
Understanding how to investigate and interpret electronic evidence is crucial in today’s interconnected world. This field involves uncovering and analyzing data to provide insights and solve complex issues. Preparing effectively ensures you can approach these scenarios with confidence and expertise.
The process includes various methodologies, tools, and techniques designed to extract valuable information. By exploring common scenarios and their solutions, individuals can enhance their problem-solving abilities and deepen their knowledge.
This article provides structured insights into essential topics, including practical methods, technical tools, and preparation strategies, offering a comprehensive resource for success.
Understanding Digital Forensics Basics
Investigating modern electronic systems requires a clear understanding of how data is stored, transmitted, and manipulated. This foundation is essential for identifying issues, interpreting information, and drawing reliable conclusions in technological environments.
- Data Structures: Learn how information is organized within devices to better recognize key patterns and anomalies.
- Storage Media: Explore different types of devices, from hard drives to solid-state systems, and their unique properties for retaining information.
- Information Recovery: Gain insights into methods used to retrieve lost or hidden data effectively.
Building expertise in these areas helps individuals understand how to manage information systems securely, troubleshoot issues, and ensure a thorough approach to data interpretation.
Key Concepts in Digital Investigations
Analyzing electronic data requires a solid grasp of foundational principles that guide the process of uncovering and interpreting evidence. These principles ensure accurate methods for examining various systems while maintaining the integrity of the information.
Chain of Custody: Maintaining a detailed record of how information is collected, handled, and stored is essential for preserving its reliability and admissibility in further use.
Data Acquisition: The process of extracting relevant information from devices without altering the original content is a critical skill, requiring specialized tools and procedures.
Integrity Verification: Ensuring that collected data remains unaltered is achieved through hash values or similar techniques, providing a reliable way to validate authenticity.
These principles form the foundation for effective practices, enabling investigators to extract meaningful insights and ensure their findings meet professional standards.
Common Tools Used in Cyber Forensics

Effectively analyzing electronic information requires specialized software and hardware designed for collecting, processing, and interpreting data. These tools simplify complex tasks and ensure the accuracy of investigations.
Software Solutions
| Tool Name | Primary Function |
|---|---|
| Data Extraction Suite | Retrieves information from various storage devices. |
| Network Analysis Platform | Monitors and captures online activity for detailed inspection. |
| Decryption Utility | Unlocks encrypted data for further examination. |
Hardware Tools
Devices used to access and examine physical media include portable readers and duplication systems. These tools help capture data directly from drives or memory cards without altering the original source.
Combining these tools provides comprehensive capabilities, enabling specialists to handle a wide range of scenarios with precision and confidence.
Preparing for Forensic Certification Exams
Achieving certification in electronic data analysis requires thorough preparation and a clear understanding of the material. This involves studying core concepts, practicing techniques, and familiarizing yourself with exam formats.
Building a Strong Knowledge Base

Focus on key areas, such as data recovery, system analysis, and network monitoring. Comprehensive guides and study materials can help reinforce your understanding and fill any knowledge gaps.
Practicing with Real-World Scenarios
Hands-on experience is invaluable. Use practice environments or simulators to replicate actual situations, allowing you to apply theoretical knowledge in practical contexts. This not only improves your skills but also boosts confidence for test day.
By combining structured study with practical application, you can ensure a well-rounded approach to certification preparation, maximizing your chances of success.
Analyzing Evidence in Computer Systems
Understanding how to examine data within computing environments is essential for identifying key information and uncovering hidden details. This process relies on structured methods and specialized tools to ensure thoroughness and accuracy.
Key Steps in Data Examination
- Data Identification: Locate relevant information stored across drives, memory, or other components.
- Preservation Techniques: Create exact copies of the data to prevent alterations to the original source.
- Extraction Processes: Retrieve specific files or traces of activity from the system for closer inspection.
Common Techniques for Analysis
- Examining file metadata to uncover timestamps or user actions.
- Reconstructing deleted files or fragmented data using recovery tools.
- Searching for traces of malicious activity through system logs or processes.
By following these methods, investigators can ensure the evidence gathered is accurate, complete, and ready for further interpretation or reporting.
Challenges in Investigating Cybercrimes

Investigating online criminal activities presents unique difficulties due to the nature of the internet and the tools involved. These challenges require advanced techniques, specialized knowledge, and an adaptable approach to overcome effectively.
Common Obstacles Faced

- Data Encryption: Criminals often use encryption to protect sensitive information, making it difficult to access crucial evidence.
- Anonymity Tools: Technologies like VPNs and proxy servers allow offenders to hide their identity and location, complicating the tracing process.
- Volatile Data: Important evidence may disappear quickly from online systems, requiring swift and accurate collection methods.
Technological Barriers
- Fast-evolving technologies can outpace investigative tools and methods, requiring continuous adaptation to new threats.
- The vast amount of data generated during an investigation can be overwhelming, requiring effective filtering and analysis techniques.
Despite these challenges, specialized tools and ongoing training allow investigators to address these issues and pursue justice in complex online crime cases.
Legal Considerations in Digital Investigations
When conducting investigations involving electronic evidence, it is essential to navigate a range of legal considerations to ensure that procedures are followed correctly and evidence is admissible in court. This area requires understanding laws related to privacy, consent, and data handling, as well as the potential consequences of mishandling evidence.
Key Legal Aspects to Keep in Mind
| Legal Issue | Description |
|---|---|
| Privacy Rights | Protecting personal information during investigation to comply with privacy laws and avoid infringement. |
| Search Warrants | Ensuring the proper legal authorization is obtained before accessing personal devices or online accounts. |
| Chain of Custody | Maintaining an unbroken record of evidence from collection to presentation in court to avoid tampering claims. |
Ensuring Compliance with Laws
It is crucial to comply with local, national, and international laws governing electronic evidence. Investigators must be aware of the specific legal frameworks that govern their region and ensure they follow correct procedures to avoid legal challenges later on.
By understanding the legal environment, investigators can conduct thorough, lawful inquiries that uphold the integrity of the process and the results.
Practical Scenarios in Forensics Exams
In any assessment related to cyber investigations, practical scenarios are often included to test an individual’s ability to apply theoretical knowledge in real-world situations. These exercises simulate challenges one might face during an actual investigation, requiring candidates to solve problems using available tools and techniques.
Common Practical Challenges
These types of scenarios typically present complex problems that require a logical and systematic approach. Below are some examples of what candidates might encounter:
- Data Recovery: Restoring deleted files from a corrupted hard drive or storage device.
- Evidence Identification: Identifying key pieces of information from a large set of data, such as logs or emails.
- Authentication: Verifying the integrity of the data and ensuring it hasn’t been tampered with during the investigation.
Approaching Practical Scenarios

To successfully complete these tasks, it is essential to have a clear methodology and understand how various tools and techniques work in practice. Applying a structured approach helps candidates to not only solve the problem at hand but also to document their findings accurately for future legal proceedings or analysis.
By engaging in these types of practical scenarios, individuals can better prepare for real-world situations where quick thinking and methodical procedures are essential to uncovering the truth.
Strategies for Answering Forensic Questions
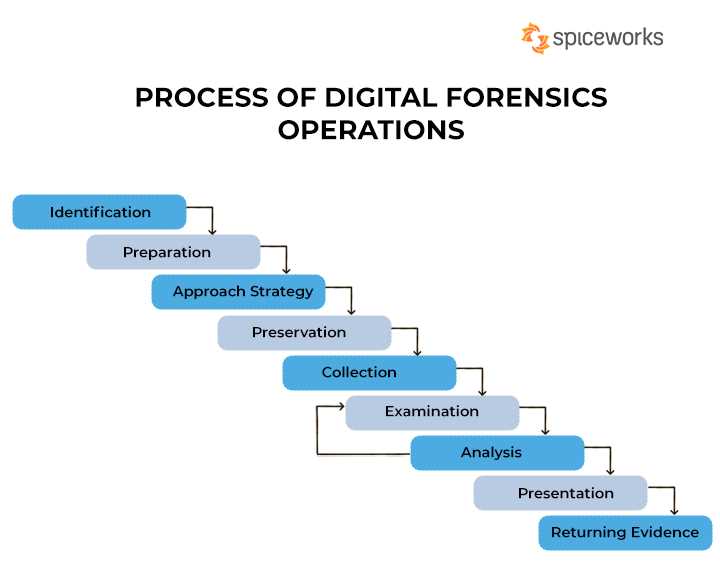
When tackling questions in cyber investigation assessments, a structured approach is crucial for providing accurate and well-supported responses. The key lies in understanding the problem, breaking it down into manageable components, and applying relevant techniques and knowledge to each aspect. The following strategies can help in navigating these complex tasks effectively.
Understanding the Question
The first step is to thoroughly read and understand what is being asked. Often, questions may include multiple parts or require a step-by-step solution. It is important to identify key terms and concepts, which can guide the response. Pay attention to the context provided, such as any data sources or technical challenges, to ensure that the answer is relevant.
Applying Knowledge and Tools
Once the question is understood, the next step is to apply your knowledge and the appropriate tools for the investigation. This could involve analyzing data, using software for recovery or extraction, or interpreting logs and reports. It’s essential to stay systematic and detail-oriented, making sure each step in your process is well-documented and justifiable. These responses often require demonstrating a combination of technical skills and analytical thinking.
By combining these strategies, individuals can improve their ability to answer complex scenarios effectively, ensuring that their responses are both accurate and comprehensive.
Insights into Mobile Device Analysis
Mobile devices have become a primary source of digital evidence, as they contain vast amounts of data, including personal communications, geolocation information, and application logs. Analyzing these devices requires specialized methods and tools, as well as an understanding of their unique characteristics. Below are key elements involved in analyzing mobile devices effectively.
Types of Data in Mobile Devices
Mobile devices store a wide range of data types, each offering valuable insights. The most common data categories include:
- Text Messages: SMS and chat logs from various apps.
- Call History: Records of incoming, outgoing, and missed calls.
- Location Data: GPS data and geotagged content from photos.
- Application Data: Data stored within apps, including caches, cookies, and user-specific information.
- Multimedia: Photos, videos, and audio recordings that may provide evidence of actions or communications.
Common Techniques for Mobile Device Investigation
To effectively retrieve and analyze data from mobile devices, investigators often employ the following techniques:
- Data Extraction: Using physical or logical methods to extract data from the device.
- Forensic Imaging: Creating an exact copy of the device’s data to ensure no tampering.
- App Analysis: Investigating installed apps for hidden or deleted data.
- Cloud Analysis: Examining cloud backups associated with the device for additional information.
Understanding these elements is crucial for investigators looking to uncover relevant information from mobile devices. Effective mobile device analysis relies on the ability to use the right tools and techniques while adhering to legal and ethical standards in handling data.
Network Forensics and Traffic Analysis
Investigating network-based incidents requires examining data traffic and identifying patterns that can reveal unauthorized access, malware activity, or other suspicious events. This process involves capturing, monitoring, and analyzing network communications to track the source of attacks and understand the actions taken within a network. Below are key aspects of network traffic analysis and the methods used to uncover hidden threats.
Key Elements of Network Traffic
Network communications carry various types of information, which investigators can analyze to detect malicious activity. Common elements include:
- Packet Capture: Monitoring network packets to examine data sent across the network.
- Protocol Analysis: Understanding different network protocols and identifying irregularities or unauthorized usage.
- IP Address and Port Tracking: Identifying the source and destination of traffic to pinpoint potential attackers.
- Traffic Flow: Examining the volume and patterns of traffic to spot anomalies.
Techniques Used in Network Traffic Investigation
To investigate network incidents effectively, various techniques are employed to capture and analyze data in real-time:
- Packet Sniffing: Using specialized tools to capture data packets moving across the network, allowing investigators to inspect content in detail.
- Flow Analysis: Analyzing the metadata of network traffic, such as the number of packets and the duration of sessions, to identify potential malicious activity.
- Log Review: Analyzing logs from network devices like routers, firewalls, and servers to trace any unusual events or breaches.
Network-based investigations are critical for uncovering attacks that bypass traditional security measures. Effective traffic analysis involves utilizing a combination of real-time monitoring, data capture tools, and an understanding of network behavior to ensure a comprehensive investigation.
Using Case Studies to Understand Forensics
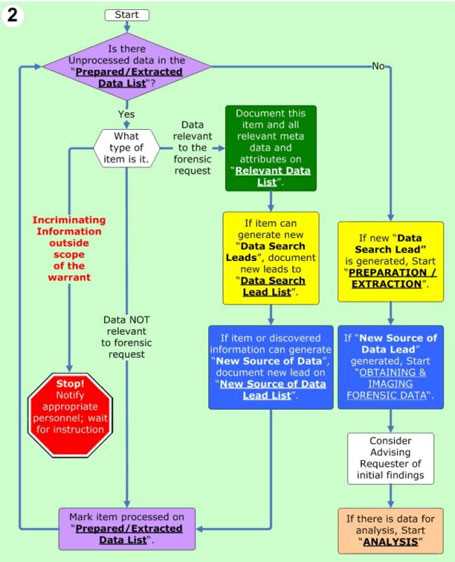
Examining real-world incidents offers valuable insights into the investigative process, helping to bridge the gap between theory and practice. By analyzing past cases, professionals can gain a deeper understanding of the techniques, challenges, and strategies used in solving complex investigations. Case studies provide a practical perspective that enhances learning and prepares individuals for real-life scenarios in the field of security and investigation.
Through detailed case studies, investigators can explore various types of incidents, including hacking, data breaches, and insider threats. These examples illustrate how evidence is collected, analyzed, and interpreted to uncover the truth. Additionally, studying the outcomes of previous cases reveals the effectiveness of different methodologies and the critical decisions made during the investigation.
By reflecting on the approaches used in these cases, professionals can refine their skills, adapt to evolving threats, and improve their problem-solving abilities. Case studies not only enhance technical knowledge but also help develop critical thinking and decision-making skills, which are essential for tackling complex security issues.
Examining Data Recovery Techniques
Recovering lost or corrupted information is a crucial aspect of many investigations. Whether dealing with accidental deletions, hardware malfunctions, or malicious attacks, the process of retrieving data requires specialized tools and methods. Understanding these techniques is essential for retrieving valuable evidence and ensuring that no crucial information is left behind.
There are various methods employed to recover data from damaged or compromised devices. These methods range from simple software-based recovery tools to more advanced techniques, such as working directly with the device’s hardware. The choice of technique depends on the type of damage, the file system in use, and the urgency of the recovery process.
Some of the most commonly used recovery techniques include file carving, which involves searching for fragments of deleted files, and imaging, where a sector-by-sector copy of the storage medium is created to preserve the original data intact. Additionally, advanced data recovery tools can be used to bypass encrypted or password-protected files, helping to uncover hidden information.
Tips for Identifying Hidden Evidence
Uncovering concealed information requires keen observation and an understanding of where and how evidence may be hidden. Investigators often face the challenge of finding data that has been deliberately concealed through various means, such as encryption, steganography, or hidden partitions. Recognizing the methods used to hide such evidence is key to uncovering it effectively.
Understanding Common Concealment Techniques
There are several common techniques used to hide data, including:
- Encryption: Data may be encrypted to prevent unauthorized access, requiring the correct decryption key to access the content.
- Steganography: Information may be hidden within other files, such as images or audio files, making it difficult to detect without specialized tools.
- Hidden Partitions: Some devices may have hidden or unallocated disk partitions that store files away from regular access.
Tools and Methods for Detection

To successfully identify hidden evidence, investigators can use specialized software tools that scan for hidden files and anomalies. Some common methods include:
- Using file carving techniques to recover deleted or hidden files from unallocated space.
- Analyzing file metadata for unusual patterns or inconsistencies.
- Using forensic imaging tools to create exact copies of storage devices and analyze them without altering the original evidence.
Role of Encryption in Investigations
Encryption plays a critical role in safeguarding information, but it also presents significant challenges for investigators seeking to uncover hidden data. By converting data into a format that is unreadable without the correct decryption key, encryption protects sensitive information from unauthorized access. However, this protection can hinder the investigative process, as investigators must find methods to break or bypass encryption in order to access potentially crucial evidence.
While encryption is often seen as a tool for privacy and security, its use in criminal activities can complicate investigations. Criminals may use encrypted devices or communications to conceal illegal actions, making it more difficult for investigators to access relevant information. Understanding encryption algorithms and having the right tools are essential for overcoming these obstacles in investigations.
Forensics in Cloud Computing Environments
As more organizations and individuals move their data and applications to cloud-based systems, the complexities of investigating potential incidents in these environments increase. Unlike traditional on-premise storage, cloud platforms involve multiple layers of infrastructure, third-party providers, and distributed data storage, which can make tracing and recovering evidence more challenging. The decentralized nature of the cloud, along with the dynamic management of data, requires specialized tools and techniques for effective investigation.
Investigating within cloud computing environments involves handling unique challenges such as data volatility, jurisdictional issues, and the need for cooperation between cloud service providers and law enforcement. Cloud service models like SaaS, PaaS, and IaaS introduce different concerns for maintaining integrity, acquiring data, and ensuring that all relevant evidence is collected in a legally acceptable manner.
Career Paths in Digital Forensics
A career in the field of technology-driven investigations offers numerous opportunities to individuals interested in problem-solving, security, and technology. Professionals in this area play a crucial role in uncovering evidence, identifying cybercrimes, and securing data. This sector requires a strong foundation in computer systems, an understanding of legal frameworks, and the ability to adapt to rapidly evolving technologies.
Individuals can pursue various career paths, depending on their interests and expertise. Some roles focus on technical analysis, where experts extract and interpret data from devices and networks. Others may involve working alongside law enforcement agencies, advising on the legal aspects of digital evidence. Regardless of the path chosen, professionals in this field often work under pressure and must stay updated with the latest trends in technology and security.
Key Roles in the Field
- Incident Responder: This role involves identifying, analyzing, and responding to potential security breaches or cyber-attacks, ensuring that digital evidence is preserved for further examination.
- Cybersecurity Analyst: Analysts focus on protecting systems and networks from cyber threats, often working in tandem with incident responders to secure evidence before an attack can cause significant damage.
- Forensic Expert: These professionals specialize in collecting and analyzing evidence from compromised systems, ensuring that all digital traces are properly handled for legal proceedings.
Skills and Certifications

To succeed in this dynamic field, candidates typically require a combination of technical skills, attention to detail, and an understanding of both technology and law. Certifications such as Certified Information Systems Security Professional (CISSP) or Certified Ethical Hacker (CEH) can enhance one’s credibility and qualifications. As technology continues to evolve, professionals must be adaptable and prepared to learn new tools and methodologies to stay effective in their roles.