
In today’s digital age, safeguarding networks, systems, and sensitive information is more crucial than ever. As technology continues to evolve, so do the methods used by those seeking to exploit vulnerabilities. Understanding the core principles and strategies involved in defending against these threats is essential for anyone aspiring to excel in this field.
Preparing for an assessment in this area requires not only technical knowledge but also the ability to apply it effectively in real-world scenarios. It’s important to focus on key concepts, critical problem-solving techniques, and the latest developments in the field to ensure success. This guide offers insights into key topics and provides valuable information for mastering the skills required to protect information in an increasingly interconnected world.
Cyber Security Final Exam Answers
When preparing for an assessment in the field of protecting information and systems, it’s important to understand the underlying principles and tactics used to safeguard against online threats. Mastery of these concepts will not only help in assessments but also in real-world applications. The key to success lies in grasping both theoretical knowledge and practical skills to handle various challenges effectively.
Understanding Core Topics
Critical subjects often covered in this field include encryption techniques, ethical hacking, network defense strategies, and the identification of vulnerabilities. A strong foundation in these areas allows individuals to quickly analyze potential risks and respond with the appropriate countermeasures. Understanding how various tools and methods work together to form a robust defense system is essential for tackling complex scenarios.
Strategies for Success
To excel, focus on a comprehensive approach to studying. Instead of memorizing facts, try to apply concepts in simulated environments or real-world cases. Engage with practice scenarios, stay updated on new trends and threats, and take time to review past materials. Practical experience combined with theoretical knowledge will provide a well-rounded skill set, increasing the chances of success in both assessments and professional situations.
Understanding Key Cyber Security Concepts
To effectively protect networks, systems, and data from malicious activities, it is essential to understand the fundamental principles that form the foundation of this field. This involves grasping key strategies and techniques used to identify, prevent, and respond to various threats. A strong grasp of these core concepts is vital for anyone aiming to build a comprehensive defense against digital attacks.
One of the most important areas to understand is the concept of risk management. This includes identifying potential threats, assessing vulnerabilities, and implementing appropriate measures to mitigate those risks. Additionally, encryption, authentication protocols, and network monitoring play a crucial role in maintaining the integrity and confidentiality of sensitive information.
Common Topics in Cyber Security Exams
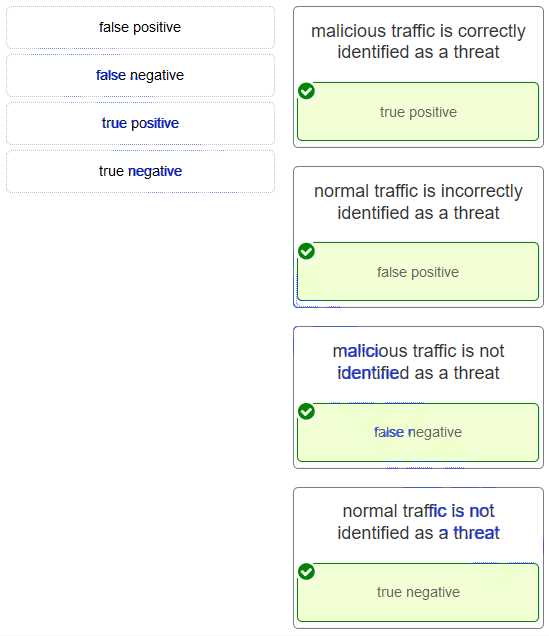
In any assessment related to the protection of digital systems, certain key areas consistently appear. These topics are crucial for understanding how to prevent, detect, and respond to various forms of online threats. Mastering these concepts is essential for anyone aiming to perform well in the field.
Among the most frequently covered subjects are encryption methods, firewalls, and intrusion detection systems. Additionally, topics like ethical hacking, vulnerability management, and incident response are often tested, as they are foundational to building a secure infrastructure. A solid understanding of these areas is necessary to ensure both theoretical knowledge and practical skills are applied effectively in real-world situations.
How to Prepare for the Exam
Effective preparation for an assessment in this field requires a structured approach. It is essential to cover both theoretical concepts and practical applications to ensure a well-rounded understanding of the subject. A combination of active study techniques, hands-on experience, and a focused review strategy will maximize your chances of success.
Develop a Study Plan
Start by creating a study schedule that allocates time for each important topic. Prioritize areas where you feel less confident and balance your time between reading materials and practicing hands-on skills.
- Focus on key areas such as encryption, network defense, and incident management.
- Review study materials and notes regularly to reinforce your understanding.
- Take breaks to avoid burnout and keep your mind sharp.
Practice with Real-World Scenarios
Theoretical knowledge alone is not enough. Practical experience is crucial for solidifying your understanding. Engage in simulations, labs, and exercises that mimic real-world situations to better prepare for the test.
- Set up your own virtual environment to test different security measures.
- Complete challenges related to identifying vulnerabilities and deploying solutions.
- Participate in online forums or groups to discuss common scenarios and solutions.
Effective Study Strategies for Cyber Security
Success in mastering the field of digital protection requires more than just passive reading. It involves an active and strategic approach to learning that combines theory with practice. Adopting the right study methods is crucial to ensure that you can not only retain information but also apply it in real-world scenarios.
One effective strategy is to break down complex topics into smaller, manageable sections. Focus on understanding the core concepts first before moving to advanced techniques. Combining different learning methods, such as reading, watching instructional videos, and participating in practical exercises, will help reinforce key points and improve retention.
Hands-On Practice
Real-world experience is invaluable when preparing for any assessment in this field. Set up a test environment to experiment with various tools and techniques. This will allow you to apply theoretical knowledge in a controlled setting and develop problem-solving skills.
- Create virtual networks to simulate attacks and defense strategies.
- Use online labs and challenges to practice identifying vulnerabilities and implementing solutions.
- Engage with simulated environments that reflect real-world scenarios.
Collaborative Learning
Studying with peers or mentors can significantly enhance your understanding. Collaborate on solving problems, share resources, and discuss various approaches to handling challenges. This interaction not only reinforces knowledge but also exposes you to different perspectives and techniques.
- Join study groups or online forums dedicated to this field.
- Participate in peer review sessions to test your knowledge and identify gaps.
- Ask questions and seek clarification on complex topics from experts.
Top Resources for Cyber Security Knowledge
Staying informed and up-to-date is crucial in the ever-evolving field of protecting digital assets. Leveraging reliable resources can significantly enhance your understanding and keep you ahead in this rapidly changing domain. From online platforms to books and certifications, there are many avenues to expand your expertise and sharpen your skills.
One of the most valuable resources is online learning platforms. These platforms offer structured courses and hands-on labs that allow you to learn at your own pace. Interactive exercises and expert-led sessions provide practical knowledge that can be directly applied in real-world situations. Many platforms also offer community discussions, where you can learn from peers and ask questions.
Recommended Online Platforms
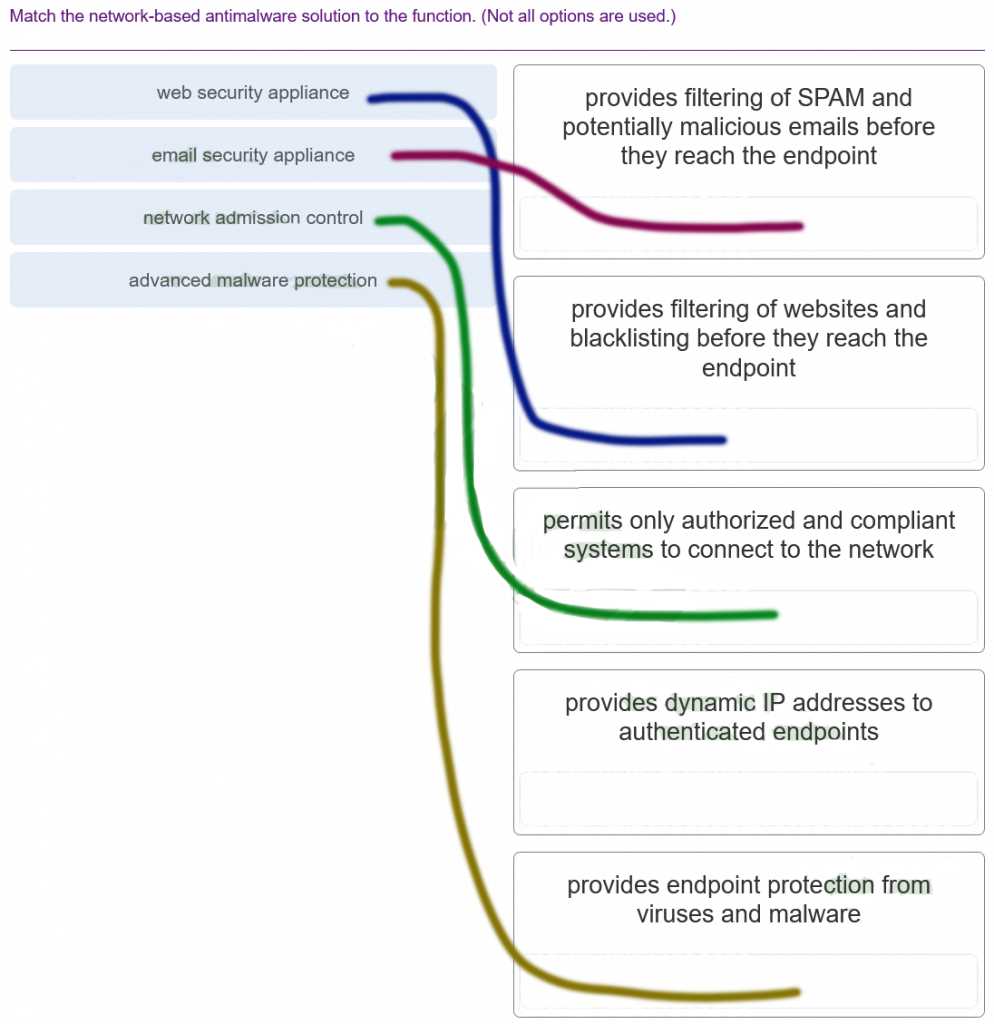
- Coursera – Offers courses from leading universities and institutions in the field of information protection.
- Udemy – Provides affordable courses that cover a wide range of topics, from basic principles to advanced techniques.
- Pluralsight – Specializes in tech and IT skills with extensive resources for both beginners and professionals.
Books and Text Resources
In addition to online learning, books remain an essential resource. Comprehensive textbooks can provide in-depth coverage of critical topics and offer structured content that serves as a solid foundation. Some books also come with practical examples and case studies, making them ideal for deeper understanding.
- The Web Application Hacker’s Handbook – A detailed guide to testing and securing web applications.
- Hacking: The Art of Exploitation – Focuses on the technical aspects of hacking and system exploitation techniques.
- Network Security Essentials – A great resource for learning network defense and vulnerability management.
Exam Tips for Cyber Security Students
Preparing for an assessment in the field of digital protection requires more than just memorizing facts. It’s essential to understand core concepts and be able to apply them effectively in different scenarios. A strategic approach to studying and proper time management can make a significant difference in achieving a strong performance.
Time Management and Prioritization
One of the key factors in performing well is managing your time effectively. Break down the material into smaller sections and focus on the most important topics first. Avoid cramming, as this can lead to information overload. Instead, allocate time for revision and practice regularly.
- Identify the core areas that are most likely to be covered in the assessment.
- Set specific goals for each study session to stay on track.
- Review notes and practice problems periodically to reinforce understanding.
Practical Application and Hands-On Practice
While theoretical knowledge is essential, practical application is just as important. Engage with labs, virtual simulations, and online challenges to apply what you have learned. Hands-on experience will help you solve real-world problems and improve your ability to respond quickly under pressure.
- Work with virtual environments to simulate different defense strategies.
- Participate in online competitions or challenges to test your skills.
- Revisit key practical tools and techniques, such as encryption methods and firewalls.
Important Security Protocols to Know

In the field of protecting information and digital infrastructures, certain protocols are fundamental to maintaining a strong defense against potential threats. These protocols govern how data is transmitted, encrypted, and verified, ensuring that communication remains secure and reliable. Understanding these protocols is essential for anyone involved in safeguarding networks and systems.
Common Encryption Protocols
Encryption plays a central role in protecting sensitive data. Various encryption protocols are designed to secure communication between devices, ensuring that information cannot be intercepted or altered during transmission.
- SSL/TLS – Used to secure connections between web browsers and servers, ensuring that data remains encrypted during transfer.
- IPSec – Protects data traffic at the IP layer, commonly used in virtual private networks (VPNs).
- PGP – A data encryption standard used to secure email communications.
Authentication and Authorization Protocols
Authentication protocols are essential for ensuring that users and systems are properly identified before they gain access to sensitive resources. Authorization protocols define what actions authenticated users are allowed to perform.
- OAuth – A widely used authorization framework that allows third-party applications to access user resources without exposing passwords.
- Kerberos – An authentication protocol used in distributed systems to verify the identity of users and services.
- RADIUS – Used for managing access to networks, particularly in remote authentication scenarios.
Ethical Hacking and Its Role in Cyber Security
In today’s digital landscape, identifying vulnerabilities before malicious actors can exploit them is critical. Ethical hacking, or penetration testing, plays a vital role in this proactive approach to protecting networks and systems. By simulating attacks in a controlled and authorized manner, professionals help organizations uncover weaknesses and strengthen defenses.
These experts use the same techniques as cybercriminals but with permission and for the purpose of improving security. Through rigorous testing, ethical hackers can pinpoint areas of risk and suggest solutions to fortify networks, applications, and infrastructures.
Key Areas of Ethical Hacking

- Vulnerability Assessments – Identifying weaknesses in software, hardware, and networks before they can be exploited.
- Penetration Testing – Simulating attacks to test the robustness of security measures and response strategies.
- Social Engineering – Assessing the human element by attempting to manipulate individuals into disclosing sensitive information.
Benefits of Ethical Hacking
By employing ethical hacking, organizations can enhance their defenses, meet compliance standards, and minimize the risk of costly breaches. The findings from these tests allow teams to patch vulnerabilities and implement stronger protections, keeping their digital assets secure.
- Early Detection – Spot vulnerabilities before malicious actors can exploit them.
- Compliance – Ensure adherence to regulations and industry standards.
- Incident Response – Improve the ability to respond quickly and effectively to potential threats.
Commonly Asked Questions in Cyber Security Exams

When preparing for assessments in the field of digital protection, understanding the types of questions commonly asked can greatly enhance your study strategy. These questions often focus on key concepts, protocols, and practical applications related to safeguarding networks, systems, and data. By becoming familiar with the common themes and structures of these questions, you can better prepare for the challenges you may encounter.
Sample Question Topics
Below is a table outlining some of the key areas that are frequently tested in assessments. These topics provide a good starting point for your review sessions.
| Topic | Question Examples |
|---|---|
| Network Protection | What are the differences between a firewall and an IDS? |
| Encryption Methods | How does RSA encryption work? |
| Authentication Protocols | What is the role of multi-factor authentication in access control? |
| Vulnerability Testing | Explain the process of performing a penetration test. |
Understanding Question Formats
These assessments often include both theoretical questions that test your knowledge of core concepts and practical questions that require you to apply your understanding. You may encounter multiple-choice questions, short answer questions, or scenario-based problems where you are asked to identify vulnerabilities and propose solutions.
Understanding Encryption and Its Importance
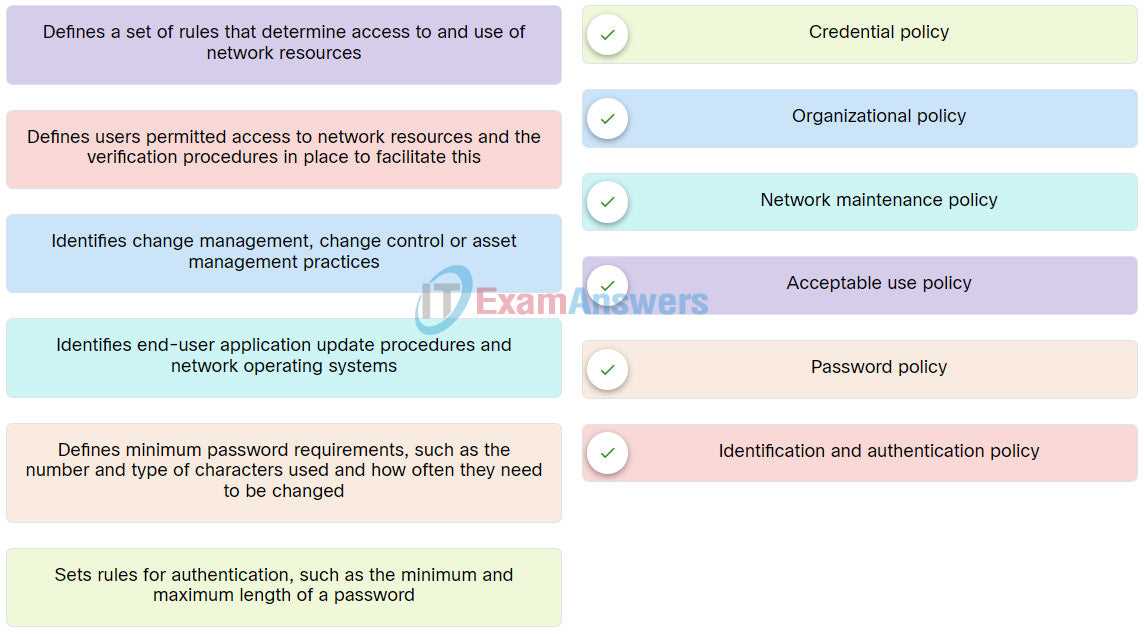
In today’s digital world, protecting sensitive information during transmission is crucial. One of the most effective ways to ensure that data remains confidential and secure is through the use of encryption. Encryption is a process that transforms readable data into a coded format, making it inaccessible to unauthorized users. This technique is fundamental in maintaining privacy and integrity across various systems, from email communications to online banking transactions.
How Encryption Works
Encryption relies on algorithms that use keys to transform plaintext data into ciphertext. Only those who possess the correct key can decrypt the data and restore it to its original form. This method ensures that even if data is intercepted during transmission, it cannot be read or misused without the decryption key.
- Symmetric Encryption – Involves the use of a single key for both encryption and decryption.
- Asymmetric Encryption – Uses a pair of keys: a public key for encryption and a private key for decryption.
The Role of Encryption in Digital Protection
Encryption plays a key role in protecting sensitive data from unauthorized access. Whether it’s safeguarding personal information, financial transactions, or communications, encryption ensures that only authorized parties can access and interpret the data. It helps to prevent data breaches, identity theft, and other forms of cybercrime, making it an essential component of any comprehensive digital defense strategy.
- Data Privacy – Protects personal and confidential information from being accessed by unauthorized individuals.
- Data Integrity – Ensures that data has not been altered or tampered with during transmission.
Cyber Security Threats and Vulnerabilities
As the digital landscape continues to evolve, so do the threats that target systems, networks, and sensitive data. Understanding the various types of risks and weaknesses that can be exploited is crucial for anyone working in this field. By identifying these threats and vulnerabilities, organizations can better prepare and defend against malicious actions that could compromise their digital infrastructure.
These vulnerabilities can stem from both technical weaknesses in software and hardware, as well as human errors. Once attackers identify a vulnerability, they exploit it to gain unauthorized access or cause damage to systems. It is essential to understand the different types of threats to create effective countermeasures.
| Threat Type | Description |
|---|---|
| Malware | Malicious software designed to damage or gain unauthorized access to a system. |
| Phishing | A form of social engineering where attackers trick individuals into revealing sensitive information. |
| Ransomware | Malicious software that locks users out of their system or data, demanding payment for restoration. |
| Denial of Service (DoS) | An attack that overwhelms a system or network, causing it to become unavailable to users. |
In addition to external threats, vulnerabilities can also arise from within an organization, such as outdated software, weak passwords, or inadequate employee training. Recognizing these internal weaknesses is just as important as defending against external attacks. A multi-layered defense strategy, which includes regular system updates, user awareness programs, and robust authentication protocols, is essential to minimizing risks.
Cyber Security Laws and Regulations
As the digital world continues to expand, the need for laws and regulations that govern the protection of sensitive data and systems becomes increasingly important. Legal frameworks are essential to ensure that individuals, businesses, and governments operate within safe and ethical boundaries when it comes to handling digital information. These laws are designed to regulate how data is stored, processed, and shared, and to establish clear guidelines for organizations on how to safeguard their networks and systems against unauthorized access or attacks.
Compliance with these regulations is not only crucial for protecting data but also for avoiding significant penalties and legal consequences. Failure to adhere to these laws can result in fines, legal actions, and damage to an organization’s reputation. Therefore, it is vital for businesses and individuals to stay informed about the evolving landscape of digital privacy and protection laws to remain compliant.
Several key regulations play a pivotal role in shaping the way data protection is approached across the globe:
- General Data Protection Regulation (GDPR) – A European Union regulation that focuses on data protection and privacy for all individuals within the EU and the European Economic Area (EEA).
- Health Insurance Portability and Accountability Act (HIPAA) – A U.S. law that mandates the protection of sensitive patient health information and imposes strict confidentiality standards in the healthcare industry.
- California Consumer Privacy Act (CCPA) – A California state law that enhances privacy rights and consumer protection for residents of California, focusing on transparency and control over personal data.
- Federal Information Security Management Act (FISMA) – A U.S. law that provides a comprehensive framework for ensuring the security of government information systems.
Understanding and adhering to these regulations is a critical component in managing digital risk. Organizations that follow legal guidelines can build stronger, more resilient systems that not only meet compliance requirements but also foster trust with their customers and clients.
Real-World Cyber Security Case Studies
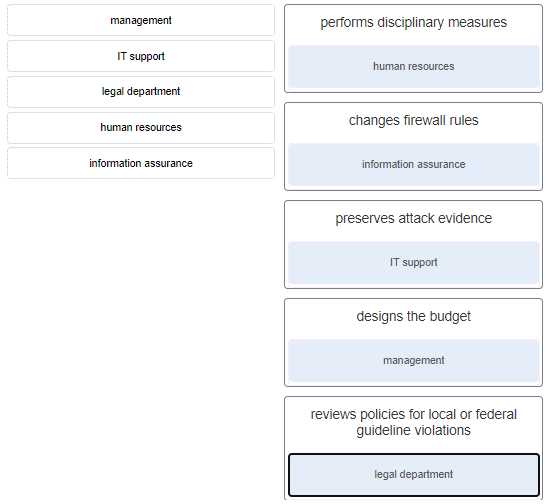
Understanding real-world incidents can provide invaluable insights into the complexities and challenges of protecting digital infrastructures. By studying past breaches and vulnerabilities, organizations can better prepare for similar threats and learn how to strengthen their systems. Case studies highlight the evolving tactics of attackers and the measures that can be taken to prevent or mitigate the impact of such incidents.
Below are several notable case studies that showcase both the risks and responses to significant digital threats:
| Case Study | Incident | Impact | Response |
|---|---|---|---|
| Equifax Data Breach (2017) | Hackers exploited a vulnerability in the company’s software, leading to the exposure of sensitive personal data of 147 million individuals. | Data including social security numbers, birth dates, and addresses were compromised. | Equifax offered free credit monitoring, but the breach highlighted the need for regular software updates and patch management. |
| WannaCry Ransomware Attack (2017) | A global ransomware attack spread through systems using Windows SMB protocol vulnerabilities. | Hundreds of thousands of computers were affected worldwide, including critical infrastructure like healthcare systems. | Systems that had not been patched were vulnerable, prompting widespread updates and stronger patch management practices. |
| Yahoo Data Breaches (2013-2014) | Hackers gained access to the accounts of over 3 billion users, stealing personal information. | Names, email addresses, phone numbers, and passwords were compromised. | Yahoo disclosed the breach in 2016 and took steps to improve their security practices, including two-factor authentication. |
These case studies demonstrate that digital threats are not only about the technology itself but also involve human and organizational factors. In many cases, a lack of proper protection measures or timely responses led to severe consequences. Understanding these incidents helps shape a proactive approach to risk management and prevention in today’s digital environment.
Practicing with Cyber Security Simulations
Engaging in realistic scenarios is an effective way to build practical skills and enhance problem-solving abilities when defending against digital threats. Simulations offer hands-on experiences that help individuals prepare for real-world challenges, providing a controlled environment to test various strategies and techniques. By practicing with simulations, learners can better understand how to identify, assess, and mitigate risks while reinforcing their technical knowledge.
Benefits of Simulated Environments
Participating in simulated exercises allows for immersive learning, where participants can:
- Develop a deeper understanding: Gain insights into how attacks unfold and learn to react effectively in a crisis.
- Test strategies: Experiment with different defensive tactics and evaluate their effectiveness in real-time situations.
- Improve decision-making: Sharpen the ability to make quick, informed decisions when under pressure.
- Enhance teamwork: Collaborate with others in a controlled setting to improve coordination and communication skills.
Types of Simulations to Try

There are various types of simulated exercises that can help learners strengthen their abilities:
- Capture the Flag (CTF) challenges: These competitions focus on solving problems related to hacking, encryption, and vulnerability exploitation.
- Penetration testing labs: These environments simulate real systems that need to be tested for weaknesses or vulnerabilities.
- Incident response simulations: These exercises involve managing a simulated attack scenario and responding to breaches, ensuring a structured and timely reaction.
By regularly participating in these activities, learners can stay up-to-date with the latest trends in digital defense and sharpen their skills to tackle increasingly sophisticated threats. The hands-on experience gained from simulations is an essential component of mastering the discipline and preparing for real-world situations.
Reviewing Past Cyber Security Exams
Going over previous assessments can be a powerful method for reinforcing knowledge and improving performance in future evaluations. By revisiting past tests, learners can identify the areas where they excelled and those that need further attention. This approach helps in understanding the types of questions typically asked and the concepts that are most often tested. It also serves as a valuable tool for assessing the depth of comprehension and identifying gaps in knowledge that may require additional focus.
Benefits of Reviewing Past Assessments

Revisiting past assessments offers several advantages, such as:
- Recognizing patterns: Identifying recurring themes or question types that frequently appear on assessments.
- Improving time management: Practicing under exam-like conditions helps in pacing oneself during actual tests.
- Strengthening weak areas: Pinpointing topics that need more study or hands-on practice to ensure a better understanding.
- Boosting confidence: Reviewing past successes can provide motivation and reassurance, leading to a more confident approach in future evaluations.
How to Effectively Review Past Tests
To make the most out of this practice, consider the following strategies:
- Focus on mistakes: Pay attention to the questions you got wrong or struggled with, and review the related material to ensure full understanding.
- Analyze explanations: Look at the explanations or solutions provided and try to grasp the reasoning behind them.
- Simulate the environment: Recreate exam conditions by timing yourself while answering past questions to improve speed and accuracy.
Incorporating these techniques into your study routine can enhance your readiness and ensure you’re well-prepared for any upcoming assessment. Reviewing past tests not only reinforces your knowledge but also helps you build a strategy for tackling similar questions in the future.
How to Stay Updated in the Field
Keeping up with the latest trends and developments in this rapidly evolving field is crucial for maintaining relevant knowledge and staying competitive. With constant advancements in technology and emerging threats, it is essential to stay informed through a variety of resources. Whether you are a professional or a student, there are many strategies you can employ to remain knowledgeable and prepared for new challenges.
Effective Ways to Stay Informed
Here are some practical ways to keep your skills and knowledge current:
- Follow industry news: Stay updated by reading articles, blogs, and news from trusted sources that cover new trends and incidents.
- Engage with online communities: Participate in forums, discussion groups, and social media channels where experts and peers share insights and advice.
- Subscribe to newsletters: Many websites and professional organizations send regular updates that summarize the latest developments and best practices.
- Attend webinars and conferences: Take advantage of online seminars, conferences, and workshops to learn about cutting-edge tools, techniques, and trends.
- Enroll in online courses: Continuously upgrade your knowledge by taking short courses or certifications offered by reputable institutions.
Additional Resources for Staying Updated
There are also specialized tools and platforms designed to keep professionals informed:
- Podcasts: Listening to expert podcasts is a great way to stay updated while on the go.
- Research papers: Read academic papers and case studies to deepen your understanding of emerging threats and innovative solutions.
- News aggregators: Use platforms like Google Alerts or RSS feeds to get real-time updates on topics that interest you.
By integrating these methods into your daily routine, you can ensure that you are always prepared for the latest developments and challenges in the field. Consistent learning and engagement are essential to advancing your expertise and maintaining a competitive edge.