
Achieving success in a penetration testing certification requires not only technical proficiency but also strategic planning. The journey involves tackling complex scenarios, utilizing various tools, and applying critical thinking to find vulnerabilities in systems. Knowing how to approach these tasks and stay organized is key to performing effectively under pressure.
Preparation plays a significant role in shaping the outcome. By understanding the structure and requirements of the test, candidates can build a solid foundation for addressing challenges. Focus on practical experience, problem-solving, and time management to ensure you’re ready for real-world application.
In this guide, we will explore essential tactics to help you navigate through the testing process, enhance your technical skills, and boost your chances of success. Whether you’re just starting or looking to refine your approach, these insights will help you gain confidence and excel in tackling demanding scenarios.
OSCP Exam Overview
Obtaining a certification in ethical hacking is a challenging yet rewarding experience. The process involves testing both your theoretical knowledge and practical abilities in identifying and exploiting security weaknesses. Candidates are expected to demonstrate competence through real-world tasks and detailed reporting on the techniques used.
Key Components of the Certification
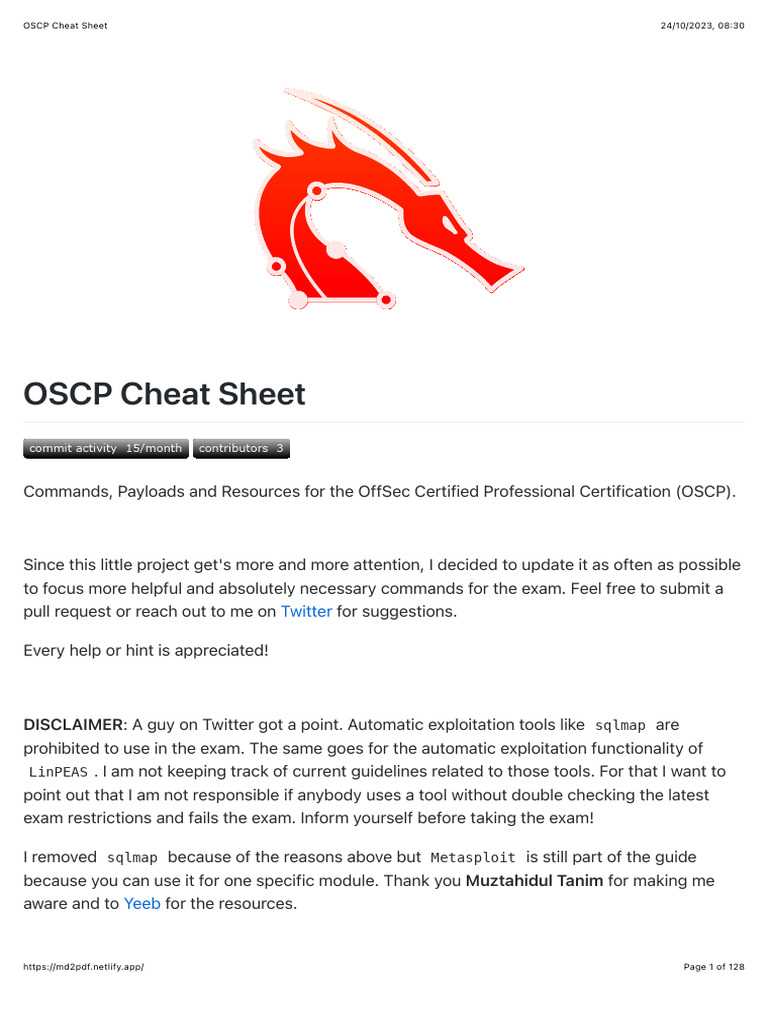
The certification journey consists of a series of structured tests, requiring participants to solve multiple penetration testing challenges. These challenges are designed to assess a wide range of skills, from vulnerability discovery to exploit development and post-exploitation techniques. Candidates must work within a limited timeframe, which emphasizes time management and precision in execution.
Skills Tested and Required

To succeed, a candidate must possess a solid understanding of penetration testing methodologies, network security, and various exploitation tools. Hands-on experience with real-world scenarios, including web application security, network security, and system exploitation, is crucial. Mastery of scripting languages and the ability to think critically in unpredictable environments is also highly valued.
What to Expect from the Exam
When preparing for a penetration testing certification, it’s essential to understand the structure and expectations of the assessment. This challenge is designed to test your practical skills in identifying, exploiting, and mitigating security vulnerabilities across various systems. The tasks are not just theoretical but involve real-time problem solving and hands-on engagement with complex environments.
The evaluation is divided into multiple practical scenarios that require you to apply both your knowledge and your ability to think critically under pressure. You will encounter challenges that involve network exploitation, web application vulnerabilities, and system penetration, all of which must be approached methodically and efficiently. Effective time management is critical, as each challenge is timed to simulate real-world deadlines.
In addition to solving the technical challenges, you will be required to document your findings in a professional report. This task tests your ability to communicate technical details clearly and concisely, a crucial skill for any penetration tester. Expect to spend a significant amount of time crafting detailed write-ups that reflect your thorough understanding of each exploitation method used.
Essential Preparation Tips
Success in a penetration testing certification requires thorough preparation and the right mindset. To excel, it’s important to focus on both technical skills and the ability to approach problems strategically. Understanding the key areas covered and practicing hands-on scenarios will help you build confidence and improve your performance.
Master the Fundamentals

Before diving into complex scenarios, ensure you have a strong grasp of basic concepts like networking, operating systems, and security protocols. Mastery of common attack vectors and vulnerability types is crucial for identifying and exploiting weaknesses in various systems. Familiarity with command-line tools and scripting languages like Python will be especially valuable.
Hands-On Practice and Labs

One of the most effective ways to prepare is through continuous, hands-on practice. Set up your own lab environment, or use platforms that simulate real-world challenges to gain practical experience. Engage in practical exercises such as network scanning, vulnerability scanning, and exploitation to strengthen your troubleshooting and problem-solving abilities. The more you practice, the more familiar you’ll become with various techniques and tools.
Understanding the Exam Structure
The certification assessment consists of a well-structured and challenging series of practical tasks designed to evaluate your technical skills and problem-solving abilities. The goal is to simulate real-world penetration testing scenarios where you must identify, exploit, and mitigate security weaknesses across multiple systems. Understanding the structure and format of the test is crucial to managing your time effectively and ensuring you can handle the complexity of each challenge.
Test Components and Tasks
The assessment is divided into several practical challenges that cover a range of cybersecurity domains. These tasks typically involve network exploitation, web application vulnerabilities, and system penetration. Each task is time-bound, so you must work efficiently to complete as many as possible within the allotted timeframe. You will also be required to produce a detailed report documenting your findings and the methods you used to exploit the systems.
Time Management and Reporting
Time is one of the most critical factors in the certification. Properly managing your hours between exploiting systems and documenting your work is essential. Candidates must complete all tasks and submit a comprehensive report within the given timeframe. The written report must accurately explain the vulnerabilities discovered, the tools used, and the steps taken to compromise the systems. Clear and concise communication is key, as it demonstrates your understanding of the exploitation techniques employed.
Common Mistakes to Avoid
During a penetration testing certification, several common mistakes can hinder your performance and prevent success. These errors typically arise from poor time management, lack of thorough preparation, or a failure to stay organized under pressure. Being aware of these pitfalls can help you avoid them and improve your chances of passing the assessment with confidence.
Poor Time Management

One of the most significant challenges is balancing the time spent on each task. It’s easy to get caught up in a single challenge and lose track of time. To avoid this, consider the following:
- Break the tasks into smaller, manageable steps.
- Prioritize challenges that are easier or more familiar to you.
- Set strict time limits for each task to avoid over-investing time in one area.
- Regularly assess your progress to ensure you’re on track to complete everything.
Inadequate Documentation
Many candidates focus too much on exploiting vulnerabilities and neglect the importance of documenting their findings. This can lead to incomplete reports that affect the final score. To improve your documentation:
- Write clear, concise explanations of the techniques you used.
- Ensure that all vulnerabilities and exploit methods are fully explained.
- Provide detailed step-by-step instructions to replicate your process.
- Always proofread your report for clarity and accuracy.
By avoiding these common mistakes, you’ll be better prepared to approach each challenge with confidence and complete the tasks efficiently.
Time Management During the Exam
Effective time management is a critical factor in successfully completing a penetration testing certification. With limited hours to tackle multiple challenges, managing your time wisely is essential for maximizing performance. A structured approach to dividing your time between different tasks ensures you don’t get overwhelmed or focus too much on any single problem, allowing you to complete everything within the allocated period.
Strategies for Time Allocation
Planning how much time to spend on each task can significantly impact your ability to finish the assessment. It’s important to remain flexible, but having an initial plan will help guide your progress. Below is a suggested breakdown of time allocation:
| Task | Suggested Time | Notes |
|---|---|---|
| Initial Setup and Recon | 1-2 hours | Focus on scanning and gathering information about targets. |
| Exploitation Phase | 3-4 hours | Prioritize systems you’re most confident in exploiting. |
| Post-Exploitation | 1-2 hours | Ensure you’ve gathered necessary data and confirmed access. |
| Report Writing | 2-3 hours | Document all findings, exploits, and methodologies clearly. |
Adjusting Based on Progress
As you progress through the challenges, be prepared to adjust your time strategy. If you’re spending too much time on one task without success, move on to another and return later with a fresh perspective. Keep track of your overall progress and adjust as necessary to ensure that you meet the final deadline.
Tools and Resources for OSCP
Equipping yourself with the right tools and resources is essential for success in any penetration testing challenge. The right set of utilities can significantly improve efficiency and effectiveness in identifying vulnerabilities, exploiting weaknesses, and conducting post-exploitation activities. Familiarity with a variety of tools, both open-source and commercial, is a key aspect of preparation.
Essential Tools for Penetration Testing
During the assessment, you’ll need to leverage a range of tools to perform network scanning, vulnerability assessment, exploitation, and reporting. Here are some of the most commonly used tools:
- Nmap – A powerful network scanner for mapping out networks and identifying open ports and services.
- Netcat – A versatile networking utility often used for creating reverse shells and transferring data.
- Metasploit – A comprehensive exploitation framework that helps in developing and executing exploit code against vulnerable targets.
- Burp Suite – An integrated platform for testing web application security, including tools for scanning, crawling, and exploiting web vulnerabilities.
- Hydra – A tool for brute-force attacks against various protocols to test password strength.
- John the Ripper – A widely used password cracking tool to test password hashes for weaknesses.
Online Resources for Practice and Learning
In addition to tools, there are several online platforms and resources that can help you sharpen your skills and prepare for the test:
- Hack The Box – A popular platform for practicing real-world penetration testing challenges and CTF (Capture The Flag) exercises.
- TryHackMe – An interactive, beginner-friendly learning platform that offers guided exercises and labs to hone penetration testing skills.
- Pentest Academy – Offers comprehensive courses and labs specifically designed for penetration testers looking to improve their technical abilities.
- SecurityTrails – A great resource for information gathering and recon, with data on domains, IP addresses, and more.
- OWASP – Provides valuable resources on web security, including the OWASP Top Ten vulnerabilities, which are important to understand during assessments.
By mastering these tools and leveraging online resources, you will improve your ability to tackle complex challenges efficiently and thoroughly.
Practice Labs and Virtual Environments
Setting up a practice lab or using virtual environments is essential for honing your skills in a controlled, risk-free space. These environments allow you to replicate real-world scenarios, explore different attack vectors, and experiment with various tools and techniques without fear of affecting live systems. By regularly practicing in such labs, you can build confidence and improve your problem-solving abilities before facing more complex challenges.
Setting Up Your Own Lab
Creating your own testing environment can help you practice in a way that mirrors the real challenges you will encounter. This process can include configuring multiple virtual machines (VMs) running different operating systems and services. Here are some elements to consider:
- Virtualization Software: Tools like VirtualBox or VMware provide a flexible environment for running multiple virtual machines on a single host.
- Operating Systems: Use a variety of OSes (Linux, Windows, etc.) to simulate different attack surfaces.
- Network Configuration: Set up network settings to simulate a realistic environment with firewalls, routers, and isolated subnets.
- Security Tools: Install and configure common penetration testing tools (like Nmap, Metasploit, and Burp Suite) on the virtual machines.
Using Online Platforms for Practice
If you prefer a pre-configured environment, several online platforms provide access to practice labs and challenges. These platforms simulate real-world scenarios with the added benefit of automated scoring and feedback. Popular platforms include:
- Hack The Box: Offers a wide range of machines and challenges designed to simulate real-world security issues, with an emphasis on both offensive and defensive techniques.
- TryHackMe: Provides guided, beginner-friendly labs and challenges covering a variety of security topics, from web application testing to network exploitation.
- VulnHub: A repository of downloadable virtual machines designed to offer hands-on security challenges, ranging from beginner to advanced levels.
- Offensive Security Proving Grounds: A platform offering challenges similar to the official assessments, with real-time simulations of penetration testing tasks.
By regularly engaging with these platforms and setting up your own practice labs, you’ll be better prepared to tackle complex penetration testing challenges with efficiency and expertise.
Test Your Skills Before the Exam
Before attempting any formal certification, it’s crucial to evaluate your skills through practical tests and challenges. This will help you identify areas where you’re proficient, as well as those where you may need further practice. By engaging in realistic scenarios and self-assessments, you can boost your confidence and readiness, ensuring you’re prepared for the full spectrum of tasks you will face during the actual assessment.
Engage in Capture the Flag (CTF) Challenges

CTF challenges are an excellent way to simulate real-world penetration testing tasks. These competitions involve solving a series of security-related puzzles that range from simple to highly complex. Engaging in CTF challenges helps you sharpen both your problem-solving skills and technical expertise. Here are some popular platforms offering CTF exercises:
- PicoCTF: A beginner-friendly platform with a wide range of puzzles to help you build a strong foundation in security testing.
- Root Me: Offers a wide variety of CTF challenges, covering topics from cryptography to web application security.
- Hack The Box: Known for its advanced-level challenges, HTB provides an environment for testing your skills in vulnerability exploitation and network pentesting.
Simulate Real-World Scenarios
One of the best ways to assess your skills is to simulate real-world penetration testing engagements. This can include tasks such as identifying vulnerabilities, exploiting systems, and gaining access to networks. Many platforms and virtual labs offer scenarios that closely resemble the actual assessment, allowing you to practice in a controlled environment. Make sure to cover a wide range of techniques, from enumeration to post-exploitation tasks, to ensure you’re well-rounded and ready for any challenge.
By participating in these practical exercises, you can confidently measure your abilities and make any necessary adjustments to your preparation strategy before the official evaluation.
Penetration Testing Techniques to Master
Mastering penetration testing techniques is essential for successfully identifying and exploiting vulnerabilities in a target system. These skills enable security professionals to assess the effectiveness of security measures and find weaknesses before malicious actors can exploit them. Familiarity with key testing methods will not only enhance your problem-solving abilities but also improve the quality and thoroughness of your security assessments.
Information Gathering and Reconnaissance
The first step in any security assessment is information gathering. This phase involves collecting as much data as possible about the target system without interacting directly with it. Reconnaissance can help you identify potential attack vectors and weak points in the network infrastructure. Key techniques to master include:
- DNS Interrogation: Using tools like nslookup and dig to gather information about domain names and IP addresses.
- Social Engineering: Techniques such as phishing or pretexting to gather information from individuals or public records.
- Network Scanning: Tools like Nmap and Masscan are crucial for identifying live hosts, open ports, and running services.
Exploitation and Privilege Escalation
Once vulnerabilities are identified, the next step is to exploit them to gain unauthorized access or elevate privileges within the system. This phase requires a deep understanding of various attack techniques and how they can be used to bypass security mechanisms. Key techniques include:
- Exploitation of Weak Services: Using tools like Metasploit to exploit vulnerabilities in services such as FTP, SSH, and HTTP.
- Buffer Overflow Attacks: Manipulating buffer overflows to execute arbitrary code and take control of the system.
- Privilege Escalation: Techniques like exploiting Sudo vulnerabilities or exploiting misconfigured permissions to gain root or admin access.
Mastering these techniques will make you a more effective penetration tester, able to conduct thorough and efficient security assessments that uncover hidden vulnerabilities.
Report Writing Best Practices
Effective report writing is an essential skill for documenting security assessments and presenting findings to stakeholders. A well-written report not only highlights vulnerabilities and issues but also provides clear, actionable recommendations for remediation. A structured, concise, and professional approach to report writing ensures that the results of an assessment are communicated effectively and understood by both technical and non-technical audiences.
Key Sections to Include
To create a comprehensive and professional report, it’s important to include key sections that detail your process, findings, and recommendations. Each section should be clear and concise, ensuring that the reader can easily follow the narrative of the assessment. The following table outlines the essential sections to include in a security report:
| Section | Description |
|---|---|
| Executive Summary | A high-level overview of the assessment, focusing on key findings, risks, and recommendations. This section should be accessible to non-technical stakeholders. |
| Methodology | Details the approach and tools used during the testing process, explaining how vulnerabilities were discovered and exploited. |
| Findings | Specific vulnerabilities discovered during the assessment, including technical details such as IP addresses, port numbers, and affected systems. |
| Risk Assessment | Evaluation of the severity of each finding, often categorized as low, medium, or high risk, with potential impact on the organization. |
| Recommendations | Clear, actionable suggestions to remediate the identified vulnerabilities and mitigate associated risks. |
| Conclusion | A summary of the key points covered in the report and any additional considerations for improving security posture. |
Clarity and Precision
When writing your report, ensure that your language is clear and precise. Avoid jargon and overly technical terms unless necessary, and always provide definitions when using complex terminology. A good report should be easily understandable by readers of varying technical expertise. Additionally, make sure your findings are backed by evidence, such as screenshots or logs, to support your claims and provide transparency in your analysis.
Following these best practices for writing security reports will help you deliver high-quality documentation that is both informative and actionable for your clients or organization.
Handling Stress and Pressure
Dealing with high-pressure situations is a crucial skill, especially when facing complex tasks with tight deadlines. Stress can significantly impact performance if not managed effectively, leading to mistakes or burnout. The key to overcoming pressure lies in developing strategies that help maintain focus, reduce anxiety, and stay productive under demanding circumstances. With the right mindset and techniques, you can turn stress into a motivating force rather than a hindrance.
Time Management and Prioritization
One of the most effective ways to manage stress is through time management. By organizing your tasks and setting clear priorities, you can avoid feeling overwhelmed. Breaking down large tasks into smaller, manageable steps helps you stay on track and reduces the feeling of being swamped. Prioritize tasks based on urgency and importance, and focus on completing them one at a time to maintain clarity and control.
- Create a schedule: Plan your day and allocate time for each task, ensuring you know exactly what needs to be done at every stage.
- Set realistic goals: Avoid overloading yourself. Be mindful of the time and resources available before committing to additional tasks.
- Take breaks: Short breaks throughout the day can help clear your mind and restore energy, reducing stress and improving concentration.
Mindset and Stress Management Techniques
Another powerful tool for managing pressure is cultivating a positive mindset. Developing resilience and staying calm in stressful situations can significantly enhance your ability to perform. Several techniques can help you manage stress effectively:
- Breathing exercises: Deep breathing techniques can help reduce anxiety and clear your mind, improving focus and calming the nervous system.
- Visualization: Picture yourself succeeding in the task at hand. This can help increase confidence and reduce feelings of fear or inadequacy.
- Positive self-talk: Replace negative thoughts with positive affirmations to boost morale and remind yourself of your abilities.
By integrating these strategies into your routine, you can build resilience, reduce stress, and enhance your performance in high-pressure situations.
How to Approach OSCP Challenges
Successfully tackling security challenges requires a methodical and strategic approach. The key to overcoming difficult problems lies in careful preparation, logical thinking, and a solid understanding of the tools and techniques at your disposal. By developing a clear plan and remaining calm under pressure, you can efficiently navigate complex tasks and achieve your objectives.
Step-by-Step Methodology
Approaching security challenges requires breaking down the task into manageable steps. The following table outlines a general framework for tackling these types of challenges:
| Step | Description |
|---|---|
| Preparation | Before starting, gather all necessary tools and resources. Familiarize yourself with the environment and the objectives, ensuring you’re fully equipped for the task ahead. |
| Reconnaissance | Begin by gathering information about the target. This can involve network scanning, port enumeration, and service discovery to map out potential attack surfaces. |
| Exploitation | Identify weaknesses and try to exploit them. Use the knowledge gained in the reconnaissance phase to launch attacks, such as exploiting vulnerabilities in the system. |
| Privilege Escalation | If initial access is gained, the next step is to escalate privileges to gain full control over the system. This may involve exploiting local vulnerabilities or misconfigurations. |
| Post-Exploitation | Once you have elevated your privileges, gather as much information as possible to further your objectives, whether it’s capturing flags or obtaining system data. |
| Reporting | Document your findings, including any vulnerabilities discovered and how they were exploited. Provide clear recommendations for mitigating the issues identified during the process. |
Key Tools and Techniques
Understanding the right tools and techniques is essential for success. Below are some of the most commonly used tools and methods that can help you approach challenges more effectively:
- Nmap: A powerful tool for network scanning and enumeration, helping you identify open ports and potential vulnerabilities in the target system.
- Netcat: A versatile tool for creating reverse shells and transferring data, often used in post-exploitation phases.
- Metasploit: A framework for testing and exploiting vulnerabilities, which can help automate attacks and simplify the exploitation process.
- Privilege Escalation Scripts: Automated scripts that search for misconfigurations and vulnerabilities that can be leveraged for privilege escalation.
By following a structured approach and utilizing the right tools, you can systematically tackle and overcome the challenges presented, improving both your skill set and confidence in the process.
Managing Exam Resources Effectively
One of the keys to success during high-pressure challenges is the efficient management of available resources. Whether it’s time, tools, or knowledge, effective resource management can significantly influence your performance. By planning ahead and prioritizing your assets, you can maximize your chances of completing tasks successfully and within the given timeframe.
Time Allocation and Prioritization
Time is often the most critical resource during any testing scenario. Allocating your time wisely ensures that you can cover all areas while still having time to troubleshoot issues that may arise. Here are some strategies to help you manage your time efficiently:
- Break Down Tasks: Divide larger tasks into smaller, manageable chunks. This will allow you to stay focused and track your progress more easily.
- Set Time Limits: Assign a specific amount of time to each task and stick to it. If you can’t solve an issue in the allocated time, move on and return to it later.
- Focus on High-Priority Areas: Identify which parts of the challenge are most critical or carry the most weight. Prioritize these tasks to ensure they are completed first.
Tools and Resources Optimization
Another important aspect of resource management is ensuring that you’re using the right tools and resources for each task. Here are some ways to optimize your tools:
- Organize Your Toolkit: Have your tools readily accessible and organized for quick use. Familiarize yourself with their functions and features beforehand to avoid wasting time during the challenge.
- Leverage Documentation: Make use of online documentation, cheat sheets, and previous research. Having a reference guide can save time when you need to troubleshoot or implement a specific technique.
- Test in Virtual Environments: If possible, practice using your tools in a controlled, virtual setting before the challenge. This allows you to understand their full potential and limitations.
By allocating your time wisely, using the right resources, and staying organized, you can effectively manage the tools and materials at your disposal, giving you a better chance of success in any scenario.
Understanding Exploits and Vulnerabilities
In the world of cybersecurity, identifying and exploiting weaknesses in a system is fundamental to assessing its security. Understanding how vulnerabilities are discovered, exploited, and mitigated is crucial for any professional aiming to enhance their skills. These weaknesses can be anything from coding errors to configuration issues, and once exploited, they can lead to unauthorized access or damage to systems.
What Are Vulnerabilities?

A vulnerability is any flaw or weakness within a system that can be exploited by an attacker to gain unauthorized access or cause harm. These vulnerabilities can exist in software, hardware, or network configurations and often arise from human error, outdated systems, or flawed designs. Here are common types of vulnerabilities:
- Software Bugs: Coding errors that allow attackers to exploit a flaw in the system’s operation.
- Misconfigurations: Incorrectly set system settings that make a system more susceptible to attacks.
- Unpatched Software: Failure to apply security updates leaves known weaknesses unaddressed, making systems vulnerable to exploitation.
- Weak Authentication: Poor password policies or authentication mechanisms that attackers can bypass easily.
How Exploits Work
An exploit is a tool or technique used by attackers to take advantage of a vulnerability. By understanding how exploits work, professionals can better protect systems and respond to potential threats. The process typically involves:
- Reconnaissance: Gathering information about the target system, including its software versions, open ports, and potential vulnerabilities.
- Exploitation: Using a specific attack method to exploit the discovered vulnerability, such as executing malicious code or gaining unauthorized access.
- Post-Exploitation: Once access is gained, attackers often maintain control or extract sensitive data before covering their tracks.
By understanding the relationship between vulnerabilities and exploits, professionals can better defend against attacks by identifying weaknesses and applying appropriate countermeasures. Regular security audits, vulnerability assessments, and the use of updated tools are essential steps in securing any environment.
How to Decode Exam Scenarios

When faced with complex challenges in a cybersecurity assessment, it is crucial to develop the ability to decode and analyze the scenario presented. These scenarios are carefully designed to assess a wide range of skills, from identifying vulnerabilities to exploiting and escalating privileges. Being able to break down these situations methodically can help you approach each task with clarity and precision, ultimately leading to a more successful outcome.
Identify Key Components

Each scenario typically contains several critical components that will guide your actions throughout the assessment. The first step in decoding any scenario is identifying these components:
- Target System Information: Look for details such as the operating system, open ports, and any specific services or applications that might be involved in the task.
- Vulnerability Clues: Pay attention to any hints or indicators about potential weaknesses in the system, such as outdated software, misconfigurations, or poor security practices.
- Task Objectives: Understand the end goal. Whether it’s gaining root access or exfiltrating a specific file, knowing what’s expected of you helps direct your efforts.
Strategize Your Approach
Once you have identified the key components, it’s essential to strategize your approach. This involves organizing your actions in a logical sequence and considering different methods to exploit the identified vulnerabilities. Common techniques include:
- Information Gathering: Start by collecting as much information as possible about the system using tools like Nmap or Netcat. Understanding the network and services is essential for identifying possible attack vectors.
- Vulnerability Scanning: Use automated tools like Nessus or OpenVAS to scan for known vulnerabilities. This can quickly reveal exploitable flaws.
- Exploitation: Once weaknesses are identified, determine the appropriate exploits. This might involve using publicly available exploits or crafting your own tailored approach.
By breaking down the scenario and applying a structured approach, you can more effectively navigate the challenges presented. Remember, thorough preparation and practice are key to mastering this skill and succeeding in any cybersecurity assessment.
Post-Assessment Review and Reflection
After completing a rigorous cybersecurity challenge, it’s crucial to take time for review and reflection. This phase allows you to assess your performance, understand areas where you succeeded, and identify opportunities for improvement. By critically evaluating your approach and results, you can sharpen your skills and refine your strategies for future assessments.
Analyze Your Performance
Once the challenge is over, it’s essential to conduct a detailed analysis of your performance. Reflect on the following points:
- Time Management: Did you allocate enough time to each task? Were you able to complete all the objectives within the given timeframe? If not, consider how better planning could have helped.
- Technical Skills: How well did you handle the technical aspects of the task? Were there any tools or techniques that you could have used more effectively?
- Problem-Solving Approach: Did you follow a logical, step-by-step method to solve problems, or did you get stuck in certain areas? Reflecting on your approach can highlight areas where you may need more practice.
Identify Areas for Improvement
Reflection should also focus on identifying gaps in knowledge or skills. Here are some key areas to consider:
- Knowledge Gaps: Were there specific vulnerabilities or attack methods you struggled with? Make a list of these topics and study them more thoroughly.
- Tool Proficiency: Did you encounter any tools you were not comfortable with? Consider dedicating time to mastering these tools for next time.
- Stress Management: Did the pressure affect your performance? If so, practicing stress-reduction techniques, like time blocking or taking short breaks, could be beneficial in the future.
By engaging in a thorough post-assessment review, you not only reinforce the lessons learned during the challenge but also enhance your overall capabilities for future endeavors. Continuous reflection and improvement are key to advancing in the field of cybersecurity.
Next Steps After Passing the Assessment
Successfully completing a challenging cybersecurity assessment marks a significant milestone in your professional journey. However, passing the test is just the beginning of a new chapter. Once you have achieved this goal, it is important to focus on how to leverage this accomplishment for continued growth and development. This phase involves consolidating your knowledge, expanding your skillset, and applying your expertise in real-world scenarios.
Enhance Your Skills and Knowledge
After passing the assessment, it is essential to keep your skills up to date. Cybersecurity is a constantly evolving field, and staying ahead requires continuous learning. Here are a few ways to further strengthen your abilities:
- Explore Advanced Topics: Take on more advanced topics such as advanced penetration testing, threat hunting, or reverse engineering. Deepen your knowledge of specialized areas that align with your career goals.
- Earn Additional Certifications: While the accomplishment is significant, there are other certifications that can complement your current achievement. Consider pursuing other industry-recognized certifications to enhance your credentials.
- Attend Training and Conferences: Participate in workshops, webinars, and cybersecurity conferences. Networking with professionals and learning from experts can provide valuable insights and opportunities.
Apply Knowledge in Real-World Scenarios

The real test of your skills lies in applying them in practical, real-world situations. Now that you have mastered the foundational concepts, it’s time to challenge yourself further:
- Engage in Capture the Flag (CTF) Competitions: Participating in CTF events is a great way to keep your skills sharp and test them in a competitive environment. These challenges provide hands-on experience and encourage creative problem-solving.
- Contribute to Open-Source Projects: Collaborating on open-source cybersecurity tools or projects allows you to refine your skills while giving back to the community. It also enhances your portfolio and builds your professional network.
- Seek Practical Experience: Whether through internships, freelance work, or full-time employment, gaining hands-on experience in penetration testing and security operations will help you grow as a professional.
By taking the next steps after passing your assessment, you continue to build on your success and move closer to becoming an expert in the cybersecurity field. The journey doesn’t end here–it’s an ongoing process of learning, applying, and evolving.