Understanding the core concepts of operating systems is essential for anyone looking to pursue a career in IT. This section covers key topics that help build a strong foundation in managing and troubleshooting modern computing environments. It introduces vital principles and practical skills necessary for system administration tasks and equips learners with the tools to efficiently navigate different environments.
One of the most important aspects of this section is familiarizing yourself with essential system operations, from managing files and directories to configuring services. In-depth knowledge of commands and utilities is critical for performing daily tasks with ease. Additionally, grasping fundamental concepts such as file system structure and user management forms the backbone of more advanced topics in system management.
By exploring real-world scenarios and problem-solving techniques, this guide will prepare you to confidently approach practical tasks and apply learned skills effectively. Whether you’re troubleshooting network issues or managing system resources, the skills developed here are vital for success in the field of technology and system support.
NDG Linux Essentials Chapter 2 Exam Answers
Mastering the foundational concepts of system administration is critical for success in the IT field. This section delves into the essential topics covered in the second module of the course, focusing on practical skills required for everyday system tasks. It emphasizes core operations that ensure smooth system management and troubleshooting, offering learners a comprehensive understanding of how to handle common technical challenges effectively.
Through this segment, you’ll become familiar with fundamental tasks such as managing user permissions, navigating file systems, and executing system commands. These skills are pivotal for configuring and maintaining an efficient working environment. Additionally, understanding system processes and the basics of networking will allow you to resolve issues quickly and maintain optimal performance across different platforms.
To excel in this area, it’s crucial to not only recognize key concepts but also to practice applying them in real-world scenarios. With a focus on practical exercises, this section ensures that learners gain hands-on experience that prepares them for further challenges in system management and support roles.
Understanding the Basics of Linux
Getting familiar with the fundamental concepts of operating systems is a key first step in any system administration journey. The ability to navigate and manage computing environments efficiently is essential for anyone looking to succeed in IT. This section focuses on building a strong foundation, introducing critical concepts and providing the knowledge necessary to handle everyday tasks effectively.
Key Components of a System
An essential part of understanding system management is recognizing the core components that make up the operating environment. These components work together to ensure smooth operations and efficient task execution. Key elements include:
- File Systems: The structure that organizes and stores data, making it accessible and manageable.
- Processes: The execution of tasks by the system, including background and foreground operations.
- Permissions: Rules that control access to files, ensuring security and proper management.
Essential System Commands
To interact effectively with the system, it’s important to master a few basic commands that allow users to perform essential tasks. These commands are the building blocks of system administration, enabling you to:
- Navigate: Moving through directories and accessing files using commands like
cd,ls, andpwd. - Manage Files: Creating, modifying, and deleting files with commands such as
touch,cp, andrm. - View Information: Displaying system information, processes, and file contents using
ps,top, andcat.
Mastering these basic skills will significantly improve your ability to manage and troubleshoot system environments, laying the groundwork for more advanced topics in system administration.
Key Concepts in Linux System Administration
Effective system administration requires a deep understanding of key principles and practices that govern how a computing environment operates. This knowledge is vital for maintaining, configuring, and troubleshooting systems. By mastering these core concepts, administrators can ensure smooth performance, security, and reliability across all operations.
The following table highlights some of the most important concepts for anyone working in system management:
| Concept | Description |
|---|---|
| File Permissions | Control access to files and directories, ensuring that only authorized users can read, write, or execute certain files. |
| Process Management | Handling running tasks and processes, including how to start, stop, and monitor them effectively. |
| System Configuration | Adjusting system settings to optimize performance, security, and user experience based on specific needs. |
| Networking | Configuring network interfaces, ensuring proper connectivity, and troubleshooting networking issues. |
| Package Management | Installing, updating, and removing software packages to keep the system up-to-date and secure. |
Familiarity with these concepts is essential for anyone aiming to excel in system administration, as they form the foundation for more advanced tasks and scenarios that may arise during day-to-day operations. Whether managing users, configuring hardware, or ensuring system security, these principles provide the building blocks for effective management and troubleshooting.
Important Commands for Chapter 2 Exam
Mastering the right set of commands is essential for anyone working with a command-line interface. These commands allow system administrators to manage files, processes, users, and other key components efficiently. Understanding and practicing these commands will ensure smooth system operation and provide a solid foundation for more advanced tasks.
Here are some critical commands that every beginner should be familiar with:
- ls – Lists the contents of a directory, showing files and folders within the current directory.
- cd – Changes the current working directory, allowing you to navigate the file system.
- pwd – Prints the current working directory, displaying the full path.
- cp – Copies files or directories from one location to another.
- mv – Moves or renames files and directories.
- rm – Removes files or directories from the system.
- cat – Displays the contents of a file on the screen.
- chmod – Changes the permissions of a file or directory, determining who can read, write, or execute.
- ps – Displays information about running processes, useful for monitoring system performance.
- top – Provides a dynamic view of system processes and their resource usage in real-time.
Being proficient with these commands will greatly improve your ability to navigate and manage systems effectively. They form the backbone of system interaction, enabling quick and efficient task execution on any platform.
File Systems and Permissions Explained
Understanding how data is stored, organized, and accessed within a system is crucial for anyone working in system administration. File systems are responsible for managing how information is stored and retrieved, while permissions control who can access and modify that information. Mastering these concepts ensures that users can interact with data securely and efficiently.
How File Systems Work
A file system organizes data on storage devices, such as hard drives or SSDs, and provides a way to store, retrieve, and manage files. It creates a structured format that makes it easy to locate and work with data, ensuring that users can store files in directories and folders with a clear, logical hierarchy. Key elements of a file system include:
- Directory Structure: The organization of files into directories (folders) that allow easy navigation and access.
- Inodes: Data structures that store information about files, such as ownership, permissions, and location on the disk.
- Mount Points: Locations where file systems are attached to the main operating environment, making external storage accessible.
Understanding File Permissions
Permissions determine who can access, modify, or execute a file or directory. These rules are essential for system security, preventing unauthorized users from accessing sensitive information. Each file and directory is associated with a set of permissions that control access for different types of users:
- Read (r): Allows the user to view the contents of a file or list the contents of a directory.
- Write (w): Allows the user to modify or delete the contents of a file or add/remove files from a directory.
- Execute (x): Grants the ability to run a file as a program or enter a directory.
These permissions are typically assigned to three types of users: the file’s owner, the group to which the owner belongs, and all other users. Administrators use commands such as chmod to modify these permissions and ensure that each user has the appropriate level of access.
Networking Essentials for Linux Users
Networking is a critical component for any system administrator, as it enables communication between devices and systems. Whether you’re setting up servers, connecting to remote machines, or troubleshooting network issues, understanding the fundamentals of network configuration is essential. This section covers the basic networking concepts and tools needed to manage and configure network settings effectively.
Key Networking Concepts
Before diving into configuration and troubleshooting, it’s important to understand some basic networking concepts:
- IP Addresses: A unique identifier assigned to each device on a network, allowing it to communicate with other devices.
- Subnetting: The process of dividing a network into smaller sub-networks to improve performance and security.
- DNS (Domain Name System): A system that translates human-readable domain names (like example.com) into IP addresses.
- Routing: The process of forwarding data between devices on different networks based on IP addresses.
Basic Networking Commands
Several commands are essential for managing and troubleshooting network settings. These tools allow users to inspect configurations, diagnose issues, and make necessary changes to network connections. Some key commands include:
- ifconfig – Displays or configures network interface parameters, such as IP address and netmask.
- ping – Tests connectivity between devices on a network, helping to identify whether a device is reachable.
- netstat – Shows network connections, routing tables, and interface statistics.
- traceroute – Traces the path data takes across a network, useful for diagnosing routing issues.
- nslookup – Queries DNS to find the IP address associated with a domain name.
Familiarity with these commands and concepts will help users configure, troubleshoot, and maintain network connections effectively. Whether you’re working with local networks or connecting to remote servers, these skills form the foundation of a reliable network setup.
Understanding Linux Process Management

Process management is a critical aspect of system administration, as it governs the execution of tasks and applications on a machine. Efficiently managing processes ensures that the system runs smoothly, optimizes resource usage, and prevents performance degradation. This section covers the fundamentals of how processes are handled, monitored, and controlled within the system.
What is a Process?
A process refers to an instance of a program that is running in memory. Each process is assigned a unique identifier known as a Process ID (PID), and it can interact with the system’s resources like CPU time, memory, and input/output devices. Processes can be either running, sleeping, stopped, or terminated, depending on their state and the system’s needs. Here are some key concepts related to processes:
- Parent and Child Processes: When a process creates another process, the original is called the parent, and the new one is the child.
- Foreground and Background Processes: Foreground processes require user interaction, while background processes run without direct user input.
- Zombie Processes: Processes that have completed execution but still remain in the process table, consuming system resources.
Managing Processes
Effective process management requires tools that help users track and control running processes. Key commands for managing processes include:
- ps – Displays a list of running processes, showing their PID and resource usage.
- top – Provides a real-time view of active processes and their CPU and memory usage.
- kill – Terminates a process using its PID, useful for stopping unresponsive tasks.
- bg – Resumes a paused process in the background, allowing users to continue other tasks.
- fg – Brings a background process to the foreground, resuming user interaction with it.
By understanding and utilizing these tools and concepts, system administrators can efficiently manage running tasks, ensuring optimal performance and troubleshooting any issues that arise with processes.
Common Troubleshooting Techniques
When managing systems, problems inevitably arise that need quick and effective resolution. Troubleshooting is the process of diagnosing and resolving issues to maintain system stability and performance. Understanding the tools and methods for troubleshooting is crucial for any administrator to keep a system running smoothly.
Identifying System Issues
The first step in troubleshooting is to identify the root cause of the problem. This often involves looking at system logs, monitoring performance, and checking system status. Key tools and techniques to identify problems include:
- System Logs: Logs are essential for identifying errors, warnings, and other events that could indicate a problem. Common log files include
/var/log/syslogand/var/log/messages. - Resource Monitoring: Monitoring tools like
top,htop, andfreecan provide insight into system resources, such as CPU, memory, and disk usage. - Ping and Traceroute: Use
pingto test network connectivity andtracerouteto trace the path data takes through the network, helping identify connection issues.
Resolving Common Issues
Once you’ve identified the source of a problem, resolving it involves applying the appropriate fixes. Some common system issues and their solutions include:
- High CPU Usage: If a process is consuming excessive CPU resources, you can use the
killcommand to stop the offending process or investigate further withtopto determine which process is causing the issue. - Disk Space Shortages: Use the
dfcommand to check available disk space, andduto locate large files. Removing unnecessary files or expanding disk space can help resolve this issue. - Network Connectivity Issues: If a machine cannot reach the network, ensure that the correct network interface is up using
ifconfigand check routing configurations withroute.
By regularly using these troubleshooting tools and techniques, administrators can efficiently identify and address issues, keeping systems stable and minimizing downtime.
Preparing for Linux Essentials Chapter 2
Getting ready for the next level of system management involves mastering core concepts, acquiring practical skills, and familiarizing yourself with key tools. Preparation for this stage requires an understanding of the tasks you’ll face, as well as how to efficiently use the right commands and troubleshoot common problems. This section will guide you through the essential elements to focus on as you prepare for a deeper understanding of system administration.
Key Areas to Focus On
Familiarizing yourself with the following areas will be crucial to success:
- System Configuration: Understanding how to configure and manage system files, user accounts, and permissions.
- Networking Basics: Knowing how to manage network interfaces, test connectivity, and configure IP addresses.
- Process Management: Learning how to monitor and manage running tasks, including starting, stopping, and troubleshooting processes.
Essential Commands and Tools
Knowing which commands to use is key for efficient system management. Below is a table that summarizes some important commands and their functions:
| Command | Function |
|---|---|
ps |
Displays the list of running processes on the system. |
ifconfig |
Shows or configures network interface parameters, such as IP addresses. |
top |
Displays real-time information about the system’s resource usage, including CPU and memory usage. |
ping |
Tests network connectivity to another machine. |
df |
Displays disk space usage for all mounted file systems. |
By practicing these commands and understanding their functionalities, you’ll be better equipped to manage and troubleshoot systems efficiently. Combining theoretical knowledge with hands-on experience will ensure that you’re well-prepared for upcoming tasks and challenges in system administration.
How to Use the Command Line
The command line is an essential tool for managing and navigating systems efficiently. By using text-based commands, administrators can interact directly with the operating system, automate tasks, and perform complex configurations. Mastery of this interface allows you to take full control over system processes, file management, and network configurations. In this section, we will explore the basic commands and techniques that will help you effectively navigate and utilize the command line.
Basic Command Syntax
Understanding the structure of commands is crucial for effective use. Most commands follow a simple syntax:
- Command: The action you want to perform (e.g.,
lsto list files). - Options: Flags or switches that modify the behavior of the command (e.g.,
-lfor a detailed list of files). - Arguments: The files, directories, or other resources the command will act upon (e.g.,
/home/user).
An example of a basic command is:
ls -l /home/userIn this case, ls is the command, -l is the option, and /home/user is the directory.
Essential Command Line Tools
Several commands are essential for everyday tasks. Below are some of the most commonly used commands for navigating and managing your system:
pwd– Prints the current working directory.cd– Changes the current directory.ls– Lists the files and directories in a specific location.cp– Copies files or directories from one location to another.mv– Moves or renames files and directories.rm– Removes files or directories.
Getting comfortable with these commands will provide you with a strong foundation for navigating the system and managing resources directly from the command line interface. The more you practice, the more proficient you will become in using these tools to enhance your workflow and productivity.
Directory Structure Overview
The directory structure of a system is the organization of files and directories that helps to manage resources effectively. It defines where different types of files are located, making it easier for users and administrators to find and organize data. Understanding this structure is crucial for navigating and performing tasks efficiently, such as managing system configurations, user data, and executable files.
Key Directories and Their Functions
Each system follows a hierarchical structure, where directories are nested within one another. The most important directories that you will encounter are as follows:
- / – The root directory, which is the top-level directory containing all other directories.
- /bin – Contains essential command binaries that are required for system boot and recovery.
- /etc – Stores system-wide configuration files for the operating system and installed applications.
- /home – The directory where users’ personal files and directories are stored. Each user typically has a subdirectory under
/home. - /var – Contains variable data such as logs, mail spools, and temporary files that change during the system’s operation.
- /usr – Contains user programs, libraries, and documentation files.
- /tmp – A temporary directory where applications can store files that are needed temporarily during the operation.
Understanding Pathnames

In this structure, pathnames are used to specify the location of a file or directory. A pathname is either absolute or relative:
- Absolute Path: Specifies the location starting from the root directory (e.g.,
/home/user/document.txt). - Relative Path: Refers to a location relative to the current working directory (e.g.,
documents/document.txt).
By understanding the layout of these directories and how to navigate between them, you will be able to efficiently manage files, troubleshoot issues, and perform system maintenance tasks.
Mastering User and Group Management
Effective management of users and groups is a fundamental aspect of maintaining a secure and organized system. By assigning permissions and organizing users into groups, administrators can control access to resources and ensure that the right individuals have the appropriate level of access. Proper user and group management not only simplifies administrative tasks but also strengthens the overall security of the environment.
There are several key tasks involved in managing users and groups, such as creating new accounts, modifying existing ones, assigning passwords, and setting specific access rights. In addition, understanding how to group users based on roles and responsibilities is crucial for streamlined access control and resource management.
Creating and Managing Users
To create and manage user accounts, several commands are used. Some of the most common tasks include:
- useradd – Used to create a new user account. This command allows you to specify details such as the user’s home directory, shell, and group membership.
- usermod – Used to modify an existing user’s account information, such as adding the user to a group or changing their login shell.
- passwd – Used to set or change a user’s password. This is a crucial command for maintaining security on the system.
- userdel – Used to delete a user account and its associated files, if necessary.
Group Management

Groups are collections of users that share common permissions. Managing groups helps simplify the process of granting access to resources. Key group management commands include:
- groupadd – Used to create a new group, allowing you to specify the group name and other settings.
- groupdel – Used to remove a group from the system.
- gpasswd – Allows you to change the password for a group, giving group members the ability to access certain resources or perform specific tasks.
- vigr – Opens the group file in a text editor, enabling you to manage group memberships manually.
By mastering these tools, you will be able to efficiently manage users and groups, ensuring that each individual has the correct permissions and access to system resources.
Filesystem Navigation and File Handling
Understanding how to navigate the filesystem and handle files effectively is essential for managing a system efficiently. By mastering basic file operations and directory navigation, users can quickly access, modify, and organize their data. File management tools enable users to perform tasks such as moving, copying, renaming, and deleting files and directories.
In this section, we’ll explore the commands that are crucial for navigating the file system, managing file permissions, and handling file operations. Knowing these commands is fundamental for any system administrator or user working in a command-line environment.
Navigating the Filesystem
To navigate through directories and locate files, various commands can be used to move between directories, list their contents, and examine file details:
- cd – Changes the current directory. You can navigate to a directory by specifying its path, such as
cd /home/user, or return to the home directory withcd ~. - pwd – Prints the working directory, displaying the full path to the current directory.
- ls – Lists the contents of a directory. With options like
-lfor detailed listing or-ato include hidden files, it provides a versatile way to explore directories. - find – Searches for files and directories within the filesystem based on criteria like name, type, and modification date.
File Operations
Handling files involves a variety of operations, from copying and moving files to changing their names and deleting them. Here are the key commands for managing files:
- cp – Copies files or directories from one location to another. For example,
cp file1.txt /home/user/copies the file to the specified directory. - mv – Moves or renames files and directories. You can move files to a different location or rename them within the same directory. For example,
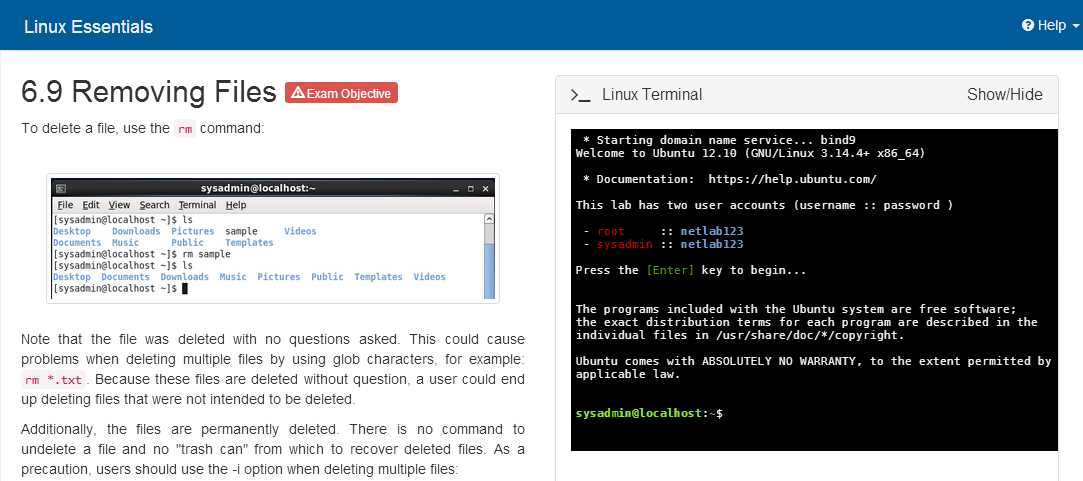
mv file1.txt newfile.txtrenames the file. - rm – Removes files or directories. Be cautious with this command, as it permanently deletes files without asking for confirmation unless used with the
-ioption. - touch – Creates an empty file or updates the timestamp of an existing file. For example,
touch newfile.txtcreates a new file if it doesn’t exist.
These commands form the backbone of filesystem navigation and file management. By becoming proficient in their use, users can effectively manage files, access important data, and organize their system’s contents with ease.
Understanding the Role of Services
In any modern system, various processes run in the background, providing essential functions such as networking, security, and application management. These background processes, known as services, are crucial for the proper functioning of the system. They operate independently of direct user interaction and ensure that the system can perform tasks efficiently without interruption.
Services are designed to manage and facilitate system functions such as file sharing, web hosting, and device management. Understanding how to interact with and manage these services is key for any system administrator or advanced user. In this section, we’ll cover the basics of how services are handled, how to start or stop them, and the tools available to monitor their status.
Common Service Management Commands
Managing services typically involves starting, stopping, or checking the status of services. Here are some of the most commonly used commands:
| Command | Description |
|---|---|
| systemctl start [service] | Starts a specific service, such as systemctl start apache2 to start the Apache web server. |
| systemctl stop [service] | Stops a running service. For example, systemctl stop apache2 stops the Apache web server. |
| systemctl status [service] | Displays the current status of a service, such as whether it is active or inactive. |
| systemctl restart [service] | Restarts a service, which is useful if the service is not functioning properly or if configuration changes need to be applied. |
| systemctl enable [service] | Enables a service to start automatically on boot. For example, systemctl enable apache2 ensures Apache starts automatically after a reboot. |
| systemctl disable [service] | Disables a service from starting automatically on boot. |
Types of Services
Services can be categorized based on their role and functionality. Here are some of the most common types:
- System Services – Essential services that the system needs to function, such as device drivers, network management, and the system clock.
- Application Services – Services that manage specific applications, such as a web server, database server, or mail server.
- Networking Services – These include services related to networking, such as DNS, DHCP, and FTP servers.
- Security Services – Services that manage authentication, firewalls, and system access controls.
Knowing how to control and troubleshoot these services allows you to maintain system stability, optimize performance, and ensure that essential tasks are being executed properly. Services are at the heart of system administration and understanding their role is critical for effective system management.
Practicing with Virtualization Tools
Virtualization tools provide a powerful way to create and manage multiple virtual environments on a single physical machine. These tools enable users to run several isolated systems, each with its own configuration, allowing for testing, development, and learning without affecting the primary system. Practicing with these tools is essential for gaining practical experience in managing virtual machines, troubleshooting, and optimizing resources.
By using virtualization, users can simulate different scenarios, experiment with system configurations, and run multiple operating systems concurrently. This is especially useful for those looking to explore system administration, network management, or software development in a controlled and safe environment. Popular tools like KVM, VirtualBox, and VMware provide the flexibility needed for different use cases, whether you’re testing applications, simulating networks, or learning new system management techniques.
Common Virtualization Tools
Several virtualization tools are widely used in the industry. Here are a few popular options:
- VirtualBox: A free, open-source tool that allows users to run multiple guest operating systems on a single machine. It is widely used for personal and educational purposes due to its ease of use and cross-platform support.
- KVM (Kernel-based Virtual Machine): A virtualization infrastructure built into the Linux kernel, which allows users to run multiple virtual machines on Linux systems. It is highly efficient and commonly used in enterprise environments.
- VMware: A popular commercial virtualization solution used in enterprise environments for creating and managing virtualized servers and desktops. VMware provides advanced features like snapshots, resource management, and high availability.
- Docker: While primarily a containerization tool, Docker allows for lightweight virtualization, enabling users to run isolated applications or services in containers. It is particularly useful for development and deployment purposes.
Getting Started with Virtualization
To get started with virtualization, follow these general steps:
- Install the Tool: Begin by installing the chosen virtualization software. For example, if using VirtualBox, download the installer and follow the on-screen instructions for setup.
- Create a Virtual Machine: Once the tool is installed, you can create a virtual machine (VM). Choose the desired operating system for the VM, allocate necessary resources like CPU, memory, and disk space.
- Install the Guest OS: Start the VM and install the operating system as you would on a physical machine. Follow the installation prompts, and configure the system based on your needs.
- Test and Experiment: With the guest OS installed, you can start experimenting with different system configurations, software installations, or network settings in a risk-free environment.
Mastering virtualization tools is essential for anyone looking to deepen their knowledge of system administration, development, or network management. They allow users to practice and experiment in a controlled setting, giving them the freedom to learn and develop skills without the fear of disrupting a live system.