
In this section, we dive into the essential building blocks of networking, focusing on the core principles that form the foundation of any network environment. Understanding these fundamentals is crucial for anyone aiming to excel in the field of network management and troubleshooting.
From the basics of communication between devices to the protocols that govern data flow, this guide will provide you with a comprehensive overview. You will explore key concepts such as addressing systems, network structure, and the devices that make up modern networks, all of which are vital for a deeper understanding of network operations.
Whether you are starting your journey in networking or enhancing your skills, mastering these foundational topics will ensure a strong grasp of the subject and set you up for success in more advanced areas.
Understanding Key Networking Concepts
Grasping the fundamental principles of networking is essential for anyone looking to build a career in the field. This section focuses on the core concepts that serve as the foundation for all advanced network-related topics. By gaining a solid understanding of these ideas, you’ll be equipped to tackle more complex subjects with confidence.
The focus is on learning how devices communicate within a network, the role of various protocols, and how data travels across different mediums. Additionally, understanding how networks are structured and the devices that make them functional is crucial for anyone seeking to understand the broader picture of network design and troubleshooting.
These foundational concepts not only provide a strong base for further study but also give practical insights into real-world networking scenarios. A clear comprehension of these basics is essential to navigating the increasingly complex world of technology and network management.
Overview of Networking Fundamentals

At the heart of every effective communication system is a strong understanding of the basic principles that govern network connections. These essential concepts lay the groundwork for more complex network design and management tasks. A network is, in essence, a collection of devices that can exchange data, and understanding how this exchange works is crucial for anyone working with technology.
Networking fundamentals cover a wide range of topics, from how data is transmitted across different devices to the structure of local and wide area networks. By gaining knowledge of these basic ideas, you’ll be better prepared to understand how devices interact, how networks are built, and how information flows securely and efficiently.
| Key Concept | Description |
|---|---|
| Data Transmission | The process of sending and receiving data between devices using different communication mediums like cables or wireless signals. |
| Network Topology | Refers to the physical and logical arrangement of devices in a network, such as star, bus, or ring configurations. |
| Protocols | Rules and conventions that determine how data is transmitted and received in a network, including TCP/IP and Ethernet standards. |
| Network Devices | Hardware such as routers, switches, and hubs that facilitate data transmission and connectivity within the network. |
Understanding these fundamental aspects not only prepares you for further study but also enhances your ability to troubleshoot and manage networks in real-world environments. These concepts are the building blocks of network operations and play a vital role in ensuring smooth communication between devices and systems.
Key Terminology for Networking Success
In the world of networking, understanding the key terms and definitions is essential for effectively communicating and solving problems. These terms serve as the foundation for all discussions and practical work involving networks, making them indispensable for anyone aiming to work with or manage network systems. Mastering this terminology is the first step toward becoming proficient in the field.
From concepts related to the transmission of data to the devices that facilitate this communication, a solid grasp of networking terminology will help you make informed decisions, troubleshoot issues, and optimize network performance. Whether you’re building, managing, or securing networks, knowing these terms will enhance your technical communication and troubleshooting skills.
| Term | Definition |
|---|---|
| IP Address | A unique numerical label assigned to each device connected to a network, identifying the device’s location. |
| Router | A device that forwards data packets between different networks, directing traffic efficiently. |
| Switch | A device used to connect devices within the same network, facilitating data transmission between them. |
| Protocol | A set of rules governing the exchange of data between devices, ensuring proper communication and data integrity. |
| Bandwidth | The maximum rate at which data can be transferred over a network connection, typically measured in bits per second (bps). |
| Subnet Mask | A number that defines the network portion and host portion of an IP address, helping devices determine which part of an address identifies the network and which part identifies the device. |
Familiarizing yourself with these key terms will provide a clearer understanding of how networking systems work and how to address common challenges that arise in network management. Whether for troubleshooting, design, or security, this terminology forms the bedrock of effective network administration.
IP Addressing and Subnetting Basics
Understanding IP addressing and subnetting is fundamental to effectively managing and designing network systems. These concepts enable devices to communicate with one another by assigning unique identifiers to each device and segmenting networks for efficient operation. Without a solid grasp of these topics, it would be difficult to structure or troubleshoot any network.
IP addressing involves assigning a unique number to each device on a network, ensuring that data can reach its correct destination. Subnetting allows networks to be divided into smaller, more manageable sections, improving performance and security. A clear understanding of both concepts is essential for anyone working with modern networks, as they play a critical role in communication and scalability.
| Concept | Explanation |
|---|---|
| IP Address | A unique identifier for a device on a network, allowing it to send and receive data. |
| Subnet | A smaller network within a larger network, created by dividing the original network for improved management and security. |
| Subnet Mask | A number that defines the network portion and host portion of an IP address, helping to determine which devices are part of the same network. |
| CIDR Notation | A method for representing IP addresses and their associated subnet masks in a compact form, such as 192.168.1.0/24. |
| Private IP Address | An IP address reserved for use within a private network, not routable on the public internet. |
By mastering these concepts, you will be able to design efficient networks, troubleshoot connectivity issues, and optimize the flow of data. IP addressing and subnetting are indispensable skills for anyone working with network infrastructure and are foundational to building robust and scalable systems.
OSI Model Layers Explained
The OSI model is a conceptual framework used to understand and troubleshoot network communication. It breaks down the entire process of data transmission into seven distinct layers, each responsible for different tasks. By learning how these layers work together, you gain a clearer picture of how data moves from one device to another across a network.
Each layer of the OSI model serves a specific function, from establishing the physical connection to ensuring the data is understood by the receiving device. Understanding these layers not only helps with network design but also assists in troubleshooting communication issues at different stages of the transmission process.
Overview of the Seven Layers
The OSI model consists of seven layers, each playing a crucial role in network communication:
| Layer | Function |
|---|---|
| Layer 1: Physical | Handles the transmission of raw data over physical media like cables or wireless signals. |
| Layer 2: Data Link | Manages error detection, correction, and frame synchronization for reliable data transfer. |
| Layer 3: Network | Responsible for routing data between different networks, using IP addresses to determine the best path. |
| Layer 4: Transport | Ensures reliable data transfer, managing flow control, error correction, and segmentation of data. |
| Layer 5: Session | Manages sessions between devices, ensuring continuous communication and data synchronization. |
| Layer 6: Presentation | Formats and encrypts data for transmission, ensuring that it is presented in a way the receiving device can understand. |
| Layer 7: Application | Interacts directly with end-user software, providing services like email, file transfer, and web browsing. |
Understanding Layer Interactions
Each layer of the OSI model interacts with the layers directly above and below it, ensuring that data is transmitted, received, and understood. The separation of responsibilities helps simplify network troubleshooting, as issues can be isolated to specific layers, whether it’s a physical connectivity problem, a routing error, or an application-level issue.
By understanding the OSI model, you can approach network issues systematically and efficiently, knowing exactly where to focus your attention to resolve problems effectively.
Ethernet Standards and Protocols
Ethernet is one of the most widely used technologies for local area networks (LANs), providing a set of standards and protocols that enable devices to communicate over a shared medium. These standards define the rules for how data is transmitted across a network, ensuring reliable and efficient communication. Understanding these standards is key to maintaining and troubleshooting modern network infrastructures.
Ethernet protocols are continuously evolving to meet the growing demand for faster and more reliable connections. Various Ethernet standards exist to support different speeds, cable types, and network configurations. By knowing which standards are applicable in different situations, you can ensure optimal performance and compatibility across devices and network segments.
Key Ethernet Standards
- IEEE 802.3 – The core standard for Ethernet, specifying how data is framed, transmitted, and accessed over a wired LAN.
- Gigabit Ethernet – A standard that supports data transfer rates of 1 Gbps, widely used in high-performance networking environments.
- 10-Gigabit Ethernet – An advanced standard providing speeds of up to 10 Gbps for very high-demand applications, such as data centers.
- Fast Ethernet – A standard supporting speeds of 100 Mbps, often used in smaller networks and older infrastructures.
Common Ethernet Protocols
In addition to standards, there are various protocols that guide how Ethernet operates and manages data flow. These protocols are essential for ensuring data is transmitted correctly and efficiently across the network.
- Carrier Sense Multiple Access with Collision Detection (CSMA/CD) – A protocol used in traditional Ethernet networks to manage how devices share the network medium and avoid data collisions.
- Ethernet II – The most commonly used Ethernet frame format, used for encapsulating data packets in modern networks.
- Address Resolution Protocol (ARP) – A protocol used to map IP addresses to MAC addresses within a local network, enabling devices to locate each other.
- Spanning Tree Protocol (STP) – A protocol used to prevent network loops in switched networks by dynamically blocking and unblocking network paths.
Understanding these standards and protocols is essential for configuring, troubleshooting, and optimizing Ethernet-based networks. Whether you’re setting up a home network or managing a large-scale corporate infrastructure, this knowledge helps ensure the efficient transfer of data and proper network functionality.
Understanding Network Topologies
Network topologies define the layout and structure of connections between devices within a network. They describe how network elements such as computers, switches, routers, and other devices are arranged and how they communicate with each other. The design of a network topology plays a crucial role in its performance, reliability, and scalability, as well as in the ease of maintenance and troubleshooting.
Each topology has its strengths and weaknesses, making some better suited for certain environments than others. Understanding the various types of network topologies helps network administrators make informed decisions when designing and managing networks. Whether it’s for a small office, a large enterprise, or a data center, selecting the right topology is essential for ensuring efficiency and performance.
Common Types of Network Topologies
- Bus Topology – A simple network design where all devices are connected to a single central cable or backbone, making it cost-effective but prone to performance issues as the network grows.
- Star Topology – Devices are connected to a central hub or switch, which acts as the focal point for communication. This topology is easy to scale and troubleshoot but relies heavily on the central device.
- Ring Topology – Devices are connected in a circular fashion, where data travels in one direction, passing through each device until it reaches the destination. While it is efficient in data flow, a single failure can disrupt the entire network.
- Mesh Topology – Every device is connected to every other device, providing high redundancy and fault tolerance. However, the complexity and cost increase with the number of devices.
- Hybrid Topology – A combination of two or more different topologies, designed to take advantage of the strengths of each while minimizing their individual weaknesses.
Choosing the Right Topology for Your Network
When selecting a network topology, it’s essential to consider factors such as the size of the network, the number of devices, the type of data being transmitted, and the required level of redundancy. Some topologies, like the star, are ideal for businesses needing easy scalability and central management, while others, like the mesh, are better suited for networks where uptime and fault tolerance are critical.
In any case, understanding the advantages and limitations of each topology will help you create a network that meets both current needs and future growth requirements.
Roles of Routers and Switches
Routers and switches are essential devices in any network, each serving distinct but complementary roles in ensuring smooth and efficient data communication. While both contribute to directing data traffic, their functions are fundamentally different, tailored to handle specific network tasks. Understanding the roles of these devices helps in designing networks that are both efficient and scalable.
Routers typically operate at the network layer and are responsible for directing data between different networks. They use routing tables and protocols to determine the optimal path for data packets to reach their destination. Switches, on the other hand, operate at the data link layer and manage data flow within a single network, forwarding frames between devices based on their MAC addresses. Both devices are crucial for maintaining the performance and security of a network.
Functions of Routers
Routers play a key role in connecting multiple networks and directing traffic between them. They are responsible for determining the best route for data to travel from the source to the destination, often across different network segments or even the internet.
- Path Determination – Routers analyze the destination address of data packets and choose the most efficient path through the network, using routing tables and protocols.
- Network Segmentation – By dividing a large network into smaller subnets, routers help improve network efficiency and reduce traffic congestion.
- Traffic Management – Routers can prioritize certain types of traffic, such as voice or video, ensuring that critical data is transmitted without delay.
Functions of Switches
Switches are primarily used to manage communication within a local network, such as a LAN, ensuring that data reaches the correct device within that network. They perform several essential tasks to keep the network running smoothly.
- Data Forwarding – Switches forward frames to the correct device based on its MAC address, ensuring that data reaches the intended recipient within the network.
- Traffic Isolation – Switches create separate collision domains for each connected device, reducing network traffic and improving performance.
- Network Expansion – By connecting multiple devices within the same network, switches help expand the network’s capacity without affecting overall performance.
Both routers and switches are integral to network operation, yet they serve different functions that complement each other. Routers manage traffic between different networks, while switches ensure efficient communication within a single network. Understanding how these devices work together is essential for building a reliable and scalable network.
Working with TCP and UDP
Transmission of data across networks involves a variety of protocols designed to ensure that information reaches its destination reliably and efficiently. Two of the most commonly used protocols for managing data transmission are TCP and UDP. These protocols play a crucial role in how devices communicate over a network, with each offering distinct advantages depending on the needs of the application.
While both protocols operate at the transport layer and facilitate communication between devices, they differ significantly in terms of reliability, speed, and error handling. TCP is known for its reliability and connection-oriented approach, ensuring that data packets are delivered in order and without error. UDP, on the other hand, is simpler and faster, but it does not guarantee delivery or order, making it suitable for real-time applications where speed is a priority.
Transmission Control Protocol (TCP)
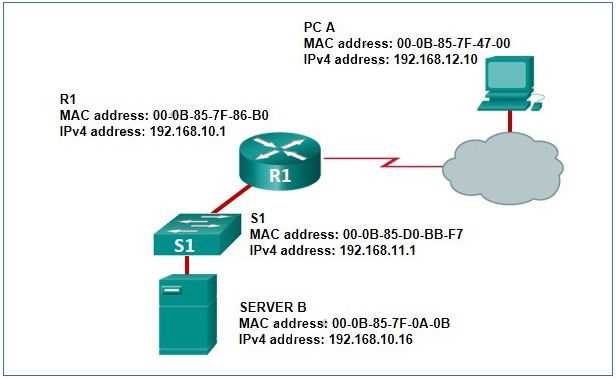
TCP is a connection-oriented protocol that ensures reliable data transfer between devices. It establishes a connection before transmitting data and guarantees that the data is delivered correctly, in sequence, and without duplication. This makes it ideal for applications where data integrity is crucial.
- Reliability – TCP ensures that all data packets are delivered in the correct order. If a packet is lost or corrupted, it is retransmitted.
- Flow Control – It regulates the rate at which data is sent to avoid overwhelming the receiving device.
- Error Detection – TCP includes mechanisms to check for errors and request retransmission if necessary.
- Connection Establishment – A three-way handshake is used to establish a connection before data transfer begins, ensuring that both devices are ready to communicate.
User Datagram Protocol (UDP)
UDP is a connectionless protocol that offers a faster, simpler alternative to TCP. Unlike TCP, UDP does not establish a connection before sending data, nor does it ensure that packets are delivered in order. This makes UDP suitable for applications where speed is more important than reliability.
- Speed – UDP is faster than TCP because it lacks the overhead of connection management and error correction.
- Low Latency – UDP is ideal for real-time applications, such as online gaming or voice over IP (VoIP), where low latency is crucial.
- Unreliable Delivery – There is no guarantee of delivery, and if packets are lost or delayed, they are not retransmitted.
- No Connection Setup – UDP transmits data without establishing a formal connection, making it quicker to start communication.
Choosing between TCP and UDP depends on the specific requirements of the application. For scenarios where accuracy and data integrity are paramount, TCP is the better choice. However, for applications that require low latency and can tolerate occasional data loss, UDP offers a faster and more efficient solution.
Data Encapsulation and De-encapsulation

Data transmission across a network involves the process of encapsulating information into packets and later extracting or “de-encapsulating” it to make sense of the original data. This concept is fundamental to understanding how devices communicate and how data is transmitted between different layers of the network. Each layer of the networking model plays a specific role in preparing and handling data as it travels across the network.
Encapsulation involves taking data from an upper layer and wrapping it in a protocol header, which contains important information such as source and destination addresses, error-checking information, and control flags. When the data reaches its destination, the receiving system “unwraps” or de-encapsulates the data, removing the headers and passing the original data to the appropriate application or service.
Process of Encapsulation
During the encapsulation process, each layer of the networking model adds its own header, with the ultimate goal of ensuring proper delivery and communication. The process starts with the application layer and ends with the physical layer.
- Application Layer: The user data is generated and prepared for transmission.
- Transport Layer: This layer adds the transport header, which contains information about the communication session, such as port numbers.
- Network Layer: At this layer, the data receives a header that includes the destination IP address.
- Data Link Layer: A frame header is added, which includes the MAC address of the sender and receiver, as well as error-checking information.
- Physical Layer: The final step involves converting the encapsulated data into electrical or optical signals for transmission over the network medium.
Process of De-encapsulation
When the encapsulated data reaches its destination, the process is reversed. Each layer of the receiving system removes the respective headers, and the original data is passed upward through the layers to the application that requested it.
- Physical Layer: The data is received as raw signals and converted back into bits for processing.
- Data Link Layer: The frame is processed, and the header is removed, revealing the network layer’s data.
- Network Layer: The IP header is stripped off, and the data is passed up to the transport layer.
- Transport Layer: The transport header is removed, and the data is delivered to the correct application based on the port number.
- Application Layer: The original data is now available to the user or application that requested it.
Understanding encapsulation and de-encapsulation is crucial for network engineers and anyone involved in networking, as it helps in troubleshooting, optimizing performance, and designing efficient network systems. Each layer plays a vital role in ensuring data is successfully delivered and understood at its destination.
IP Routing and Packet Delivery

In a network, data is transferred between devices using packets that need to follow specific routes to reach their destination. The process of directing these packets from one device to another across different networks is known as routing. Routing ensures that data takes the most efficient path, allowing devices to communicate even when they are far apart or on separate networks. This process is essential for packet delivery, as it determines how and where the data should travel to reach its final destination.
At its core, packet delivery involves determining the correct destination address, selecting the appropriate route, and forwarding the packet through the network. Routing decisions are made by network devices, such as routers, which use routing tables to decide the best path for data transmission. The ability to route packets efficiently plays a key role in network performance, reducing latency and packet loss.
How Routing Works
Routing uses logical addresses (IP addresses) to determine where data packets should be sent. Routers analyze the destination address in each packet and make forwarding decisions based on their routing tables, which contain information about available paths in the network.
- Routing Table: A list of possible paths for data to travel. The table helps routers determine the most efficient route based on network topology and conditions.
- Static Routing: Predefined routes are manually set by network administrators. This method is simple but lacks flexibility.
- Dynamic Routing: Routers automatically adjust routes based on network changes. This method uses protocols to update routing tables in real-time.
Steps in Packet Delivery
Once the routing decision is made, the data packet is forwarded through the network, passing through multiple devices before reaching its destination. The packet may traverse several intermediate routers, each making routing decisions based on its table, until it reaches the correct endpoint.
- Packet Encapsulation: The data is encapsulated with the necessary information for transmission, including the destination address and routing information.
- Forwarding: Routers forward the packet to the next device along the path, using the routing table to make decisions about the next hop.
- De-encapsulation: Upon reaching the destination, the packet is de-encapsulated, and the data is extracted and passed to the appropriate application or service.
In complex networks, routing protocols help maintain up-to-date routing tables and adapt to changes, such as new paths or network failures. Protocols like RIP, OSPF, and BGP play essential roles in dynamic routing by enabling routers to share information about network changes and optimize packet delivery.
Common Network Troubleshooting Tools
Effective network troubleshooting relies on a set of tools that help identify and resolve connectivity issues. These tools allow network administrators to diagnose problems with data transmission, check for faults in devices or connections, and determine the root cause of performance issues. By using these utilities, professionals can ensure networks operate smoothly and efficiently, minimizing downtime and improving overall performance.
Network troubleshooting tools can range from simple command-line utilities to more sophisticated diagnostic programs. They help in isolating network issues, such as packet loss, latency, and incorrect configurations, and assist in analyzing network traffic to pinpoint the cause of disruptions.
Key Troubleshooting Tools
Several tools are commonly used for troubleshooting networks, each with specific functions and use cases:
- Ping: A basic utility used to test connectivity between two devices on a network. It sends small packets to a destination address and waits for a reply, helping identify whether the destination is reachable.
- Traceroute: This tool tracks the path packets take to reach their destination. It helps determine where delays or packet loss occur along the route, which is valuable in diagnosing issues with intermediate devices or connections.
- nslookup: A tool for querying Domain Name System (DNS) servers to resolve domain names into IP addresses. It helps verify DNS configurations and diagnose issues related to name resolution.
- Netstat: A command-line tool that displays the network connections, routing tables, and protocol statistics. It helps monitor active connections and identify any unexpected or unauthorized activity on the network.
Advanced Troubleshooting Tools
For more complex network issues, advanced tools provide deeper analysis of network traffic and performance metrics:
- Wireshark: A network protocol analyzer that captures and inspects data packets in real-time. It allows for in-depth analysis of network traffic, making it useful for identifying issues such as misconfigured protocols or suspicious network behavior.
- iPerf: A tool used for measuring network bandwidth between two devices. It helps test the performance of network connections by generating traffic and measuring throughput, jitter, and packet loss.
- PathPing: A combination of Ping and Traceroute, PathPing provides a more detailed view of packet loss and latency over multiple hops. It is useful for diagnosing intermittent issues and network congestion.
By mastering these common troubleshooting tools, network professionals can quickly identify and address issues, ensuring that networks run efficiently and remain secure.
Understanding VLAN and Switching
In modern networks, managing traffic and segmenting data flows is crucial for optimizing performance and security. Virtual Local Area Networks (VLANs) and the role of switches are central to achieving this. VLANs allow administrators to group devices logically, regardless of their physical location, which enhances network efficiency and security. Switches, on the other hand, play a key role in directing traffic between devices within the same network or across VLANs.
By using VLANs, a network can be divided into smaller, more manageable sections, each with its own set of rules and policies. This not only improves the security of each group but also minimizes unnecessary traffic. Switches operate by forwarding data only to the appropriate devices, based on their MAC addresses, and can also manage traffic between different VLANs if configured to do so.
Key Concepts of VLANs
VLANs offer several advantages for network management, such as improved security and better traffic management. Here are the main concepts behind VLANs:
- Logical Grouping: VLANs group devices based on function, department, or security level rather than physical location.
- Broadcast Control: By isolating broadcast traffic within VLANs, the network’s overall performance is improved, reducing unnecessary network traffic.
- Enhanced Security: Devices within different VLANs are logically separated, preventing unauthorized access to sensitive resources across the network.
The Role of Switches in VLANs
Switches are responsible for forwarding data between devices within the same network and can be configured to support VLANs. The role of a switch in a network is critical, as it can isolate traffic, direct packets to the correct destination, and support communication between different VLANs.
- Port-Based VLANs: Each port on a switch is assigned to a specific VLAN, and any device connected to that port will automatically become part of the VLAN.
- Trunking: To allow communication between devices on different VLANs, trunk links are used to carry traffic for multiple VLANs across the same physical connection between switches.
- Inter-VLAN Routing: Switches can be configured with routing capabilities to manage traffic between VLANs, allowing them to communicate while maintaining logical separation.
Proper VLAN and switch configuration ensures efficient traffic management, enhanced security, and an overall better network performance. Network administrators need to understand how to effectively implement VLANs and configure switches to optimize network functionality and maintain robust security standards.
Best Practices for Network Design
Designing a network is a critical task that directly influences the performance, scalability, and security of a company’s infrastructure. A well-designed network not only supports the current needs of an organization but also provides the flexibility to adapt to future growth and technological changes. Adopting best practices ensures that the network is reliable, efficient, and secure while meeting the demands of users and applications.
Effective network design involves a thorough understanding of the organizational requirements, the traffic patterns, and the technologies that will be used. Planning for redundancy, scalability, and security from the beginning can help prevent issues down the line and reduce the cost of future upgrades. Additionally, the use of standardized frameworks and principles allows for easier management and troubleshooting.
Key Considerations in Network Design
To achieve optimal performance and reliability, consider these essential factors when designing a network:
- Redundancy and Failover: Design the network with backup paths and devices to ensure availability in case of failure. Implementing failover mechanisms reduces downtime and ensures business continuity.
- Scalability: Build a network that can scale as the organization’s needs grow. This means selecting components that can easily be upgraded or expanded without disrupting operations.
- Security: Implement strong security measures, including firewalls, intrusion detection systems, and secure access controls, to protect against threats and unauthorized access.
- Performance: Optimize network performance by carefully selecting hardware and managing traffic to avoid bottlenecks. Consider factors like bandwidth, latency, and packet loss.
Documentation and Monitoring

Documentation is essential in network design to ensure that network components, configurations, and configurations are well understood and easy to manage. Monitoring tools help track network performance, diagnose issues, and ensure that everything is functioning as expected.
- Network Maps: Create detailed network diagrams that outline the physical and logical layout of the network. This aids in troubleshooting and future upgrades.
- Continuous Monitoring: Implement network monitoring solutions to detect performance degradation, potential security breaches, or equipment failures in real-time.
By following these best practices, organizations can ensure that their networks are resilient, efficient, and ready to meet the challenges of the future. Thoughtful design can help reduce operational costs, improve user experience, and ensure that the network evolves with the organization’s growth.
Preparing for the Certification Test
Preparing for a networking certification test requires focused study, practical experience, and a solid understanding of foundational concepts. It’s important to approach the process methodically, ensuring that all critical topics are covered and that you are ready to apply theoretical knowledge to real-world scenarios. A well-planned preparation strategy can make all the difference in achieving a successful outcome.
To prepare effectively, start by reviewing the core principles of networking, including the basics of networking protocols, routing, switching, and security. Hands-on practice is essential for reinforcing theoretical knowledge and gaining confidence in configuring devices, troubleshooting network issues, and applying best practices. Time management during the study phase, along with the use of reliable resources, will help ensure a comprehensive understanding of all necessary topics.
Key Areas to Focus On
When preparing for the test, prioritize these key areas:
- Networking Fundamentals: Understand how networks operate, the role of different devices, and the basics of IP addressing, subnetting, and routing.
- Network Protocols: Learn about important protocols like TCP/IP, UDP, and ICMP, and how they enable communication across networks.
- Routing and Switching: Study the principles behind routing and switching, including how routers and switches determine data paths in a network.
- Security Measures: Familiarize yourself with the various security measures used to protect a network, including firewalls, access control lists, and encryption techniques.
Study Tips and Resources
Effective preparation also involves using a variety of resources and study techniques to ensure a comprehensive understanding of the material:
- Books and Online Materials: Refer to up-to-date books, online courses, and practice exams to reinforce your understanding and identify weak areas.
- Hands-on Practice: Use network simulators or actual lab equipment to practice configuration and troubleshooting tasks, as practical experience is key to success.
- Study Groups and Forums: Join online study groups or forums where you can discuss concepts, ask questions, and share resources with others preparing for the test.
By following these strategies and focusing on the key areas of the test, you can increase your chances of success and confidently approach the certification process. Consistency, hands-on practice, and continuous learning are essential for mastering the material and excelling in the test.