
In academic and professional settings, the breach of sensitive material during assessments can have severe consequences. When confidential content is shared without authorization, it undermines the integrity of the process and threatens the fairness of evaluations. Such incidents can arise from various factors, including negligence, malicious intent, or even external interference. The repercussions of these actions extend far beyond the immediate violation, affecting not only the individuals involved but also the credibility of the institutions responsible for safeguarding these materials.
Confidentiality in testing environments is paramount to ensuring equal opportunities for all participants. When certain content is made accessible to unauthorized parties, it creates an unfair advantage, damaging trust in the system. This can lead to serious legal and ethical challenges, as well as jeopardizing future assessment processes.
Protecting the integrity of evaluations is a shared responsibility, requiring vigilance from both institutions and individuals to prevent such breaches. Understanding the methods of prevention and recognizing the potential consequences of sharing restricted materials can help maintain a secure and equitable environment for all involved.
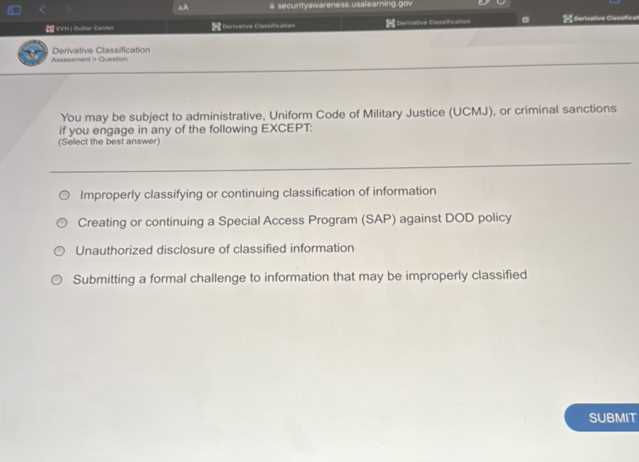
Unauthorized Disclosure of Sensitive Test Content

When private materials related to assessments are shared with individuals who are not authorized to access them, it creates significant risks for both the credibility of the process and the fairness of outcomes. Such incidents may result from intentional actions or unintended leaks, but the impact remains the same: it undermines the integrity of evaluation systems and raises serious ethical and legal concerns.
Consequences for Individuals and Institutions
The consequences of releasing restricted content without proper authorization can be severe for both the individuals involved and the institutions that oversee assessments. Legal action may be taken against those who intentionally leak sensitive data, and those who fail to uphold confidentiality can face penalties, ranging from disciplinary measures to criminal charges. Educational institutions may also face damage to their reputation, affecting their trustworthiness in future assessments and research activities.
Steps to Prevent Breaches

Preventing the unauthorized release of sensitive assessment materials requires a comprehensive approach. This includes implementing strict access controls, educating staff and participants about the importance of confidentiality, and employing technological safeguards to track and protect sensitive content. Regular audits and clear policies are essential to ensure that security measures are followed, reducing the risk of leaks and preserving the integrity of the assessment process.
What Constitutes Unauthorized Disclosure?
Revealing protected materials or confidential content to individuals who are not permitted to access it can lead to serious breaches of security and ethics. Such violations can take various forms, but they all share the common element of compromising the integrity of the protected process or system. Understanding what actions constitute a breach helps prevent these incidents and ensures proper management of sensitive materials.
Common examples of unauthorized release include:
- Sharing restricted materials with people who lack the required clearance or authorization.
- Improperly handling confidential documents or failing to follow security protocols.
- Intentionally or accidentally distributing private content via digital or physical channels without authorization.
- Allowing others to overhear or access protected materials in unsecured environments.
- Failure to report a known breach or suspicious activity related to confidential content.
Any of these actions, intentional or not, can undermine the confidentiality of protected data and create risks for individuals and organizations alike. It is crucial to have clear guidelines and procedures in place to prevent such breaches from occurring.
Legal Consequences of Information Breach
Revealing sensitive material to unauthorized individuals can result in significant legal repercussions. Depending on the nature of the breach and the laws governing the protected content, individuals and institutions can face penalties ranging from fines to imprisonment. Legal frameworks are in place to address such violations, aiming to deter breaches and ensure accountability for those involved.
Criminal Penalties
In many cases, intentionally releasing confidential content is treated as a criminal offense. Individuals found guilty of these actions can face serious consequences, including:
- Criminal charges, such as theft of intellectual property or violation of national security laws.
- Imprisonment, depending on the severity of the breach and its impact on national or institutional security.
- Fines and restitution, particularly if the breach leads to financial damage for the affected parties.
Civil Liabilities
Along with criminal penalties, those responsible for breaches may also face civil lawsuits. These can result in:
- Compensation for damages caused by the release of confidential materials.
- Loss of reputation, leading to diminished career prospects or business opportunities.
- Employment termination or professional disbarment for individuals in regulated industries.
The legal consequences are designed to emphasize the importance of protecting sensitive materials and maintaining the integrity of processes that depend on confidentiality.
Types of Protected Content in Assessments
In any formal evaluation process, certain materials are considered sensitive and are protected by strict confidentiality rules. These protected materials can vary depending on the type of assessment and the level of security required. Understanding the different categories of such content is crucial for ensuring their proper handling and preventing unauthorized access.
Test Materials and Questions
One of the most important types of protected content in assessments is the actual test content itself. This includes:
- Questions and problems that are specific to a particular evaluation session.
- Specialized scenarios or case studies designed to assess higher-level skills.
- Drafts or preliminary versions of future tests that are not yet publicly available.
Evaluation Criteria and Grading Systems
Alongside the actual content, the criteria used to assess performance is also considered sensitive. This includes:
- Detailed grading rubrics that are specific to each type of assessment.
- Marking schemes, which outline how points are awarded for each question or section.
- Key to scoring systems that are used to determine overall performance in the assessment.
Protecting these types of materials ensures fairness, prevents cheating, and maintains the integrity of the assessment process.
Common Ways Content Gets Leaked
In many situations, sensitive materials related to assessments can be unintentionally or deliberately exposed. These breaches can occur through various channels, and understanding how these leaks happen is essential in preventing them. Whether through negligence or malicious actions, the consequences of such leaks can be significant and far-reaching.
Physical Security Failures
One common way that protected content becomes accessible to unauthorized individuals is through lapses in physical security. These breaches can occur in several ways:
- Improper storage of test materials, leaving them in unsecured areas.
- Employees or participants accessing restricted areas without proper clearance.
- Lack of supervision during the handling of sensitive documents.
- Physical theft of materials during transport or storage.
Digital Leaks and Cybersecurity Issues
Another significant cause of leaks is digital vulnerabilities. In today’s world, many materials are stored or transmitted electronically, which can open up new avenues for exposure:
- Weaknesses in digital security systems that allow hackers to access protected data.
- Improper sharing of files through unsecured networks or unauthorized email.
- Inadvertent sharing of materials via social media or other digital platforms.
- Insufficient encryption and protection of sensitive files during digital storage or transmission.
Both physical and digital security failures contribute to the risks of sensitive content being leaked, making it crucial to implement effective protection strategies in both realms.
Impact on National Security and Assessments
When confidential materials related to formal evaluations are exposed, the consequences can extend far beyond the immediate breach. Such incidents not only undermine the credibility of the assessment process but can also jeopardize national security, particularly when the content involves sensitive topics or individuals’ performance in critical areas. The exposure of protected content creates vulnerabilities that can be exploited by malicious actors, with lasting effects on both the integrity of academic or professional systems and broader security concerns.
Effects on National Security
When protected content involves national defense or intelligence-related assessments, the consequences of exposure are particularly grave. Breaches can lead to:
| Potential Impact | Description |
|---|---|
| Risk of Espionage | Leaked materials can provide critical insights to adversaries, compromising the security of national defense strategies. |
| Compromise of Sensitive Operations | Exposure of test content or performance data may reveal ongoing or planned operations, putting lives and resources at risk. |
| Loss of Trust | National security agencies may lose the trust of citizens and global allies, undermining their effectiveness in future operations. |
Impact on the Integrity of Assessments
The integrity of formal assessments can be severely impacted when sensitive materials are leaked. This includes:
- Undermining the fairness of the process, as some participants gain an unfair advantage through unauthorized access.
- Damage to the reputation of institutions that conduct high-stakes assessments, affecting their credibility in future endeavors.
- Potential legal action and penalties for individuals or organizations responsible for the breach, further eroding trust in the system.
The broader consequences of such breaches can be widespread, affecting not only national security but also public confidence in the integrity of key systems that rely on confidentiality.
Understanding the Severity of Violations
When protected materials related to assessments are compromised, the consequences can be far-reaching. The severity of such breaches depends on several factors, including the type of content involved, the intent behind the leak, and the potential damage caused. Understanding the scale of these violations helps to highlight the importance of maintaining strict confidentiality in all aspects of sensitive processes.
Impact on Individuals
For individuals involved in the leak, the consequences can be severe. Not only can they face legal action, but their personal and professional reputations may also be permanently tarnished. Criminal charges and fines are common legal outcomes, and those responsible may also face employment termination or be permanently banned from participating in certain professional fields. The violation can also result in personal consequences, such as social stigma or damage to relationships within the community.
Consequences for Institutions
When the breach involves an institution, the fallout can be just as significant. Educational or professional organizations that fail to safeguard sensitive materials risk losing the trust of their stakeholders. This erosion of trust can lead to:
- Legal liabilities, with potential financial penalties or lawsuits.
- Reputational damage, which may impact future collaborations or partnerships.
- Increased scrutiny from regulatory bodies, which may impose stricter policies and oversight.
The severity of a breach is not limited to the immediate consequences but also includes the long-term damage that can undermine the institution’s credibility and effectiveness.
Ethical Considerations in Assessment Integrity
Maintaining the integrity of formal evaluations goes beyond following legal guidelines–it also requires a strong commitment to ethical principles. When sensitive materials are compromised, the impact extends far beyond the immediate breach. Understanding the ethical implications of such actions is essential for protecting fairness, trust, and accountability within evaluation systems.
Respecting Fairness and Equal Opportunity
One of the key ethical considerations in maintaining assessment integrity is ensuring that all participants have an equal opportunity to succeed. When protected materials are exposed, it creates an unfair advantage for some, while disadvantaging others who rely on their knowledge and preparation. This undermines the principle of fairness, which is foundational to most educational and professional systems. Some consequences include:
- Unjust competition, where some individuals may gain an edge they did not earn.
- Disillusionment among honest participants, who may feel their efforts are in vain.
- Damage to the credibility of the assessment process itself.
Responsibility to Protect Sensitive Content
Another ethical consideration is the duty to safeguard sensitive content. Professionals involved in the handling, storage, and transmission of evaluation materials must adhere to strict ethical standards. Failing to do so not only exposes individuals to risks but can also result in broader societal consequences. The responsibility to protect such content involves:
- Ensuring that all materials are handled with the highest level of confidentiality.
- Being vigilant about the security measures in place to prevent any unauthorized access.
- Recognizing that even small lapses in security can have far-reaching effects on the integrity of the entire system.
Adhering to ethical standards in evaluation systems ensures that trust is maintained, and the credibility of both institutions and individuals is preserved.
Penalties for Unauthorized Sharing of Sensitive Content
Sharing confidential materials without proper authorization is a serious offense, and the consequences can be severe. When sensitive content is exposed, whether intentionally or due to negligence, the law imposes penalties to deter such actions and maintain the integrity of systems that rely on confidentiality. These penalties vary depending on the nature of the violation, the severity of the breach, and the parties involved.
Legal Consequences
Depending on the jurisdiction, individuals who share protected content without permission may face significant legal penalties. These may include:
- Criminal Charges: Violators can face criminal prosecution, with charges ranging from misdemeanors to felonies, depending on the severity of the breach.
- Fines: In many cases, individuals found guilty of improper sharing may be required to pay substantial fines as part of the penalty.
- Imprisonment: For particularly serious offenses, individuals may face jail time, especially if the breach compromises national security or results in significant harm.
Professional and Social Consequences

In addition to legal penalties, individuals involved in sharing sensitive materials without authorization often experience long-term damage to their personal and professional lives. The consequences may include:
- Job Loss: Individuals caught sharing confidential content may lose their employment, especially if the violation violates company or institutional policies.
- Reputation Damage: A breach of trust can tarnish an individual’s reputation, making it difficult to find future employment or maintain relationships within their professional community.
- Legal and Civil Suits: In some cases, the affected parties may pursue civil litigation, seeking compensation for the harm caused by the breach.
The penalties for improperly sharing sensitive content are designed to protect the integrity of the systems and ensure that those responsible face appropriate consequences for their actions.
How to Prevent Information Leaks in Exams

Protecting sensitive materials during assessments is crucial for maintaining fairness and the integrity of the process. There are several strategies and best practices that can be implemented to minimize the risk of leaks and ensure that all participants are evaluated under equal conditions. These measures focus on strengthening security, raising awareness, and establishing clear protocols for handling confidential content.
Effective Security Measures
One of the most important steps in preventing leaks is enhancing the security of both digital and physical materials. Some key actions include:
| Security Measures | Benefits |
|---|---|
| Encryption of digital files | Prevents unauthorized access to digital content during transmission. |
| Restricted access to sensitive materials | Limits exposure to only authorized personnel, reducing the chance of leaks. |
| Physical security measures (e.g., locked storage) | Ensures that hard copies of materials are securely stored, minimizing the risk of physical theft. |
| Secure printing and copying protocols | Prevents unauthorized duplication or distribution of materials. |
Training and Awareness
All individuals involved in handling sensitive materials must be properly trained and made aware of their responsibilities. This includes:
- Educating staff on security policies and procedures to ensure they understand how to safeguard materials.
- Regular security briefings to keep everyone updated on potential threats and the latest security practices.
- Implementing non-disclosure agreements (NDAs) for those who handle or have access to protected materials.
By taking proactive steps to enhance security and foster a culture of responsibility, institutions can significantly reduce the likelihood of sensitive content being compromised during assessments.
Role of Education Institutions in Protection
Educational institutions play a crucial role in safeguarding sensitive materials and ensuring the integrity of assessment processes. They are responsible for creating a secure environment in which both students and staff understand the importance of confidentiality and the consequences of breaching that trust. Implementing effective protection measures and enforcing strict protocols is key to maintaining the credibility of academic systems.
Key Responsibilities of Educational Institutions
Schools, colleges, and universities must take proactive steps to prevent any unauthorized access to protected materials. Their responsibilities include:
| Responsibility | Action |
|---|---|
| Setting clear policies | Institutions should establish clear, written guidelines regarding the handling and protection of sensitive materials. |
| Training staff and students | Providing regular training sessions on the importance of confidentiality and how to avoid potential risks. |
| Monitoring access | Monitoring who has access to sensitive materials, ensuring that only authorized individuals are involved in the process. |
| Implementing technology solutions | Using encryption, access controls, and secure online platforms to protect digital materials and communications. |
Collaborative Approach
In addition to internal measures, educational institutions can work collaboratively with external organizations, including security experts and law enforcement, to ensure that they are up-to-date with best practices for safeguarding protected materials. This collaborative approach enhances the overall security and minimizes the risks of leaks.
By taking these steps, educational institutions contribute significantly to the protection of sensitive content and uphold the fairness of academic assessments.
Case Studies of Exam Information Leaks
Over the years, several incidents have occurred where confidential materials related to academic assessments were improperly shared, leading to serious consequences. These cases highlight the importance of robust security measures and the need for vigilance in handling sensitive content. Examining real-life examples can provide valuable insights into how leaks happen and what can be done to prevent them in the future.
In one notable case, a university experienced a breach when a staff member accidentally shared a digital version of a test with unauthorized recipients. This error led to widespread cheating, as students gained access to the questions ahead of time. The institution took swift action, revoking access to the materials and implementing stricter controls on how test content was handled.
Another case involved a group of students who used their online platform to share answers during a timed assessment. Despite efforts to monitor the system, the students managed to coordinate their actions, exploiting loopholes in the platform’s security. This led to a review of the online testing software and significant updates to prevent similar occurrences in the future.
These examples emphasize the need for educational institutions to continuously review and enhance their security protocols, ensuring that materials are only accessible to those who are authorized and that technology used in assessments is fully secure.
How Whistleblowers Can Affect Exam Security
Whistleblowers can play a pivotal role in maintaining the integrity of academic assessments by exposing unethical or illegal activities related to the handling of protected materials. When individuals within an institution or involved in the assessment process become aware of irregularities or breaches, their decision to report these incidents can significantly impact the overall security of the system. However, the involvement of whistleblowers can be both beneficial and challenging, depending on how the information is handled and the consequences of the exposure.
The Role of Whistleblowers

Whistleblowers are individuals who reveal information about wrongdoing, often at great personal risk. In the context of academic settings, they may expose activities such as:
- Leaking test content to students ahead of time.
- Collusion between staff members and students.
- Inadequate security measures that make assessments vulnerable to cheating.
When these issues are brought to light, institutions are forced to address the root causes and implement corrective measures. Whistleblowers can thus act as catalysts for positive change, leading to tighter controls and improved systems for protecting sensitive materials.
Challenges and Implications

While whistleblowers can help to uncover issues, their actions can also have unintended consequences. If the information is not handled properly or if the whistleblower’s motives are questioned, the situation can escalate and damage the reputation of the involved parties. Furthermore, whistleblowing can sometimes lead to retaliation, creating a chilling effect where others may be hesitant to report problems in the future.
Overall, the involvement of whistleblowers can be a double-edged sword, but when managed correctly, their actions can lead to stronger protections, more transparency, and a fairer academic environment.
The Role of Technology in Exam Protection

Technology plays a crucial role in safeguarding sensitive academic content, offering innovative tools and systems designed to prevent breaches and maintain the integrity of assessments. With the growing reliance on digital platforms for testing, ensuring that these systems are secure is more important than ever. Technology not only helps in monitoring and securing materials but also provides mechanisms for verifying the identity of participants and ensuring fair access to resources.
One of the primary ways technology helps in exam protection is through secure online platforms that encrypt materials and monitor student behavior during assessments. These platforms use various features like randomized question pools, time limits, and digital tracking to reduce the risk of cheating. Additionally, advanced technologies such as artificial intelligence (AI) are being utilized to detect suspicious activities in real-time, enhancing the ability to prevent dishonesty.
Another key aspect of technological protection is the use of biometric authentication. Systems that require fingerprint scanning, facial recognition, or even voice verification ensure that only the authorized individuals are able to participate in assessments, reducing the risk of impersonation and other forms of fraud. Furthermore, digital proctoring has become a common method for monitoring remote assessments, providing a virtual safeguard to ensure that participants adhere to the rules and guidelines of the testing environment.
Overall, the integration of technology into academic security systems provides institutions with powerful tools to protect their materials and ensure that assessments are conducted fairly and securely.
Best Practices for Secure Exam Design
Designing secure assessments is essential to prevent breaches and ensure fairness for all participants. A well-constructed testing environment minimizes opportunities for cheating or manipulation while maintaining the integrity of the evaluation process. To achieve this, educators and administrators must employ strategies that focus on both digital and physical safeguards. Below are several best practices that can help enhance the security of academic evaluations.
1. Use Randomization and Question Pools
One of the most effective ways to reduce the likelihood of cheating is by utilizing randomized question sets. By creating pools of questions that are randomly assigned to each participant, it ensures that no two individuals receive the same set of queries. This reduces the chances of students collaborating or accessing previous exam materials. Key strategies include:
- Generating multiple question versions with varying difficulty levels.
- Shuffling question order for each student.
- Ensuring questions test different aspects of the subject matter.
2. Implement Strong Authentication and Monitoring
To ensure that only authorized individuals participate, implementing strong authentication measures is crucial. This may include biometric verification, secure login credentials, and two-factor authentication. In addition to identity checks, it is essential to monitor participant behavior during assessments. Tools such as remote proctoring and surveillance software can help prevent cheating by tracking unusual activity or movement.
- Require students to verify their identity with multiple forms of authentication.
- Use surveillance tools to monitor behavior during online assessments.
- Enable real-time alerts for suspicious activities such as screen sharing or excessive time on a single question.
3. Limit Access to Test Materials
Controlling access to assessment materials is a critical step in securing academic content. This can be achieved by using secure platforms that prevent unauthorized access and by ensuring that test materials are only available to those who need them. Restrictions can include:
- Providing access to questions only within a specific time frame.
- Limiting materials to specific devices or networks to prevent external access.
- Restricting copying, downloading, or printing of test content.
By integrating these best practices, institutions can create a more secure testing environment that protects both the students and the academic integrity of the institution.
Reporting Suspected Information Breaches
When a security breach occurs, it is critical to act swiftly and appropriately to mitigate potential harm. Identifying and reporting any suspicious activity related to sensitive materials is essential for maintaining the integrity of an institution’s operations. Prompt reporting allows authorities to investigate and take corrective measures before further damage is done. Below are key steps to follow if a breach is suspected.
1. Recognizing Potential Breaches
Before reporting a suspected breach, it’s important to recognize what constitutes unusual behavior or compromised security. Some signs may include:
- Unexplained access to restricted documents or systems.
- Sudden spikes in data transfers or download activity.
- Unauthorized sharing or copying of sensitive files.
- Suspicious communication or interactions with individuals outside the organization.
If any of these signs are observed, it is crucial to report them immediately to the relevant authorities or security team. Early intervention can prevent more severe consequences.
2. How to Report Suspected Breaches
Reporting a suspected breach involves several steps to ensure proper documentation and action. The process typically includes:
- Contacting Security Personnel: Notify the organization’s security team or IT department about the incident.
- Providing Detailed Information: Be prepared to provide clear details about the event, including the time, location, and any individuals involved.
- Following Protocols: Ensure you follow any internal reporting procedures or use designated channels for security concerns.
Once a report is made, the incident will be thoroughly investigated, and appropriate actions will be taken to mitigate risks. Depending on the severity of the breach, additional steps may involve legal actions or system audits.
By promptly reporting suspected breaches, everyone plays a crucial role in protecting sensitive materials and maintaining a secure environment.
Long-Term Effects on Academic Reputations
When sensitive materials are compromised, the repercussions can extend far beyond immediate consequences. Institutions and individuals involved in such breaches may face long-lasting damage to their credibility. The effects on reputation can be particularly severe for academic institutions, which rely on trust, integrity, and the protection of their intellectual environment. This section explores the far-reaching consequences of such breaches on academic standing and the trust placed in educational systems.
1. Damage to Institutional Trust
Once a breach occurs, it can significantly undermine public confidence in the institution’s ability to safeguard its operations. Students, faculty, and external stakeholders may question the effectiveness of policies in place to protect sensitive materials. The resulting distrust can lead to:
- A decrease in student enrollment and faculty recruitment.
- Loss of funding or support from governmental and private organizations.
- Negative media attention that tarnishes the institution’s reputation.
Over time, the damage to an institution’s reputation may take years to rebuild, especially if corrective actions are not taken promptly or effectively. The lingering effects of a breach can hinder an institution’s ability to attract top talent or maintain its position within academic rankings.
2. Impact on Individual Careers
For those directly involved in a breach, the effects on personal reputations can be devastating. Academic staff or students found to be associated with compromised materials may struggle to regain professional trust. Some of the long-term consequences include:
- Difficulty in securing future academic or professional positions.
- Loss of professional credibility, which can hinder career advancement.
- Damage to personal relationships within academic networks.
Even if an individual is not directly responsible for the breach, merely being linked to the event can tarnish their reputation for years to come. This can create challenges in rebuilding one’s professional standing, especially in a highly competitive field like academia.
In summary, breaches involving sensitive academic materials have the potential to inflict severe long-term damage on both institutional and individual reputations. The recovery process is often slow, requiring concerted efforts to rebuild trust and restore credibility.