In this section, we will explore the essential steps and techniques required to successfully complete a networking exercise that challenges your skills in configuring devices and solving common connectivity issues. The task involves setting up a network environment, configuring various devices, and applying your knowledge to ensure everything operates smoothly. As you progress through the exercise, you’ll encounter multiple scenarios that test your understanding of network principles and troubleshooting methods.
Mastering the process requires attention to detail and a solid grasp of key concepts such as IP addressing, routing protocols, and device configuration. You’ll learn how to navigate through a simulated network setup, identify problems, and apply solutions efficiently. This guide will help you build the necessary skills to approach similar challenges in real-world network management tasks, ensuring your ability to troubleshoot and optimize network performance effectively.
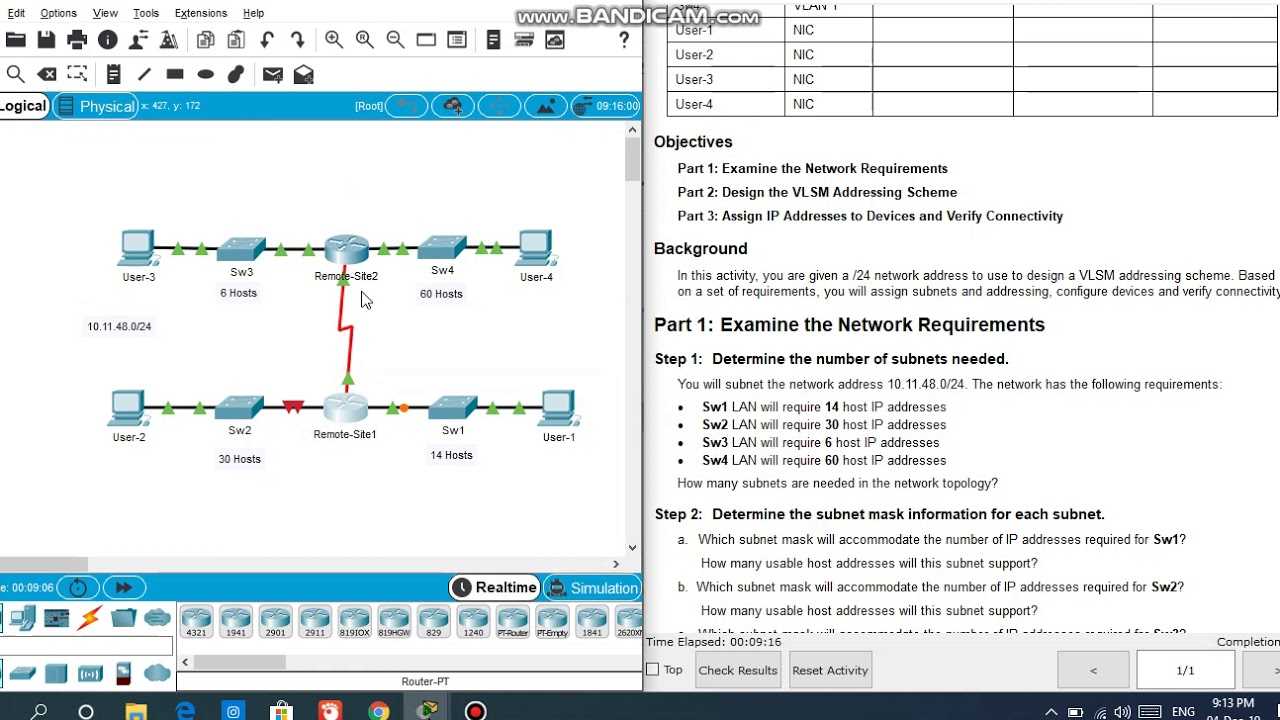
4 Network Configuration Answer Overview
This section focuses on providing a comprehensive overview of the solution to a complex network simulation challenge. The task involves configuring and testing various devices within a simulated environment, requiring a thorough understanding of network fundamentals. You will be guided through the steps necessary to ensure each component communicates effectively and operates as expected. A strong grasp of network principles is essential to identify and resolve potential issues that may arise during the setup process.
Key Steps in Completing the Task
To successfully complete this exercise, you must carefully configure devices, set appropriate IP addresses, and apply routing protocols. Each step must be verified to ensure the network functions properly, with all devices able to communicate. Troubleshooting may be required if issues emerge, such as incorrect configurations or unresponsive devices.
Common Challenges and Solutions
As with any complex network setup, several common obstacles may arise, including configuration errors, connectivity issues, or routing misconfigurations. Understanding how to address these problems efficiently is crucial. Verification of each step is key to preventing issues from escalating and ensuring smooth operation of the entire network.
Understanding the Exercise
The exercise challenges your ability to configure and troubleshoot a simulated network environment. It involves setting up multiple devices, establishing connections, and ensuring the network operates as intended. Each stage requires a combination of theoretical knowledge and practical application, focusing on key networking concepts such as IP addressing, routing protocols, and device management.
By completing this task, you will gain hands-on experience in diagnosing and resolving common network issues. Understanding the purpose of each device and how they interact within the network is crucial to success. Proper configuration and verification of each component will ensure seamless communication across the entire setup, while troubleshooting techniques help identify and fix problems that may arise during the process.
Key Concepts in Network Simulation
In network simulation, understanding key concepts is essential to successfully configuring and managing network environments. The process involves various stages, including device setup, IP addressing, and communication protocols. Mastering these foundational elements allows you to design efficient and reliable networks that operate seamlessly.
Some of the critical concepts include network topology, which defines the layout of connected devices, and routing, which determines how data travels across the network. Configuring switches, routers, and endpoints correctly ensures that each device interacts as expected. Additionally, troubleshooting methods, such as ping tests and examining routing tables, help identify and resolve issues effectively within the simulated environment.
Step-by-Step Guide for Completion
To successfully complete the network simulation task, follow these steps to ensure proper configuration and functionality. Each stage of the process is critical to achieving the desired outcome, from setting up devices to verifying connectivity. Below is a structured guide to help you navigate through the exercise efficiently.
- Set up the devices: Begin by placing all required devices on the simulation workspace. This includes routers, switches, and endpoints like computers or servers.
- Configure IP addresses: Assign appropriate IP addresses to each device according to the network design. Ensure that subnetting is correct for communication between devices.
- Apply routing protocols: Set up routing protocols to enable data transfer between devices. This may involve configuring static routes or dynamic routing protocols like RIP or OSPF.
- Establish connections: Use the appropriate cables to connect the devices, ensuring that physical connections match the required network topology.
- Verify configuration: Once all configurations are in place, verify that devices can communicate with each other by running basic tests like ping or traceroute.
- Troubleshoot issues: If there are any connectivity problems, check for common configuration mistakes such as incorrect IP addresses, faulty cabling, or misconfigured routing protocols.
- Document your setup: Record the settings, IP addresses, and any relevant troubleshooting steps to ensure your work is well-documented and reproducible.
By following these steps, you will be able to set up and verify your network configuration successfully. Each stage builds upon the previous one, so make sure to carefully check your work to avoid any issues later in the process.
Common Mistakes and Solutions
While configuring and troubleshooting network environments, several common mistakes can hinder progress and lead to connectivity issues. Recognizing these errors early on can save time and prevent frustration. In this section, we’ll cover some frequent problems and provide solutions to resolve them effectively.
One common mistake is improper IP addressing, where devices are assigned incorrect IPs or are placed in the wrong subnet. This can prevent devices from communicating with each other. The solution is to carefully verify the subnet mask and ensure that all devices are in the same network range if they need to communicate directly. Double-checking the gateway settings can also help resolve connectivity issues between different network segments.
Another frequent issue arises from misconfigured routing protocols. If routing is not properly set up, data packets may not find the correct path to their destination. This can be resolved by ensuring that routing tables are correctly updated and that any static routes are configured properly. Additionally, if dynamic routing protocols are used, make sure that the correct protocol (e.g., RIP, OSPF) is enabled and that all routers are using compatible settings.
Connectivity issues can also stem from physical layer mistakes, such as using the wrong type of cable or incorrect port connections. This problem can usually be fixed by reviewing the topology and ensuring that all connections match the design. For example, using a crossover cable instead of a straight-through cable can cause communication issues between certain devices.
By identifying and addressing these common mistakes, you can ensure smoother configuration and troubleshooting of network environments. Regularly reviewing and testing each step of the process will help prevent errors from compounding and affecting the overall setup.
How to Analyze Network Configurations
Analyzing network configurations is a critical skill for ensuring that all devices within a network communicate properly and effectively. Proper analysis helps identify potential issues and optimize the performance of the network. By reviewing settings such as IP addressing, routing protocols, and device connections, you can ensure a smooth and reliable network setup. Below are the key steps and methods for analyzing configurations.
One of the most effective ways to analyze a network is by checking the device configurations and their interactions. Start by reviewing the IP addresses assigned to each device to ensure they fall within the correct subnet and range. Additionally, verify that all required services, such as DHCP or DNS, are properly configured on relevant devices.
| Device | Configuration Check | Potential Issue | Solution |
|---|---|---|---|
| Router | IP Address and Routing Table | Incorrect IP or missing routes | Check routing protocol settings and verify IP addressing |
| Switch | VLAN Configuration | VLAN mismatch | Ensure correct VLAN assignments on switch ports |
| End Devices | DHCP Settings | IP Address conflicts or no address | Verify DHCP server configuration and static IP assignments |
Another essential aspect is reviewing the routing protocols configured across the network. Ensure that the correct routing protocols are enabled and that they are compatible with each device in the network. Misconfigured routing tables can result in poor data transmission or loss of connectivity. Use network simulation tools to run tests, such as ping or traceroute, to verify the network’s operational status and identify any areas that need attention.
By systematically analyzing each device’s configuration and ensuring that the network settings align with the intended design, you can effectively diagnose and resolve any issues, ultimately improving network efficiency and performance.
Network Simulation Tools You Need
To effectively design and troubleshoot network environments, having access to the right tools is essential. These tools allow you to simulate devices, configure settings, and test network behavior in a controlled virtual environment. Understanding how to use these tools will help you diagnose problems, verify configurations, and ensure your network operates as intended. Below are some of the most important tools you need when working on network simulations.
Device Configuration Tools
One of the key aspects of network setup is configuring devices like routers, switches, and computers. The configuration interface typically includes command-line or graphical tools that allow you to input settings, such as IP addresses, routing protocols, and security configurations. These tools enable you to directly modify the settings of network devices, ensuring they meet the requirements of your network design. Accessing these interfaces lets you fine-tune your network setup and troubleshoot any issues that may arise during the process.
Testing and Diagnostic Tools
Once your network is set up, testing and diagnostic tools are crucial for verifying connectivity and identifying potential problems. Common tools include:
- Ping – This tool tests the basic connectivity between devices on the network, helping you ensure that devices can communicate with one another.
- Traceroute – Traceroute helps map the path that data packets take through the network, showing where delays or failures may occur.
- Simulation Mode – This allows you to see how data moves through your network in real-time, providing insights into the performance and efficiency of the configuration.
By utilizing these tools, you can optimize your network setup and resolve any issues more efficiently, ensuring smooth and reliable network performance.
Setting Up the Network Topology
Establishing a well-structured network topology is the foundation for any successful network design. The topology defines how devices are connected, where they interact, and how data flows throughout the network. By carefully planning and setting up the network layout, you can ensure that each device functions optimally and that the overall performance is reliable. Proper topology setup helps in maintaining scalability, fault tolerance, and efficient data routing.
The first step in setting up the network topology is choosing the appropriate layout for the network’s needs. There are various options, such as star, bus, mesh, and ring topologies, each offering its own advantages depending on the size and complexity of the network. Once the layout is selected, devices like switches, routers, and endpoints (such as computers or servers) need to be placed accordingly.
Next, connect the devices using the proper cables. Depending on the devices involved, you may use different types of cables, such as Ethernet cables for wired connections or fiber-optic cables for high-speed links. Ensuring correct physical connections is crucial to prevent any interruptions in communication. After the devices are connected, configure the devices to communicate with each other, ensuring that each one is assigned the correct IP address and subnet settings.
Finally, it’s important to verify the topology setup by testing connectivity between devices. This can be done using tools like ping or by checking routing tables. By following these steps, you can establish a functional and well-organized network topology that facilitates efficient data transfer and supports seamless communication between devices.
Configuring Devices in Network Simulations
Configuring network devices is a crucial step in setting up any network environment. This process involves assigning the correct settings to each device so they can communicate with each other and function properly within the network. By adjusting the configurations of routers, switches, and end devices, you ensure the network operates smoothly and efficiently. This section will guide you through the essential steps for configuring devices in a simulated network environment.
Basic Configuration Steps
The first task when configuring a device is to assign an IP address that fits within the network’s range. For routers, you also need to configure interfaces, including their IP addresses and any routing protocols. For switches, configuration mainly involves setting up VLANs, ensuring each port is assigned to the correct VLAN for proper communication.
| Device | Configuration Task | Explanation |
|---|---|---|
| Router | Assign IP addresses to interfaces | Each router interface must be configured with a valid IP address to facilitate communication between networks. |
| Switch | Set VLANs on switch ports | VLANs help segment the network and isolate traffic, improving performance and security. |
| PC/Server | Assign Static IP or Enable DHCP | End devices need a proper IP address, either through DHCP or static configuration, to communicate with the network. |
Advanced Configuration Tips
For more complex setups, you may need to configure routing protocols (such as RIP, OSPF, or EIGRP) on routers to manage traffic between different network segments. Additionally, configuring NAT (Network Address Translation) allows devices on a private network to communicate with external networks. You may also need to set up security features such as access control lists (ACLs) to restrict traffic flow and improve the network’s safety.
Once all devices are configured, testing and verifying the setup using tools like ping and traceroute will help confirm that the network operates as expected. Troubleshooting and fine-tuning settings can ensure that any potential issues are addressed promptly.
Effective Troubleshooting Tips
When working with networks, troubleshooting is an essential skill that helps identify and resolve issues quickly. Whether it’s a connectivity problem, misconfigured device, or routing issue, effective troubleshooting ensures minimal disruption and restores network functionality. A systematic approach is key to diagnosing and fixing problems efficiently. In this section, we will explore some practical strategies for troubleshooting network configurations and devices.
The first step in troubleshooting is to verify the physical layer. Ensure that all cables are properly connected and that devices are powered on. A simple check of the hardware can often resolve issues that may seem more complex. Once the physical layer is confirmed, move on to the logical layer, where network settings and configurations play a crucial role. Incorrect IP addresses, subnet masks, or VLAN assignments can prevent communication, so always double-check these configurations.
Common Troubleshooting Steps:
- Ping the device: Use the ping command to check connectivity between devices. If the ping fails, it indicates a potential problem with the network path.
- Check the routing table: Ensure that routers have the correct routes to direct traffic between different segments. An incorrect or missing route can block communication.
- Verify IP configurations: Make sure that devices are assigned the proper IP addresses, and check for conflicts in the network range.
- Review logs: Device logs can provide valuable insights into what might be going wrong. Look for error messages or failed attempts to communicate.
By following these steps and using diagnostic tools, you can effectively pinpoint the root cause of network issues. Troubleshooting is often a process of elimination, and a clear methodical approach will save time and effort in resolving problems. Once the issue is identified, make the necessary adjustments and test the network again to ensure it operates smoothly.
Using Simulation Mode for Testing
Simulation mode is a powerful tool that allows you to visualize and test the behavior of network configurations without the need for physical devices. This mode enables you to simulate traffic flow, analyze device interactions, and troubleshoot network problems in a controlled environment. It provides an invaluable method for experimenting with different configurations and scenarios, offering insights into how a network will respond under various conditions.
How Simulation Mode Works
In simulation mode, network traffic is captured and displayed in real time. This helps you track the path of data packets as they travel between devices, providing a clear view of how different components interact. You can monitor the entire network, visualize packet transmission, and pause the simulation to inspect the flow of information at any point. This feature is particularly useful for understanding complex network setups and diagnosing issues that may not be immediately apparent in a live network.
Benefits of Simulation Mode
- Visualization: See how packets move through the network and track their journey step by step.
- Controlled Environment: Test configurations without affecting a live network, ensuring safety and flexibility.
- Troubleshooting: Quickly identify issues such as misconfigured devices or routing errors by monitoring the data flow.
- Testing Scenarios: Simulate different traffic conditions, such as congestion or network failures, to observe the impact on performance.
Simulation mode also allows for precise error detection. You can pause the simulation, examine the state of devices, and determine where packets are being dropped or delayed. This level of detail makes it easier to diagnose problems and test potential solutions before implementing them in a real-world scenario. By leveraging simulation tools, network administrators can optimize configurations, improve efficiency, and ensure that the network functions as intended under various conditions.
How to Verify Your Answer
Once you have configured your network and implemented the necessary settings, it is crucial to verify that everything works as intended. Verification is the process of confirming that your network setup functions correctly, and that all devices communicate as expected. It involves running tests, checking configurations, and validating connections to ensure your configuration is both accurate and effective.
Steps to Verify Your Network Configuration
- Ping Test: Begin by pinging various devices on your network to confirm connectivity. If a ping fails, it usually indicates a misconfiguration or a physical connection issue.
- Check IP Settings: Verify that all devices have the correct IP addresses, subnet masks, and default gateways assigned. Incorrect IP configurations can prevent devices from communicating.
- Use Traceroute: Utilize the traceroute tool to track the path packets take through the network. This can help identify where packets are being delayed or lost.
- Inspect Routing Tables: Ensure that routers have the correct routing entries to facilitate proper data transfer between subnets or different network segments.
- Verify Device Status: Check the status of devices such as switches and routers to ensure that their interfaces are up and running.
Tools for Verification
- Simulation Mode: Use simulation mode to visualize the flow of packets through the network and verify that traffic is being routed correctly.
- Configuration Review: Double-check your device configurations for errors. Even small mistakes, such as incorrect VLAN assignments, can disrupt communication.
- Network Logs: Review device logs for error messages or warnings that might indicate potential issues with the network setup.
Verifying your configuration is an essential step in network management. By following these methods and using the appropriate tools, you can ensure that your network setup is functioning as expected and troubleshoot any problems that arise efficiently.
Optimizing Network Settings
Optimizing network settings involves fine-tuning various components to ensure smooth, efficient communication between devices. By configuring devices correctly and ensuring that the network operates with minimal latency and maximum throughput, network performance can be significantly improved. Proper optimization also helps in reducing network congestion and avoiding unnecessary errors, leading to a more stable and reliable environment.
Key Areas for Optimization
When optimizing network settings, focus on the following critical areas:
| Optimization Area | Impact on Performance | Recommended Actions |
|---|---|---|
| IP Addressing | Ensures proper device communication and reduces conflicts | Assign static IPs for critical devices and configure DHCP for others |
| Subnetting | Improves traffic management and reduces network congestion | Use appropriate subnet masks to divide networks into manageable segments |
| Routing Protocols | Enhances routing efficiency and fault tolerance | Configure dynamic routing protocols such as OSPF or EIGRP |
| Quality of Service (QoS) | Prioritizes traffic for critical applications and reduces delays | Set QoS policies to prioritize voice and video over other traffic types |
| Network Security | Prevents unauthorized access and ensures secure communication | Implement firewalls, access control lists (ACLs), and encryption methods |
Performance Monitoring
After optimizing network settings, it is essential to monitor the network performance regularly. By using network monitoring tools, you can track real-time traffic, identify potential bottlenecks, and ensure that optimization efforts are effective. Some key metrics to focus on include:
- Latency: Measure the time it takes for data to travel from source to destination.
- Throughput: Check the volume of data successfully transmitted over the network.
- Packet Loss: Identify any dropped packets, which can impact performance.
- Bandwidth Utilization: Ensure the network’s bandwidth is not being overused, leading to congestion.
Regular optimization and monitoring help in maintaining an efficient and high-performing network, ensuring that devices communicate seamlessly and network resources are used optimally.
Advanced Techniques for Networking Tasks
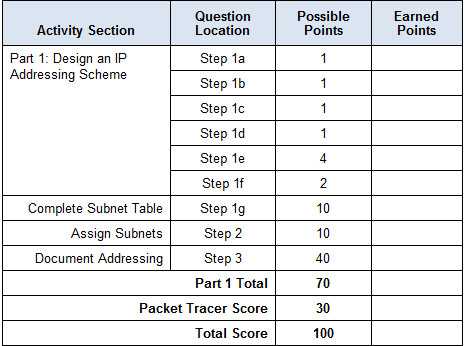
Advanced networking techniques involve utilizing specialized methods to solve complex tasks, improve network performance, and troubleshoot issues that may arise in large-scale systems. These methods require in-depth knowledge of network protocols, devices, and configurations. By mastering these techniques, network professionals can enhance network efficiency, security, and overall reliability.
Key Advanced Networking Techniques
Here are some essential advanced techniques to consider when working on networking tasks:
- VLAN Configuration: Virtual Local Area Networks (VLANs) allow you to logically segment a network into smaller, manageable units. This technique helps reduce broadcast traffic, improves network performance, and enhances security.
- Link Aggregation: By combining multiple network connections into a single logical link, link aggregation improves bandwidth and provides redundancy in case of a link failure. This technique is especially useful in environments with high data traffic.
- Quality of Service (QoS): QoS ensures that critical applications, such as voice or video, receive higher priority over less sensitive data, such as email. This is crucial for minimizing latency and packet loss in real-time communication.
- Network Address Translation (NAT): NAT is used to map private IP addresses to public IP addresses, enabling devices within a private network to access the internet. It also provides a layer of security by hiding internal network addresses from external sources.
- Dynamic Routing Protocols: Protocols like OSPF (Open Shortest Path First) and EIGRP (Enhanced Interior Gateway Routing Protocol) allow for automatic route calculation and network topology adjustments. These protocols are essential for large, complex networks that require fast route convergence and fault tolerance.
- Firewall Configuration: Advanced firewall configurations enable granular control over incoming and outgoing traffic, enhancing network security. Properly configuring firewalls with rules and access control lists (ACLs) can block malicious traffic while allowing legitimate connections.
Tips for Mastering Networking Techniques
To effectively apply advanced networking techniques, consider the following tips:
- Understand Network Topology: A clear understanding of the network’s structure will allow you to design better solutions and troubleshoot problems more effectively.
- Document Configurations: Keep detailed records of network configurations, changes, and settings. This documentation helps in troubleshooting and planning future upgrades.
- Regular Testing: Perform frequent testing and monitoring to ensure that network performance is optimal. Use simulation tools to evaluate the impact of changes before implementing them in a live environment.
- Stay Updated: Networking technologies evolve rapidly. Staying current with new protocols, tools, and best practices ensures your network remains secure and efficient.
By applying these advanced techniques, networking professionals can optimize system performance, increase network resilience, and resolve issues quickly, ensuring smooth operation even in the most demanding environments.
Understanding IP Addressing in Packet Tracer
IP addressing is a fundamental concept in network design, serving as the method by which devices identify each other and communicate across networks. It involves assigning unique numerical identifiers to network devices, ensuring that data is directed to the correct destination. In network simulation environments, mastering IP addressing is essential for ensuring that devices can interact correctly, whether they are within a local network or connected to a larger system.
Key Concepts of IP Addressing
When working with IP addresses, it is important to understand a few core concepts:
- Subnetting: This process involves dividing a larger network into smaller subnetworks. Each subnetwork has its own address range, allowing for more efficient routing and improved security within a network.
- Public vs. Private IPs: Public IP addresses are used on the wider internet, while private IPs are reserved for internal networks. Understanding which type of address to use is crucial for controlling the flow of data and ensuring proper communication within different parts of a network.
- Subnet Masks: A subnet mask defines the portion of an IP address that represents the network versus the portion representing individual devices. It is essential for routing devices to correctly determine the network boundaries.
- Static vs. Dynamic IPs: Static IP addresses are manually assigned and do not change, while dynamic IPs are automatically assigned by a network’s DHCP server and may change over time. Understanding the use cases for each is vital for configuring network devices effectively.
Configuring IP Addresses in a Simulation Environment

When setting up devices within a simulation tool, IP configuration involves several steps to ensure proper network functionality:
- Assigning IPs: Devices must be assigned unique IP addresses within their respective subnets. This ensures that each device can be accurately reached within the network.
- Configuring Subnets: Proper subnetting is key to managing IP addresses. By defining subnet masks and IP ranges, network designers can ensure that communication is efficient and that devices are properly segmented.
- Routing and Communication: Routers are responsible for forwarding data between different subnets. Configuring routes correctly is essential to enable smooth communication between devices on different segments of the network.
By fully understanding and configuring IP addressing correctly, network administrators can ensure that devices within a simulated environment function as expected, with minimal errors and maximum performance.
Practical Use of Routing Protocols
Routing protocols play a crucial role in ensuring that data packets find the most efficient path from one network to another. In real-world networking, these protocols are used to dynamically share information between routers, allowing them to make routing decisions based on factors like network topology, traffic conditions, and link costs. By implementing the right routing protocols, network administrators can enhance network reliability, scalability, and performance.
Types of Routing Protocols
Routing protocols can be classified into different types based on their functionality and the algorithms they use. Here are some commonly used protocols in network configurations:
- Distance-Vector Protocols: These protocols determine the best path by calculating the “distance” (usually hop count) to reach a destination. Examples include RIP (Routing Information Protocol) and IGRP (Interior Gateway Routing Protocol).
- Link-State Protocols: Unlike distance-vector protocols, link-state protocols maintain a detailed map of the entire network and update their routing tables based on changes to network topology. OSPF (Open Shortest Path First) is one of the most widely used link-state protocols.
- Path-Vector Protocols: These protocols are used in larger networks, typically in inter-domain routing. BGP (Border Gateway Protocol) is the primary example and is essential for routing between different autonomous systems on the internet.
Configuring Routing Protocols
To ensure smooth communication across multiple networks, it’s essential to properly configure routing protocols on routers. The process involves several key steps:
- Enabling the Protocol: The first step is to enable the desired routing protocol on the router. This is usually done by entering a specific configuration mode in the router’s command-line interface.
- Defining Network Statements: After enabling the protocol, it’s necessary to define which networks the router will advertise. This is typically done by entering the network’s IP address range into the router’s configuration.
- Adjusting Timers and Metrics: Most routing protocols allow for tuning various parameters such as routing update intervals, hold-down times, and cost metrics. Fine-tuning these values can optimize the protocol’s performance based on the network’s requirements.
By configuring routing protocols correctly, network engineers can ensure efficient data routing, minimize downtime, and adapt the network as it scales. Proper understanding and practical implementation of these protocols are key to successful network design and operation.
Ensuring Network Security Measures
Network security is a critical aspect of any modern IT infrastructure. To safeguard sensitive data and ensure the integrity of communication, organizations must implement a range of protective measures. These strategies aim to prevent unauthorized access, mitigate potential threats, and provide a robust defense against cyberattacks. A strong network security framework incorporates various tools and techniques to identify vulnerabilities, monitor activity, and respond to potential breaches swiftly.
Key Security Measures to Implement
Several essential security practices are crucial for maintaining a safe network environment. These measures help in reducing the risk of attacks and securing the network from internal and external threats:
- Firewalls: A firewall acts as a barrier between a trusted internal network and untrusted external networks. It monitors and controls incoming and outgoing traffic based on predetermined security rules, helping to block malicious traffic.
- Encryption: Encrypting sensitive data both in transit and at rest ensures that even if intercepted, the data remains unreadable without the proper decryption key. This is vital for protecting confidential information during communication over networks.
- Access Control: Limiting access to network resources based on user roles and permissions helps to reduce the risk of unauthorized access. This can include methods such as password protection, multi-factor authentication, and user-specific access levels.
- Intrusion Detection Systems (IDS): IDS monitor network traffic for signs of suspicious activity and potential threats. By identifying abnormal patterns, these systems can alert administrators to potential security breaches in real time.
Best Practices for Securing Your Network
Beyond implementing security tools, there are several best practices that network administrators should follow to strengthen security measures:
- Regular Software Updates: Keeping software and firmware up to date is essential to patch any known security vulnerabilities. Updates often include critical security fixes that help protect the network from newly discovered threats.
- Network Segmentation: Dividing a network into smaller, isolated segments can limit the spread of potential attacks. Each segment can have its own security measures, making it harder for intruders to access the entire network.
- Employee Awareness Training: Educating employees about network security best practices, such as recognizing phishing emails and avoiding unsafe online behaviors, is a key element in preventing human error-related security breaches.
- Backup and Recovery Plans: Regularly backing up critical data and having a disaster recovery plan in place ensures that in the event of a breach or attack, the organization can quickly restore its systems and minimize downtime.
By implementing these security measures and practices, organizations can better protect their networks from a wide range of cyber threats and ensure the continued availability and integrity of their digital resources.
Resources for Further Learning
Expanding your knowledge in network configuration and troubleshooting is a continuous journey, and there are numerous resources available to help you deepen your understanding of networking concepts. Whether you’re a beginner or looking to refine your skills, these tools and materials offer valuable insights, practical exercises, and in-depth tutorials. Below are several categories of resources to enhance your learning experience:
- Online Courses: Many platforms offer comprehensive courses on networking fundamentals, advanced techniques, and certification preparation. Websites like Udemy, Coursera, and Pluralsight provide structured learning paths with video lectures, quizzes, and hands-on labs.
- Books: A variety of books cater to all levels of network professionals. Titles like CCNA Routing and Switching Study Guide by Todd Lammle and Network Warrior by Gary A. Donahue are excellent resources for both beginners and seasoned experts.
- Forums and Communities: Engaging in online communities such as Reddit, Stack Overflow, and Networking Forum can help you connect with other learners and professionals. These platforms offer a place to ask questions, exchange knowledge, and stay updated on industry trends.
- Simulation Tools: Utilizing network simulation software like GNS3, Cisco Packet Tracer, or Boson NetSim can help you practice real-world scenarios in a controlled environment. These tools provide an opportunity to configure devices, simulate network traffic, and troubleshoot problems without needing physical hardware.
- Certifications: Earning certifications such as the CompTIA Network+, Cisco CCNA, and Juniper JNCIA can help you validate your skills and open up new career opportunities in the networking field. These certifications often provide both theoretical knowledge and hands-on practice.
By leveraging these resources, you can build a strong foundation in networking and stay up-to-date with the latest industry practices. Continuous learning and practice are key to mastering the complexities of networking technologies and achieving success in the field.