruptions in service. Understanding how to configure routing protocols, assign IP addresses, and implement security measures can ensure that routers perform optimally. When problems do occur, systematic troubleshooting can help pinpoint the root causes, whether it’s a configuration error, hardware failure, or connection issue.
Steps for Configuring Routers
- Initial Setup: Connect to the router’s console port to access the command-line interface (CLI) and perform basic configurations such as setting up the hostname, IP addresses, and routing protocols.
- Routing Configuration: Set up routing protocols like RIP, OSPF, or EIGRP to enable the router to communicate with other routers and direct traffic efficiently across the system.
- Security Measures: Implement access control lists (ACLs), firewall rules, and encryption protocols to secure router configurations and prevent unauthorized access.
- Testing: Use commands like “ping” and “traceroute” to verify that the router is forwarding data correctly and that there are no connectivity issues.
Troubleshooting Common Router Issues
Despite proper configuration, routers can still experience problems. Here are some common issues and troubleshooting steps:
- Incorrect IP Configuration: Ensure the IP addresses, subnet masks, and gateway settings are properly configured. A mismatch can cause connectivity issues.
- Routing Problems: Verify that routing tables are correctly populated and that routing protocols are functioning as expected. Misconfigured routes can lead to network segments being unreachable.
- Hardware Failures: Inspect router hardware components for physical damage or malfunction. This can include checking cables, interfaces, or the power supply.
- Access Control Issues: Review ACLs and firewall rules to ensure they are not blocking legitimate traffic. Modify the settings if necessary to allow proper communication.
Managing Switches and VLANs Efficiently

Efficient management of switches and Virtual Local Area Networks (VLANs) plays a crucial role in ensuring smooth data traffic flow and security within a system. Switches help direct traffic within a specific segment, while VLANs segment large networks into smaller, more manageable sections. Proper configuration and maintenance of these components enhance performance, minimize bottlenecks, and isolate network traffic, making it easier to manage and secure communication.
VLANs allow network administrators to logically segment networks based on departments, functions, or other criteria, even if devices are physically dispersed. This segmentation can improve security, limit broadcast traffic, and enhance overall performance. Meanwhile, managing switches efficiently ensures that data is transmitted quickly and without interruptions between devices, facilitating smooth communication within and between VLANs.
Best Practices for Switch Configuration
- Initial Setup: Configure basic switch settings such as device names, IP addresses, and management VLANs. Enable necessary protocols like STP (Spanning Tree Protocol) to avoid network loops.
- Port Configuration: Assign ports to specific VLANs based on organizational needs. Use access ports for end-user devices and trunk ports for connections between switches.
- VLAN Management: Create and assign VLANs to switch ports, ensuring that devices in the same VLAN can communicate efficiently. Use VLAN tagging to distinguish traffic between switches.
- Security Measures: Implement port security by limiting the number of MAC addresses per port to prevent unauthorized devices from accessing the network.
Optimizing VLAN Performance
To ensure optimal performance of VLANs, consider the following:
- Minimize Broadcast Traffic: Assign devices to the most appropriate VLAN to reduce unnecessary broadcast traffic. Too much broadcast traffic can slow down the network.
- Use VLAN Routing: For communication between VLANs, implement inter-VLAN routing. This ensures that devices in different VLANs can exchange data securely and efficiently.
- Monitor VLAN Usage: Regularly monitor the performance and traffic of each VLAN. Look for signs of congestion or underutilization to adjust configurations as needed.
- VLAN Security: Restrict access between VLANs by applying access control lists (ACLs) or firewalls. This ensures that sensitive information is protected from unauthorized users.
Wireless Networks and Their Challenges
Wireless communication systems offer convenience and flexibility, allowing devices to connect without the need for physical cables. These systems enable data transmission over airwaves, making them ideal for environments where mobility and ease of installation are important. However, despite their advantages, wireless setups come with a variety of challenges that require careful planning and management to ensure reliability and security.
While wireless solutions provide users with the freedom to connect from virtually any location within range, they are also susceptible to issues such as interference, limited coverage, and security vulnerabilities. These challenges can affect the overall performance and efficiency of wireless communication, especially in dense or high-traffic areas.
Common Issues in Wireless Systems
- Signal Interference: External factors such as electronic devices, physical obstructions, or competing wireless signals can interfere with the strength and clarity of the signal, leading to disruptions or slower data transfer speeds.
- Limited Range: Wireless signals can degrade over distance. The further a device is from the access point, the weaker the signal becomes, which can lead to slow speeds or loss of connection.
- Security Concerns: Wireless connections are more vulnerable to unauthorized access and cyberattacks if not properly secured. Strong encryption protocols and secure passwords are essential to mitigate these risks.
- Congestion and Bandwidth Issues: In crowded environments, too many devices connected to the same wireless system can cause congestion, reducing bandwidth and affecting performance. Managing network traffic and implementing quality of service (QoS) settings can help alleviate this.
Tips for Overcoming Wireless Challenges
- Channel Management: Select the optimal channel for the wireless system to avoid interference from other nearby devices. Using 5GHz frequencies can also help minimize congestion compared to the 2.4GHz band.
- Signal Boosting: Use repeaters, extenders, or additional access points to extend coverage in larger areas or environments with obstructions, ensuring that the signal reaches all devices reliably.
- Implement Strong Security Protocols: Protect wireless connections with advanced encryption methods, such as WPA3, and use secure passwords to prevent unauthorized access to the system.
- Optimize Placement of Access Points: Place access points strategically to minimize dead zones and improve coverage. Avoid physical barriers like thick walls or metal objects that can block signals.
Exam Preparation Strategies for Success
Effective preparation is key to mastering any subject and performing well in assessments. Developing a solid study plan, organizing materials, and understanding key concepts are essential steps in ensuring success. It’s not just about memorizing information but also about practicing problem-solving and applying knowledge in various scenarios. With the right strategies, you can approach your assessment with confidence and clarity.
To succeed, it’s important to start studying early, break down the material into manageable sections, and prioritize areas of weakness. Consistent review and hands-on practice can significantly boost retention and understanding. The following strategies can help streamline your preparation and maximize performance.
Building a Study Plan
- Start Early: Give yourself ample time to review all material and identify areas where you may need additional focus.
- Set Clear Goals: Break down the material into sections and set specific goals for each study session to track progress.
- Prioritize Difficult Topics: Focus more on areas you find challenging, ensuring you allocate more time to mastering them.
Maximizing Study Methods
- Practice with Sample Questions: Use practice tests and sample questions to get comfortable with the format and the types of problems that might appear.
- Active Learning: Engage in active learning techniques like summarizing material in your own words or teaching the concept to someone else.
- Review Regularly: Consistent review is crucial. Set aside time each day to go over previously studied material to reinforce memory.
Staying Focused and Relaxed
- Take Breaks: Avoid long study sessions without breaks. Short, frequent breaks help maintain focus and prevent burnout.
- Get Enough Rest: Ensure you’re well-rested before the assessment. Sleep is essential for memory consolidation and mental clarity.
- Stay Positive: Approach your preparation with a positive mindset. Confidence and a calm approach can significantly impact your performance.
Tips for Answering Network Exam Questions
When it comes to answering assessment questions, strategy plays a crucial role in demonstrating your knowledge and skills effectively. It’s important to not only understand the material but also to know how to approach each question in a way that maximizes your potential score. Focused preparation and smart techniques can help you organize your thoughts and answer confidently, even when faced with challenging queries.
Before diving into answering, it’s essential to carefully read each question and understand what is being asked. Time management is key, so allocate your time wisely to ensure you can address each part of the question thoroughly. Below are a few strategies to enhance your ability to provide clear, concise, and correct answers during your assessment.
Understanding the Question
- Read Carefully: Take time to thoroughly read each question to ensure you understand its requirements before answering.
- Identify Key Terms: Focus on the keywords in the question. These often highlight the key concept or idea that needs to be addressed.
- Break Down Complex Questions: If a question is long or complicated, break it into smaller, more manageable parts to avoid confusion.
Organizing Your Answer
- Be Clear and Concise: Ensure your answers are to the point. Avoid unnecessary details that could distract from the main idea.
- Use Bullet Points: For lists or multiple-step processes, consider using bullet points or numbered lists to make your response clearer.
- Show Your Work: If applicable, outline the steps you took to reach your answer, especially when solving problems or performing calculations.
By staying focused, carefully reading each question, and structuring your responses clearly, you’ll be able to navigate even the most challenging questions with ease.