
In today’s interconnected world, safeguarding sensitive information is more critical than ever. Effective security measures require individuals to understand the risks and adopt preventive behaviors that protect both personal and organizational data. Building a strong foundation of knowledge in security principles helps reduce vulnerabilities and enhance overall defense strategies.
Strengthening security protocols involves more than just using the latest technology. It requires a proactive approach where individuals are equipped with the skills to identify potential threats, recognize patterns of suspicious activity, and respond accordingly. Understanding the fundamentals of secure behavior and applying them consistently is key to minimizing risks.
Practical education on security practices ensures that everyone, from entry-level employees to seasoned experts, is on the same page. By addressing common misconceptions and providing clear, actionable guidance, individuals can improve their ability to protect sensitive information from various types of threats. This section will explore essential topics and effective strategies for improving overall security practices.
Security Knowledge and Best Practices
Ensuring effective protection of sensitive information involves understanding potential risks and taking steps to mitigate them. Individuals at all levels must be equipped with the knowledge to identify threats, follow secure practices, and react swiftly when necessary. This section delves into essential concepts, providing guidance on how to enhance personal and organizational security by following proven methods and practices.
By focusing on common questions and scenarios, it becomes easier to pinpoint where individuals often need more guidance or clarification. Offering structured responses to these situations helps in building a consistent and effective security culture across the organization. Below is a table summarizing key security measures, clarifying some of the most frequently encountered challenges and solutions.
| Security Challenge | Recommended Solution |
|---|---|
| Identifying Phishing Emails | Check the sender’s email address, avoid clicking on suspicious links, and verify requests through official channels. |
| Weak Password Practices | Use strong, unique passwords for each account and consider a password manager for better organization. |
| Insecure Data Sharing | Encrypt sensitive files and share them through secure, verified channels. |
| Unprotected Devices | Ensure that all devices are password-protected, and utilize encryption and multi-factor authentication where possible. |
| Social Engineering Threats | Be cautious when sharing information, especially over the phone or online, and always verify before acting on requests. |
Understanding the Basics of Security Practices
At the core of any effective defense system lies a solid understanding of how to protect sensitive information from potential threats. By identifying key risks and learning how to mitigate them, individuals can make more informed decisions, reducing vulnerabilities within both personal and organizational settings. Recognizing what constitutes a threat and applying proactive measures is crucial in maintaining a secure environment.
Key Concepts for Protecting Information

Protecting sensitive data involves a range of practices designed to secure communication, prevent unauthorized access, and limit the exposure of critical details. A fundamental aspect of security is understanding the flow of information–who has access to it, how it is shared, and the potential dangers of mishandling it. By knowing the risks associated with different forms of data storage and transfer, individuals can avoid common pitfalls.
Basic Principles for Minimizing Risks
Mitigating security risks requires a combination of technological solutions and human vigilance. Simple actions such as using strong passwords, keeping software updated, and being cautious of unsolicited messages can significantly reduce the chances of a breach. Additionally, creating a culture of responsibility where everyone understands their role in maintaining security is essential for long-term success. The key lies in integrating security habits into everyday practices and continually staying informed about emerging threats.
Why Security Practices Matter in Protecting Information
In today’s digital landscape, securing sensitive information is not just about using advanced technology; it’s about understanding the behavior and actions that can compromise or safeguard valuable data. Every decision, from how information is shared to how devices are secured, can either strengthen or weaken an organization’s defense against cyber threats. Maintaining strong protective measures is a continuous effort that requires vigilance and knowledge at every level.
The Role of Human Behavior in Security
Human actions play a critical role in preventing security breaches. Even with the most sophisticated technology, a single careless mistake can lead to a data leak or system compromise. Understanding the importance of securely handling information, avoiding risky online behaviors, and recognizing potential threats are all essential in minimizing the risk of attacks. Training individuals to make the right decisions in everyday tasks is key to maintaining a secure environment.
Long-Term Benefits of Strong Security Practices
When security practices are consistently applied, the organization not only reduces its vulnerability to attacks but also builds trust with clients, customers, and partners. Security is a long-term investment that helps preserve the integrity of data, ensures compliance with regulations, and prevents costly breaches. As threats evolve, so must the approach to safeguarding information. A strong security culture creates a resilient framework capable of adapting to new challenges, ensuring ongoing protection for sensitive data.
Common Mistakes in Security Practices
Even with the best intentions, individuals and organizations can make critical errors that compromise security. These mistakes often stem from a lack of understanding, complacency, or simply overlooking basic precautions. Identifying and addressing these common pitfalls is essential to strengthen overall defense strategies and ensure that sensitive information remains protected.
One of the most frequent mistakes is the use of weak or reused passwords. Many individuals rely on simple, easy-to-remember passwords for multiple accounts, making it easier for attackers to gain access. Another common issue is neglecting software updates. Failure to install updates and patches promptly leaves systems vulnerable to known exploits. Additionally, employees often underestimate the risks associated with public Wi-Fi networks, unknowingly exposing sensitive information to potential interceptors.
Another prevalent error is sharing too much information online or over unsecured channels. Whether it’s through social media, email, or messaging platforms, oversharing can lead to identity theft, phishing attacks, or social engineering schemes. Additionally, some individuals fail to recognize the importance of device encryption, leaving personal and professional data vulnerable if a device is lost or stolen. Addressing these common mistakes and implementing proactive measures can greatly reduce the likelihood of a security breach.
How to Assess Security Vulnerabilities
Understanding the weaknesses in your security practices is crucial to improving overall protection. To effectively safeguard sensitive information, it’s important to regularly assess vulnerabilities and identify areas where defenses may be lacking. By systematically evaluating potential risks, you can prioritize actions and implement targeted strategies to address weaknesses before they can be exploited.
Identifying Potential Risks

The first step in assessing security vulnerabilities is identifying potential risks. This involves reviewing all aspects of your organization’s operations, from employee behavior to technological systems. Evaluate how information is stored, transferred, and accessed, and look for any gaps or inconsistencies in protection. Pay particular attention to high-risk areas such as communication channels, data storage, and user access privileges. Identifying these potential threats is the foundation for creating a more secure environment.
Regular Audits and Assessments
To accurately measure the effectiveness of your security measures, it’s essential to conduct regular audits and assessments. This can be done through simulated attacks, vulnerability scans, or by enlisting external experts to provide an objective evaluation. Regular assessments help identify emerging threats, evaluate whether existing security practices are sufficient, and determine if new vulnerabilities have developed over time. Continual evaluation allows organizations to adapt to the ever-evolving landscape of digital threats.
Top Tools for Enhancing Security Practices
In the modern digital landscape, having the right tools to manage and strengthen security is crucial. The right solutions can help individuals and organizations identify potential vulnerabilities, prevent data breaches, and streamline secure communication. Below are some of the most effective tools available for improving overall security and reducing the risk of unauthorized access.
Essential Security Tools for Individuals
- Password Managers: These tools help generate, store, and manage complex passwords, reducing the risk of using weak or reused credentials. Popular options include LastPass, 1Password, and Dashlane.
- Antivirus Software: A reliable antivirus program is essential for detecting and removing malicious software before it can cause harm. Leading options include Norton, McAfee, and Bitdefender.
- Virtual Private Networks (VPNs): A VPN encrypts internet traffic and hides a user’s location, making it harder for cybercriminals to intercept communications. Popular VPNs include ExpressVPN, NordVPN, and CyberGhost.
Tools for Organizations and Teams
- Encryption Software: Encrypting sensitive data is a vital step in ensuring that it remains secure, even if devices are lost or hacked. Tools like VeraCrypt and BitLocker are commonly used for file and disk encryption.
- Firewalls: Firewalls monitor and control incoming and outgoing network traffic based on predetermined security rules. Some widely-used firewalls include ZoneAlarm and Cisco ASA.
- Security Information and Event Management (SIEM): SIEM systems aggregate and analyze data from various security tools, providing a centralized view of security incidents. Examples include Splunk and SolarWinds SEM.
By incorporating these tools into daily practices, both individuals and organizations can significantly enhance their ability to detect threats and respond to security challenges in a timely and effective manner.
Identifying Threats to Your Security
Recognizing potential threats to your security is the first step in protecting sensitive information and ensuring a safe environment. Threats can come in various forms, ranging from cyberattacks to physical breaches, and it is crucial to understand where vulnerabilities may lie. Identifying these risks early allows you to take preventative measures and mitigate the impact of any potential attack.
Common Security Threats

- Phishing Attacks: Cybercriminals use deceptive emails, messages, or websites to trick individuals into revealing personal information, login credentials, or financial data.
- Malware: Malicious software designed to damage, disrupt, or steal data from your systems. This includes viruses, ransomware, and spyware.
- Social Engineering: Manipulating individuals into disclosing confidential information by exploiting human psychology, such as pretending to be a trusted source.
- Data Breaches: Unauthorized access to sensitive data, often leading to identity theft, financial loss, or damage to an organization’s reputation.
Assessing Your Vulnerabilities
- Weak Passwords: Using simple or repeated passwords across multiple platforms makes systems easy targets for attackers.
- Lack of Encryption: Failing to encrypt sensitive data, whether in transit or at rest, exposes it to unauthorized access and theft.
- Unpatched Software: Not updating software and applications regularly leaves systems vulnerable to known exploits and security flaws.
- Unsecure Networks: Using public or unsecured Wi-Fi networks without encryption can expose communications and personal information to interception.
Identifying these threats and understanding where vulnerabilities exist within your systems is essential to creating an effective security strategy and protecting valuable assets from harm.
Best Practices for Secure Communication
Ensuring the confidentiality and integrity of information shared between individuals or organizations is crucial in maintaining a secure environment. Implementing secure communication practices helps protect sensitive data from unauthorized access, interception, or alteration. Following the best practices outlined below can significantly reduce the risk of security breaches.
Key Guidelines for Safe Communication
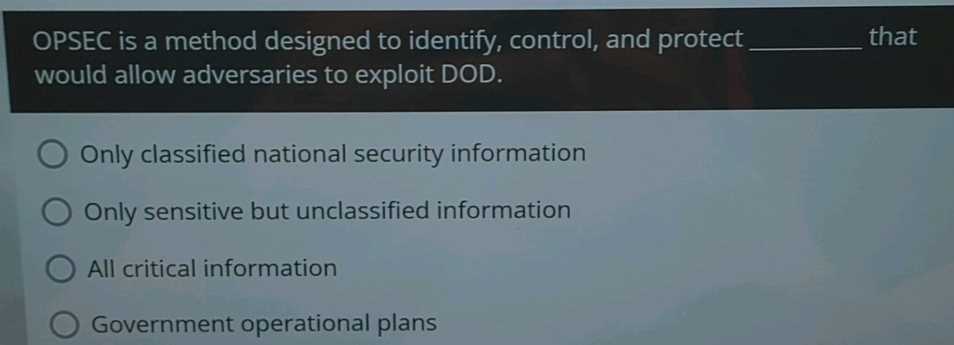
- Use Encryption: Always encrypt sensitive messages and communications to prevent unauthorized individuals from accessing the content.
- Verify Recipients: Confirm the identity of recipients before sending sensitive information, especially in email or messaging systems.
- Use Secure Platforms: Utilize trusted, secure communication platforms that offer end-to-end encryption and other security features.
- Regularly Update Software: Keep communication software, devices, and systems up to date with the latest security patches to protect against vulnerabilities.
Security Features to Look for in Communication Tools
| Feature | Description |
|---|---|
| End-to-End Encryption | Ensures that only the sender and recipient can read the message, protecting the content from interception. |
| Two-Factor Authentication | Requires an additional verification step to ensure the identity of the user accessing the communication platform. |
| Secure File Sharing | Allows safe transfer of files with encryption, ensuring that files are protected during transmission. |
| Message Expiration | Automatically deletes messages after a set time, reducing the risk of leaving sensitive data vulnerable. |
By following these best practices and using secure communication tools, individuals and organizations can safeguard their sensitive conversations and data from potential threats.
Opsec in the Digital Age
In today’s interconnected world, securing personal and organizational information is more challenging than ever. With the rapid advancement of technology, the risks associated with data breaches and cyberattacks have grown exponentially. Protecting sensitive information now requires understanding and implementing advanced security measures to safeguard against increasingly sophisticated threats.
The rise of digital platforms and online communication channels has introduced new vulnerabilities. From social media and cloud storage to messaging apps and email, every digital tool presents potential entry points for malicious actors. As these technologies evolve, so too must the strategies for protecting valuable data and ensuring privacy.
Key Considerations for Digital Security

- Data Encryption: Encrypting sensitive data ensures that even if information is intercepted, it remains unreadable to unauthorized parties.
- Multi-Factor Authentication (MFA): Adding an extra layer of security through MFA ensures that users must verify their identity in multiple ways before accessing sensitive systems.
- Regular Software Updates: Keeping systems and software up to date with the latest security patches reduces vulnerabilities that could be exploited by cybercriminals.
- Safe Browsing Practices: Being mindful of phishing schemes and ensuring that websites are secure (look for “https” and padlock symbols) can help prevent cyber attacks.
How to Protect Information in a Digital World

- Use Strong Passwords: Employ complex, unique passwords for each account to prevent unauthorized access.
- Avoid Public Wi-Fi for Sensitive Transactions: Using unsecured networks for financial or confidential communications can expose you to potential risks.
- Monitor Digital Footprints: Regularly check your online presence and be aware of what personal information is available to others.
- Limit Data Sharing: Be cautious about what personal information you share online, and adjust privacy settings on social media platforms.
By adopting these practices, individuals and organizations can mitigate the risks associated with digital vulnerabilities and ensure that their information remains secure in an increasingly connected world.
Training Your Team in Security Best Practices
Ensuring that your team understands the importance of safeguarding sensitive information is crucial for maintaining a secure environment. Effective training helps employees recognize potential threats and empowers them to take proactive steps in mitigating risks. Without proper knowledge and preparation, even the most advanced security measures can be compromised by human error or neglect.
Providing your team with the necessary resources and guidelines can make a significant difference in preventing breaches. From recognizing phishing attempts to understanding how to handle confidential data, fostering a culture of vigilance and responsibility is key. Additionally, regular updates and ongoing education will ensure that team members stay informed about emerging threats and evolving security practices.
Key Topics to Cover
- Secure Communication: Teach employees how to use encryption tools and secure messaging platforms to protect sensitive information during communication.
- Data Protection: Emphasize the importance of safeguarding files, emails, and documents, particularly when working remotely or with third parties.
- Phishing and Social Engineering: Train team members to identify deceptive tactics used by attackers to gain access to confidential information.
- Safe Internet Practices: Highlight the importance of avoiding unsafe websites and using secure networks for online activities.
Effective Training Methods
- Interactive Workshops: Engage employees with hands-on activities and scenarios that simulate real-world threats, helping them learn how to respond effectively.
- Regular Assessments: Conduct periodic tests to evaluate your team’s understanding and preparedness regarding security procedures.
- Ongoing Education: Implement a system of continuous learning through newsletters, seminars, and webinars to keep security knowledge up-to-date.
By investing in training and developing your team’s skills, you ensure a more secure working environment where each individual is equipped to contribute to the overall security posture of the organization.
Effective Methods for Teaching Security Best Practices
When it comes to educating individuals on the importance of safeguarding sensitive information, choosing the right methods is essential. Effective learning techniques can help employees understand how to identify potential threats and implement preventative measures to protect valuable assets. From hands-on experience to interactive tools, these approaches make the concepts more accessible and memorable.
To ensure the success of security education programs, it’s vital to use a variety of methods that cater to different learning styles. Visual aids, real-world scenarios, and engaging activities can help reinforce key concepts. In addition, creating an environment where continuous learning is encouraged will help team members stay informed about evolving risks and solutions.
Key Teaching Methods
- Interactive Simulations: Use practical scenarios where employees can experience security challenges in a controlled environment and practice responding effectively.
- Group Discussions: Facilitate open conversations about security concerns, allowing team members to share experiences and discuss best practices for protecting sensitive information.
- Gamification: Implement gamified learning modules that make security education enjoyable while reinforcing critical concepts through quizzes and competitions.
- Real-Life Case Studies: Analyze actual security breaches or threats to help individuals understand the consequences of poor security practices and learn from past mistakes.
Key Tools for Teaching Security Concepts
| Method | Description |
|---|---|
| Online Courses | Provide a structured learning path for employees to complete at their own pace, with video lessons and assessments to track progress. |
| Workshops | Conduct in-person or virtual sessions that engage participants with discussions, hands-on activities, and role-playing scenarios. |
| Infographics and Guides | Offer visual aids and step-by-step guides that employees can refer to quickly for understanding key security practices. |
Using these methods in combination can significantly enhance the learning experience, ensuring that employees are well-equipped to protect themselves and the organization from security risks.
Building a Strong Security Culture
Establishing a robust security culture within an organization is crucial for protecting sensitive information and minimizing risks. A strong culture empowers individuals at all levels to prioritize security in their daily tasks and decision-making processes. By fostering an environment that values security, organizations can reduce vulnerabilities and strengthen their defenses against potential threats.
Creating a security-focused culture requires more than just implementing policies; it involves engaging employees and making security practices an integral part of the organizational mindset. When individuals understand the importance of safeguarding data and are equipped with the knowledge to do so, they become active participants in securing the organization’s assets.
Key Steps to Cultivate a Security-Oriented Environment
- Leadership Commitment: Leaders must demonstrate a strong commitment to security, setting the tone for the entire organization by prioritizing it in both communication and actions.
- Clear Communication: Clearly communicate security goals, policies, and expectations to all employees to ensure that everyone understands their role in maintaining a secure environment.
- Regular Updates: Provide regular updates on potential security threats and best practices, ensuring that employees are aware of the latest developments and are prepared to respond.
- Rewarding Safe Practices: Encourage safe security practices by recognizing and rewarding employees who consistently follow security protocols and demonstrate strong security habits.
Engaging Employees in Security Initiatives
- Interactive Training: Use interactive learning sessions to engage employees and give them hands-on experience with security scenarios, helping them understand real-world applications of security practices.
- Security Ambassadors: Identify and empower security ambassadors within the organization to help spread awareness and act as advocates for strong security measures.
- Feedback Channels: Establish open channels for employees to report security concerns, share feedback on existing practices, and suggest improvements.
Building a strong security culture is an ongoing process that requires dedication, collaboration, and continuous improvement. By making security an integral part of the organization’s values, employees will be better prepared to protect the organization from threats and contribute to its overall resilience.
Evaluating Security Instruction Success
Assessing the effectiveness of security education initiatives is essential to determine if employees have absorbed the necessary information and are applying best practices in their daily activities. A successful program not only imparts knowledge but also influences behavior, ensuring that security protocols are followed and that risks are mitigated effectively. To measure this success, it is important to evaluate various aspects such as participation, knowledge retention, and real-world application of security measures.
Key Metrics for Success Evaluation
- Engagement Levels: Monitor the participation rate in training sessions, as well as the enthusiasm and involvement of employees throughout the process. Active engagement often correlates with higher knowledge retention and understanding.
- Knowledge Assessment: Regular quizzes and tests can help evaluate the retention of key concepts and identify areas where further clarification may be needed.
- Behavioral Change: Observe the practical application of security principles in the workplace. For example, are employees consistently following protocols for data protection, password security, and risk mitigation?
- Incident Reduction: Track the frequency of security incidents before and after the education program to determine if there has been a noticeable reduction in breaches or near-miss events.
Feedback and Continuous Improvement
- Employee Feedback: Gathering feedback from participants can provide insights into the effectiveness of the content and delivery methods. Surveys or informal discussions can help identify strengths and areas for improvement.
- Ongoing Evaluation: Security challenges evolve over time, and so should the educational approach. Regularly review and update training materials to reflect emerging threats and new best practices.
- Reinforcement Activities: Periodic refresher courses and micro-learning opportunities can help reinforce concepts and maintain high levels of security consciousness among employees.
By regularly evaluating the success of educational programs, organizations can ensure that their security practices remain robust, and that employees are equipped with the knowledge and skills to protect the organization from evolving threats.
How to Handle Security Breaches
When a security breach occurs, it is crucial to act quickly and effectively to minimize the damage and prevent further compromise. The first step is to identify the breach, understand its scope, and take immediate action to contain it. A well-prepared organization should have clear procedures in place to handle such incidents, ensuring a quick and organized response. Addressing the breach involves coordination between relevant teams, proper communication, and documentation to support both immediate recovery and long-term prevention.
Here are key steps to follow when handling a security breach:
- Identify and Confirm the Breach: The first priority is to quickly identify the breach. Determine what systems or data were affected, who is responsible for the incident, and how the breach occurred. Conduct an initial analysis to verify the scope of the breach.
- Contain the Incident: Once confirmed, isolate the affected systems or networks to prevent further access or data loss. Disconnect compromised devices from the network if necessary to stop the attack from spreading.
- Notify Relevant Authorities: Inform internal stakeholders and external authorities (such as regulatory bodies or law enforcement) depending on the severity and legal requirements of the breach. Transparency is essential to comply with regulations and maintain trust.
- Communicate with Stakeholders: Keep all stakeholders, including employees and customers, informed. A clear communication plan can help manage expectations and reduce panic. Be honest and transparent about the breach while emphasizing corrective actions being taken.
- Analyze and Mitigate: Conduct a thorough investigation to understand the breach’s cause. Assess any vulnerabilities that may have been exploited and implement corrective measures. This may include patching software vulnerabilities, changing passwords, or enhancing security protocols.
- Recovery and Prevention: After containment and analysis, focus on recovery. Restore normal operations and systems as quickly as possible. In the long term, review and revise security policies and implement improvements to prevent future incidents.
By handling breaches efficiently and transparently, organizations can not only minimize the impact but also strengthen their security posture and prevent similar incidents in the future.
Security Strategies for Remote Work
With the rise of remote work, it has become essential to implement strategies that ensure the protection of sensitive information and secure communication between teams. Remote work environments present unique challenges, including the use of personal devices, unsecured networks, and potential exposure to cyber threats. Adopting strong security practices is critical to maintaining the integrity of both company data and personal privacy. Establishing clear guidelines and utilizing appropriate tools can help mitigate risks while promoting a secure work-from-home culture.
Best Practices for Remote Workers
To maintain secure operations when working remotely, consider the following best practices:
- Use Secure Connections: Always connect to a trusted, encrypted network (e.g., VPN) when accessing work-related resources. Avoid public Wi-Fi networks, which may expose data to unauthorized users.
- Implement Strong Authentication: Enforce multi-factor authentication (MFA) to add an extra layer of security. This ensures that even if credentials are compromised, unauthorized access is prevented.
- Regular Software Updates: Keep all devices up to date with the latest software patches. This helps close security loopholes that could be exploited by cybercriminals.
- Secure Devices: Use strong passwords and encryption on all devices used for work purposes. This helps protect data in case a device is lost or stolen.
Managing Remote Access and Data Protection
Properly managing access to sensitive data and ensuring secure communication are key to safeguarding information in remote work setups:
- Limit Access to Sensitive Data: Ensure that employees only have access to the information necessary for their role. Implement data segmentation to reduce the risk of exposure.
- Utilize Secure Collaboration Tools: Use encrypted messaging, video conferencing, and document-sharing platforms to maintain the privacy of team communications and files.
- Monitor and Audit Remote Access: Regularly monitor remote access and conduct audits to detect any suspicious activities. Early detection is crucial in preventing potential breaches.
By following these strategies, remote workers can reduce vulnerabilities and contribute to a more secure digital work environment.
Integrating Security into Daily Operations

Incorporating robust security practices into everyday tasks is essential for protecting sensitive information and ensuring the safety of digital assets. This approach should not be seen as an isolated activity but as an ongoing part of routine operations. By embedding security measures into daily processes, organizations can create a proactive culture that minimizes risks and enhances overall resilience against potential threats. Regularly reviewing and updating procedures is vital to staying ahead of evolving security challenges.
Key Areas for Integration
To seamlessly integrate security into daily operations, focus on the following core areas:
| Area | Best Practices |
|---|---|
| Employee Behavior | Ensure staff members follow secure password practices, avoid sharing sensitive data via unsecured methods, and recognize phishing attempts. |
| Data Handling | Establish clear protocols for handling and storing sensitive data. Implement encryption and secure access controls to prevent unauthorized viewing. |
| Communication | Use encrypted communication tools for all internal and external exchanges. Avoid transmitting sensitive information over unsecured channels. |
| Device Management | Ensure all devices used for work purposes are secured with strong authentication measures, encryption, and up-to-date security software. |
Continuous Improvement
Security is not a one-time fix but requires continuous monitoring and improvement. To ensure that security measures remain effective, organizations should:
- Regularly update security protocols and tools in response to new threats.
- Conduct frequent audits and risk assessments to identify vulnerabilities.
- Encourage a culture of open communication, where employees can report potential security issues without fear of retaliation.
By integrating security into daily operations, organizations can foster a secure environment that supports both efficiency and protection against evolving threats.
Future Trends in Security Practices
As the digital landscape continues to evolve, so too does the need for more advanced and adaptive measures to safeguard sensitive information. Emerging trends in the realm of security practices are reshaping how organizations approach risk management and data protection. With new technologies and strategies, it is essential to stay ahead of potential threats and continually refine defensive tactics. The following are some of the key trends shaping the future of security management.
Key Trends Shaping the Future

Several developments are expected to play a pivotal role in the coming years, including:
- Artificial Intelligence and Automation: The integration of AI and automation will allow security systems to detect and respond to threats more quickly and accurately, reducing human error and increasing efficiency.
- Enhanced Encryption Technologies: With the rise of quantum computing, next-generation encryption algorithms will be developed to protect sensitive data against future decryption methods.
- Remote Work Security: As more businesses embrace remote work, securing personal and organizational data outside of traditional office environments will become a critical area of focus.
- Privacy Regulations and Compliance: Governments worldwide are strengthening regulations around data privacy, which will lead to more stringent compliance requirements for organizations handling sensitive information.
- Human Element and Training: While technology plays a crucial role, the human factor remains a significant vulnerability. Increasing focus will be placed on continuous education and reinforcing secure behaviors among employees.
Adapting to New Challenges
The key to staying ahead of evolving threats will be adaptability. Organizations must be proactive in assessing the effectiveness of their security measures and adapting their strategies as new risks emerge. Embracing innovation and fostering a security-conscious culture will be vital in maintaining a strong defense against future challenges.
As new tools and strategies emerge, organizations that invest in evolving their security practices will be better equipped to face the complexities of an increasingly interconnected and digital world.