
Ensuring compliance with privacy and security standards in the healthcare sector is essential for professionals. Understanding the foundational principles and regulations that protect sensitive patient data is crucial. Achieving proficiency in these standards often requires passing assessments designed to test knowledge and application in real-world scenarios.
Throughout this guide, we will explore the best strategies for navigating these assessments, offering insights into key areas and common pitfalls. Whether you’re looking to solidify your understanding or aiming to improve your performance, this resource will help you approach certification with confidence.
Preparation is key, and with the right resources and techniques, mastering the material becomes a manageable task. With detailed explanations and practical examples, we’ll cover the core areas you need to understand for success in the healthcare compliance landscape.
Healthcare Compliance Certification Success
Mastering the essential regulations that protect patient data is a key component for professionals in the healthcare field. Whether you’re seeking to validate your knowledge or aiming for certification, understanding the key principles and best practices is crucial. Achieving proficiency requires both theoretical knowledge and the ability to apply that knowledge in real-life situations. This section will guide you through effective methods for approaching the certification assessment and improving your results.
Success in this process is more than memorizing facts. It requires a clear understanding of privacy and security requirements, as well as the ability to apply those standards in various scenarios. Here are some important factors to consider when preparing:
- Familiarity with key regulations and their impact on healthcare operations
- Ability to identify sensitive data and ensure its protection
- Awareness of common compliance challenges faced by healthcare providers
- Understanding how breaches occur and the necessary steps for reporting
One of the most effective ways to prepare is by taking practice assessments. These can help familiarize you with the structure of the questions and the types of issues you will encounter. Practice tests also offer insight into areas that may require further study, allowing you to focus on the most challenging topics.
In addition to practice questions, here are some tips for achieving optimal results:
- Review official guidelines and case studies to understand real-world applications.
- Study the policies related to confidentiality, security, and patient rights.
- Focus on regulatory requirements related to data breaches and reporting procedures.
- Take time to understand the enforcement mechanisms and penalties for non-compliance.
By following these strategies, you’ll be well-equipped to succeed in the certification process, ensuring you meet the necessary standards for healthcare data privacy and security.
What is Healthcare Privacy and Security Education?
Ensuring the confidentiality, integrity, and availability of sensitive patient information is a core responsibility for healthcare professionals. This type of education focuses on equipping individuals with the necessary knowledge to handle patient data in compliance with legal and ethical standards. It emphasizes understanding key regulations and procedures designed to protect personal health information and maintain privacy in various healthcare settings.
Key Topics Covered
The primary goal of this educational process is to instill a deep understanding of privacy and security principles. Topics typically covered include:
- Confidentiality and safeguarding patient data
- Understanding the legal requirements for data protection
- Handling and disposing of sensitive records
- Identifying and responding to potential breaches or security threats
Why is it Essential?
Healthcare professionals must be well-versed in these standards to avoid potential violations and ensure patient trust. Non-compliance with these regulations can lead to severe legal and financial consequences. Therefore, the education is not only a requirement but also an essential part of fostering a secure and ethical healthcare environment.
Why Pass the Certification Assessment?
Successfully completing a certification assessment in healthcare privacy and security is essential for professionals working with sensitive patient data. It demonstrates a thorough understanding of the regulations and procedures designed to protect personal health information. Passing this assessment not only ensures compliance but also enhances career opportunities and professional credibility.
Achieving certification provides a clear indication to employers and patients alike that an individual is well-equipped to handle data securely and ethically. It also reinforces trust in healthcare systems, which are increasingly reliant on secure information management. Furthermore, for those seeking career advancement, completing the certification can open doors to higher-level positions, leadership roles, and increased responsibilities within healthcare organizations.
Key Concepts of Healthcare Privacy and Security Compliance
Understanding the fundamental principles behind data protection and confidentiality is essential for anyone working in the healthcare industry. The core concepts of compliance revolve around safeguarding sensitive patient information, ensuring its confidentiality, and adhering to regulations that govern its use and disclosure. These principles are designed to prevent unauthorized access and misuse of health records while promoting trust in the healthcare system.
Confidentiality is a cornerstone of compliance. It involves ensuring that personal health information remains private and is only shared with authorized individuals under specified conditions. This extends to both digital and physical records, with strict protocols in place to manage and protect data throughout its lifecycle.
Security measures are equally critical. These include both physical safeguards, like secure access to records, and technical safeguards, such as encryption and secure networks. The goal is to protect information from unauthorized access, alteration, or destruction, whether intentional or accidental.
Another essential aspect of compliance is the right to access, which allows patients to review and request corrections to their health records. This right is vital for maintaining transparency and ensuring the accuracy of personal health information.
Finally, it’s important to understand the procedures surrounding breach notification. When a data breach occurs, healthcare organizations must inform affected individuals and regulatory authorities within a set time frame, outlining the nature of the breach and steps being taken to mitigate its impact.
Common Mistakes in Healthcare Compliance Assessments
While preparing for certification assessments related to healthcare privacy and security, many individuals encounter challenges that can affect their performance. Understanding and avoiding these common mistakes is crucial for achieving success. These errors often stem from misunderstanding key concepts, misinterpreting questions, or failing to apply knowledge in practical scenarios.
Misunderstanding Regulations
One of the most frequent mistakes is a lack of clarity regarding the regulations that govern patient data protection. Many candidates confuse the different rules that apply to various types of health information, leading to incorrect responses. It’s essential to understand not only the specific requirements of each regulation but also the broader context in which they apply to healthcare operations.
Overlooking Practical Application
Another common error is focusing too much on theoretical knowledge without considering how it applies in real-world situations. Many questions require an understanding of how to respond to practical scenarios involving patient data management, security breaches, and confidentiality. Failing to think critically about these situations can lead to missed answers.
By avoiding these common mistakes and focusing on both theoretical and practical knowledge, individuals can significantly improve their chances of success in the certification process.
Privacy Rule Explained
The Privacy Rule establishes key guidelines for the protection of personal health information within the healthcare system. This regulation aims to ensure that sensitive patient data remains confidential and is only shared in accordance with strict standards. It governs how healthcare providers, insurers, and other entities handle, store, and transmit private information, with the primary focus on limiting unauthorized access and misuse.
At the core of the Privacy Rule is the concept of patient consent, which empowers individuals to control who can access their personal health records. The rule requires healthcare organizations to obtain explicit consent before disclosing any personal health information, except in certain circumstances, such as for treatment or legal compliance. In addition, the Privacy Rule mandates that patients have the right to access their health records and request corrections if needed.
Another important aspect of the Privacy Rule is the implementation of security safeguards to protect data from unauthorized access, both electronically and physically. Healthcare entities must ensure that appropriate administrative, technical, and physical measures are in place to safeguard the privacy of health information throughout its lifecycle.
Understanding the Security Rule
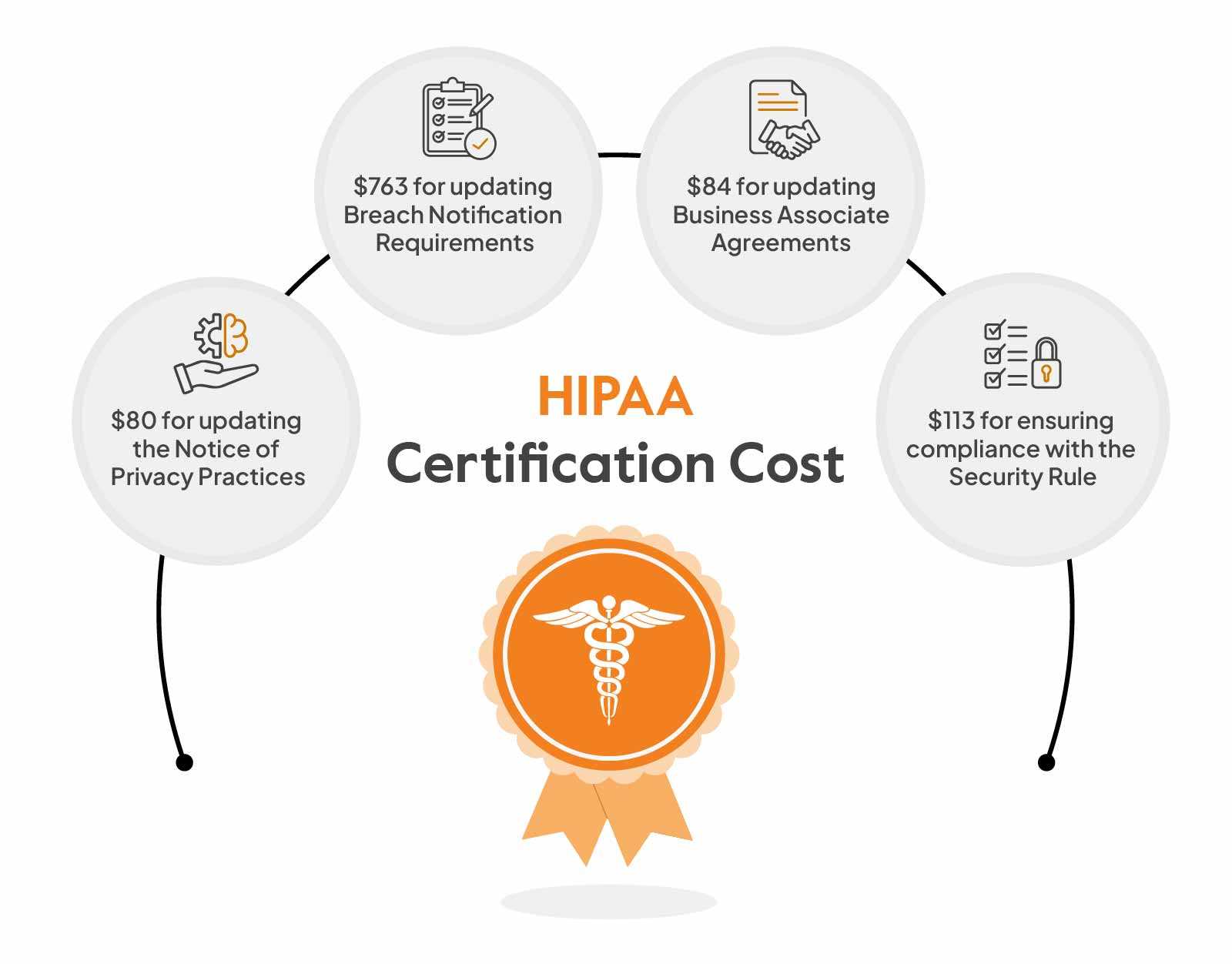
The Security Rule establishes a framework to protect sensitive patient information stored and transmitted electronically. It outlines the requirements for healthcare organizations to implement appropriate measures to prevent data breaches, unauthorized access, and cyber threats. This regulation is designed to ensure the confidentiality, integrity, and availability of electronic health information throughout its lifecycle.
Key Components of the Security Rule

The Security Rule is built around three main principles, often referred to as the CIA Triad: confidentiality, integrity, and availability. These principles guide organizations in their approach to securing health data.
- Confidentiality: Ensuring that only authorized individuals can access sensitive information.
- Integrity: Protecting data from unauthorized alteration or destruction.
- Availability: Ensuring that health information is accessible to authorized users when needed.
Safeguards and Best Practices
To comply with the Security Rule, healthcare organizations must implement both administrative and technical safeguards to protect patient data. Administrative safeguards include policies and procedures that define how data should be handled, while technical safeguards focus on the use of technology to secure data. Examples of these measures include encryption, access control systems, and regular risk assessments.
Healthcare entities must also ensure that all employees are properly trained on security protocols and procedures. Regular audits and monitoring are essential to ensure compliance and address any vulnerabilities that may arise.
Impact of Violating Privacy and Security Guidelines
Failure to adhere to established privacy and security guidelines can have severe consequences for healthcare professionals and organizations. Violations not only compromise the trust patients place in their healthcare providers but can also result in significant legal, financial, and reputational damage. Understanding the potential impacts of non-compliance is essential for maintaining the integrity of healthcare systems and safeguarding patient information.
When privacy and security regulations are violated, the outcomes can range from financial penalties to criminal charges. Here are some of the most common consequences:
- Financial Penalties: Organizations may face substantial fines, often in the millions of dollars, depending on the severity of the violation.
- Reputation Damage: Public disclosure of a breach can damage the reputation of healthcare providers, eroding patient trust and loyalty.
- Legal Action: Violations can result in lawsuits, either from affected individuals or government regulators, leading to costly settlements or judgments.
- Criminal Charges: In cases of intentional or egregious misconduct, individuals may face criminal charges, including imprisonment.
Additionally, organizations found to be non-compliant may be subject to increased scrutiny and audits from regulatory bodies, further complicating operations. For employees, being involved in a violation can lead to disciplinary actions, including termination and loss of professional certifications.
In sum, non-compliance with privacy and security rules can have far-reaching effects, not only for the individuals directly involved but also for the broader healthcare system. It’s essential to take every precaution to prevent violations and ensure that sensitive patient information remains protected at all times.
How to Prepare for the Certification Assessment
Successfully preparing for a certification assessment in healthcare data privacy and security requires a strategic approach that focuses on understanding key concepts and applying them to real-world scenarios. Thorough preparation is essential for mastering the material and ensuring that you’re ready to meet the requirements of the assessment. By following a structured study plan, you can increase your chances of success.
Begin by reviewing all the core topics outlined in the certification guidelines. Familiarize yourself with the relevant regulations, best practices for data management, and the security protocols that protect patient information. Pay special attention to any areas where you might feel less confident, as these will require additional focus.
Practical Application is critical for demonstrating your understanding of how privacy and security rules are implemented in everyday healthcare settings. Be sure to consider how these concepts apply in various scenarios, such as managing health records, handling sensitive data, and responding to security incidents. Practice by using case studies or example questions to test your knowledge.
Another essential preparation step is to take practice assessments. These mock tests simulate the actual assessment experience, helping you become familiar with the format and timing. They also provide insight into the types of questions you may encounter and allow you to pinpoint areas that require further study.
Stay organized throughout your study process. Create a timeline that includes specific goals for each study session and allow enough time to review all necessary materials before the assessment. Don’t forget to get plenty of rest before the day of the test to ensure that you are mentally sharp and focused.
Top Tips for Certification Success
Achieving success in a certification assessment, especially one focused on healthcare data protection, requires more than just knowledge–it demands careful preparation, strategic study habits, and a focused mindset. By adopting a few key practices, you can improve your performance and boost your confidence as you approach the test.
1. Understand the Core Concepts
Ensure you have a solid grasp of the fundamental principles related to privacy, security, and confidentiality in healthcare. Focus on understanding the core regulations and how they apply in real-world scenarios. This deeper understanding will help you not only recall facts but also apply them effectively during the assessment.
2. Practice Regularly
Consistent practice is crucial. Utilize practice questions and mock assessments to familiarize yourself with the format of the test and identify areas where you need improvement. The more you practice, the more comfortable you’ll be when faced with challenging questions.
3. Break Down Study Sessions
Don’t try to cram all your studying into one long session. Break your study time into manageable chunks with frequent breaks. This approach improves focus and retention, allowing you to absorb information more effectively.
4. Stay Organized
Keep track of important deadlines and set clear, achievable goals for each study session. Organizing your study materials and sticking to a structured study schedule will help you stay on track and reduce last-minute stress.
5. Take Care of Your Well-Being
A healthy body and mind are essential for peak performance. Make sure you’re getting enough sleep, eating well, and managing stress in the days leading up to the assessment. Exercise and relaxation techniques can help improve focus and reduce anxiety.
By following these tips, you’ll be well on your way to passing your certification with confidence and success.
Documentation Requirements for Healthcare Privacy and Security
Maintaining proper records is a critical aspect of ensuring compliance with privacy and security standards in healthcare. Accurate documentation not only demonstrates adherence to regulations but also provides an essential framework for managing sensitive information. The right documents can help organizations protect patient data and avoid costly violations.
Key Documentation Areas
There are several key areas where proper documentation is required to maintain privacy and security standards. These include:
- Policies and Procedures: Organizations must have clear, written policies outlining how they protect patient information and respond to potential breaches. These should be reviewed and updated regularly.
- Training Records: All personnel who handle patient data must undergo appropriate training, and organizations must document training sessions, including topics covered and employee participation.
- Incident Reports: Any incidents involving potential breaches or security risks should be documented, including the steps taken to mitigate the issue and prevent future occurrences.
- Access Logs: Detailed records of who has accessed sensitive data and when are essential for maintaining transparency and tracking any unauthorized access attempts.
Retention and Access
It’s crucial to ensure that all documentation is retained for the required length of time as specified by applicable laws and regulations. In addition, these records must be accessible for audit purposes, allowing organizations to demonstrate their commitment to maintaining the highest standards of patient confidentiality and security.
By keeping comprehensive and up-to-date documentation, organizations not only ensure compliance but also strengthen their overall data management practices. Proper documentation is a key component of a well-rounded approach to patient privacy and protection.
Real-Life Scenarios and Solutions

In the realm of healthcare data protection, practical situations often arise where understanding and applying privacy and security protocols is essential. These real-world challenges provide valuable lessons in how to handle sensitive information properly and prevent violations. By exploring different scenarios and examining effective solutions, individuals and organizations can better prepare for managing privacy risks and ensuring compliance.
Scenario 1: Unauthorized Access to Patient Information
Imagine a situation where an employee inadvertently accesses a patient’s confidential data without a legitimate reason. This could occur when a staff member accesses a file out of curiosity or due to a lack of clear access restrictions.
Solution: Organizations must ensure that all staff members are trained on the appropriate procedures for accessing patient records. Access should be restricted to authorized personnel only, and audit logs should be regularly reviewed to detect any unauthorized access. In case of a breach, the organization must follow its incident response protocol, including notifying affected individuals and taking corrective measures to prevent future occurrences.
Scenario 2: Breach of Confidentiality During Communication

Another scenario involves an employee accidentally sharing patient details in an unsecured email or while speaking in a public area where others could overhear the conversation. This could result in a breach of confidentiality if sensitive information is disclosed improperly.
Solution: Organizations should implement secure communication channels, such as encrypted emails, and enforce policies regarding the sharing of sensitive information. Employees should be trained on the importance of confidentiality and instructed to use discretion when discussing patient details, especially in public or semi-public spaces. Additionally, reviewing communication protocols regularly can help prevent such incidents from occurring.
By addressing these and other potential challenges with well-established policies and solutions, healthcare organizations can significantly reduce the risk of privacy violations and maintain compliance with regulations. Real-life scenarios offer practical insights that enhance the ability to manage sensitive data effectively.
Using Practice Tests for Better Results
One of the most effective methods for ensuring success when preparing for assessments in the field of healthcare data privacy and security is the use of practice tests. These tests offer a simulated experience of the real evaluation, helping individuals familiarize themselves with the format and type of questions that may appear. By incorporating practice assessments into the study routine, learners can identify their strengths and areas in need of improvement.
Benefits of Practice Tests
Practice tests provide numerous advantages for learners aiming to excel in privacy and security assessments:
- Improved Familiarity: Taking multiple practice tests helps individuals become accustomed to the structure and timing of the evaluation process, reducing anxiety on test day.
- Identifying Knowledge Gaps: By reviewing the answers to practice questions, learners can pinpoint topics they need to focus on and improve their understanding of key concepts.
- Building Confidence: Regular practice allows individuals to track their progress, boosting their confidence as they improve their performance over time.
- Reinforcing Learning: Repetition of test material reinforces concepts, ensuring better retention of important information.
How to Maximize Practice Test Effectiveness
To make the most of practice tests, consider the following strategies:
- Simulate Real Conditions: Take practice tests under timed conditions to mirror the actual testing environment. This helps build time-management skills.
- Review Mistakes: After completing each test, carefully review any incorrect answers to understand why they were wrong and learn from those mistakes.
- Focus on Weak Areas: Use the results of practice tests to focus your studies on areas where you are struggling, ensuring targeted improvement.
- Consistency: Incorporate practice tests regularly into your study routine to reinforce knowledge and track progress over time.
Incorporating practice assessments into your study plan can greatly enhance your ability to succeed. They provide valuable insights into your readiness and help ensure that you are well-prepared for the actual evaluation.
Dealing with Complex Questions
When facing intricate or multi-part questions, it’s essential to approach them with a clear and organized strategy. These types of questions often require careful analysis and critical thinking to break them down into manageable parts. Developing a systematic approach can help reduce confusion and increase the likelihood of selecting the correct response.
Step-by-Step Approach
To tackle complex questions effectively, follow these steps:
- Read the Question Carefully: Take time to fully understand what is being asked. Look for key terms that can guide you toward the correct answer.
- Identify Sub-questions: If the question contains multiple parts, break it down into smaller, more digestible components. This will help you address each part more thoroughly.
- Look for Clues: Often, the question itself will contain hints or details that can steer you toward the right answer. Pay attention to keywords and phrases.
- Eliminate Obvious Incorrect Options: If you encounter multiple-choice questions, eliminate the choices that are clearly wrong. This narrows down your options and increases your chances of selecting the correct one.
- Stay Focused: Avoid getting distracted by irrelevant information. Stick to the key points and stay focused on answering what is specifically being asked.
Handling Multi-Step or Scenario-Based Questions
For questions that present a scenario or require multiple steps to answer, use the following strategy:
- Understand the Context: Begin by identifying the main issue or challenge presented in the scenario. Focus on what is relevant and avoid unnecessary details.
- Break It Down: If the question asks you to apply knowledge in a sequence of steps, list them out in order. This will help you maintain clarity in your thought process.
- Consider the Implications: When scenarios involve decision-making or cause-and-effect, think about the possible outcomes of each action before selecting your response.
- Check Your Work: After choosing an answer, revisit the scenario to make sure it aligns with the details provided. Re-assess to confirm that the answer is the best fit.
By following these steps, you can confidently approach complex questions and increase your ability to select the correct answers. Practicing this approach will not only improve your accuracy but also enhance your problem-solving skills in high-pressure situations.
Understanding the Breach Notification Rule
In situations where sensitive data is compromised, it is essential for organizations to have clear procedures in place to inform affected individuals and authorities. This rule outlines the requirements for notifying individuals whose information has been exposed, as well as the steps that organizations must follow to maintain transparency and accountability in the event of a breach.
Key Components of the Breach Notification Rule
The following table outlines the key elements and timelines organizations must adhere to when a breach occurs:
| Action | Timeframe | Details |
|---|---|---|
| Notification to Affected Individuals | Within 60 days of discovery | Individuals must be notified in writing, including details about the breach and steps they can take to protect themselves. |
| Notification to the Secretary | Within 60 days of discovery | Organizations must report the breach to the appropriate government authority, including specific information about the incident. |
| Notification to the Media | If more than 500 individuals are affected | If the breach affects 500 or more people, public notification must be made to the media in the affected area. |
| Notification to Business Associates | Within 60 days of discovery | If a breach involves a business associate, they must also be notified promptly to ensure appropriate action is taken. |
Ensuring Compliance and Avoiding Penalties
Failure to comply with breach notification requirements can result in significant penalties and loss of trust from both individuals and regulatory bodies. To avoid these risks, organizations should regularly audit their data protection practices and ensure that all employees are trained on how to respond to breaches. Implementing a proactive breach detection and response strategy is essential for minimizing the impact of a data security incident.
Resources for HIPAA Training
Access to reliable and comprehensive learning materials is essential for anyone involved in maintaining compliance with privacy and security standards. These resources help individuals understand key regulations, enhance their knowledge, and apply practices that ensure the protection of sensitive information. Below are some valuable tools and platforms designed to support your educational needs in this area.
Online Courses and Webinars
Several platforms offer detailed courses and interactive sessions to help users grasp the nuances of data protection requirements:
- HealthIT.gov: This official site provides an array of resources, including free webinars, guidelines, and tutorials designed to explain the federal regulations on protecting patient data.
- Coursera: Offers comprehensive online courses developed by recognized institutions, giving learners flexibility to study at their own pace.
- Udemy: Features affordable, self-paced courses that cover everything from basic to advanced topics related to safeguarding private health information.
Guidelines and Official Documentation
For those seeking to study the core principles in depth, official documents provide a foundational understanding of the required standards:
- U.S. Department of Health & Human Services (HHS): The HHS website is the go-to place for accessing the full set of regulations, guidelines, and resources related to privacy protections and compliance procedures.
- National Institutes of Standards and Technology (NIST): NIST offers a detailed set of standards on information security, often referenced for securing sensitive data in various industries.
- State Resources: Many state health departments provide additional guidance, tools, and training materials to ensure compliance with both federal and state-specific privacy rules.
Books and Study Guides
Printed and digital study guides can be a useful resource for those who prefer to learn offline:
- The Complete HIPAA Compliance Guide: A comprehensive guidebook that covers everything from risk management to data protection strategies.
- HIPAA for Health Care Providers: An in-depth book specifically designed for medical professionals, focusing on practical compliance strategies.
- Self-Study Workbooks: Several publishers offer workbooks with quizzes and case studies to help individuals test their knowledge and apply what they’ve learned.
By leveraging these resources, individuals can ensure they are equipped with the necessary knowledge to uphold high standards of privacy and security in handling sensitive information. Regularly updating knowledge and staying informed about changing regulations is key to maintaining compliance and avoiding costly mistakes.
Post-Exam Steps and Certification

After completing the assessment, the next steps involve reviewing your performance, addressing any areas of weakness, and obtaining certification. These processes ensure that you not only understand the material but are also prepared to implement the knowledge in real-world situations. Here is an overview of what you can expect after finishing the evaluation.
Reviewing Results

Once the assessment is complete, reviewing the results is crucial for identifying both strengths and areas for improvement. Understanding which questions you answered incorrectly can help you focus on specific areas in the future:
- Analyze Incorrect Answers: Take the time to understand why you chose the wrong answers. This will give you insight into potential gaps in your knowledge.
- Seek Additional Resources: If necessary, refer to supplementary materials to clarify any concepts or regulations you may have missed.
- Consult with Experts: If you’re unsure about any topic, speaking with professionals or instructors can provide valuable clarification.
Certification Process
Once you’ve successfully passed the assessment, the next step is obtaining certification. This official recognition verifies that you have the knowledge required to meet the necessary standards and regulations. Below is a table summarizing the key steps in the certification process:
| Step | Description |
|---|---|
| 1. Submit Documentation | Submit proof of your completed assessment and any additional required documents to the certifying organization. |
| 2. Verification | The certifying body will verify your results and ensure all criteria have been met. |
| 3. Certification Issuance | Once your submission is verified, you’ll receive your official certification, confirming your proficiency in the subject matter. |
Upon successful certification, you’ll have the confidence to apply your knowledge in practice, knowing that you’ve met the required standards and are well-equipped for compliance and operational excellence.
Staying Updated on HIPAA Regulations
In any field involving sensitive information, remaining informed about the latest standards and legal requirements is essential for compliance. Regularly updating your knowledge ensures that practices remain aligned with evolving rules and minimizes the risk of non-compliance. Here’s how you can keep track of changes and stay current on the latest requirements.
- Subscribe to Industry Newsletters: Many organizations and professional bodies send out newsletters that highlight important updates and changes to legal standards. Subscribing to these sources helps you stay informed in real time.
- Participate in Webinars and Conferences: Attending events focused on privacy and security regulations is a great way to hear directly from experts, engage in discussions, and learn about new challenges and solutions.
- Join Professional Networks: Being part of a professional community provides access to valuable resources, including guidelines, workshops, and peer advice on the latest legal developments.
- Monitor Official Websites: Government sites and other official bodies regularly publish updates on legal requirements. Keeping an eye on these platforms ensures that you’re aware of any regulatory changes as soon as they occur.
By utilizing these resources, you can proactively adapt to shifts in regulations, ensuring both compliance and the protection of sensitive data in your practices.