
Studying for technical assessments in the field of modern technology requires a deep understanding of essential concepts and principles. Gaining a solid grasp of the core topics is crucial for excelling in any evaluation related to devices, networks, and software systems. This guide aims to provide a comprehensive overview of the subjects that are most commonly covered in such evaluations, helping you focus on what matters most.
Through this article, you will explore the critical aspects of the subject matter, ranging from system structures to network integration. Key principles such as security, platform differences, and application development will be addressed. Focusing on these core areas will not only enhance your knowledge but also prepare you for the types of challenges you may encounter in a formal setting. Effective preparation is about mastering these building blocks and being able to apply them in real-world scenarios.
Mobile Computing Exam Questions and Answers
Preparing for assessments in this field involves understanding various topics that are essential for success. These tests often evaluate your knowledge on system design, connectivity, and security in today’s digital landscape. To perform well, it’s important to familiarize yourself with the types of challenges that typically appear, including theoretical concepts and practical applications.
Key areas often explored include device architecture, wireless networks, and platform interoperability. Being able to explain how these components work together is essential. Additionally, understanding security protocols, data storage solutions, and user interface design will be beneficial. This section provides an overview of the subjects that you should focus on when revising for upcoming evaluations.
Overview of Mobile Computing Concepts

Understanding the fundamental principles that drive today’s portable technologies is crucial for mastering this field. At its core, this discipline involves the integration of hardware and software to enable users to perform tasks on the go. The primary focus is on the seamless interaction between devices, networks, and applications to provide continuous functionality across various environments.
Key Components of Modern Systems
Modern systems rely on multiple interconnected components to function effectively. These include hardware devices such as smartphones, tablets, and laptops, along with the software platforms that support applications and communication. The relationship between these elements is essential for ensuring smooth operation and optimal user experience.
Challenges in Connectivity and Security
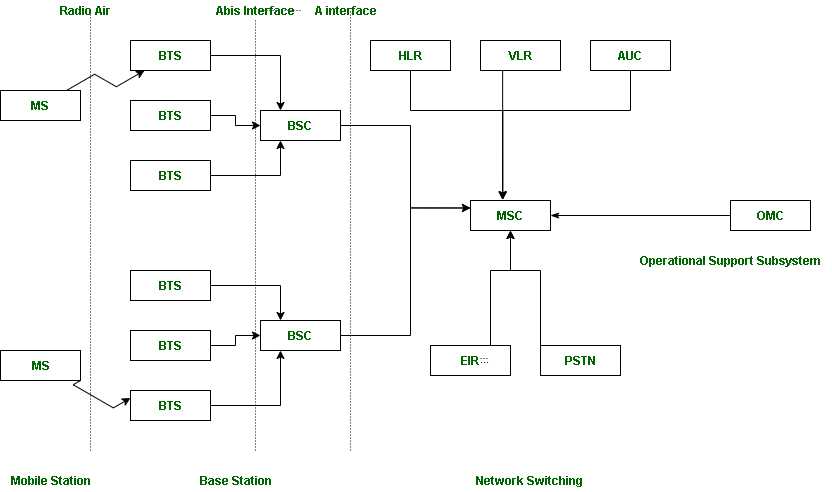
One of the main challenges in this field is ensuring reliable connectivity and maintaining security. As more devices are connected to various networks, the potential for data breaches and disruptions increases. Understanding encryption methods, secure communication protocols, and the risks involved is vital for navigating these complexities.
Commonly Asked Mobile Computing Questions
In any evaluation related to portable technology, certain topics tend to appear more frequently than others. These areas often revolve around core concepts, the functionality of devices, and their interaction with networks. By focusing on these key subjects, you can better prepare for common challenges that arise in assessments.
Frequently Discussed Topics
Some of the most commonly addressed themes in this area include system architecture, connectivity protocols, and security measures. The following table highlights some of the typical areas that are explored during assessments, along with their associated concepts.
| Topic | Description |
|---|---|
| Device Architecture | The structure and components of portable devices, including hardware and software interactions. |
| Networking | Various communication protocols and standards used to connect devices and exchange data. |
| Security Protocols | Methods for securing data and communications between devices, focusing on encryption and authentication. |
| Cloud Integration | The role of cloud services in expanding storage and processing capabilities for portable devices. |
| Application Development | Understanding how apps are created and optimized for use on portable devices, including cross-platform functionality. |
Common Challenges in Assessments
During evaluations, it is essential to demonstrate not only theoretical knowledge but also practical understanding of how these concepts work in real-world scenarios. Being able to apply knowledge to case studies or problem-solving situations is often a key focus in assessments.
Key Topics for Exam Preparation
When preparing for assessments in this field, focusing on specific areas is essential for ensuring success. Key subjects that frequently appear in evaluations revolve around understanding the relationship between devices, networks, and applications. By mastering these critical themes, you can increase your chances of performing well in any test or practical application scenario.
Key topics often include the principles of device functionality, communication protocols, and security measures. A solid understanding of how these elements interact and support each other will provide a strong foundation for handling a wide range of questions that may arise during evaluations. Whether it’s theoretical knowledge or real-world scenarios, these areas will likely be at the core of any challenge you encounter.
Understanding Wireless Communication Technologies

Effective communication between devices relies heavily on the use of wireless technologies, which enable the exchange of data without physical connections. These technologies are the backbone of modern connectivity, allowing information to be transmitted across different networks and systems. Gaining an in-depth understanding of how these systems operate is crucial for mastering the key concepts in this field.
Types of Wireless Communication

There are various types of wireless communication technologies that support different ranges and purposes. Each has unique characteristics and is suited to specific applications. Below are some of the most commonly used technologies:
- Wi-Fi: Provides high-speed internet access over short distances, commonly used in homes, offices, and public areas.
- Bluetooth: Allows for short-range communication between devices, often used for peripherals such as headphones or speakers.
- Cellular Networks: Supports mobile communication across wide areas, including voice calls, text messaging, and data transfer.
- Infrared: A short-range technology used for devices like remote controls or data transfer between devices in close proximity.
- Zigbee: Designed for low-power, low-data-rate applications, commonly used in home automation and IoT devices.
Key Challenges in Wireless Communication

While wireless technologies offer significant convenience, they come with their own set of challenges. Some of the main issues include:
- Interference: Signal disruptions caused by other devices or environmental factors can degrade performance.
- Security: Protecting data transmission from unauthorized access or breaches is a major concern in wireless networks.
- Bandwidth: Limited bandwidth in some wireless technologies can restrict data speeds, impacting user experience.
- Range: The effective range of certain technologies can be constrained, limiting their application in larger areas.
Mobile Operating Systems and Their Features
The foundation of any portable device’s functionality is the software that powers it. Operating systems specifically designed for these devices play a crucial role in managing hardware resources, running applications, and ensuring smooth user experiences. These systems are built to be lightweight and efficient, balancing performance and battery consumption to meet the needs of users on the go.
Each operating system has unique features that cater to different user preferences and device requirements. Some prioritize seamless integration with other systems, while others focus on offering a customizable environment or advanced security features. Understanding these distinctions is key for selecting the right platform or for preparing for assessments in this field.
| Operating System | Key Features |
|---|---|
| Android | Open-source, customizable, supports a wide range of applications, integrated Google services. |
| iOS | Intuitive interface, seamless integration with Apple ecosystem, strong security features. |
| Windows Phone | Live tiles interface, tight integration with Microsoft services, smooth multitasking. |
| Ubuntu Touch | Open-source, customizable, focuses on privacy and security, supports convergence. |
| HarmonyOS | Cross-platform support, fast performance, IoT and device interconnectivity features. |
Importance of Mobile Network Security
As portable devices become an integral part of daily life, ensuring the security of the networks they connect to is paramount. The increasing reliance on wireless communication for both personal and professional tasks has made these systems more vulnerable to various types of cyber threats. Protecting the data and maintaining the integrity of communications is essential to safeguard user privacy and prevent unauthorized access.
Security in wireless environments is particularly challenging due to the open nature of the communication channels. It is crucial to implement strong encryption methods, use secure protocols, and adopt best practices for device authentication. Failure to address these security concerns can lead to serious consequences, including data breaches, identity theft, and service interruptions. Protecting network infrastructure not only enhances user trust but also ensures that sensitive information remains safe from malicious attacks.
Exam Tips for Mobile Computing Success

Preparing for assessments in this field requires more than just understanding theoretical concepts; it involves strategic planning, time management, and effective study techniques. Mastering the key topics is important, but how you approach the preparation process can make a significant difference in your performance.
To help you succeed, here are some practical tips to guide your preparation:
- Understand Core Concepts: Focus on the fundamental principles, such as device architecture, wireless communication, and security protocols.
- Practice Real-World Scenarios: Apply your knowledge to practical examples and case studies. This will improve your problem-solving skills and better prepare you for practical questions.
- Review Past Assessments: Go through previous tests or practice papers to familiarize yourself with the format and types of questions that might appear.
- Stay Updated: Keep up with the latest trends and advancements in technology, as the field is constantly evolving.
- Manage Your Time: Allocate sufficient time to each topic, ensuring you cover all essential areas before the assessment date.
By following these tips, you can enhance your knowledge, increase your confidence, and improve your overall performance during evaluations in this dynamic field.
Mobile Computing Architecture and Models
The structure of a portable device’s functionality is driven by specific architectural models that define how the system interacts with both hardware and software. These frameworks are designed to optimize performance, connectivity, and scalability. Understanding the fundamental models behind these architectures is crucial for grasping how devices communicate, process data, and integrate into larger networks.
There are various models that represent different layers of interaction and functionality. These models provide guidelines for designing efficient systems that can support a variety of applications, from simple communication to complex computational tasks. A solid understanding of how these models work enables better decision-making when developing or managing such systems.
Key architectural models include:
- Client-Server Model: This model separates the roles of servers, which provide resources or services, and clients, which request them. It’s essential for understanding how information flows in distributed environments.
- Peer-to-Peer Model: In this decentralized architecture, devices directly exchange data with each other, reducing reliance on central servers. It’s often used in file-sharing systems.
- Cloud-Based Model: This approach relies on remote servers to store data and perform computational tasks, providing flexibility and scalability for users.
Adapting these models to specific needs is key to optimizing both performance and security in modern systems. Understanding their strengths and limitations helps ensure that the technology can evolve with new challenges.
Types of Mobile Devices and Platforms
In the world of portable technology, there is a wide variety of devices, each designed to meet different user needs and offer specific functionalities. These devices run on various software platforms that allow them to interact with applications, networks, and other systems. Understanding the different types of devices and platforms is essential for recognizing how they fit into the broader technology ecosystem and support various activities.
Different devices cater to diverse use cases, from basic communication tools to advanced personal assistants and entertainment systems. Similarly, the platforms that power these devices offer distinct features that affect usability, security, and compatibility. Below are some of the most common devices and platforms:
Types of Devices

- Smartphones: Portable communication devices with advanced capabilities, including internet access, applications, and multimedia support.
- Tablets: Larger, touchscreen devices ideal for media consumption, browsing, and productivity tasks. They offer portability similar to smartphones, with more screen space.
- Smartwatches: Wearable devices that offer notifications, health tracking, and other functionalities, often paired with smartphones for enhanced features.
- Laptops: While primarily designed for computing tasks, modern laptops often come with mobile capabilities, including portability and wireless connectivity.
- E-readers: Specialized devices designed for reading digital books, offering features like long battery life and e-ink screens for easy reading.
Common Platforms
- Android: An open-source platform developed by Google, widely used across a range of devices, from smartphones to tablets and wearables.
- iOS: Apple’s proprietary operating system, known for its seamless integration across devices like iPhones, iPads, and smartwatches.
- Windows: A versatile platform used on laptops, tablets, and some mobile devices, offering strong compatibility with desktop applications and services.
- Linux-based OS: Open-source operating systems like Ubuntu Touch and Tizen, used in various smart devices and IoT applications.
By understanding these devices and platforms, users can better navigate the landscape of portable technology and make informed decisions based on their needs.
Frequently Tested Mobile Computing Algorithms
In the realm of portable device technologies, certain algorithms are frequently tested due to their crucial role in optimizing performance, efficiency, and reliability. These algorithms govern how data is processed, transmitted, and stored across various systems, and understanding them is vital for both developers and users. Whether focusing on wireless communication, data compression, or network routing, each algorithm plays a significant role in enhancing device functionality.
Below are some key algorithms that are commonly tested in assessments related to portable systems:
- Routing Algorithms: These algorithms determine the most efficient paths for data to travel across networks, ensuring fast and reliable communication between devices.
- Compression Algorithms: Used to reduce the size of data for faster transmission over limited bandwidth, these algorithms help optimize storage and improve overall device performance.
- Encryption Algorithms: These are critical for securing communications and protecting sensitive data from unauthorized access, ensuring privacy in wireless networks.
- Scheduling Algorithms: Employed to manage the distribution of tasks in multitasking systems, ensuring optimal use of device resources and efficient performance.
- Cache Management Algorithms: These algorithms help manage the temporary storage of frequently accessed data, improving speed and reducing the need for constant data retrieval.
- Network Access Algorithms: These are used to regulate the way devices access and share network resources, optimizing performance in environments with multiple devices and users.
Mastering these algorithms can significantly improve your understanding of how portable systems function and how they handle critical tasks such as communication, security, and resource management.
Questions on Cloud Computing Integration

In today’s tech landscape, integrating remote data storage and services has become increasingly important. Understanding how different systems, devices, and applications interact with cloud resources is key to developing efficient, scalable solutions. The integration of external platforms and cloud services plays a major role in how data is accessed, processed, and stored, enabling seamless functionality across various systems.
Several important aspects must be considered when exploring cloud system integration, ranging from security protocols to data synchronization techniques. The following sections will cover common areas of focus related to this topic:
Key Considerations for Integration

- Data Security: How can sensitive information be securely transmitted and stored in cloud environments?
- Service Compatibility: What challenges arise when integrating different service providers and platforms with existing infrastructure?
- Scalability: How do cloud-based systems scale to meet the growing demands of users and applications?
- Reliability: What measures ensure that cloud services remain reliable and available even during peak usage periods?
Popular Integration Models
- Hybrid Cloud: What benefits and challenges exist when combining public and private cloud systems for enhanced flexibility and security?
- Multi-Cloud: How does using multiple cloud service providers impact performance, risk management, and costs?
- Cloud-Native Applications: How are applications developed specifically to run within cloud environments optimized for performance and scalability?
By understanding these integration strategies and their associated challenges, individuals can gain a deeper insight into how cloud resources enhance the capabilities of modern systems and services.
Data Storage Solutions in Mobile Computing
In today’s world of portable devices, efficient data management is crucial for ensuring both performance and security. With limited storage capacity and the need for quick data access, choosing the right storage solution is essential for users and developers. From on-device storage to cloud-based options, various strategies are employed to store, retrieve, and protect data across diverse systems. Each approach offers its unique advantages and limitations depending on the needs of the user or application.
Below are some common data storage solutions used in portable systems:
| Storage Type | Description | Advantages | Limitations |
|---|---|---|---|
| Flash Storage | Solid-state storage integrated into devices for local data saving. | Fast access speeds, durable, energy-efficient. | Limited capacity, potential data loss over time. |
| Cloud Storage | Remote storage managed by third-party service providers, accessible via the internet. | Large capacity, accessible from anywhere, scalable. | Dependent on internet access, potential security risks. |
| Hybrid Storage | A combination of on-device and cloud-based storage for balanced data management. | Combines the benefits of local speed and cloud scalability. | Complex management, higher cost. |
| External Storage | Physical media, such as microSD cards or USB drives, used to extend device storage. | Portable, easy to upgrade capacity. | Vulnerable to physical damage, slower data transfer rates. |
Choosing the appropriate storage solution depends on various factors, including the type of device, data security requirements, and the need for mobility. Balancing local storage with cloud integration can optimize performance and reliability in modern portable systems.
Challenges in Mobile Computing Environments
As the use of portable devices becomes more widespread, ensuring smooth and efficient operations in diverse environments remains a significant challenge. The unique constraints of these systems–such as limited resources, varying network conditions, and the need for high levels of user mobility–pose considerable obstacles. Addressing these challenges requires innovative solutions that balance performance, security, and usability.
Key Issues in Portable Systems
- Limited Battery Life: Devices often struggle to maintain long-lasting power while performing resource-intensive tasks, requiring efficient energy management.
- Network Instability: Variability in network connectivity can hinder performance, especially when relying on cloud services or remote access for data.
- Data Security and Privacy: Ensuring data protection on portable systems is more complex due to the risk of unauthorized access and data breaches.
- Hardware Constraints: Portable devices often have limited processing power, memory, and storage, making it difficult to handle large-scale applications.
- Synchronization: Keeping data synchronized across multiple devices and platforms is a persistent challenge, especially when dealing with inconsistent connectivity.
Overcoming the Obstacles
While the challenges in portable environments can seem daunting, various solutions have emerged to tackle these issues. For instance, energy-efficient hardware, advanced encryption protocols, and adaptive network technologies help address some of the most pressing concerns. Additionally, hybrid architectures combining local and cloud resources are increasingly being used to mitigate limitations and improve overall performance. By employing these strategies, developers and users can navigate the complexities of modern portable systems with greater success.
Preparing for Real-World Mobile Scenarios
In today’s fast-paced technological landscape, understanding the practical application of portable devices is essential. Being prepared for real-world situations requires more than just theoretical knowledge; it involves understanding how to navigate the complexities of using these systems under various conditions. This includes dealing with fluctuating network connectivity, managing limited resources, and ensuring seamless interaction between different platforms and services.
Practical Considerations in Fieldwork
- Efficient Resource Management: Devices often operate under constraints such as limited processing power and storage, so efficient use of resources is crucial.
- Network Adaptability: Users need to be prepared to handle varying network conditions, from high-speed connections to unreliable or slow signals.
- Real-Time Data Synchronization: Ensuring data consistency and synchronization across devices, especially in remote locations, is a key factor in successful operations.
- Security and Data Integrity: Protecting sensitive information and ensuring that data remains intact during transmission are critical, especially in decentralized environments.
- System Integration: Effective integration of hardware, software, and services is necessary to ensure smooth operations across diverse platforms and devices.
Strategies for Success in Real-World Situations
To effectively address the challenges faced in practical scenarios, it’s important to implement robust solutions. Employing technologies that allow for offline capabilities, such as local data caching, can help manage connectivity issues. Additionally, using adaptive algorithms to adjust power consumption and resource usage based on real-time conditions can extend the life of portable devices. Moreover, adopting a layered approach to security, including encryption and authentication protocols, ensures that sensitive information remains secure, even in dynamic environments.
Mobile Application Development Overview
Creating applications for portable devices involves a series of stages, from initial concept to deployment. The development process requires knowledge of both the hardware constraints of the device and the specific software environment. Whether building apps for smartphones, tablets, or other handheld devices, developers must ensure functionality, performance, and user experience are optimized across varying operating systems and device specifications.
Successful development not only includes writing the core code but also understanding the different tools, frameworks, and programming languages available. Additionally, developers must account for design principles that prioritize user interfaces and experience, as well as integrate key features such as data storage, network connectivity, and security measures to ensure that the application works seamlessly in the real world.
Best Resources for Exam Preparation
Preparing effectively for any assessment requires access to the right materials and tools. There are various resources available that can help candidates deepen their understanding of core concepts and improve their problem-solving skills. These materials range from textbooks and online courses to practice tests and discussion forums. Using a variety of resources ensures that the learner is well-equipped to tackle diverse topics that may be covered during the evaluation.
Online platforms and educational websites often offer structured learning paths, including video lectures and quizzes that mirror real-world scenarios. Moreover, joining study groups or seeking guidance from experts can also provide valuable insights and help reinforce key ideas. By exploring a combination of theoretical and practical approaches, individuals can enhance both their theoretical knowledge and practical application skills.