
In today’s rapidly changing landscape of information security, understanding the principles behind classifying sensitive material is essential. Properly labeling and handling protected data ensures compliance with legal standards and safeguards against unauthorized access. It is critical for professionals to be well-versed in these protocols to maintain the integrity of sensitive information.
Preparing for the assessment that tests your ability to correctly identify and manage various types of classified content requires a deep understanding of the underlying rules and regulations. Success in such evaluations relies not only on knowledge but also on the ability to apply these guidelines accurately in practical situations.
With new regulations and best practices constantly evolving, keeping up-to-date is crucial for passing these assessments. This guide will provide key insights and strategies to help you navigate the complexities of these tests and emerge successfully, ensuring your role in maintaining national security and regulatory compliance.
Derivative Classification Exam Overview

Understanding how to handle and label sensitive information correctly is a crucial skill in many professional fields. The assessment designed to test this knowledge evaluates a person’s ability to identify, interpret, and apply the rules governing the handling of protected material. Passing this evaluation ensures that individuals can effectively protect data from unauthorized disclosure while complying with regulatory standards.
Structure of the Assessment
The structure of this evaluation is carefully crafted to assess both theoretical knowledge and practical application. The test typically involves a series of scenarios where participants must determine how to properly mark and handle information based on given guidelines. It includes multiple-choice questions, practical exercises, and sometimes case studies that require real-world decision-making skills.
Skills Tested in the Evaluation
Key skills assessed during the test include the understanding of various legal frameworks, the correct application of marking procedures, and the ability to navigate complex classification systems. In addition to knowledge of the rules, candidates must demonstrate their ability to make informed decisions in situations where information might require different levels of protection. Mastering these concepts is essential for those working in sensitive government or corporate environments.
Key Concepts in Derivative Classification
To effectively manage sensitive information, it is essential to understand the fundamental principles that guide how material is handled and protected. These core concepts form the foundation of maintaining confidentiality and securing data in compliance with legal and regulatory standards. Understanding these principles ensures that individuals can correctly assess the sensitivity of information and apply appropriate protections when necessary.
Key Principles of Handling Sensitive Information

Several key ideas are critical when working with protected materials:
- Marking Requirements: Knowing when and how to label content to indicate its sensitivity level.
- Authorized Access: Ensuring that only individuals with proper clearance can access or distribute sensitive materials.
- Handling and Storage Guidelines: Following strict rules regarding the storage, sharing, and transmission of sensitive data.
- Legal and Regulatory Compliance: Adhering to the laws and rules governing the protection of classified information.
Challenges in Properly Handling Information
There are common difficulties individuals face when applying the principles of handling sensitive materials, including:
- Understanding the nuances of what constitutes sensitive information.
- Determining the correct level of protection needed for various types of material.
- Keeping up with changing regulations and standards related to information security.
- Ensuring consistency in the application of marking and handling procedures across different departments.
Exam Format and Structure for 2025

The assessment designed to test knowledge in handling sensitive information follows a clear structure aimed at evaluating both theoretical understanding and practical application. Participants are expected to demonstrate their ability to interpret rules, apply guidelines, and make decisions in scenarios involving the protection of classified materials. The structure of this evaluation ensures that it thoroughly tests all necessary skills while maintaining a focus on real-world applications.
Format of the Assessment
The evaluation is typically divided into multiple sections, each targeting specific areas of knowledge. It may include:
- Multiple-Choice Questions: Questions that test the participant’s understanding of key concepts and regulations.
- Practical Scenarios: Situational questions requiring decision-making based on real-life situations.
- Case Studies: In-depth analysis of hypothetical scenarios to assess the participant’s ability to apply rules to complex situations.
Time Allocation and Scoring
Participants are given a set amount of time to complete the assessment, with each section allocated a specific duration. Scoring is typically based on the accuracy of responses, with correct application of guidelines and regulations carrying more weight. Successful completion of the evaluation requires not only theoretical knowledge but also the ability to apply that knowledge correctly in practical contexts.
Common Topics Covered in the Exam
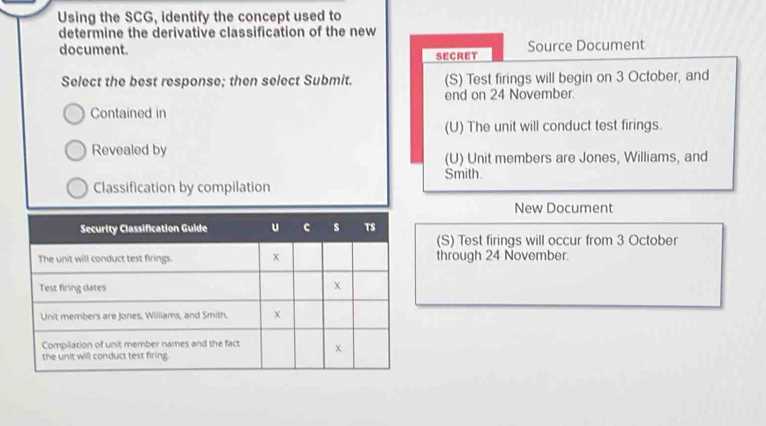
The assessment evaluates various critical areas related to the protection and handling of sensitive data. The topics are designed to ensure that individuals are equipped with the knowledge and skills necessary to correctly manage classified information. These areas are essential for maintaining compliance with legal and regulatory standards in environments that deal with sensitive material.
Some of the most commonly covered topics in the evaluation include:
- Security Markings: Understanding when and how to apply security labels and markings to materials based on their sensitivity.
- Handling Procedures: Correct protocols for storing, sharing, and transporting protected information.
- Access Control: Determining who can access sensitive data and under what circumstances, based on clearance and need-to-know principles.
- Legal Guidelines: Familiarity with laws and regulations governing the protection of classified materials and the consequences of non-compliance.
- Document Declassification: Processes involved in determining when and how to declassify information or change its sensitivity level.
These topics form the foundation of the knowledge required for successful completion of the assessment and are integral to maintaining secure handling practices in any field that deals with protected materials.
How to Prepare for the Test
Preparing for an assessment that evaluates your ability to handle sensitive information requires a focused approach. Success in the test depends on a solid understanding of the rules and regulations governing the protection of classified material. With proper preparation, you can develop the knowledge and skills needed to perform well and ensure compliance with security protocols.
Study Materials and Resources
To effectively prepare, it is essential to review all available study materials, including official guides, practice questions, and training modules. These resources provide valuable insights into the concepts covered in the test and help reinforce your understanding of the necessary procedures.
| Resource | Description |
|---|---|
| Official Guidelines | Review legal and regulatory documents that outline the handling procedures for sensitive materials. |
| Practice Tests | Take practice tests to familiarize yourself with the format and types of questions you may encounter. |
| Training Courses | Enroll in courses that provide in-depth knowledge of the principles and protocols related to data protection. |
Effective Study Techniques
In addition to reviewing study materials, adopting effective study techniques will help you retain information and perform well on the test. Consider using active recall, self-quizzing, and group study sessions to enhance your understanding. Practicing real-world scenarios can also improve your decision-making skills when applying security protocols.
Understanding Classification Markings
Properly labeling materials based on their sensitivity is a crucial part of information security. Understanding how to assign and interpret markings ensures that sensitive content is handled according to established protocols. These markings serve as clear indicators of the level of protection required and guide individuals in safeguarding critical data appropriately.
Types of Security Markings
There are several levels of protection that materials can be subject to, each requiring specific markings to indicate their sensitivity. The most common types of markings include:
- Top Secret: Used for highly sensitive material that could cause grave harm to national security if disclosed.
- Secret: Applied to information that could cause serious damage to national security if released.
- Confidential: Used for materials that could harm national security if exposed but to a lesser degree.
- Unclassified: Indicates information that does not require protection but still may be restricted under certain conditions.
How to Apply Markings Correctly
It is essential to apply markings correctly to ensure proper handling and protection. Follow these key steps:
- Evaluate Sensitivity: Assess the content to determine the appropriate protection level based on its impact if disclosed.
- Apply Markings: Mark the document, file, or material clearly with the correct security designation at the top or in a prominent location.
- Include Dissemination Instructions: If necessary, provide additional instructions regarding who can access or view the material.
- Review and Update: Regularly review and update markings to ensure they remain accurate based on any changes to the material’s status or sensitivity.
Rules for Derivative Classification
When working with sensitive information, it is essential to follow strict guidelines to ensure that materials are properly marked and protected. These rules provide a framework for determining how and when information should be classified or reclassified, based on its content, origin, and the level of sensitivity it holds. Adhering to these guidelines helps prevent unauthorized disclosure and maintains the integrity of the information security process.
Key Guidelines to Follow
There are several core rules to consider when dealing with materials that require protection:
- Consistency: Ensure that all materials are marked consistently according to established procedures and reflect their proper sensitivity level.
- Proper Documentation: Maintain records that outline the original classification of the material and the rationale behind the designation.
- Proper Application: When creating new documents or materials based on classified information, apply the same security markings as the original source.
- Preservation of Markings: Do not alter or remove security markings without proper authorization or until the classification status has changed in accordance with procedures.
Situations Requiring Special Consideration
Some situations may require additional attention or clarification when applying classification rules:
- Derived Documents: If new materials are created from classified sources, ensure they carry the same markings as the original documents unless the sensitivity level has changed.
- Changes in Sensitivity: If the status of a document or material changes, update the classification markings accordingly and ensure that all affected documents are reviewed.
- Access and Dissemination: Clearly specify who can access or distribute the material based on its classification level, ensuring that unauthorized individuals are excluded.
Challenges in Derivative Classification Exams
Completing assessments related to information security and sensitivity handling can be complex due to the variety of rules, guidelines, and practical scenarios that need to be understood. The challenge lies in correctly interpreting the regulations and applying them to real-world situations, where the potential consequences of mistakes are significant. Individuals must demonstrate a comprehensive understanding of the principles and how to implement them effectively.
Some of the most common challenges faced during these assessments include:
| Challenge | Explanation |
|---|---|
| Ambiguity in Rules | Some guidelines may be open to interpretation, making it difficult to know how to apply them in specific contexts. |
| Complex Scenarios | Real-world situations can be more complicated than theoretical examples, requiring quick and accurate decision-making. |
| Keeping Up with Updates | Security protocols and classification standards may change, making it challenging to stay up-to-date with the latest regulations. |
| Understanding Multiple Layers of Security | Some materials have multiple layers of security, which must be correctly identified and handled according to their level of sensitivity. |
These challenges highlight the importance of comprehensive training and practice to ensure individuals are fully prepared to meet the requirements of the test. Addressing these difficulties requires a clear understanding of the principles and a methodical approach to applying them correctly in different situations.
Resources for Study and Practice
Preparing for assessments related to handling sensitive information requires access to reliable resources that can enhance understanding and improve performance. These resources are crucial for familiarizing yourself with the rules, procedures, and practical applications that will be tested. Whether through official materials, online courses, or practice exercises, the right tools can make a significant difference in mastering the necessary concepts.
Key resources to consider include:
- Official Guidelines: Government publications and official documentation provide the foundation for understanding the principles of information protection. These resources outline the rules and procedures that must be followed.
- Training Modules: Online courses and workshops offer structured learning experiences that cover both theoretical and practical aspects of data handling and security protocols.
- Practice Questions: Regularly working through practice exercises allows you to test your knowledge and identify areas where you may need further study.
- Study Groups: Joining a study group or forum with others who are preparing for the same assessment can help reinforce learning through discussion and shared insights.
By using a variety of these resources, individuals can strengthen their understanding and ensure they are prepared to successfully complete the assessment while maintaining the highest standards of information security.
Frequently Asked Questions About the Exam
Preparing for an assessment related to information handling and protection often comes with many questions. Understanding the process, requirements, and what to expect can help reduce anxiety and improve performance. Below are some of the most common questions people have when preparing for this type of test.
General Questions
- What topics are covered in the test? The assessment typically covers principles of information security, rules for handling sensitive data, and procedures for marking and protecting classified materials.
- How long is the test? The length of the assessment varies depending on the specific guidelines, but most tests are designed to be completed within a few hours.
- Is there a passing score? Yes, a minimum score is required to pass the assessment, which generally reflects a deep understanding of the materials and procedures involved.
- Can I retake the test if I fail? In most cases, individuals are allowed to retake the test after a specified period if they do not achieve the required passing score.
Preparation Questions
- How should I prepare for the assessment? Review official guidelines, participate in training courses, and practice with sample questions to build a solid understanding of the material.
- Are there practice exams available? Yes, practice tests are often available through training programs and can help you gauge your readiness for the actual assessment.
- What resources should I use to study? Official documentation, online training courses, and discussion forums are valuable resources to deepen your knowledge.
Common Mistakes to Avoid During the Exam
While taking an assessment related to information security, it is easy to make simple mistakes that could affect your performance. Being aware of these common errors can help you avoid them and ensure a smoother experience. Focusing on details and following the rules carefully are key to succeeding in these types of tests.
Here are some of the most common mistakes to watch out for:
- Misinterpreting the Rules: Failing to fully understand the guidelines can lead to incorrect answers. Take your time to read and comprehend the instructions before answering.
- Rushing Through the Test: Time pressure might cause you to skip important steps or make hasty decisions. It’s crucial to manage your time effectively and approach each question carefully.
- Overlooking Key Details: Small details, such as specific wording or exceptions, are essential to answering questions correctly. Pay close attention to every part of the material presented.
- Not Reviewing Your Answers: Before submitting your test, always review your responses to ensure they align with the rules and concepts you’ve learned.
- Ignoring Practice Tests: Skipping practice exercises or mock tests means missing out on valuable experience. Practice helps you familiarize yourself with the format and improves your confidence.
By avoiding these mistakes, you can significantly increase your chances of performing well on the assessment and demonstrating a strong understanding of the necessary concepts.
How to Pass the Assessment
Successfully completing an assessment related to handling sensitive information requires careful preparation and attention to detail. To ensure you pass the test with confidence, it is essential to focus on key topics, understand the rules thoroughly, and practice consistently. Below are some strategies that will help you prepare and perform well on the test.
Effective Study Tips
- Understand the Guidelines: Make sure you have a clear understanding of the guidelines for managing sensitive data. Knowing the rules and when to apply them is crucial for answering questions correctly.
- Focus on Key Concepts: Pay special attention to the core concepts that are frequently tested. These often include the principles of information protection, marking protocols, and security measures.
- Take Practice Tests: Engage in practice exercises to simulate the test environment. This will help you become familiar with the question format and improve your ability to recall important details.
- Review Mistakes: After completing practice tests, take time to review any mistakes you made. Understand why your answer was incorrect and what the correct approach should be.
Time Management Strategies
- Plan Your Time: Allocate a set amount of time for each section of the test. Managing your time will prevent you from rushing through questions or spending too much time on one answer.
- Read Carefully: Take your time to read each question carefully before answering. Often, misinterpreting the question can lead to mistakes.
- Stay Calm: Keep a calm and focused mindset during the test. If you feel overwhelmed, take a short break to refocus before continuing.
By following these strategies, you can ensure that you are well-prepared to pass the assessment and demonstrate a strong understanding of the rules for managing sensitive information.
Tips for Time Management on the Test
Effective time management during a test is crucial for ensuring that you can answer all questions accurately and without feeling rushed. By planning your approach and pacing yourself throughout the assessment, you increase your chances of performing well. Here are some helpful tips to manage your time efficiently during the test.
Time Allocation Strategies
- Set a Time Limit for Each Section: Before starting, divide the total time available by the number of sections or questions. Assign an appropriate amount of time for each part of the test to ensure that you don’t spend too much time on any one question.
- Start with the Easy Questions: Quickly go through the questions and begin with the ones that seem the easiest. This will help build confidence and allow you to tackle more difficult questions later.
- Don’t Dwell on Difficult Questions: If you find a question that is taking too long, move on and come back to it later. It’s better to answer all the questions you can and return to the tough ones if you have time.
Tracking Your Progress
- Use a Watch or Timer: Keep track of the time by using a timer or watch. This will help you stay on schedule and avoid spending too much time on any particular section.
- Monitor Your Speed: Periodically check your progress throughout the test. If you are behind schedule, speed up to catch up. If you’re ahead of schedule, take a moment to double-check your answers.
Test Time Management Table

| Task | Recommended Time |
|---|---|
| Read Instructions | 5 minutes |
| Easy Questions | 40% of total time |
| Medium Difficulty Questions | 35% of total time |
| Review and Difficult Questions | 20% of total time |
By following these time management strategies, you can approach the test with a clear plan, stay on track, and complete the assessment without unnecessary stress.
Important Legal and Regulatory Aspects
Understanding the legal and regulatory framework surrounding the handling of sensitive information is essential for anyone involved in the process. There are various laws and policies in place that govern how information should be categorized, accessed, and disclosed. Failing to comply with these regulations can lead to severe legal consequences and compromise national security. This section will highlight key aspects that all individuals must be aware of to remain compliant.
Key Legal Frameworks
- National Security Act: This act provides the foundation for safeguarding sensitive government data and establishes the guidelines for its management and dissemination.
- Freedom of Information Act (FOIA): While this act ensures transparency in government activities, it also outlines exceptions for protecting classified information that could harm national interests.
- Executive Orders and Directives: These documents set forth specific protocols and responsibilities for federal agencies and employees when dealing with classified materials.
Compliance and Penalties
- Violations of Regulations: Breaching legal obligations related to sensitive data can result in severe penalties, including fines, imprisonment, or loss of security clearance.
- Reporting Requirements: Individuals must promptly report any mishandling or accidental disclosure of classified material to the appropriate authorities.
- Training and Certification: Regular training is required for personnel to ensure they remain up to date with evolving regulations and best practices.
Adhering to these legal and regulatory guidelines ensures that sensitive information remains secure and is handled with the utmost care, minimizing risks to national security and personal liability.
Impact of Failing the Derivative Exam
Failing a test related to the handling of sensitive or restricted information can have significant consequences, not only for the individual but also for the organization they work for. The impact extends beyond the immediate effects of failing the assessment, potentially affecting job security, reputation, and future opportunities. Understanding these consequences is crucial for anyone preparing for such an evaluation.
For individuals, failing this type of assessment may lead to the loss of security clearance, preventing them from accessing important materials required for their role. It could also result in the need for retraining or a reassessment, both of which can delay career progression and impact personal job stability. In some cases, repeated failure could lead to job termination.
On an organizational level, the consequences of an employee’s failure to pass such a test can be far-reaching. Mishandling sensitive information due to lack of knowledge could lead to breaches of confidentiality, legal consequences, and a loss of public trust. The organization may face penalties or restrictions, affecting its ability to operate smoothly. In extreme cases, it could also damage relationships with government entities or other critical partners.
Ultimately, the failure to pass this assessment underscores the importance of proper training and preparation. Ensuring that all personnel are adequately equipped with the knowledge and skills necessary to handle sensitive materials is vital to maintaining both individual and organizational integrity.
Future Trends in Classification Training
The landscape of training for handling sensitive and confidential information is rapidly evolving, with new trends and methodologies reshaping the way employees are prepared for their roles. As organizations face increasing challenges around data security and privacy, the future of training in this area will focus on improving accessibility, effectiveness, and adaptability to keep pace with emerging technologies and regulatory changes.
Technological Integration in Training Programs
One of the key trends in training for information management is the growing integration of technology. Virtual reality (VR), artificial intelligence (AI), and machine learning are beginning to play a larger role in providing interactive and personalized training experiences. These technologies can simulate real-world scenarios, helping individuals better understand complex concepts and procedures in a controlled environment. Additionally, AI can provide real-time feedback, identifying areas where an individual may need further improvement and suggesting specific training modules tailored to their needs.
Increased Focus on Continuous Learning and Adaptability
As the regulatory environment surrounding information security becomes more complex, the emphasis is shifting towards continuous learning rather than one-time training sessions. Professionals will need to stay updated with the latest best practices, legal requirements, and technological advancements. Microlearning, which involves short, focused training sessions, is expected to become more common, allowing employees to quickly adapt to new challenges without interrupting their workflow. Furthermore, companies are expected to prioritize training programs that foster a culture of adaptability, ensuring that personnel can easily adjust to changes in regulations and information management practices.
In conclusion, the future of training for managing sensitive information will be defined by greater technological integration and a commitment to lifelong learning. By embracing these trends, organizations can ensure their workforce is well-prepared to navigate the complexities of data security in an increasingly dynamic world.
Where to Find Official Test Information
For those preparing for official assessments related to managing sensitive information, knowing where to access reliable and up-to-date resources is crucial. Official materials can ensure that candidates are familiar with the latest guidelines and regulatory standards. Below are several trusted sources where candidates can find the most accurate and comprehensive information for test preparation.
Trusted Government and Regulatory Websites
The most authoritative resources for preparation can often be found directly through government and regulatory bodies that oversee information security. These organizations frequently publish training materials, guides, and detailed instructions on handling sensitive data. By visiting their official websites, individuals can access the most current standards and practices. Key sites to consider include:
- National Archives and Records Administration (NARA): A key resource for government employees handling classified materials.
- Department of Defense (DoD): Offers in-depth training resources on security practices and guidelines.
- Federal Acquisition Regulation (FAR): Provides specific regulatory guidelines that may impact various organizations’ operations.
Training Platforms and Certification Programs

In addition to government websites, there are a number of accredited training platforms and certification programs that provide comprehensive preparation materials. These resources often include mock assessments, quizzes, and instructional videos designed to help candidates hone their knowledge. Some platforms also offer updated materials following regulatory changes, ensuring that learners are always working with the most relevant content. Some widely recognized platforms include:
- Defense Acquisition University (DAU): Known for providing specialized courses and exams related to information handling.
- International Information System Security Certification Consortium (ISC)²: Offers training resources for those handling classified data and information.
- Coursera and LinkedIn Learning: Online learning platforms that offer both free and paid courses on data security and privacy.
By leveraging these resources, individuals can ensure that they are thoroughly prepared for the assessment process and have access to the most accurate and relevant materials available.