In today’s interconnected world, protecting personal information and understanding online risks has become essential. With increasing threats to privacy, learning how to identify potential hazards and adopt security measures is crucial for everyone. From phishing attacks to malware, being prepared for these challenges can significantly reduce the likelihood of falling victim to malicious activities.
Learning to recognize and avoid digital threats empowers individuals to navigate the internet with confidence. Proper training can help distinguish legitimate sources from harmful ones, ensuring that users remain safe in various online environments. The ability to identify risks and implement protective actions is not only beneficial for individuals but also for organizations aiming to safeguard their data.
By enhancing your understanding of security protocols and preventive steps, you can stay ahead of cybercriminals. This guide will provide valuable insights and tips to help you prepare for various scenarios and improve your overall protection in the digital realm.
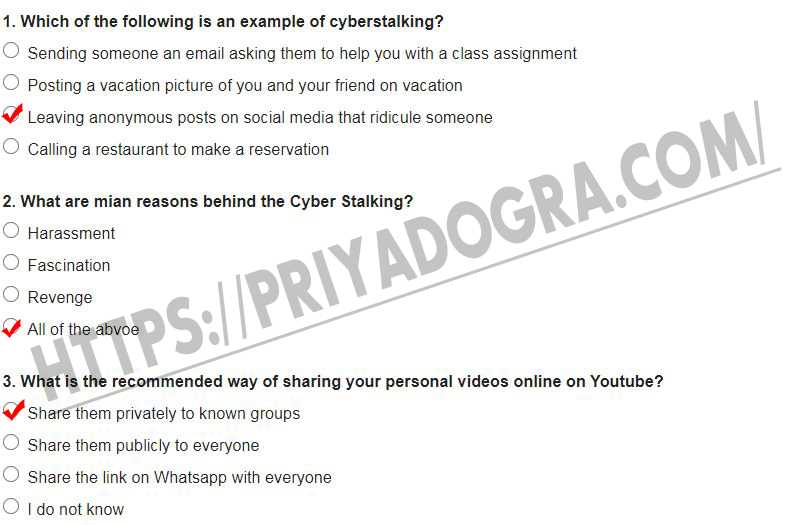
Cyber Awareness Challenge Test Answers
Being well-prepared for online security assessments is essential for effectively safeguarding personal and professional information. Understanding common risks and knowing the correct responses to various scenarios can help enhance your security skills. This section highlights key strategies and insights to help you succeed in these evaluations and ensure that you’re ready for any potential digital threats.
To improve your preparedness, consider the following areas of focus:
- Identifying phishing attempts and recognizing suspicious emails or messages.
- Understanding the importance of strong, unique passwords for all accounts.
- Knowing how to spot malicious websites and avoiding them.
- Responding to data breaches or compromised security in the right way.
- Practicing safe browsing habits on both personal and work devices.
Mastering these aspects will not only help you perform well in such assessments but also equip you with the knowledge to protect yourself and your data in the digital world.
Importance of Digital Security Knowledge for Everyone
In today’s digital landscape, understanding the risks and best practices for staying secure online is crucial for everyone. With the rise of online threats, from malicious software to social engineering tactics, it is essential for individuals to be equipped with the right knowledge to protect their personal and professional data. This awareness is not just for experts but is vital for every internet user.
Having a basic understanding of common online threats helps individuals make informed decisions, reducing the likelihood of falling victim to harmful situations. Below are key reasons why digital security knowledge is important:
- Protecting personal information: Understanding how to safeguard sensitive data is crucial for avoiding identity theft and fraud.
- Minimizing the risk of attacks: Recognizing potential threats like phishing or malware helps prevent them from succeeding.
- Promoting a secure online environment: By practicing good security habits, individuals contribute to a safer internet for everyone.
- Increasing confidence: Being knowledgeable about security measures boosts confidence when navigating digital platforms.
By staying informed and practicing the correct security protocols, individuals can greatly reduce their risk of encountering problems online, ensuring both personal and collective digital safety.
Key Concepts in Security Training
To effectively defend against online threats, it is essential to understand several foundational concepts that underpin digital security. Proper training focuses on equipping individuals with the knowledge necessary to identify and mitigate risks, ensuring both personal and organizational data remain secure. These concepts are critical in recognizing potential dangers and implementing proper protective measures.
Core Areas of Security Training
Security training typically covers a variety of topics that address different aspects of online protection. Some key areas include:
| Concept | Description |
|---|---|
| Phishing and Social Engineering | Learning to identify deceptive attempts to obtain sensitive information. |
| Malware and Ransomware | Understanding the threats posed by harmful software and how to prevent infections. |
| Data Protection | Methods for safeguarding personal and organizational data from unauthorized access. |
| Password Management | Best practices for creating and managing strong, unique passwords. |
Security Protocols and Best Practices
Mastering security protocols is essential for individuals to protect themselves effectively. A combination of knowledge and routine practices–such as updating software, using encryption, and avoiding suspicious links–forms the foundation of robust online safety strategies.
Common Mistakes in Security Evaluations
When participating in evaluations related to online protection, individuals often make several common mistakes that can impact their performance. These errors typically stem from misunderstandings of best practices or overlooking key security measures. Identifying these pitfalls is essential for improving one’s ability to navigate digital risks and respond effectively to potential threats.
Some of the most frequent mistakes include:
- Ignoring suspicious emails: Many individuals fail to recognize the signs of phishing attempts, which can lead to compromised information.
- Weak password habits: Using simple or reused passwords across multiple platforms increases vulnerability to hacking.
- Neglecting regular updates: Failing to keep software and security programs up to date leaves systems exposed to new threats.
- Underestimating the importance of encryption: Not utilizing encryption for sensitive data can lead to exposure in case of a breach.
- Assuming online sources are trustworthy: Clicking on links or downloading files from unverified sources can introduce malware into systems.
By being aware of these common mistakes, individuals can take steps to avoid them and better protect themselves in the digital environment.
How to Approach the Evaluation
When preparing for an online security evaluation, it is essential to approach it with the right mindset and strategies. Understanding the scope of the evaluation and focusing on the core principles of online protection can greatly enhance your ability to perform well. Taking time to review key topics, recognizing common pitfalls, and applying practical knowledge are vital steps in ensuring success.
Here are some effective strategies for approaching such an evaluation:
- Review basic security principles: Familiarize yourself with essential topics such as recognizing phishing attempts, understanding secure passwords, and the importance of software updates.
- Stay calm and focused: Many evaluations are designed to test your reaction to typical online threats. Avoid rushing through questions and take time to consider each option carefully.
- Learn from past mistakes: If you have participated in similar assessments before, review any mistakes you may have made to ensure you don’t repeat them.
- Practice safe online habits: The more you practice secure online behaviors, the more naturally you will be able to identify correct responses during an evaluation.
By staying organized, calm, and informed, you can confidently navigate the evaluation and enhance your understanding of digital safety.
Understanding Phishing Scams and Prevention

Phishing is a deceptive tactic used by malicious individuals to obtain sensitive information, such as passwords, credit card numbers, and personal details. This form of online fraud is often disguised as legitimate communication, making it difficult to distinguish from genuine messages. Recognizing phishing attempts is critical in preventing data theft and protecting your online identity.
Common signs of phishing attempts include:
- Suspicious sender: Phishing emails often appear to come from familiar sources, but with slight variations in the email address or domain name.
- Urgent requests: These scams frequently create a sense of urgency, such as claiming an account has been compromised and demanding immediate action.
- Unusual links: Phishing emails often contain links that, when clicked, direct users to fake websites designed to steal personal data.
- Generic greetings: Many phishing attempts use generic salutations like “Dear Customer” rather than addressing you by name.
To prevent falling victim to phishing scams, follow these best practices:
- Verify the sender: Always double-check the sender’s email address, especially if the message seems suspicious or unexpected.
- Hover over links: Before clicking any link, hover your mouse over it to preview the actual URL and ensure it matches the legitimate website.
- Use multi-factor authentication: Enable additional layers of security for your accounts to reduce the risk of unauthorized access.
- Stay informed: Regularly update your knowledge about common scams and new phishing techniques to recognize them early.
By staying alert and following these preventative measures, you can significantly reduce your risk of falling for phishing scams and protect your personal information online.
Recognizing Malware and Its Dangers
Malicious software poses a significant threat to individuals and organizations alike, often causing damage to systems, stealing sensitive information, or compromising personal privacy. Understanding the types of malicious programs and knowing how to spot signs of infection are essential for preventing damage. This section provides key insights into identifying these risks and how to protect against them.
Common Types of Malicious Software
There are various forms of malicious programs, each with its own unique capabilities. Some of the most common types include:
| Type | Description |
|---|---|
| Viruses | Programs that attach themselves to files or software, spreading when executed. |
| Trojans | Malware disguised as legitimate software that, once activated, can cause damage or steal data. |
| Ransomware | Malicious software that encrypts files and demands payment for their release. |
| Spyware | Software designed to collect information from a user without their consent. |
Recognizing the Signs of Infection
Detecting malware early is critical for minimizing damage. Some warning signs to watch for include:
- Slow performance: A sudden slowdown in system speed may indicate that your device is infected.
- Unexpected pop-ups: Frequent pop-up advertisements, especially those that seem suspicious or unrelated to your browsing, can signal the presence of malware.
- Strange behavior: Unexplained system crashes, files disappearing, or programs opening and closing on their own could be symptoms of infection.
- Unusual network activity: Increased data usage or strange connections in your network traffic may suggest malicious activity.
Recognizing these symptoms early on allows you to take swift action, such as running security scans or disconnecting the affected device from the network, to limit potential damage.
Best Practices for Digital Hygiene
Maintaining strong digital practices is essential for safeguarding personal and professional information. By adhering to basic guidelines and routines, individuals can reduce the risk of security breaches and protect their devices from various threats. This section outlines key actions that everyone should take to ensure their online safety and privacy.
Regular Software Updates
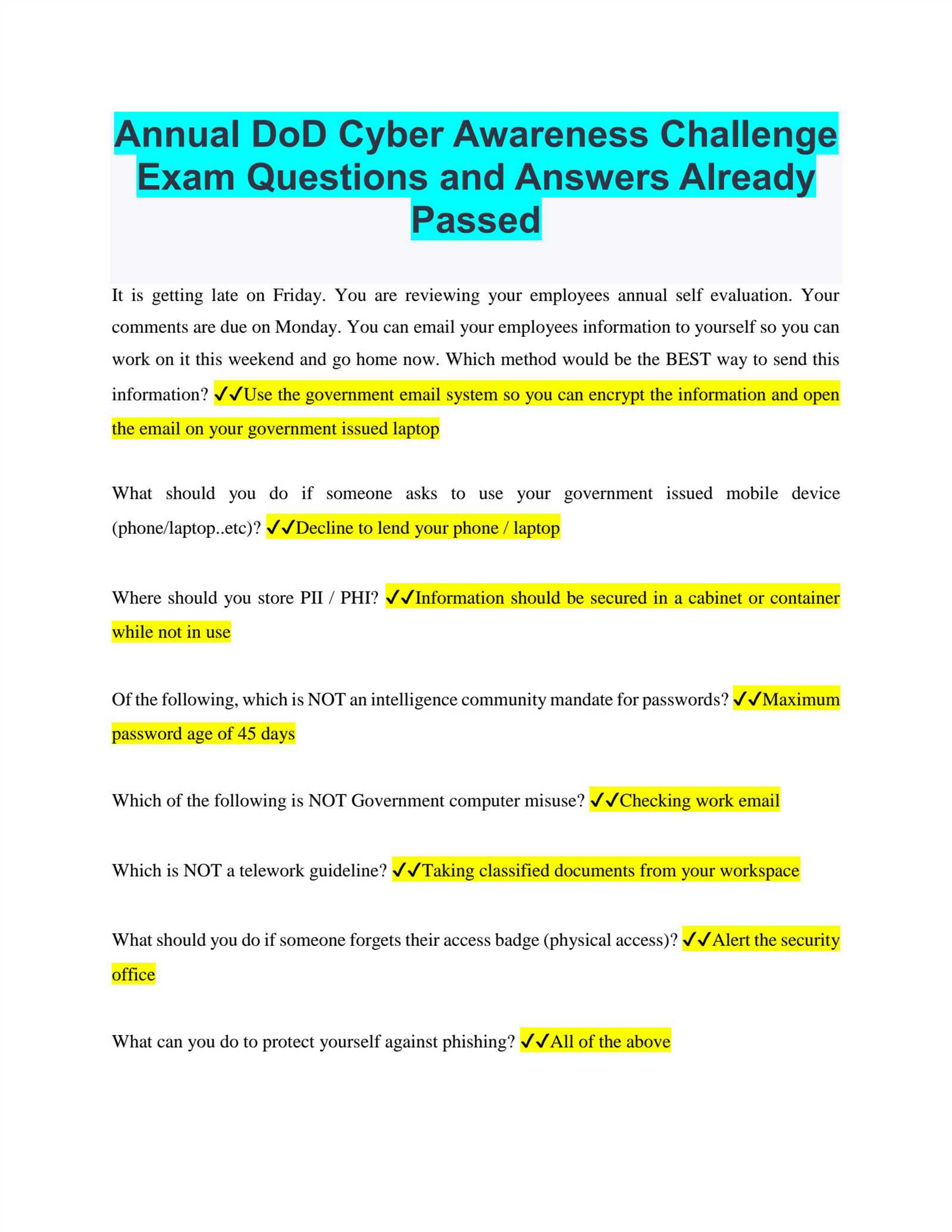
Keeping all software up to date is one of the most effective ways to defend against security vulnerabilities. Updates often include important patches that address known weaknesses, which cybercriminals can exploit if left unaddressed.
- Operating System: Enable automatic updates for your operating system to ensure timely fixes for security flaws.
- Applications: Regularly update all installed applications, including browsers and productivity tools, as they may also have critical security patches.
- Security Software: Ensure that your antivirus and firewall software are set to update automatically to stay protected against new threats.
Use Strong, Unique Passwords
Passwords are often the first line of defense against unauthorized access to accounts and systems. Strong, unique passwords make it more difficult for attackers to gain access.
- Length and Complexity: Create passwords that are at least 12 characters long, combining uppercase and lowercase letters, numbers, and special characters.
- Unique for Each Account: Never reuse passwords across multiple sites. Consider using a password manager to store them securely.
- Two-Factor Authentication: Enable two-factor authentication (2FA) whenever possible, adding an extra layer of security to your accounts.
By following these best practices, you can significantly enhance your digital hygiene and reduce the risk of falling victim to online threats. Regular vigilance and adherence to security habits will help protect your personal and sensitive data from malicious actors.
Steps to Safeguard Personal Information
Protecting personal data is crucial in today’s digital age. Whether it’s sensitive financial details, personal identification, or online account credentials, ensuring this information remains secure is essential. This section outlines practical steps individuals can take to safeguard their personal information and reduce the likelihood of it being compromised.
Strengthen Online Accounts
The first step in protecting your personal data is to secure the accounts you use online. Weak or reused passwords can expose you to unnecessary risks, making it easier for hackers to access your information.
- Use Unique, Complex Passwords: Avoid simple or common passwords. Utilize a combination of letters, numbers, and symbols, and ensure they are unique for each account.
- Enable Two-Factor Authentication: Adding an extra layer of security will make it much harder for unauthorized users to gain access to your accounts.
- Review Account Settings: Regularly check the security settings on your online accounts and enable the highest level of security available.
Be Cautious with Sharing Personal Details
How much information you share online plays a critical role in your security. It’s important to think carefully before disclosing sensitive data.
- Avoid Oversharing on Social Media: Limit the amount of personal information shared publicly, such as your home address, phone number, or financial details.
- Beware of Phishing Attempts: Be cautious about unsolicited emails or messages asking for personal information. Always verify the source before providing any sensitive data.
- Limit Sharing on Websites: Only provide personal information on trusted websites with secure connections (look for “https” in the URL and a padlock icon).
By following these simple yet effective steps, you can better protect your personal information from potential threats, ensuring that your data remains secure in both the online and offline worlds.
Data Protection Rules and Compliance

In an increasingly digital world, protecting personal and organizational data has become a legal and ethical necessity. Adhering to data protection regulations ensures that sensitive information is handled securely and responsibly. This section highlights the key regulations and best practices that organizations and individuals must follow to ensure compliance with data protection laws.
Key Regulations and Laws

Various laws and regulations have been established to protect personal data from misuse. These laws define how data should be collected, processed, stored, and shared, aiming to protect individuals’ privacy and rights.
- General Data Protection Regulation (GDPR): A comprehensive law in the European Union that sets guidelines for the collection and processing of personal data. It emphasizes transparency, accountability, and user consent.
- California Consumer Privacy Act (CCPA): A privacy law that gives California residents more control over the personal data collected by businesses, including rights to access, delete, and opt out of data sales.
- Health Insurance Portability and Accountability Act (HIPAA): A U.S. regulation that sets standards for protecting sensitive patient information in the healthcare sector.
- Payment Card Industry Data Security Standard (PCI DSS): A set of security standards for organizations that handle credit card information to ensure data is stored, processed, and transmitted securely.
Best Practices for Compliance
To ensure compliance with data protection laws, organizations should implement a range of best practices aimed at securing personal data and maintaining privacy standards.
- Data Minimization: Collect only the data necessary for the purpose at hand. Avoid excessive data collection to limit exposure in case of a breach.
- Encryption: Encrypt sensitive data both in transit and at rest to protect it from unauthorized access or theft.
- User Consent: Ensure that individuals provide clear and informed consent for data collection and processing, particularly for sensitive personal information.
- Regular Audits: Conduct routine audits to evaluate data handling practices, identify vulnerabilities, and ensure compliance with applicable laws and regulations.
Compliance with data protection regulations not only reduces the risk of fines and legal penalties but also helps build trust with customers and partners. By following the outlined practices, organizations can effectively safeguard data while ensuring they meet legal requirements.
How to Spot Social Engineering Attacks
Social engineering attacks rely on manipulating individuals into revealing confidential information or performing actions that compromise security. These attacks exploit human behavior, rather than technical vulnerabilities, to gain unauthorized access to systems, networks, or sensitive data. Understanding the signs of these tactics is essential for preventing harm and protecting both personal and organizational security.
Common Tactics Used by Attackers
Attackers use various techniques to deceive and manipulate their targets. These methods often involve creating a sense of urgency, trust, or fear to persuade individuals to act against their best interests.
- Phishing: Attackers impersonate legitimate entities, such as banks or service providers, to trick individuals into sharing sensitive information via email, phone calls, or websites.
- Pretexting: An attacker fabricates a false identity or story to gain access to personal or confidential information. They might claim to be a colleague, support agent, or someone in a position of authority.
- Baiting: The attacker offers something enticing, like free software or access to exclusive content, in exchange for sensitive data or access to systems.
- Tailgating: In physical environments, attackers may gain access to restricted areas by following authorized personnel without proper identification or permission.
How to Recognize and Avoid Social Engineering Attacks
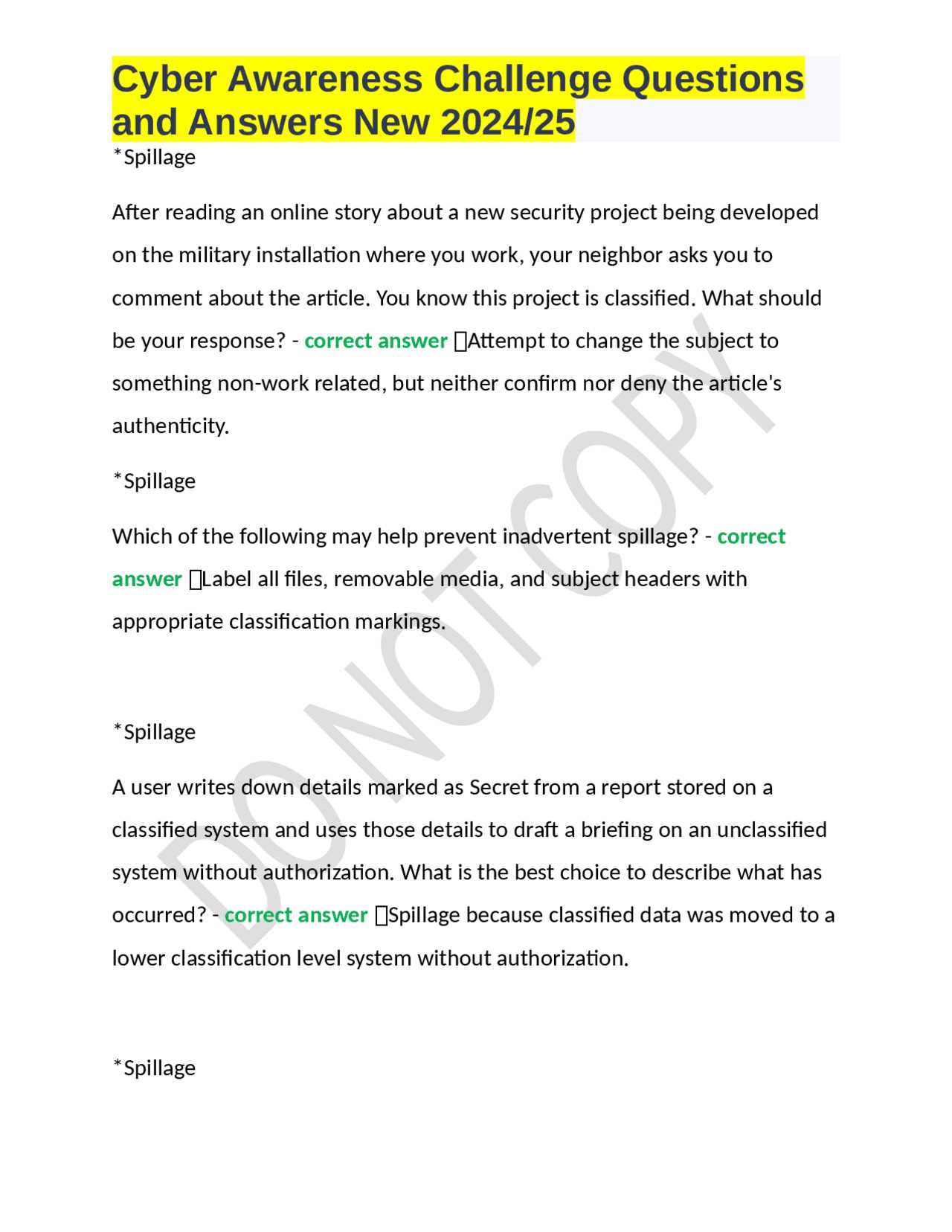
Recognizing the signs of a social engineering attack can help you avoid falling victim. Here are some red flags and tips for staying safe:
- Suspicious Requests: Be wary of unsolicited requests for sensitive information, whether through email, phone, or in person. Verify the identity of the requester before sharing anything.
- Unusual or Urgent Messages: Social engineers often create a sense of urgency or an emergency to pressure you into making hasty decisions. Take time to assess the situation and avoid acting impulsively.
- Uncommon Contact Methods: If you receive a message from an unknown number or email address, especially if it contains suspicious links or attachments, proceed with caution and avoid clicking on anything.
- Inconsistencies in Communication: Look out for discrepancies in the sender’s language, email address, or tone. Official messages typically follow consistent formats and language.
By staying vigilant and skeptical of unsolicited requests, individuals can significantly reduce the risk of falling victim to social engineering tactics. It’s important to always verify the source and be cautious before sharing personal or confidential information.
Importance of Strong Password Management

Managing passwords securely is crucial to safeguarding personal and organizational data. Weak or poorly managed passwords make systems vulnerable to unauthorized access, putting sensitive information at risk. Implementing strong password practices can significantly reduce the likelihood of falling victim to malicious activities and data breaches.
Why Strong Passwords Matter
In today’s digital world, passwords are the primary line of defense against unauthorized access to accounts and systems. However, simple or reused passwords are often easy for attackers to guess or crack. Strengthening password security is vital to maintaining privacy and preventing identity theft or other malicious actions.
- Protection from Brute Force Attacks: Weak passwords are often vulnerable to automated tools that attempt various combinations to guess the correct one. Strong passwords make these attempts much harder to succeed.
- Preventing Unauthorized Access: Strong, unique passwords prevent hackers from easily accessing accounts and personal information, especially when combined with additional security layers like multi-factor authentication (MFA).
- Safeguarding Personal and Professional Data: Passwords protect not only personal accounts but also sensitive business data. A compromised password can lead to devastating consequences for both individuals and organizations.
Best Practices for Managing Passwords
Adopting good password management habits can greatly enhance your security posture. The following guidelines can help ensure that your passwords remain strong and protected:
- Create Complex Passwords: Use a mix of uppercase and lowercase letters, numbers, and special characters. Avoid common phrases or easily guessable information such as birthdays or pet names.
- Avoid Reusing Passwords: Never use the same password across multiple accounts. If one account is compromised, others become vulnerable as well.
- Use a Password Manager: A reliable password manager can help generate and securely store complex passwords for each account. This way, you don’t need to remember every password but can ensure they remain unique and strong.
- Enable Multi-Factor Authentication (MFA): MFA adds an extra layer of security by requiring a second form of verification in addition to your password, such as a code sent to your phone or a fingerprint scan.
By following these best practices, you can better protect your digital identity and reduce the risk of security breaches. Strong password management is a simple yet highly effective way to safeguard personal and organizational information from malicious actors.
Tips for Securing Your Devices
Securing your devices is essential to prevent unauthorized access and protect personal data from potential threats. With the increasing number of cyberattacks, ensuring the safety of your smartphones, computers, and other connected devices is more important than ever. By following a few simple yet effective practices, you can minimize the risk of compromise and maintain your privacy.
Essential Steps to Enhance Device Security
Protecting your devices requires a combination of software, hardware, and user habits. Below are key actions to help secure your devices:
- Install Regular Software Updates: Ensure your devices are always running the latest operating system and application updates. Updates often contain important security patches that fix vulnerabilities that hackers may exploit.
- Enable Firewalls and Anti-virus Protection: Turn on built-in firewalls and use reputable anti-virus software to add an extra layer of protection against malware and other security threats.
- Use Strong Passwords and PINs: Create complex, unique passwords for each device and service you use. Avoid using easily guessable information, such as your name or birthdate. Consider using multi-factor authentication wherever possible for an added layer of security.
- Encrypt Sensitive Data: Enable encryption on your devices to ensure that even if your device is lost or stolen, the data remains unreadable without the correct password.
- Secure Your Wi-Fi Network: Use a strong password for your home or office Wi-Fi and avoid using default credentials. Consider using WPA3 encryption for a more secure connection.
Additional Tips for Device Security
There are also a few everyday practices that can make a big difference in maintaining your devices’ security:
- Avoid Public Wi-Fi for Sensitive Activities: Public networks are often unsecured, making them an easy target for attackers. Use a virtual private network (VPN) when connecting to public Wi-Fi.
- Be Cautious with Downloaded Apps and Files: Only download applications and files from trusted sources. Malware often disguises itself as legitimate software.
- Lock Your Devices When Not in Use: Always use a screen lock, password, or biometric authentication (like fingerprint or facial recognition) to protect your device when you’re not using it.
Table of Best Practices for Device Security
| Security Practice | Description |
|---|---|
| Install Software Updates | Keep your devices up-to-date with the latest security patches to protect against vulnerabilities. |
| Use Strong Passwords | Create complex, unique passwords for all your devices and online accounts to make unauthorized access more difficult. |
| Encrypt Your Data | Enable encryption on your devices to protect sensitive data, even in case of theft. |
| Activate Multi-Factor Authentication | Use multi-factor authentication to add another layer of protection to your devices and accounts. |
By incorporating these simple yet effective security measures, you can significantly reduce the risk of your devices being compromised and better protect your personal data from potential threats.
Cybersecurity Tools and Resources
In today’s digital age, securing sensitive data and protecting online activities requires a wide range of tools and resources. From basic software to advanced security platforms, there are numerous options available to individuals and organizations to defend against malicious threats. Utilizing the right tools can help you safeguard personal information, detect vulnerabilities, and stay protected from potential cyberattacks.
Essential Security Tools for Protection
There are many effective tools available that can significantly enhance your security posture. Here are some key categories of tools and their functions:
- Firewalls: Firewalls act as a barrier between your device or network and external threats. They filter incoming and outgoing traffic to block malicious activities. Both hardware and software firewalls are essential for protecting sensitive information.
- Antivirus Software: These programs detect, quarantine, and remove malicious software such as viruses, worms, and trojans. Regular updates ensure the software remains effective against the latest threats.
- Virtual Private Networks (VPNs): VPNs provide a secure and private connection to the internet by encrypting your online activity. Using a VPN is especially important when connecting to public or unsecured networks.
- Password Managers: These tools help you generate and store strong, unique passwords for all your online accounts. By using a password manager, you reduce the risk of reusing weak passwords and ensure better security.
Useful Resources for Ongoing Learning
Staying informed about the latest threats and best practices is crucial for maintaining good security hygiene. Here are some valuable resources that can help:
- Security Blogs and Websites: Websites such as Dark Reading and Krebs on Security provide up-to-date news on security breaches, new vulnerabilities, and emerging cyber threats.
- Online Courses: Platforms like Coursera, edX, and Udemy offer a variety of courses on digital security, from beginner to advanced levels, helping you build a solid understanding of best practices and tools.
- Government and Industry Guidelines: Organizations like the National Institute of Standards and Technology (NIST) and the European Union Agency for Cybersecurity (ENISA) provide guidelines and frameworks for ensuring the security of networks and data.
By leveraging these tools and resources, you can enhance your security posture, stay updated on the latest trends, and protect both personal and professional data from potential threats.
Responding to Cyber Incidents Properly
When an online threat or security breach occurs, quick and effective action is essential to minimize potential damage. Knowing how to respond properly in such situations can significantly reduce the impact of the incident, protect sensitive information, and help restore normal operations. Understanding the right steps and having a solid response plan can ensure that you effectively manage and mitigate risks when an attack happens.
Immediate Steps to Take After a Breach
In the event of a security incident, there are several important actions to take right away:
- Contain the Situation: The first step is to isolate the affected systems or network to prevent the breach from spreading. Disconnecting devices from the internet or shutting down compromised systems can help stop further damage.
- Identify the Source: Understanding the nature of the attack is crucial. Determine what caused the incident, whether it was malware, phishing, or another form of attack. This can guide your next steps in addressing the threat.
- Notify Key Stakeholders: Inform internal teams, such as IT and security personnel, and relevant external parties, such as customers or regulatory bodies, if necessary. Prompt notification helps in coordinating the response and limiting the incident’s impact.
Long-Term Strategies for Incident Management
Once the immediate steps have been taken, it’s important to implement a comprehensive strategy for managing the aftermath of the breach:
- Conduct a Detailed Investigation: After securing the environment, a thorough investigation should be performed to determine the full extent of the damage. This includes analyzing system logs, identifying compromised data, and understanding how the attack unfolded.
- Strengthen Security Measures: Once the root cause is identified, it’s essential to implement stronger security measures. This might involve updating software, patching vulnerabilities, or revising access controls to prevent future incidents.
- Review and Update the Incident Response Plan: Following the resolution of the incident, it’s important to review and revise your response plan based on lessons learned. Continuous improvement in response strategies ensures better preparedness for future threats.
By acting quickly and following a structured approach, you can limit the damage caused by security breaches and strengthen your defenses against future incidents.
The Role of Employee Training in Security
Training employees on best practices for maintaining a secure environment is a critical aspect of safeguarding any organization’s resources. When staff members are equipped with the knowledge and skills to recognize and respond to potential threats, the overall security posture of the organization improves. Proper education can prevent many common mistakes and enhance the ability to protect sensitive information, ensuring both internal and external risks are minimized.
Building a Security-Conscious Workforce
One of the most effective ways to strengthen an organization’s defenses is through consistent and relevant training. Employees should be educated on a variety of potential threats, such as phishing attempts, unauthorized access, and malware, and be made aware of the best practices to mitigate such risks. Encouraging a proactive approach to security, where employees feel responsible for the protection of company assets, can make a significant difference in preventing breaches.
- Phishing Awareness: Employees should be trained to recognize suspicious emails, links, and attachments, and to verify the authenticity of requests before responding.
- Strong Password Practices: Encourage the use of complex, unique passwords and the importance of regular password updates.
- Safe Browsing Habits: Teach staff to avoid visiting insecure websites and downloading unknown software, which could contain malware or malicious code.
Continuous Education and Simulation Exercises

Security training should not be a one-time event. Regular updates and simulated exercises help reinforce the knowledge employees have acquired and expose them to real-world scenarios. This ongoing education ensures that the workforce remains vigilant and adaptable to evolving threats. For example, phishing simulations can be used to test employee responses and provide feedback to improve their skills in identifying suspicious activities.
By making security training a core part of an organization’s culture, businesses can foster an environment where employees contribute to the overall safety of the digital space, reducing the likelihood of costly security incidents.
How to Stay Updated on Cyber Threats

Staying informed about the latest threats is crucial in maintaining a strong defense against potential attacks. As new risks emerge regularly, keeping up-to-date ensures that individuals and organizations can implement the right preventive measures in a timely manner. Regular monitoring of trusted sources and participating in ongoing education are key to identifying emerging dangers before they can cause harm.
Reliable Sources for Threat Intelligence
There are numerous platforms and organizations that provide valuable insights into the latest security risks. Relying on reputable sources helps ensure that you receive accurate and actionable information. Below are some of the most effective ways to stay informed:
- Security Blogs and Websites: Follow industry-leading blogs that regularly update readers on emerging threats and security trends. Sites like TechCrunch or SecurityWeek offer timely news and expert analyses.
- Social Media Channels: Many security experts and organizations share real-time updates through social platforms like Twitter and LinkedIn, making it easy to stay informed on the go.
- Threat Intelligence Services: Subscribing to threat intelligence services can provide tailored alerts and insights regarding specific threats that might affect your organization.
Participating in Security Communities and Forums
Engaging with online communities dedicated to security can provide access to collective knowledge and shared experiences. Active participation in forums allows individuals to exchange insights, ask questions, and stay updated on new vulnerabilities. Below are some valuable communities to explore:
- Reddit Security Subreddits: Subreddits like r/netsec and r/security provide discussions, updates, and advice on the latest trends and threats.
- Security Conferences and Webinars: Attending industry events, even virtually, helps professionals learn directly from experts and network with others in the field.
By regularly checking these sources and engaging with the community, individuals and businesses can stay ahead of threats and take proactive measures to protect their systems and data.
Taking the Security Knowledge Assessment
Engaging in a security knowledge assessment can help individuals and organizations evaluate their understanding of best practices for protecting sensitive information and systems. These assessments provide valuable insights into areas that may need improvement and help reinforce key principles of maintaining a secure environment. Participating in such evaluations is an essential step toward strengthening security protocols and building awareness about potential risks.
Benefits of Participating in the Assessment
Participating in this type of assessment can have several advantages, such as:
- Identifying Knowledge Gaps: The assessment allows participants to pinpoint areas where their security knowledge may be lacking, enabling focused improvements.
- Improving Security Practices: By answering questions about common security issues, participants can reinforce their understanding of effective protective measures.
- Boosting Confidence: Completing the assessment successfully can instill greater confidence in handling security-related challenges in real-life situations.
Types of Questions Covered
The assessment typically includes a variety of questions designed to test an individual’s knowledge on different aspects of security, such as:
| Topic | Description |
|---|---|
| Phishing | Questions related to identifying and avoiding deceptive emails or messages designed to steal sensitive information. |
| Password Management | Assessing knowledge of creating and maintaining strong passwords to protect accounts and sensitive data. |
| Malware Protection | Questions that focus on recognizing malware and understanding the importance of preventive measures like antivirus software. |
By addressing these topics and more, the security knowledge assessment helps ensure that individuals are well-prepared to defend against threats and contribute to a secure environment.