
As the digital landscape becomes more complex, understanding how to protect information and systems has never been more essential. Building a strong foundation in network security is critical for anyone aiming to pursue a career in technology. Mastery of the core concepts in this field is crucial for both professionals and enthusiasts who want to ensure they are prepared for the challenges ahead.
Preparation is the key to success in any field, and network defense is no exception. By focusing on key principles, practical knowledge, and strategic approaches, individuals can gain the necessary skills to tackle various security challenges. This journey requires a blend of theoretical understanding and hands-on experience, both of which are integral to achieving proficiency in this domain.
Through targeted learning and practice, individuals can enhance their ability to identify vulnerabilities, mitigate risks, and respond effectively to potential threats. These capabilities not only provide a deeper understanding of how to secure networks but also build confidence in navigating complex security scenarios. The following sections will guide you through the necessary steps to prepare effectively and succeed in mastering the key concepts of network protection.
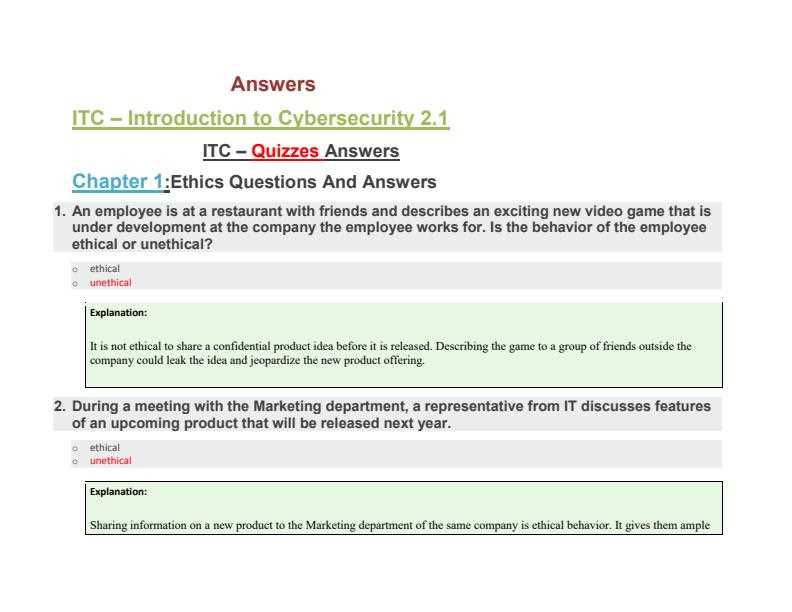
Cisco Final Exam Answers for Cybersecurity
When preparing for any major certification related to network security, it is essential to familiarize yourself with the key topics and challenges that may arise. Mastering the core concepts and strategies will not only help you understand the material better but also give you the confidence to tackle any scenario. This section focuses on providing insights and strategies that are crucial for those seeking to pass the assessment on information protection.
Success in any security certification requires a blend of knowledge and practical experience. Focusing on the most critical concepts and ensuring a deep understanding of essential techniques is fundamental. Through carefully structured study and strategic review, you can effectively prepare for the questions and scenarios that are commonly included in the assessment.
One of the best ways to prepare is by practicing with sample questions and examining the reasoning behind each answer. This method ensures you can apply theoretical knowledge to real-world situations and helps strengthen your problem-solving skills. By focusing on the most frequently covered topics and learning from your mistakes, you can improve your performance and increase your chances of success.
Understanding the Cybersecurity Curriculum

Gaining a comprehensive understanding of network defense principles is essential for anyone pursuing a career in protecting digital assets. The curriculum designed to teach these concepts provides a structured approach, guiding learners through foundational topics and advanced strategies. Whether you are new to the field or looking to expand your knowledge, understanding the curriculum is the first step toward mastering security protocols and risk management.
Key Topics in Network Defense
The curriculum typically covers a broad range of subjects, starting with basic principles and gradually advancing to more complex topics. Key areas of focus include securing systems against common vulnerabilities, understanding encryption methods, and learning to identify and prevent potential threats. Each topic builds upon the previous one, ensuring that learners develop a well-rounded understanding of how to safeguard information in a connected world.
Practical Skills and Application
Beyond theory, the curriculum emphasizes the importance of hands-on practice. Practical exercises and real-world scenarios are incorporated to help learners apply what they’ve learned in a controlled environment. This blend of theory and practice ensures that individuals are not only knowledgeable but also capable of implementing security measures and responding to threats as they arise.
Preparing for Certification Success in Network Security
Successfully preparing for a network defense certification involves more than just memorizing facts; it requires a strategic approach that combines theory with practical skills. A well-rounded study plan ensures that you grasp essential concepts and gain hands-on experience, which will ultimately lead to confidence during the assessment. Understanding what to focus on and how to approach the materials is key to your success.
Key Steps for Effective Preparation
When preparing for a certification in information protection, it is crucial to follow a structured plan that covers all aspects of the learning process. Here are some steps to guide your preparation:
- Review Core Concepts: Familiarize yourself with the foundational topics such as risk management, data protection, and threat detection.
- Practice Hands-On Scenarios: Engaging in practical exercises and lab simulations will help you apply the knowledge in real-world situations.
- Focus on Weak Areas: Identify areas where you are less confident and dedicate extra time to those topics.
- Take Practice Tests: Completing mock tests will help you familiarize yourself with the format and timing of the assessment.
Managing Your Study Time
Effective time management is essential for preparation. Breaking your study schedule into manageable segments and prioritizing topics based on their importance ensures that you can cover all necessary materials without feeling overwhelmed. Consider the following strategies:
- Set Realistic Goals: Establish achievable objectives for each study session.
- Stick to a Schedule: Consistency is key. Create a timetable that includes regular review periods.
- Allow Time for Rest: Don’t overwork yourself–rest is crucial for maintaining focus and productivity.
Common Topics Covered in Network Security Certification
When preparing for a certification in digital protection, understanding the core topics that will be assessed is essential. These subjects lay the foundation for the knowledge required to secure systems, prevent attacks, and safeguard sensitive data. Familiarizing yourself with these areas will help you approach the test with confidence and a clear understanding of the material.
Core Principles of Network Defense
One of the main focuses of any security certification is the understanding of how to defend digital networks and data. Key principles include:
- Risk Management: Identifying, assessing, and mitigating potential risks to an organization’s systems.
- Encryption Techniques: Understanding the importance of protecting data through various encryption methods.
- Firewall Configuration: Learning how to configure firewalls to protect against unauthorized access.
- Access Control: Implementing strategies to control who can access various network resources.
Advanced Security Strategies
In addition to basic protection techniques, advanced methods are crucial for more complex threats. Topics include:
- Intrusion Detection and Prevention: Identifying and stopping unauthorized attempts to access a network.
- Incident Response: Preparing for and responding to security breaches or attacks.
- Malware Analysis: Understanding the different types of malicious software and how to combat them.
- Security Auditing: Regularly reviewing systems for vulnerabilities and ensuring compliance with security standards.
How to Navigate Certification Questions
Successfully tackling assessment questions requires a clear strategy and focused approach. Understanding how to analyze and respond to each question is just as important as knowing the content itself. By familiarizing yourself with question formats and developing effective techniques, you can improve both your accuracy and speed during the test.
One effective method is to carefully read each question before jumping to conclusions. Look for keywords that highlight the main idea and identify what is being asked. Pay attention to specific instructions such as time limits or question types (e.g., multiple-choice or scenario-based questions). This will help you avoid common mistakes and better allocate your time across the test.
Additionally, it’s important to remain calm and methodical, especially with questions that seem complex or unfamiliar. Start by eliminating obviously incorrect answers, then focus on narrowing down the remaining options. Practice this approach with sample questions to build confidence and familiarity with the types of questions you’ll encounter.
Essential Skills for Network Security Certification
To succeed in a certification focused on protecting digital assets and information, certain skills are crucial. These abilities not only help you perform well during the assessment but also ensure you can handle real-world security challenges. A strong foundation in both theoretical knowledge and practical application will set you apart and equip you with the tools needed for effective defense against threats.
Core Competencies to Master
There are several key skills that will directly contribute to your success in this field. These include:
- Risk Assessment: Understanding how to evaluate and prioritize potential vulnerabilities within a system.
- Incident Response: Developing the ability to quickly react to and manage security breaches or attacks.
- Encryption and Decryption: Knowing how to protect sensitive data through various cryptographic techniques.
- Network Monitoring: Being able to track and analyze network traffic to identify unusual patterns or security risks.
- Threat Detection: Mastering the use of tools and techniques to identify malware, phishing attempts, and other malicious activities.
Practical Knowledge and Hands-On Experience

In addition to theoretical knowledge, practical experience is key to building confidence and refining your skills. Hands-on labs, simulations, and scenario-based exercises provide invaluable practice. These allow you to apply concepts in a controlled environment, making it easier to solve complex problems when they arise in real situations.
- Firewall Configuration: Knowing how to set up and maintain firewalls to block unauthorized access.
- Security Auditing: Performing regular checks and assessments to ensure the system is secure and compliant with best practices.
- System Hardening: Learning how to implement security measures that reduce the risk of exploitation.
Tips for Time Management During the Assessment

Effective time management is crucial when taking any test, especially when dealing with complex topics related to information protection. Properly allocating your time ensures you can address all the questions without feeling rushed. Developing strategies to efficiently use the allotted time can significantly improve your performance and reduce stress.
Prioritize and Plan Your Time
Before diving into the test, take a few minutes to review the entire set of questions. This allows you to gauge their difficulty and decide which ones to tackle first. Start by identifying the questions that are easier for you and can be answered quickly, then move on to the more challenging ones. This approach ensures you don’t spend too much time on any one question.
- Scan the Entire Test: Skim through all questions at the start to plan your time efficiently.
- Answer the Easy Questions First: Tackle straightforward questions to build momentum and save time for harder ones.
- Allocate Time for Each Section: Divide your time according to the weight of the sections or questions, ensuring enough time for each.
Avoid Spending Too Much Time on One Question
If you encounter a particularly tough question, it’s easy to get stuck. However, spending too much time on a single question can waste precious minutes. If you’re unsure about an answer, make your best guess, mark it, and move on. You can always come back to it later if time permits.
- Don’t Get Stuck: Move on if a question is taking too long; it’s better to answer the ones you know first.
- Use Time Wisely: Leave a few minutes at the end to review your answers, focusing on marked or uncertain responses.
Understanding Network Protection Frameworks
A robust security framework is essential for creating a solid defense against digital threats and vulnerabilities. A comprehensive framework not only provides guidelines for protecting systems but also helps in identifying potential risks and responding effectively to incidents. By understanding the structure of a leading network protection framework, you can better prepare for challenges in safeguarding critical data and resources.
Core Components of the Framework
Effective network defense frameworks consist of several key elements that work together to establish a secure environment. These components address different aspects of protection and ensure that all layers of the system are covered. The core areas typically include:
- Risk Management: Identifying, assessing, and prioritizing risks to mitigate potential damage.
- Threat Detection: Using tools and techniques to spot suspicious activities or potential intrusions.
- Incident Response: Developing procedures for handling and recovering from security breaches or attacks.
- Security Monitoring: Continuously observing network activity to detect any signs of compromise.
- Data Protection: Implementing encryption and other measures to safeguard sensitive information.
Implementing the Framework in Practice

To apply this framework effectively, security professionals must integrate these components into the daily operations of the organization. This involves not only configuring systems for maximum protection but also establishing proactive policies and training programs for staff. Successful implementation requires a balance of technology, process, and people working together to defend against evolving threats.
- Training and Awareness: Ensure that all team members understand security practices and potential threats.
- Ongoing Risk Assessment: Regularly evaluate and adjust security measures based on emerging risks.
- Automation: Use automated tools to assist in monitoring and threat detection, reducing response time.
Understanding Network Protection Frameworks
A robust security framework is essential for creating a solid defense against digital threats and vulnerabilities. A comprehensive framework not only provides guidelines for protecting systems but also helps in identifying potential risks and responding effectively to incidents. By understanding the structure of a leading network protection framework, you can better prepare for challenges in safeguarding critical data and resources.
Core Components of the Framework
Effective network defense frameworks consist of several key elements that work together to establish a secure environment. These components address different aspects of protection and ensure that all layers of the system are covered. The core areas typically include:
- Risk Management: Identifying, assessing, and prioritizing risks to mitigate potential damage.
- Threat Detection: Using tools and techniques to spot suspicious activities or potential intrusions.
- Incident Response: Developing procedures for handling and recovering from security breaches or attacks.
- Security Monitoring: Continuously observing network activity to detect any signs of compromise.
- Data Protection: Implementing encryption and other measures to safeguard sensitive information.
Implementing the Framework in Practice
To apply this framework effectively, security professionals must integrate these components into the daily operations of the organization. This involves not only configuring systems for maximum protection but also establishing proactive policies and training programs for staff. Successful implementation requires a balance of technology, process, and people working together to defend against evolving threats.
- Training and Awareness: Ensure that all team members understand security practices and potential threats.
- Ongoing Risk Assessment: Regularly evaluate and adjust security measures based on emerging risks.
- Automation: Use automated tools to assist in monitoring and threat detection, reducing response time.
Reviewing Key Security Principles for Assessment
When preparing for any security-related evaluation, it’s essential to focus on the foundational principles that guide secure system design and operation. Understanding these key concepts allows you to approach questions with a structured mindset and apply best practices in real-world scenarios. Mastering these principles not only helps in passing assessments but also builds a strong foundation for future security roles.
Core Security Principles to Understand

The following principles form the backbone of effective security strategies. These principles apply to both the protection of digital information and the management of security risks:
| Principle | Description |
|---|---|
| Confidentiality | Ensuring that information is accessible only to those authorized to view it. |
| Integrity | Maintaining the accuracy and trustworthiness of data during storage, transmission, and processing. |
| Availability | Ensuring that authorized users have access to data and systems when needed. |
| Non-Repudiation | Ensuring that actions or transactions cannot be denied or disputed by their originator. |
| Authentication | Verifying the identity of users and systems before granting access to resources. |
Applying These Principles in Practice

While these principles provide a theoretical framework, they must be applied through practical measures. This includes configuring access controls, monitoring systems for unauthorized activity, and establishing robust encryption practices. Understanding how these principles work in tandem with each other will help ensure that systems remain secure against a wide range of threats.
Common Mistakes to Avoid in the Assessment
When preparing for a test, it’s easy to fall into certain traps that can negatively affect your performance. Recognizing and avoiding these common mistakes will help you approach the assessment more confidently and increase your chances of success. From misinterpreting questions to time management errors, being aware of potential pitfalls is essential for achieving the best results.
Top Mistakes to Avoid
Below are some of the most common errors candidates make during assessments, along with tips for avoiding them:
| Mistake | Why to Avoid | How to Prevent |
|---|---|---|
| Skipping Questions | Skipping questions may lead to missed opportunities and wasted time. | Answer all questions, even if it means coming back to the harder ones later. |
| Overthinking Answers | Overanalyzing questions can cause confusion and delays. | Stick to your first instinct unless you have strong reason to reconsider. |
| Ignoring Instructions | Missing important instructions can result in incorrect answers. | Read all instructions carefully before beginning each section. |
| Panic Under Pressure | Stress can cloud your judgment and slow your decision-making. | Stay calm, breathe deeply, and pace yourself throughout the assessment. |
| Time Mismanagement | Spending too much time on a single question may leave you with insufficient time for others. | Keep track of time and allocate a set duration for each question or section. |
Effective Strategies for Avoiding Mistakes
To perform your best, it’s important to implement effective strategies. Prioritize accuracy over speed, stay organized, and focus on one question at a time. With practice and a clear mindset, you can avoid the common pitfalls that many candidates fall into.
Importance of Practice Tests in Preparation
Engaging with practice assessments is a critical aspect of effective preparation. They not only simulate the real testing environment but also provide valuable insight into your understanding of the material. By practicing regularly, you can identify knowledge gaps, improve your time management, and enhance your confidence before the actual evaluation. These mock tests serve as both a learning tool and a performance benchmark.
Key Benefits of Practice Tests
Here are several reasons why practice tests should be an essential part of your preparation strategy:
- Familiarity with Format: Practice tests mirror the format of the actual evaluation, helping you become comfortable with the structure and types of questions.
- Identifying Weak Areas: They allow you to pinpoint areas where your knowledge may be lacking, enabling targeted review.
- Improved Time Management: By simulating the real testing environment, practice assessments teach you how to pace yourself and manage time effectively during the actual test.
- Reduced Test Anxiety: Repeated practice can build familiarity and reduce nervousness, allowing you to approach the real assessment with more confidence.
Maximizing the Effectiveness of Practice Tests

To get the most out of practice tests, it’s important to treat them seriously. Take them under timed conditions, review your incorrect answers, and understand why they were wrong. By approaching practice tests strategically, you’ll gain a clearer understanding of the material and refine your test-taking techniques.
Strategies to Tackle Multiple-Choice Questions
Multiple-choice questions are a common type of assessment format. They can be challenging due to the variety of answer options, making it easy to second-guess yourself. However, with the right strategies, you can approach these questions with confidence and increase your chances of selecting the correct answer. Understanding the structure and applying effective techniques can help you navigate these questions more effectively.
Effective Techniques for Answering Multiple-Choice Questions

Below are several key strategies that can help you tackle multiple-choice questions efficiently:
| Strategy | Why It Works | How to Apply |
|---|---|---|
| Eliminate Obvious Wrong Answers | By removing answers that are clearly incorrect, you increase your chances of selecting the correct option. | Read each option carefully and cross out answers that are irrelevant or nonsensical. |
| Look for Key Words | Key words in both the question and the answer choices can guide you toward the right answer. | Identify terms such as “always,” “never,” or “best” that can provide clues to the correct response. |
| Use the Process of Elimination | When in doubt, narrowing down the choices can increase your odds of selecting the correct answer. | If you’re unsure, start by eliminating the answers you know are wrong, then focus on the remaining options. |
| Read All Choices Carefully | Sometimes, one answer may seem correct at first glance, but a more accurate answer is available in the options. | Even if the first answer seems right, double-check all choices to ensure you’re selecting the most accurate one. |
| Don’t Overthink | Overthinking can cause unnecessary confusion and make you doubt your initial instinct. | If you’re confident in your first choice, trust your judgment unless you find compelling evidence to change it. |
Additional Tips for Multiple-Choice Success
While the above strategies are helpful, practicing with multiple-choice questions will improve your skills and familiarity with common patterns. Familiarity with how questions are structured and what to expect can make all the difference when the actual assessment comes. Regular practice and these strategies will enable you to approach multiple-choice questions with clarity and confidence.
Exploring Networking Security Focus
In today’s digital landscape, securing networks is more critical than ever. The protection of sensitive data, prevention of unauthorized access, and ensuring the integrity of communication channels are essential for organizations of all sizes. By focusing on network security, professionals aim to defend against various threats, such as malware, phishing attacks, and data breaches, while maintaining smooth and reliable connectivity for all users. Understanding key strategies and technologies involved in network protection is crucial for anyone aiming to advance in the field.
One of the main focuses within networking security is the concept of building robust defense mechanisms that can prevent unauthorized access to a network. This involves both proactive measures such as firewalls, encryption, and intrusion detection systems, as well as reactive strategies to deal with potential breaches or attacks. To effectively secure a network, it’s vital to understand the various vulnerabilities that exist, how they can be exploited, and how to mitigate the risks associated with them.
Modern network security requires a combination of strong technical skills and strategic thinking. By continuously assessing and adapting to new challenges, professionals can implement effective solutions that safeguard the integrity of an organization’s data and infrastructure. Whether it’s through maintaining secure connections, implementing multi-factor authentication, or ensuring compliance with industry standards, a comprehensive approach is necessary to address both internal and external threats.
What to Expect on the Networking Security Assessment
When preparing for a comprehensive evaluation in the field of networking security, it’s important to understand the general structure and content of the assessment. This type of evaluation typically tests a broad range of concepts, from fundamental security principles to more advanced defensive strategies. The goal is to assess both theoretical knowledge and practical application skills. A successful participant must demonstrate their ability to analyze security risks, implement protective measures, and respond to real-world challenges in a network environment.
Key Topics to Cover
The assessment will likely include questions covering various core areas of networking security. The following topics are commonly tested:
- Network Fundamentals: Understanding of network protocols, IP addressing, and routing.
- Security Devices: Knowledge of firewalls, intrusion detection systems, and VPN technologies.
- Risk Management: Identifying vulnerabilities and implementing security measures to protect sensitive information.
- Encryption Techniques: Proficiency in encryption methods to secure data transmission.
- Incident Response: Ability to respond to security breaches and mitigate potential damage.
Types of Questions
The assessment may include different formats of questions to evaluate various skills:
- Multiple Choice: Questions that test your theoretical understanding of security principles.
- Simulations: Practical exercises that require hands-on application of network security solutions.
- Scenario-Based: Situations where you must analyze a network environment and recommend appropriate security measures.
Expect to see both theoretical questions that assess your knowledge and practical questions that test your ability to apply that knowledge in real-world scenarios. Thorough preparation is key to succeeding in this comprehensive assessment.