Preparing for an essential assessment in the field of digital protection requires a clear understanding of key concepts and effective study methods. As technology evolves, the need for proficient professionals who can safeguard systems against various threats has never been greater. Whether you’re new to the field or looking to sharpen your skills, excelling in this evaluation is a crucial step towards building a strong foundation in security practices.
To succeed in this challenge, it’s important to focus on core topics such as threat detection, risk management, and protection protocols. Building knowledge around these fundamental areas will not only prepare you for the test itself but also equip you with the practical expertise necessary for real-world applications. Developing a strategic approach and reviewing critical materials will give you the edge you need to perform confidently.
Comprehensive preparation and smart study habits are key to navigating through complex scenarios and questions. With the right approach, you can successfully demonstrate your understanding and secure your place as a well-versed professional in the field of digital security.
Key Topics Covered in the Assessment
When preparing for this important evaluation, it’s essential to focus on a range of topics that are critical to understanding and managing digital security. The test covers various areas of knowledge, from basic principles of protection to more advanced concepts related to system vulnerabilities. Each topic is designed to assess your ability to recognize, analyze, and respond to potential threats in the digital environment.
Core Concepts of Digital Defense
One of the primary areas addressed is the foundational knowledge of protecting data and networks from unauthorized access or harm. Topics such as encryption, firewalls, and authentication protocols are often tested, as they form the core of any defense strategy. Understanding how these mechanisms work and their role in maintaining secure systems is key to success.
Identifying and Mitigating Risks

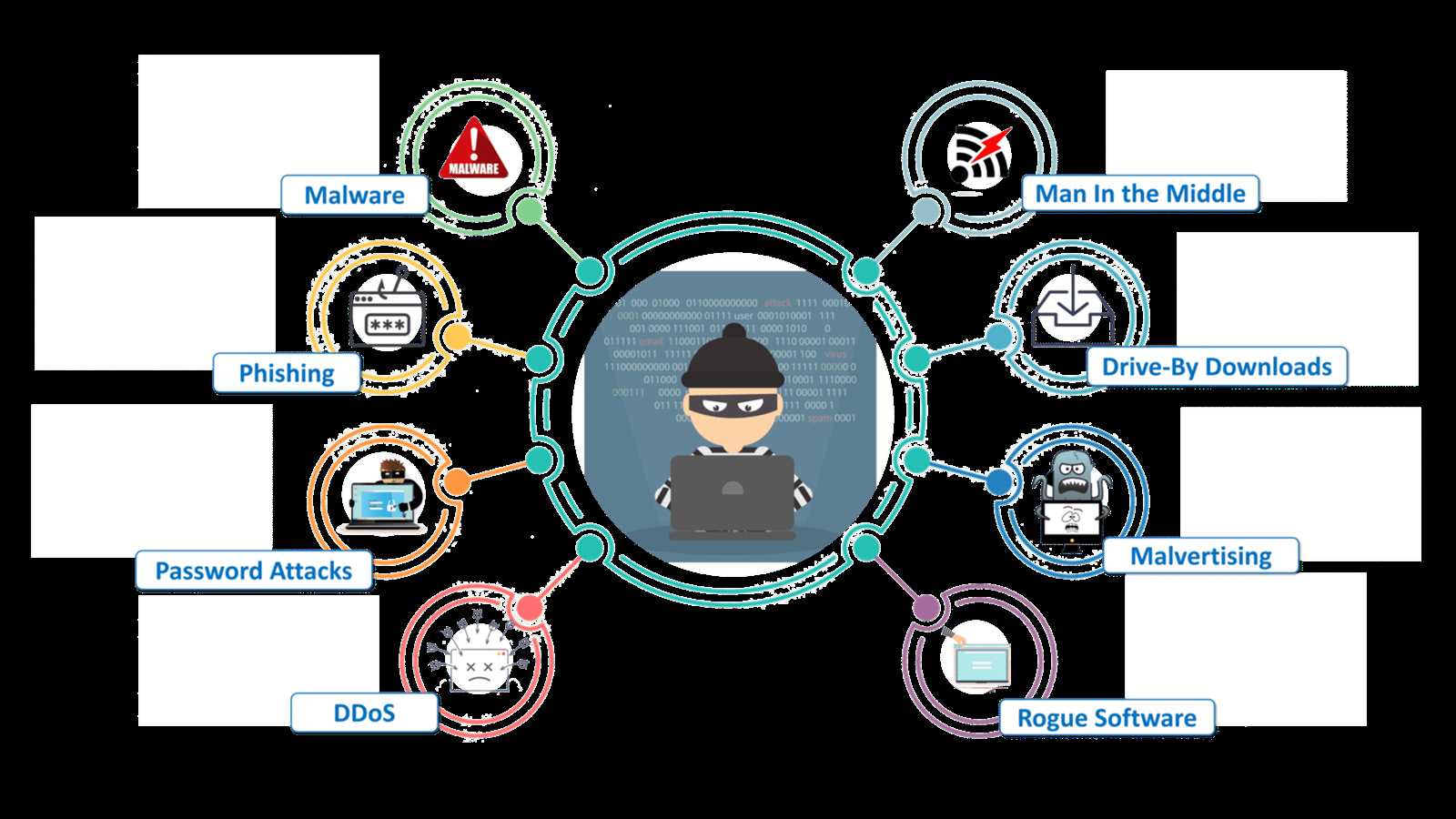
Another critical area of focus involves identifying potential threats and learning how to mitigate their impact. The ability to assess various types of risks, including malware, phishing, and social engineering attacks, is essential for creating a comprehensive defense strategy. Successful candidates will demonstrate their capacity to develop solutions for managing these risks and protecting valuable assets.
Mastering these key topics is crucial for anyone looking to excel in the field of digital security. Having a deep understanding of these areas not only helps in assessments but also ensures readiness for real-world challenges in securing systems and networks.
How to Prepare for the Digital Security Assessment
Preparing for a security-focused evaluation requires a well-structured approach that targets both theoretical knowledge and practical skills. Successful candidates understand the importance of grasping key concepts and familiarizing themselves with common scenarios in the field. A thorough review of essential topics combined with hands-on practice is critical to performing well in this assessment.
Start by reviewing the core principles of digital protection, including risk management, data integrity, and network security protocols. Be sure to explore real-world case studies and common security threats to gain a deeper understanding of how these concepts are applied. It’s important to not only memorize key facts but also to develop the analytical skills needed to solve complex problems.
Additionally, setting a study schedule and sticking to it will ensure consistent progress. Using resources such as practice tests, study guides, and online forums can help reinforce your knowledge and identify areas that require further attention. This combination of theory and practice will increase your chances of success when the time comes.
Common Challenges in the Test

As you prepare for a security evaluation, it’s important to anticipate the challenges you may face during the process. Many candidates struggle with particular areas that require not just memorization, but also the application of knowledge to real-world situations. Recognizing these common obstacles early on will help you better manage your time and approach to the assessment.
One of the primary difficulties lies in understanding the intricate details of certain security protocols and concepts. Another common challenge is applying theoretical knowledge to practical scenarios, which often require problem-solving skills under time pressure. Additionally, the variety of question types can catch many off guard, especially if you’re not well-prepared for complex, multi-step problems.
| Challenge | Description |
|---|---|
| Complex Terminology | Many questions use technical jargon that may be difficult to understand without in-depth study. |
| Scenario-based Questions | Applying theory to real-world situations can be challenging, especially with limited practical experience. |
| Time Constraints | Limited time can create pressure, making it difficult to think critically through each question. |
| Unfamiliar Topics | Some subjects may be covered in greater depth than expected, requiring extra focus during preparation. |
By preparing for these potential challenges and focusing your efforts on problem-solving and practical application, you can increase your confidence and improve your chances of success on the test.
Understanding Cybersecurity Fundamentals
To excel in any assessment related to digital protection, it is essential to have a strong grasp of the foundational principles. These principles form the basis for all advanced concepts and practices in the field, and they are crucial for effectively securing systems and networks against malicious activities. A clear understanding of the basic components of digital security will allow you to identify potential risks and apply suitable defense measures.
Core Principles of Protection
The core elements of digital defense include the confidentiality, integrity, and availability of information. These principles, often referred to as the CIA triad, serve as the foundation for designing robust security systems. Ensuring that data remains private, intact, and accessible only to authorized users is essential in safeguarding sensitive information.
Common Threats and Defense Mechanisms

It’s also important to be familiar with the most common threats that target digital systems. From viruses and malware to phishing attacks and denial-of-service breaches, understanding these risks helps in creating effective countermeasures. Protection strategies such as firewalls, encryption, and access control mechanisms are vital in defending against these persistent threats.
Mastering these basic concepts will give you the tools needed to approach more complex topics with confidence, setting a solid foundation for further study and practical application in the field of digital security.
What to Expect on the Test
When preparing for the assessment, it’s important to understand the structure and types of questions that will be presented. The test is designed to evaluate both your theoretical knowledge and your ability to apply concepts in real-world scenarios. By knowing what to expect, you can approach the evaluation with greater confidence and focus.
The content will primarily focus on key concepts, threat management, security protocols, and risk mitigation strategies. You’ll need to demonstrate your understanding of various defense mechanisms, identify potential vulnerabilities, and make informed decisions to secure digital systems.
| Section | What You’ll Face |
|---|---|
| Basic Concepts | Questions will cover fundamental principles like data protection, encryption, and authentication methods. |
| Threat Identification | Expect to analyze different types of risks, such as malware, phishing, and denial-of-service attacks. |
| Practical Scenarios | Some questions will present real-life situations where you must apply your knowledge to solve security issues. |
| Security Protocols | There will be questions testing your understanding of common defense tools like firewalls and access controls. |
Overall, the test is designed to assess your comprehensive understanding of the field. It is important to stay calm and approach each question methodically, using the knowledge you’ve gained through your preparation.
Important Concepts for Digital Protection
When preparing for an assessment in the field of digital security, it’s essential to understand the key concepts that form the backbone of the discipline. These concepts are vital not only for passing tests but also for effectively defending against digital threats in real-world environments. A strong foundation in these topics will help you navigate complex security challenges and develop comprehensive protection strategies.
Below are some of the core topics you should focus on when preparing for any digital defense evaluation:
- Risk Management: The ability to assess and manage risks is crucial for securing systems. This involves identifying potential vulnerabilities and implementing countermeasures to minimize potential damage.
- Network Security: Understanding how to protect networks from unauthorized access and attacks is fundamental. This includes knowledge of firewalls, intrusion detection systems, and network segmentation.
- Encryption and Authentication: These methods ensure that data remains confidential and is accessible only to authorized users. Understanding encryption techniques and authentication protocols is key to securing sensitive information.
- Malware and Threats: Being able to identify and mitigate threats such as viruses, ransomware, and phishing attacks is a critical skill. Knowing how these threats work and how to defend against them is vital in modern security practices.
- Compliance and Policies: Security policies, as well as legal and regulatory requirements, guide how organizations protect their data and systems. Familiarity with these guidelines is important for creating a secure environment.
Mastering these topics will give you a comprehensive understanding of digital protection, allowing you to confidently handle security tasks, whether on a test or in a professional setting. Make sure to allocate time to study each area thoroughly for the best results.
Tips for Passing the Digital Security Assessment
Successfully navigating a security-focused evaluation requires more than just understanding the material–it’s about effectively applying that knowledge under test conditions. While thorough preparation is key, there are several strategies that can improve your chances of success and help you stay focused during the assessment. By following these tips, you can approach the test with confidence and clarity.
Start by creating a study plan that covers all key topics. Allocate time to review both theoretical concepts and practical applications. The more you familiarize yourself with potential scenarios, the better you’ll be at tackling problem-solving questions. Practice with mock tests and quizzes to build your speed and accuracy, and assess areas where you need more focus.
On the day of the assessment, make sure you manage your time wisely. Read each question carefully, and don’t rush through any of them. If you’re unsure about a question, try to eliminate obviously incorrect answers and make an educated guess. If you get stuck on a question, move on and return to it later if time allows.
Stay calm and approach each question logically. Even if you’re faced with a challenging problem, break it down into smaller parts to identify the best solution. Remember that thorough preparation, combined with a calm mindset and strategic approach, is your best tool for success.
Cybersecurity Tools and Techniques Reviewed
Effective protection of digital systems requires the use of various tools and techniques that help safeguard data, prevent breaches, and mitigate risks. These instruments are essential for professionals looking to identify vulnerabilities and respond to security threats. Understanding the core tools and methods used in the field allows for better preparation and effective defense strategies.
Key Tools for Digital Defense
There are numerous tools available for securing systems and networks. Some of the most widely used include:
- Firewalls: These act as barriers between trusted networks and untrusted ones, helping prevent unauthorized access.
- Antivirus Software: Essential for detecting, quarantining, and removing malicious software that could compromise a system.
- Intrusion Detection Systems (IDS): These tools monitor network traffic for suspicious activities and alert administrators to potential threats.
- Encryption Tools: Used to convert sensitive data into unreadable formats, ensuring it remains protected even if intercepted.
Techniques for Threat Mitigation

In addition to tools, professionals must be proficient in various security techniques to respond to threats and minimize risks. Some critical methods include:
- Access Control: Restricting access to sensitive information based on user roles and permissions to prevent unauthorized usage.
- Network Segmentation: Dividing networks into smaller, isolated segments to limit the impact of a potential breach.
- Patch Management: Regularly updating software and systems to fix vulnerabilities and improve overall security.
- Threat Hunting: Proactively searching for signs of potential attacks and anomalies within networks before they cause harm.
By reviewing and mastering these tools and techniques, individuals can build a solid foundation for identifying and neutralizing threats in their systems, ensuring robust protection against malicious activities.
Questions You Should Focus On
When preparing for a security assessment, focusing on the right set of questions is crucial to success. Some topics and areas tend to appear more frequently and are central to the overall understanding of security principles. By targeting these key questions, you can ensure that your preparation is aligned with the most critical concepts and increase your chances of performing well.
The following areas are often emphasized and should be given extra attention during your study sessions:
- Risk Identification and Management: Be prepared to address how to identify, assess, and mitigate security risks. Understanding the risk management lifecycle is essential.
- Threat Landscape: Questions related to different types of digital threats, including malware, phishing, and social engineering, are common. Understand how to identify and respond to these threats.
- Security Policies and Protocols: You should focus on questions about security frameworks, compliance regulations, and protocols that help manage risks and secure systems.
- Network Defense Mechanisms: Expect to see questions about the implementation and configuration of firewalls, intrusion detection/prevention systems, and network monitoring tools.
- Encryption Techniques: A solid understanding of encryption methods, including symmetric and asymmetric encryption, is essential. Be prepared to answer questions about how and when to use these techniques.
- Incident Response and Recovery: Understand the steps involved in responding to a security breach, from detection to containment and recovery.
By reviewing these key areas and practicing related questions, you’ll be better equipped to handle the most common and challenging topics in the test. A focused approach will help you answer confidently and accurately.
Best Resources for Test Preparation
Effective preparation for a digital security assessment requires access to the right resources. These materials help deepen your understanding of the key concepts, sharpen your problem-solving skills, and ensure you are ready for any challenge. Whether you prefer textbooks, online platforms, or hands-on practice, a variety of tools can enhance your study sessions and help you feel confident going into the test.
Here are some of the most valuable resources to use when preparing for a security-focused evaluation:
- Official Study Guides: Comprehensive guides, often created by exam providers, are a great starting point. They cover all the essential topics and provide practice questions to test your knowledge.
- Online Learning Platforms: Websites like Udemy, Coursera, and LinkedIn Learning offer courses tailored to digital security certifications. These platforms often feature video tutorials, quizzes, and hands-on labs to reinforce key skills.
- Practice Tests: Taking practice tests under timed conditions helps you get used to the format of the questions and manage your time effectively during the real assessment.
- Books and Textbooks: Books such as “The Web Application Hacker’s Handbook” and “Security+ Guide to Network Security Fundamentals” provide in-depth knowledge on security principles and techniques. They are essential for building a strong foundational understanding.
- Community Forums and Study Groups: Online communities like Reddit or study groups on platforms like Discord allow you to connect with other candidates, share study tips, and discuss complex topics with peers.
- Labs and Simulations: Virtual labs and simulations allow you to practice real-world scenarios in a controlled environment. Platforms like TryHackMe and Hack The Box offer practical exercises that simulate security breaches and threat scenarios.
By leveraging a combination of these resources, you will be able to reinforce your knowledge and gain hands-on experience, which are crucial for performing well on any security assessment.
How to Study Effectively for Digital Security
Studying for a security-related assessment requires a focused and strategic approach. With a wide range of topics, from risk management to defensive techniques, it’s crucial to use efficient methods to absorb and retain the material. By organizing your study plan and incorporating diverse learning techniques, you can optimize your preparation and improve your performance.
Create a Structured Study Plan
The first step in effective preparation is to develop a clear and structured study plan. Break down the topics into manageable chunks and allocate time to focus on each one. Consider the following tips:
- Set Specific Goals: Identify key areas that require more attention and set achievable goals for each study session.
- Prioritize Key Topics: Focus on high-priority subjects that are frequently covered in the assessment, such as network security, threat identification, and risk management.
- Review Regularly: Make sure to revisit topics you have already covered to reinforce your understanding and ensure retention.
- Balance Theory and Practice: Combine theoretical study with hands-on practice to deepen your understanding and gain practical experience.
Use Active Learning Techniques
Active learning is proven to help you understand and remember concepts better. Incorporating different techniques can make your study sessions more engaging and effective. Consider using the following strategies:
- Practice with Simulations: Set up virtual labs or use simulation platforms to apply what you’ve learned in real-world scenarios.
- Teach Someone Else: Explaining complex topics to a peer or study group helps reinforce your own understanding and identify gaps in knowledge.
- Use Flashcards: Create flashcards for key terms, definitions, and processes to improve recall during your study sessions.
- Take Practice Quizzes: Regularly test yourself using online quizzes or practice exams to gauge your progress and get used to the format of the questions.
By applying these strategies, you can maximize your study efforts and ensure you’re fully prepared to tackle any challenge in a digital security assessment.
Understanding Cyber Threats and Solutions
In the realm of digital security, it’s essential to have a clear understanding of the various threats that exist and the effective measures that can be used to mitigate them. These threats can take many forms, from malware and phishing attacks to more sophisticated vulnerabilities that target critical systems. Recognizing the types of threats and knowing how to defend against them is fundamental to maintaining a secure digital environment.
Common Types of Digital Threats
There are several categories of threats that individuals and organizations face. Understanding these will help you identify potential risks and develop strategies to protect against them:
| Threat Type | Description | Common Targets |
|---|---|---|
| Malware | Software designed to harm or exploit any device or network, including viruses, worms, and ransomware. | Computers, mobile devices, networks |
| Phishing | A fraudulent attempt to obtain sensitive information by impersonating a trustworthy entity via email or other communication channels. | Individuals, organizations |
| Man-in-the-middle Attacks | An attack where a third party intercepts communication between two parties to steal or alter data. | Online communication, financial transactions |
| DDoS Attacks | Distributed denial-of-service attacks overload a system with traffic to disrupt its services. | Websites, online services |
Effective Solutions to Counter Threats
To protect against the growing array of threats, several defense techniques can be employed. These solutions are designed to safeguard networks, systems, and sensitive information:
- Firewalls: Firewalls serve as the first line of defense by monitoring and controlling incoming and outgoing network traffic based on predetermined security rules.
- Antivirus Software: Antivirus programs are essential for detecting and removing malicious software before it can cause harm to devices or networks.
- Encryption: Encrypting sensitive data ensures that even if intercepted, it cannot be read or misused by unauthorized parties.
- Multi-Factor Authentication: Adding layers of security beyond just passwords ensures that even if one factor is compromised, attackers cannot easily access critical systems.
- Employee Training: Educating employees about security best practices, such as recognizing phishing attempts, can significantly reduce human error and vulnerability.
By understanding the common threats and applying appropriate countermeasures, individuals and organizations can reduce the risk of a breach and enhance their overall security posture.
What the Cybersecurity Certification Tests
When preparing for a certification in the field of digital security, it is important to understand the key areas that the assessment will cover. The test is designed to assess a candidate’s knowledge and practical skills across a range of topics related to protecting systems and networks. The focus is on evaluating both theoretical understanding and the ability to apply security techniques to real-world scenarios.
Key Areas Tested
The following are the core topics typically tested in this type of certification, designed to ensure candidates are well-rounded in their security knowledge:
- Network Security: Understanding how to protect data and systems from unauthorized access through techniques like firewalls, VPNs, and network segmentation.
- Threat Management: Identifying and responding to common threats such as malware, ransomware, and phishing attacks.
- Access Control: Implementing strategies to manage and control user access to systems, ensuring only authorized users can access sensitive data.
- Incident Response: Developing the skills necessary to respond effectively to security breaches or attacks, including detection, containment, and recovery.
- Risk Management: Understanding how to assess and manage potential risks to systems and data through various methods such as vulnerability scanning and risk analysis.
- Security Architecture: Designing secure network infrastructures, ensuring that all aspects of the network are protected from internal and external threats.
Practical Skills Tested
In addition to theoretical knowledge, candidates will also be tested on their practical skills, such as:
- Configuring Security Devices: The ability to set up and configure devices like firewalls and intrusion detection systems (IDS) to secure networks.
- Implementing Encryption: The knowledge to apply encryption protocols to protect sensitive information during transmission or storage.
- Simulating Cyber Attacks: Creating and testing simulated attacks to assess the security posture of a system and identify potential vulnerabilities.
Overall, the certification aims to evaluate a candidate’s ability to think critically and act swiftly in addressing potential security challenges in a variety of environments.
Reviewing Past Papers for Success
One of the most effective strategies for mastering a certification is to review past assessments. This approach not only helps you understand the format of the questions but also allows you to identify recurring themes and concepts that are often tested. By practicing with previous papers, you can gauge your understanding of the material and improve your time management skills for the real test.
Why Reviewing Past Papers is Crucial
Going through past papers offers several key benefits:
- Familiarization with Question Types: You become familiar with the structure and style of questions, which helps reduce anxiety and boosts confidence.
- Reinforcement of Key Concepts: By repeatedly encountering certain topics, you reinforce your understanding and identify areas that need more attention.
- Improved Time Management: Practicing under timed conditions helps you learn how to manage your time effectively, ensuring that you complete the test within the allotted period.
- Identifying Weak Areas: Reviewing past papers helps pinpoint the topics where you need further revision, allowing you to focus your efforts more efficiently.
How to Maximize Your Review Sessions
Here are a few strategies to make the most of your past paper review sessions:
- Simulate Test Conditions: Practice answering the questions in a timed setting to simulate the real test environment. This helps you get accustomed to working under pressure.
- Analyze Mistakes: After completing a past paper, review the questions you answered incorrectly and understand why you made those mistakes. This will help you avoid repeating them in the future.
- Focus on High-Weight Topics: Pay extra attention to topics that have been frequently tested in previous papers. These areas are more likely to appear again and should be mastered thoroughly.
- Review Multiple Papers: To get a broader perspective, review several past papers to identify trends and patterns in the types of questions asked.
By integrating this approach into your study plan, you can build a strong foundation and increase your chances of success when taking the test.
Importance of Networking in Cybersecurity
In the modern digital landscape, understanding and managing networks is critical for protecting systems from potential threats. The ability to secure communication channels, detect vulnerabilities, and respond to attacks relies heavily on a deep knowledge of networking principles. Strong networking skills are essential for building robust defenses against unauthorized access, data breaches, and other malicious activities. This section will explore why a strong foundation in networking is crucial for professionals in the field of digital security.
Understanding Network Vulnerabilities
A well-designed network is essential for ensuring secure data exchange. However, vulnerabilities within the network can be exploited by attackers to gain unauthorized access to sensitive information. Understanding how different network protocols work and how attackers can target weak points is crucial for identifying and mitigating risks. Some key areas to focus on include:
- Firewalls: These are crucial barriers that prevent unauthorized access to or from private networks.
- Network Segmentation: By splitting networks into smaller segments, the impact of potential breaches can be minimized.
- Intrusion Detection Systems (IDS): These systems monitor network traffic for signs of malicious activity.
Building a Secure Network Infrastructure
Networking plays a fundamental role in building secure infrastructures. A secure network architecture not only defends against external attacks but also ensures the integrity of internal communications. Key principles for securing network infrastructures include:
- Encryption: Encrypting data transmission ensures that even if the network is compromised, sensitive data remains protected.
- Access Control: Defining and enforcing strict access policies ensures that only authorized users can access sensitive systems or data.
- Monitoring: Continuously monitoring network traffic and system logs can help detect