In the world of networking, mastering complex configurations and troubleshooting scenarios is crucial for anyone pursuing a career in this field. The ability to solve real-world problems using networking tools and protocols is essential for success. Understanding how to approach these challenges efficiently can make a significant difference when faced with timed tasks or performance-based assessments.
Preparing for network-related tasks requires more than just memorizing concepts. It demands practical skills and the ability to think critically under pressure. In this guide, we will explore strategies to help you navigate through configuration and troubleshooting questions, focusing on practical approaches and common issues faced during assessments. With the right preparation, you can confidently tackle any networking challenge that comes your way.
CCNA 2 Packet Tracer Final Exam Answers
Networking assessments often present complex scenarios that test your ability to apply theoretical knowledge in real-world situations. The key to success lies in understanding the underlying concepts and techniques that drive network configurations and troubleshooting. In this section, we’ll explore how to tackle such challenges and provide effective solutions based on common network issues.
Key Concepts for Network Configuration Tasks
Before diving into specific tasks, it’s essential to have a solid understanding of fundamental network components and how they interact. Proper addressing, routing protocols, and switch configurations are just a few of the building blocks that ensure a network operates efficiently. Below is a summary of the most critical concepts that will help you navigate configuration tasks successfully.
| Concept | Importance | Application |
|---|---|---|
| IP Addressing | Ensures proper communication between devices on a network. | Configuring routers and devices with correct IPs for connectivity. |
| Routing Protocols | Defines how data is directed across networks. | Setting up protocols like RIP or OSPF for efficient routing. |
| VLANs | Improves network security and performance by segmenting traffic. | Configuring switches to assign devices to specific virtual LANs. |
| Subnetting | Optimizes IP address usage and network design. | Calculating subnet masks for proper network segmentation. |
Common Troubleshooting Steps
During network tasks, issues often arise due to misconfigurations or connectivity problems. Troubleshooting is a critical skill that requires a methodical approach. Follow these basic steps when diagnosing and resolving issues:
| Step | Action |
|---|---|
| Step 1 | Check physical connections and ensure all cables are properly connected. |
| Step 2 | Verify that IP addresses and subnet masks are correctly configured. |
| Step 3 | Ping devices within the same network to check connectivity. |
| Step 4 | Test routing protocols and ensure proper routes are in place. |
| Step 5 | Review logs and diagnostic tools for any errors or warnings. |
By mastering these techniques, you’ll be well-prepared to handle any network configuration challenge and troubleshoot effectively under test conditions.
Essential Tips for Packet Tracer Success
Mastering network simulation tools requires a blend of technical knowledge, hands-on practice, and efficient problem-solving techniques. Success in these scenarios depends not only on your understanding of theoretical concepts but also on your ability to apply them effectively under time constraints. Below are essential strategies to help you excel in network configuration tasks and ensure smooth progress throughout the process.
One of the most important aspects is to familiarize yourself with the interface and tools available within the simulation software. Knowing where to find key settings and how to navigate the workspace can save valuable time during challenging tasks. Additionally, understanding the proper sequence of steps for configuring network devices and protocols ensures that you approach each scenario systematically.
Another critical point is attention to detail. Many network-related issues stem from minor oversights, such as incorrect IP assignments or missing cables. Double-checking your work and verifying configurations step by step can prevent these common mistakes. By being thorough and organized, you’ll be able to address problems before they escalate.
Finally, continuous practice is key. The more you engage with simulated scenarios, the more proficient you’ll become at troubleshooting and optimizing network setups. Focus on a variety of tasks and configurations to build a well-rounded skill set. With consistent effort, you’ll improve your ability to solve complex problems efficiently and confidently.
How to Approach Network Configuration Questions
When faced with network configuration tasks, a structured approach can make a significant difference in your ability to solve the problem efficiently. Rather than jumping straight into the configuration, it’s important to assess the situation and plan your steps logically. This method will not only help you avoid mistakes but also ensure that your solutions are both effective and scalable.
Step-by-Step Approach
Breaking down the task into smaller, manageable steps is key to maintaining focus and ensuring you don’t miss any crucial details. Follow these guidelines:
- Understand the Requirements: Carefully read the task description and identify the objectives. Make sure you understand the specific configurations needed, such as IP addressing, routing, and security settings.
- Plan Your Configuration: Think about how each component (routers, switches, devices) needs to be set up. Visualizing the network topology can help organize your approach.
- Verify Connections: Ensure all physical connections, like cables and interfaces, are correctly placed before proceeding with configurations.
- Implement the Configuration: Apply the settings step by step, starting with basic network setup like IP addresses, followed by advanced configurations like routing protocols and VLANs.
- Test and Troubleshoot: After configuring, test connectivity and verify that each device is working as expected. If issues arise, troubleshoot systematically using diagnostic tools.
Common Mistakes to Avoid
Even experienced network engineers can fall into common traps. Stay mindful of the following:
- Skipping initial planning, which can lead to missed configurations or inefficient setups.
- Overlooking interface status (enabled vs disabled) or physical connections.
- Misconfiguring IP addresses, subnet masks, or default gateways, which can lead to connectivity issues.
- Forgetting to save configurations, resulting in lost progress after a reboot.
By following a clear, methodical approach and avoiding these pitfalls, you will increase your chances of successfully completing network configuration tasks with accuracy and confidence.
Common Mistakes in Packet Tracer Exams
While working through network simulations, many individuals make simple yet impactful mistakes that can derail their progress. These errors often stem from overlooking basic concepts or failing to properly execute the steps required for a correct setup. Understanding these common pitfalls can help you avoid them and ensure a smoother experience when tackling these tasks.
By focusing on the core elements of network configuration and troubleshooting, you can minimize the risk of making critical mistakes. Below are some of the most frequent errors that users encounter, along with tips for how to avoid them.
Frequent Errors and How to Avoid Them
- Incorrect IP Addressing: Misassigning IP addresses, subnet masks, or default gateways can lead to connectivity issues between devices. Always double-check the IP scheme and ensure consistency across your network setup.
- Not Saving Configurations: Forgetting to save the configurations after making changes means losing progress once the devices are rebooted. Remember to save regularly to avoid this problem.
- Failure to Enable Interfaces: Network interfaces may be in a disabled state by default. Always check that all relevant interfaces are enabled before proceeding with configurations or testing connectivity.
- Overlooking VLAN Settings: Not properly assigning VLANs to switches or devices can lead to traffic not being routed correctly. Ensure each device is configured with the correct VLAN assignments to avoid segmentation issues.
- Skipping Routing Protocol Configurations: Routing protocols are essential for proper data forwarding between networks. Always verify that routing protocols are correctly set up and interfaces are included in the routing process.
- Improper Cable Connections: Physical connections, such as cables and port assignments, are critical for communication between devices. Make sure all devices are connected appropriately to the correct interfaces.
- Neglecting Troubleshooting: If something isn’t working as expected, don’t hesitate to troubleshoot. Use ping tests, show commands, and other diagnostic tools to identify and resolve issues quickly.
Tips for Success
- Review Configuration Carefully: Double-check all settings before moving to the next step, including IP addresses, routing protocols, and security configurations.
- Practice Regularly: The more experience you gain with simulations, the more familiar you will become with the process, reducing the likelihood of mistakes.
- Stay Organized: Work step by step and keep track of your progress to ensure no task is overlooked.
By being aware of these common mistakes and taking proactive measures to avoid them, you can greatly improve your performance and confidence when working through network configuration tasks.
Understanding Key Routing Protocols
Routing protocols are essential for enabling communication between devices across different networks. They determine how data packets are forwarded from one network to another, ensuring that information reaches its intended destination. A solid understanding of these protocols is crucial for configuring and troubleshooting network setups effectively.
There are several types of routing protocols, each designed for specific use cases and environments. These protocols can be categorized as distance-vector, link-state, and hybrid, depending on how they determine the best path for data. Familiarity with these protocols will allow you to make informed decisions about which one to use in different network configurations.
Types of Routing Protocols
Below are some of the most common routing protocols, their characteristics, and typical use cases:
- RIP (Routing Information Protocol): A distance-vector protocol that uses hop count as its metric. Best for smaller networks due to its simplicity but limited scalability.
- OSPF (Open Shortest Path First): A link-state protocol that uses a more sophisticated metric based on cost, typically used in larger and more complex networks for better scalability and efficiency.
- EIGRP (Enhanced Interior Gateway Routing Protocol): A hybrid protocol that combines elements of both distance-vector and link-state protocols. Known for faster convergence times and better handling of large networks.
- BGP (Border Gateway Protocol): A path-vector protocol primarily used for routing between different autonomous systems (ASes), such as those in the internet backbone.
How Routing Protocols Work
Each protocol operates differently depending on its design and purpose. Here’s a brief overview of how they work:
- Distance-Vector Protocols: These protocols periodically send out their entire routing table to neighbors, with the goal of finding the best path based on hop count. While easy to configure, they tend to be slower and less efficient in larger networks.
- Link-State Protocols: Link-state protocols maintain a map of the entire network topology, allowing them to make more informed routing decisions. They are more scalable but require more memory and processing power.
- Hybrid Protocols: Hybrid protocols, such as EIGRP, combine the best features of both distance-vector and link-state protocols. They are typically faster in convergence and more reliable for larger networks.
Understanding these protocols and knowing when to use each one is vital for configuring and managing efficient network routes, especially in complex, enterprise-level environments.
How to Solve IP Addressing Problems
IP addressing is a fundamental aspect of networking, and errors in configuration can lead to significant connectivity issues. Properly assigning IP addresses to devices is crucial for ensuring seamless communication across the network. To solve IP addressing problems effectively, it’s important to follow a methodical approach, taking into account subnetting, address allocation, and the range of valid addresses for each segment of the network.
The process of solving IP addressing issues involves understanding the structure of IP addresses, recognizing the common pitfalls, and applying troubleshooting steps to identify and resolve misconfigurations. Below is a guide on how to approach and solve common IP addressing problems.
Common IP Addressing Issues
Below are some of the most frequent IP addressing problems encountered in network configuration:
| Problem | Description | Solution |
|---|---|---|
| IP Address Conflicts | Two devices on the network are assigned the same IP address, causing communication issues. | Ensure each device has a unique address. Use DHCP to automate address assignment where possible. |
| Incorrect Subnet Mask | Devices are unable to communicate across subnets due to an incorrect subnet mask. | Verify the subnet mask is consistent across devices in the same subnet and correctly matches the IP address range. |
| Missing Default Gateway | Devices are unable to reach networks outside their local subnet. | Ensure the default gateway is correctly configured on all devices that need to access external networks. |
| Overlapping Subnets | Two subnets are configured to overlap, causing routing problems. | Review the IP address assignments and subnetting to ensure there is no overlap between different network segments. |
Steps to Resolve IP Addressing Issues
When troubleshooting IP addressing problems, follow these steps to quickly and efficiently identify the root cause:
- Verify IP Address Configuration: Check that all devices have the correct IP address, subnet mask, and default gateway settings.
- Check for Address Conflicts: Use tools like
pingorarpto detect duplicate IP addresses on the network. - Test Connectivity: Use the
pingcommand to test if devices can communicate with each other within the same subnet and to the default gateway. - Validate Routing and Subnetting: Ensure that routers are correctly routing traffic between subnets and that subnet masks align with the network’s address ranges.
- Review DHCP Settings: If using DHCP, ensure that the server is properly assigning IP addresses and that there is no exhaustion of the address pool.
By following these steps and maintaining consistent addressing practices, you can efficiently resolve most IP addressing problems and ensure smooth network operation.
Analyzing Network Topology Scenarios
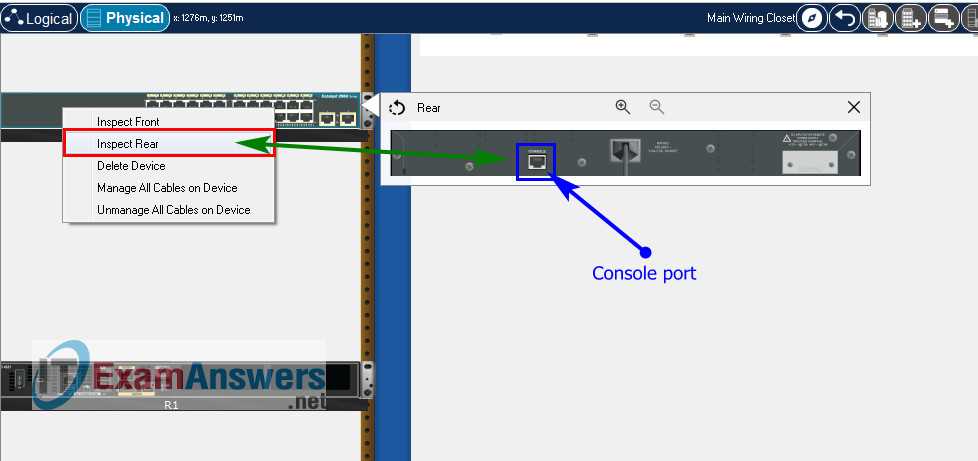
Understanding network topology is essential for designing and maintaining a robust and efficient network. Network topology defines the physical and logical arrangement of devices and how they communicate with each other. By analyzing different topology scenarios, network administrators can optimize network performance, identify potential weaknesses, and troubleshoot effectively. Whether you’re working on a small home network or a large-scale enterprise environment, assessing the layout of your network is a crucial step in problem-solving and network planning.
When analyzing network topology, it’s important to consider the type of topology in use, the devices involved, and the flow of data between them. Each topology has its strengths and weaknesses depending on factors such as scalability, redundancy, and performance. Below are some common network topologies and key considerations for analyzing their effectiveness.
Common Network Topologies
Different network topologies are used for various environments and needs. Below are the most common types and factors to consider when analyzing them:
- Bus Topology: All devices are connected to a single central cable (the bus). It’s easy to install but can become slow or unreliable with high traffic.
- Star Topology: Devices are connected to a central hub or switch. This topology is scalable and provides better fault tolerance, but the central device is a single point of failure.
- Ring Topology: Devices are connected in a circular fashion, where each device has two neighbors. It’s efficient for data transfer but can be disrupted by a single point of failure.
- Mesh Topology: Every device is connected to every other device, providing high redundancy and reliability. However, it’s costly and complex to implement.
- Hybrid Topology: A combination of two or more topologies, often used in large-scale networks. It allows for flexibility but requires careful planning to avoid complexity.
Steps to Analyze Network Topology
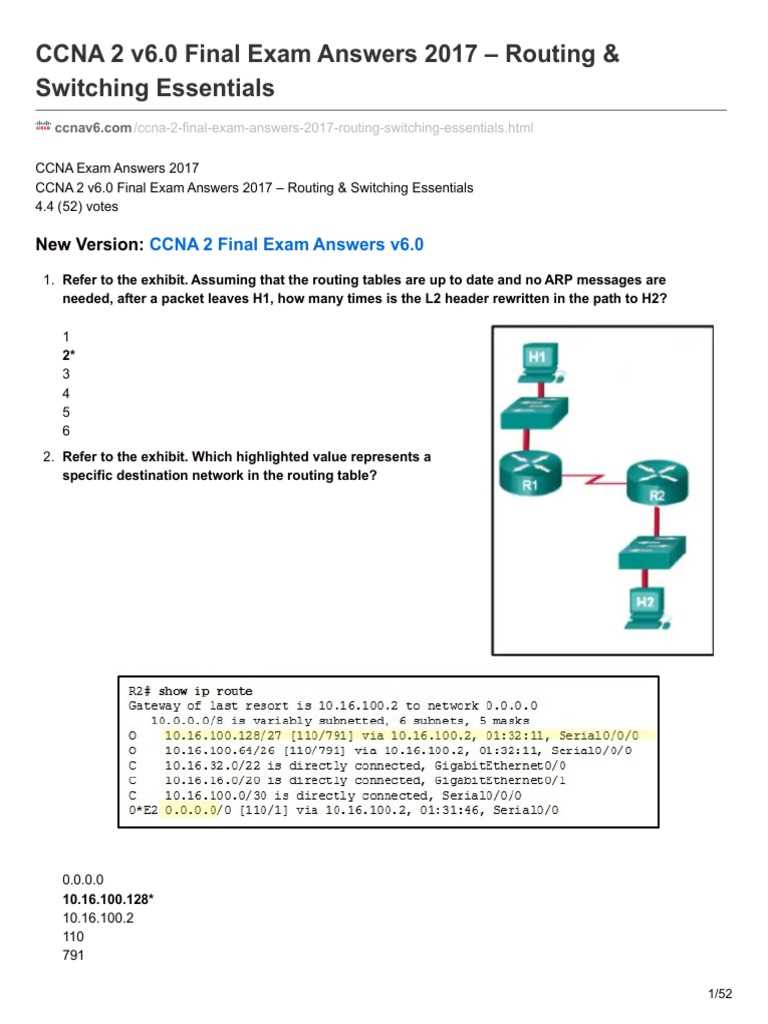
When evaluating network topology, follow these steps to assess the overall health and performance of the network:
- Review the Physical Layout: Examine how devices are physically connected. Are they using the most efficient paths for data transmission? Identify any bottlenecks or unnecessary complexity.
- Assess the Logical Design: Look at how data flows across the network. Is routing and switching optimized? Are there redundant paths to ensure high availability?
- Identify Single Points of Failure: Determine where failures could occur and what impact they would have. Is there adequate redundancy to handle device or link failures?
- Evaluate Scalability: Consider whether the topology can handle future growth. Will the network design support additional devices or higher data traffic without performance degradation?
- Test Network Performance: Use diagnostic tools to assess the network’s performance. Are there any slowdowns, errors, or issues with packet loss? Optimize configurations where necessary.
By methodically analyzing network topologies, you can identify areas for improvement and ensure your network operates at peak efficiency. Whether it’s optimizing the current design or planning for future expansions, this analysis is key to maintaining a healthy network infrastructure.
Packet Tracer Commands You Must Know
When working with network simulations, mastering essential commands is crucial for configuring devices and troubleshooting network issues. Command-line interfaces (CLI) are widely used for configuring routers, switches, and other network devices. Understanding the core set of commands not only speeds up the configuration process but also enables effective problem-solving and diagnostics.
In this section, we’ll cover the most important commands you should be familiar with when working in a simulation environment. These commands will allow you to configure devices, verify settings, and troubleshoot network issues effectively.
Basic Device Configuration Commands
These commands are used for configuring and managing network devices such as routers and switches:
- enable – Enters privileged exec mode, providing access to higher-level commands.
- configure terminal – Enters global configuration mode, where device settings can be changed.
- hostname – Sets the device’s hostname to a recognizable name for easier identification.
- interface – Accesses specific interface configurations (e.g.,
interface gig0/1) to set IP addresses or modify interface settings. - ip address – Assigns an IP address and subnet mask to a network interface (e.g.,
ip address 192.168.1.1 255.255.255.0). - no shutdown – Enables an interface, turning it on for communication. By default, many interfaces are administratively shut down.
- exit – Exits the current configuration mode and returns to the previous level.
Verification and Troubleshooting Commands
Once configurations are in place, these commands help verify settings and troubleshoot potential issues:
- show ip interface brief – Displays the status of all interfaces, including IP address, subnet mask, and their operational state.
- show running-config – Displays the current configuration of the device, showing all applied settings.
- show ip route – Displays the routing table, showing how traffic will be forwarded through the network.
- ping – Sends ICMP echo requests to test connectivity between devices. A successful ping indicates a working connection.
- traceroute – Traces the path that a packet takes to reach its destination, helping identify routing issues or delays.
- show version – Displays the software version, system uptime, and hardware details of the device.
- clear ip route – Clears the routing table, useful when troubleshooting routing problems or after changes in the network topology.
Mastering these fundamental commands will help you navigate through network configurations, verify settings, and troubleshoot issues efficiently. By regularly practicing these commands, you’ll become more proficient in managing and maintaining networks in a simulation environment or real-world setup.
Understanding VLAN Configuration in Detail
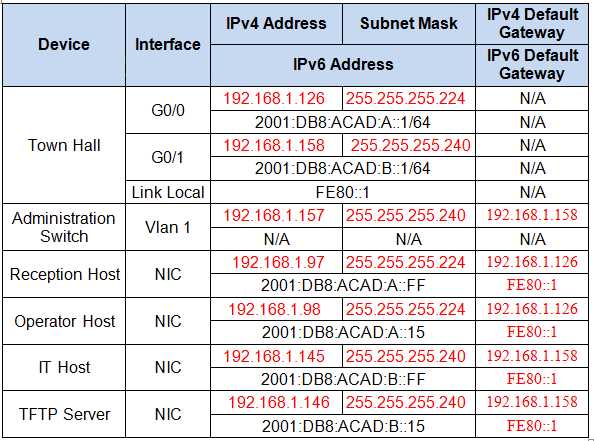
VLANs (Virtual Local Area Networks) are crucial for segmenting networks into smaller, more manageable groups. By creating VLANs, network administrators can improve network performance, enhance security, and simplify management. Understanding how to configure and manage VLANs is key to effective network design and troubleshooting.
VLAN configuration involves setting up network switches to assign devices to specific broadcast domains. This segmentation can help isolate network traffic, limit congestion, and control access between different departments or teams. In this section, we will explore how VLANs are configured, the importance of VLAN tagging, and common challenges encountered in the process.
VLAN Creation and Basic Configuration
To create and configure a VLAN, a series of steps must be followed. Below are the basic commands and actions to implement VLANs on network switches:
- Define the VLAN: The first step is to create the VLAN by specifying a unique VLAN ID (from 1 to 4095). This is done using the
vlancommand followed by the VLAN ID. - Assign a Name: Giving the VLAN a name is a good practice to easily identify it within the network. Use the
namecommand under VLAN configuration mode. - Assign Ports to VLAN: After creating the VLAN, assign switch ports to it. This can be done using the
switchport mode accesscommand followed byswitchport access vlan [VLAN_ID]. - Verify VLAN Configuration: Use the
show vlan briefcommand to check which VLANs are configured and which ports are assigned to each VLAN.
VLAN Tagging and Inter-VLAN Routing
VLAN tagging is used to identify which VLAN a frame belongs to as it travels across trunk links between switches. The following points outline how VLAN tagging works and the role of inter-VLAN routing:
- VLAN Tagging: When traffic moves between switches or across trunk links, VLAN tags are added to each frame. The
encapsulation dot1qcommand is used to configure trunk ports to support VLAN tagging (IEEE 802.1Q standard). - Trunk Ports: Trunk ports allow multiple VLANs to traverse a single physical link between switches. Use the
switchport mode trunkcommand to configure a port as a trunk. - Inter-VLAN Routing: To enable communication between different VLANs, a router or Layer 3 switch is required for routing between the VLANs. This is typically done by configuring subinterfaces on a router or enabling routing on a Layer 3 switch.
Common VLAN Configuration Issues
While VLAN configuration is straightforward, there are several common challenges that can arise:
- VLAN Mismatch: Ensure that the VLAN IDs match on both ends of the trunk link. If VLANs are not properly configured on both switches, traffic may not flow correctly.
- Port Misassignment: Double-check that all necessary ports are assigned to the correct VLAN. Misassigning a port can lead to network connectivity issues.
- Routing Problems: If inter-VLAN communication is not working, verify that routing is enabled on the correct device and that subinterfaces or Layer 3 switches are correctly configured.
Proper VLAN configuration helps improve the overall efficiency, security, and management of a network. Understanding how to assign VLANs, use trunking, and enable inter-VLAN routing is essential for network optimization and problem-solving.
Configuring Switches for Optimal Performance
Proper configuration of switches is essential for ensuring that your network operates efficiently, with minimal downtime and maximum throughput. Switches serve as the backbone of many networks, connecting devices and enabling communication. Configuring switches correctly can improve network speed, reduce collisions, and help avoid potential security vulnerabilities. Understanding the key configuration settings is important for optimizing switch performance and maintaining a reliable network environment.
In this section, we will explore several essential techniques for configuring switches to ensure optimal performance. These methods focus on enhancing network efficiency, ensuring proper security measures, and improving traffic management across the network.
Basic Switch Configuration for Performance
The initial setup of a switch lays the foundation for its performance. Here are some critical configuration steps:
- Assign a Hostname: Naming the switch helps with network management and troubleshooting. Use the
hostnamecommand to assign a unique name to each switch. - Configure Management IP Address: To access the switch remotely, assign an IP address to the VLAN interface using the
interface vlan 1command followed byip address [IP address] [subnet mask]. - Enable Remote Access: For remote management, enable SSH or Telnet. Use the
ip domain-nameandcryptocommands to set up SSH. - Disable Unused Ports: Disable ports that are not in use to prevent unauthorized access and reduce the risk of security breaches. Use the
shutdowncommand on inactive interfaces.
Advanced Switch Configuration for Performance Optimization
Once the basic configuration is in place, the next steps focus on optimizing switch performance, enhancing security, and improving network reliability:
- VLAN Configuration: Dividing the network into VLANs improves traffic management by segmenting broadcast domains. Use the
vlan [VLAN ID]command to create and assign VLANs to ports. - Spanning Tree Protocol (STP): Enabling STP prevents network loops and ensures redundancy in case of link failures. Use the
spanning-treecommand to configure STP on the switch. - Port Security: To prevent unauthorized devices from connecting, enable port security by limiting the number of MAC addresses on each port using the
switchport port-securitycommand. - Trunking Configuration: When connecting multiple switches, enable trunking to carry multiple VLANs over a single link. Use the
switchport mode trunkcommand for this configuration. - Quality of Service (QoS): QoS ensures that critical traffic, such
Tricks for Troubleshooting Network Issues
Network issues can disrupt communication and hinder productivity, making it essential to identify and resolve problems quickly. Whether it’s a slow connection, a device not connecting, or packet loss, troubleshooting requires a structured approach to identify the root cause. By using the right methods and tools, network problems can be efficiently diagnosed and fixed.
This section highlights effective troubleshooting techniques and strategies to help you resolve network issues, from basic connectivity problems to more complex configurations. A systematic approach combined with key tools and commands can make all the difference when diagnosing network faults.
Key Troubleshooting Steps
To solve network problems efficiently, follow these troubleshooting steps:
- Check Physical Connections: Ensure that all cables, switches, routers, and devices are properly connected. Look for loose cables or damaged ports that might cause connectivity problems.
- Verify IP Configuration: Ensure that devices have the correct IP address, subnet mask, and default gateway. Use the
ipconfig(Windows) orifconfig(Linux) command to check the settings. - Ping Test: Use the
pingcommand to test connectivity between devices. Start by pinging the local device, then move on to other network devices to isolate where the problem lies. - Trace the Route: Use the
traceroutecommand to track the path data takes across the network. This helps identify any delays or bottlenecks along the way. - Check DNS Settings: If devices can’t resolve domain names, check the DNS server settings. You can use the
nslookupcommand to troubleshoot DNS issues.
Advanced Troubleshooting Commands
For more advanced network troubleshooting, use the following commands to dig deeper into network issues:
Command Description show ip interface briefDisplays the status of all interfaces on a router or switch, including IP address, interface state, and whether the interface is up or down. show running-configDisplays the current configuration of a device, which can be useful to check for misconfigurations. show arpShows the Address Resolution Protocol (ARP) table, helping to verify the relationship between IP addresses and MAC addresses on the network. clear countersResets the interface counters, which can be useful for monitoring traffic after addressing a potential issue. debugEnables real-time debugging of various protocols. Be cautious when using it, as it can generate a lot of output. These commands give network administrators valuable insights into device configurations, interface statuses, and data paths. The right combination of these commands will quickly highlight where issues exist in your network and guide you toward an effective solution.
By following these troubleshooting steps and using the appropriate tools, you can quickly identify and resolve network issues. Effective troubleshooting not only improves network performance but also reduces downtime and enhances user experience.
Preparing for Simulation-based Exam Tasks
Simulation-based tasks in networking assessments require you to apply theoretical knowledge to real-world scenarios. Unlike multiple-choice questions, these tasks test your ability to configure devices, troubleshoot network issues, and implement solutions in a virtual environment. To perform well, you need not only technical skills but also the ability to think critically and adapt quickly to evolving challenges.
This section offers guidance on how to effectively prepare for simulation tasks. By focusing on key skills and adopting a strategic approach to practice, you can increase your confidence and performance in these hands-on assessments.
Focus on Core Network Concepts
Before diving into simulation-based tasks, ensure you have a solid understanding of core networking principles. These concepts will be essential as you configure devices, troubleshoot network problems, and design solutions:
- IP Addressing: Understand subnetting, IP address classes, and how to assign and configure IP addresses on devices.
- Routing and Switching: Know the basics of routing protocols, VLANs, trunking, and switch configurations.
- Network Security: Be familiar with basic security measures, such as ACLs, firewall rules, and securing network devices.
- Wireless Configuration: Learn how to configure wireless settings, including SSIDs, encryption types, and authentication methods.
Practice Using Simulation Software
Simulation software is a critical tool in preparing for practical assessments. Tools like GNS3, Packet Tracer, and Boson NetSim allow you to practice configuring networks in a controlled, virtual environment. Here’s how to make the most of these tools:
- Build Realistic Scenarios: Set up networks that mimic real-world situations, such as creating VLANs, configuring routing protocols, and setting up firewalls.
- Use Timed Simulations: Practice completing tasks within a set time frame to simulate the pressure of an actual assessment.
- Test Troubleshooting Skills: Create network issues and practice resolving them. For example, simulate connectivity problems or misconfigured IP settings.
Work on Configurations and Commands
Simulation-based tasks often involve running specific commands to configure devices. Ensure you are comfortable with common configuration commands for routers, switches, and other network devices. Here are some essential commands to master:
- Router Configuration: Familiarize yourself with commands for setting up routing protocols (e.g.,
router ospf,router eigrp) and managing interfaces (e.g.,interface g0/1,ip address). - Switch Configuration: Learn commands to create VLANs, configure trunk links (
switchport mode trunk), and implement security measures like port security. - Network Troubleshooting: Be prepared to use commands such as
ping,traceroute, andshow ip interface briefto identify and fix problems.
By preparing with a combination of theoretical knowledge and hands-on practice, you will be well-equipped to tackle simulation-based tasks. Each task provides an opportunity to strengthen your problem-solving skills and gain experience with real-world networking scenarios.
How to Manage Time During the Exam
Time management is a critical factor when facing any kind of assessment, especially in a task-based setting where every minute counts. Balancing speed with accuracy can be challenging, but with the right strategies, you can maximize your performance and ensure you complete all tasks effectively. This section will explore proven techniques to help you manage your time efficiently during such assessments.
The key to successful time management lies in preparation and approach. By prioritizing tasks, staying focused, and using the right tools, you can work through the assessment without unnecessary stress. Below are some strategies to help you stay on track and make the most of the available time.
Set Priorities and Focus on Key Tasks
It is essential to prioritize tasks based on their complexity and point value. Here’s how you can approach this:
- Read the Instructions Carefully: Before diving into the tasks, take a moment to read all instructions thoroughly. This helps you avoid mistakes caused by misunderstandings.
- Identify Easy Wins: Start with tasks that are straightforward and require less time. Completing these first will give you confidence and secure points early in the assessment.
- Allocate Time for Difficult Tasks: For more complex problems, estimate how long each will take and stick to that time frame. If you encounter difficulties, move on and return to it later if time permits.
Use Time-efficient Techniques
In addition to prioritizing tasks, applying time-efficient techniques can make a big difference:
- Practice Time-Management in Simulations: Before the assessment, use simulation software to practice completing tasks within a set time. This will help you get accustomed to working under pressure.
- Break Down Tasks: If a task seems overwhelming, break it down into smaller, manageable steps. Completing one step at a time can prevent feeling overwhelmed and save time in the long run.
- Use Shortcuts and Commands: Familiarize yourself with essential commands and shortcuts that can help speed up configuration and troubleshooting tasks.
By implementing these strategies, you can approach each task methodically, reduce stress, and ensure that you make the most of the available time.
Studying Advanced Routing Techniques
Mastering advanced routing techniques is crucial for building efficient, scalable networks. These techniques go beyond basic routing and address complex scenarios where optimal routing paths and resource management are essential. Understanding how to configure, troubleshoot, and optimize advanced routing protocols is key to ensuring network reliability and performance.
This section explores essential advanced routing strategies that every networking professional should study. By gaining in-depth knowledge of these techniques, you can prepare yourself for tackling intricate routing challenges and improving network performance in real-world environments.
Understanding Routing Protocols in Depth
Advanced routing relies heavily on understanding and configuring sophisticated routing protocols. These protocols help determine the most efficient paths for data across a network. Some of the most commonly used routing protocols include:
- OSPF (Open Shortest Path First): A link-state routing protocol that efficiently handles large networks and provides faster convergence times compared to older protocols.
- EIGRP (Enhanced Interior Gateway Routing Protocol): A hybrid routing protocol offering the benefits of both distance-vector and link-state protocols, ideal for larger networks with high scalability needs.
- BGP (Border Gateway Protocol): The standard exterior gateway protocol used for routing between autonomous systems, commonly applied in internet backbone routing.
Implementing Route Summarization and Redistribution
When dealing with complex networks, route summarization and redistribution are essential techniques for optimizing routing tables and reducing network overhead.
- Route Summarization: This technique allows you to condense multiple network routes into a single, summarized route, thereby reducing the size of routing tables and improving performance.
- Route Redistribution: When multiple routing protocols are used in a network, redistribution allows the routes learned by one protocol to be shared with another, ensuring consistent routing information across all devices.
Studying these advanced routing techniques will provide you with the knowledge needed to configure and maintain robust, efficient networks. The ability to implement these strategies effectively will also set you apart as a skilled network engineer capable of handling complex routing scenarios.
Packet Tracer Exam Question Formats
When preparing for a network configuration assessment, it’s crucial to understand the different formats in which questions might be presented. These assessments test your practical skills, requiring you to configure devices, troubleshoot network issues, and solve real-world problems. Knowing the various question types helps you manage time, allocate resources, and approach tasks more effectively during the assessment.
This section will provide an overview of common question formats you may encounter during hands-on networking assessments. Understanding these formats allows you to better prepare and respond efficiently to each type of challenge.
Configuration Tasks
Configuration-based questions require you to set up and configure network devices to meet specific requirements. These questions may involve:
- Device Configuration: Setting up routers, switches, and other network devices with correct IP addresses, routing protocols, and security settings.
- VLAN Configuration: Implementing VLANs and trunking on switches to segregate network traffic based on different requirements.
- Routing Protocols: Configuring protocols like OSPF or EIGRP to enable communication between routers and ensure network optimization.
Troubleshooting Tasks
Troubleshooting questions present network problems that require quick identification and resolution. Common troubleshooting tasks include:
- Connectivity Issues: Identifying and fixing issues such as misconfigured IP addresses, broken links, or incorrect subnet masks that prevent devices from communicating.
- Protocol Errors: Diagnosing problems related to routing or switching protocols, such as routing loops or incorrect VLAN assignments.
- Security Problems: Troubleshooting security-related issues such as unauthorized access or incorrect access control list (ACL) configurations.
Being familiar with these question types will help you approach the assessment with a clear plan. Practice with a variety of configuration and troubleshooting scenarios to ensure you are ready to tackle any task that comes your way.