In this section, we will explore essential concepts and techniques to help you successfully navigate the core elements required for your certification. The focus is on understanding key systems and commands, as well as troubleshooting strategies that are critical for anyone aiming to achieve proficiency in this field.
As you prepare for the certification, it is important to familiarize yourself with common topics, such as user management, file systems, and network configurations. A clear understanding of these subjects will not only help you excel in assessments but also strengthen your practical skills for real-world applications.
Through carefully structured explanations and targeted practice, you will gain the knowledge needed to approach the certification process with confidence. Consistent practice and focused study are key to mastering these areas effectively.
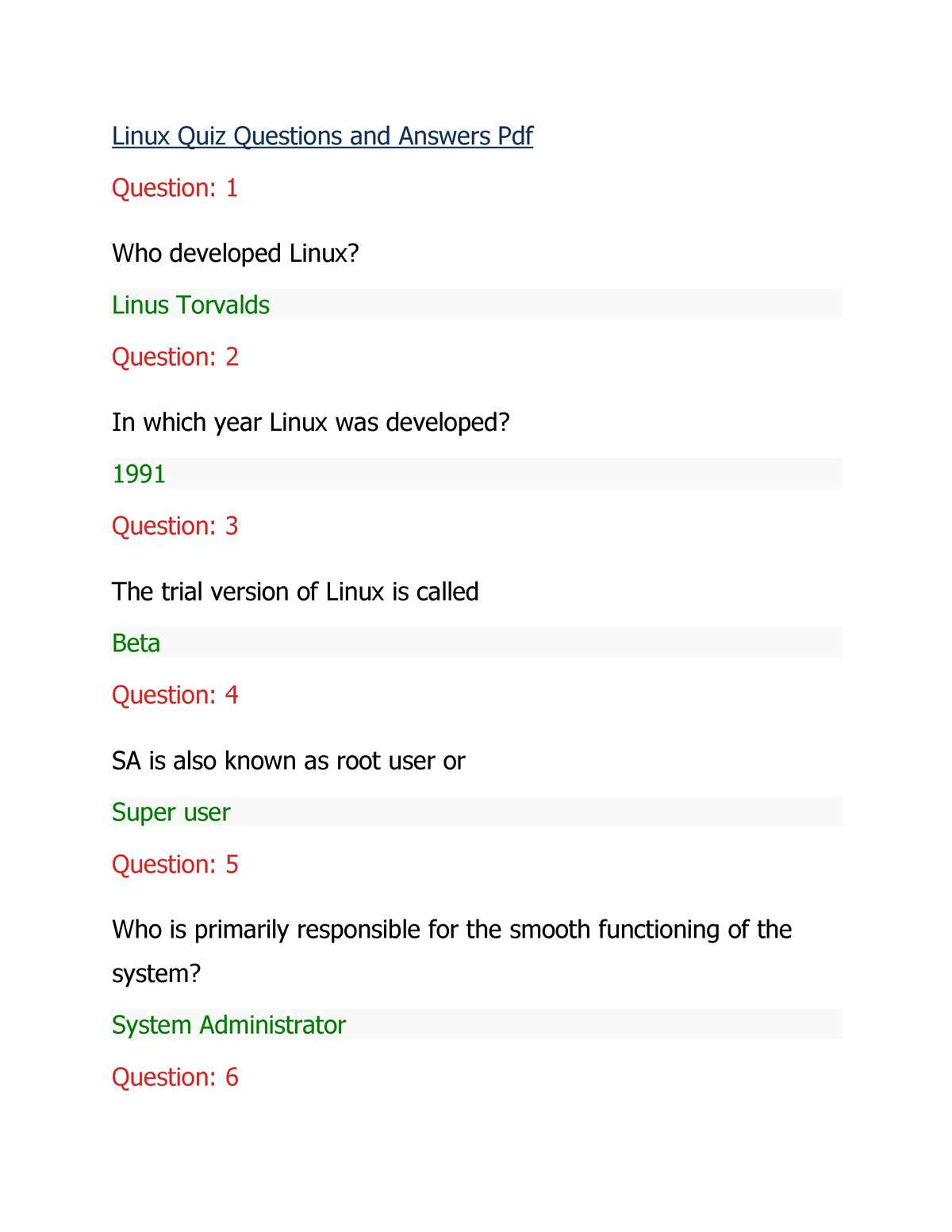
Linux Chapter 2 Exam Answers Overview
This section provides a comprehensive guide to understanding the key concepts covered in the second part of the certification process. By focusing on fundamental tasks and configurations, you’ll gain the insights needed to approach real-world challenges with greater ease and confidence. The goal is to equip you with practical knowledge that is applicable not only for assessments but also in daily operations within the system environment.
You’ll be introduced to a range of critical topics such as managing users, configuring file systems, and handling networking setups. These areas are essential for building a strong foundation, ensuring that you are prepared to tackle the most common challenges that arise in administrative roles. Developing a solid grasp of these concepts will contribute significantly to your overall proficiency.
With clear explanations and targeted examples, this section aims to simplify complex material. The aim is to give you the tools needed to successfully navigate the tasks at hand and improve your overall understanding of system management procedures.
Key Concepts Covered in Chapter 2
This section focuses on essential principles and practices that are fundamental for system administration. Understanding these core areas is critical for anyone looking to enhance their technical skills and become proficient in managing complex environments. These concepts are directly applicable to the tasks and challenges you’ll encounter in your professional work, as well as in certification assessments.
User Management and Permissions
One of the primary topics covered is the management of users and their permissions. Learning how to create, modify, and delete user accounts is vital for controlling access and maintaining security within a system. You’ll also gain an understanding of how to assign appropriate privileges to users, ensuring that each individual has the correct level of access for their role.
File Systems and Directory Structure
An in-depth exploration of file systems and their organization is another critical area. You’ll learn how to navigate the directory structure, manage files, and understand the various file types that are integral to the system. This knowledge will allow you to handle file storage, retrieval, and permissions effectively, all of which are key tasks for system administrators.
Important Topics to Review
This section highlights the key areas you should focus on to ensure a thorough understanding of essential concepts. By reviewing these topics, you will be better prepared to handle the various tasks and challenges that may arise in real-world system administration scenarios. Mastering these subjects is crucial for gaining both theoretical and practical expertise.
System Configuration and Setup
One of the most important areas to review is the proper configuration and setup of the operating environment. This includes understanding how to configure network settings, system services, and initial system installations. Knowing how to manage configurations will allow you to maintain a smooth and secure operational system.
File Management and Permissions
File management is another critical topic to focus on. Understanding how to manage files, directories, and permissions is essential for controlling access and maintaining data integrity. This knowledge is fundamental for ensuring that the system is organized and secure, particularly when dealing with multiple users and large amounts of data.
Mastering Commands for Success
To truly excel in system administration, it’s essential to master a range of fundamental commands. These tools are the foundation of efficient management and troubleshooting within any system environment. Gaining proficiency with these commands will not only help you perform tasks more quickly but also ensure accuracy and reliability in your work.
Focusing on core utilities such as file manipulation, process management, and system monitoring will give you the skills needed to navigate and control your environment. Being comfortable with these commands allows you to execute operations confidently, whether you’re configuring settings or resolving issues.
In addition, understanding how to use command-line options and arguments effectively can significantly enhance your productivity. Familiarity with syntax and command combinations is key to performing complex operations with ease.
Common Mistakes to Avoid in Chapter 2
When working through key system management tasks, it’s easy to overlook small details that can lead to bigger issues. Identifying and understanding common mistakes will help you navigate tasks more effectively and avoid unnecessary setbacks. This section highlights some of the most frequent errors made during practice, helping you stay on track and sharpen your skills.
Misunderstanding Permissions and Access Control
One of the most common errors involves mismanaging user permissions or failing to set proper access controls. Incorrect permissions can lead to security vulnerabilities or prevent users from accessing necessary resources. Make sure to always check user roles and privileges carefully.
- Assigning overly permissive access
- Forgetting to apply changes to directories recursively
- Confusing user and group ownership settings
Neglecting File System Integrity
Another frequent mistake is overlooking file system integrity and structure. Properly organizing files and understanding the role of various directories is crucial for maintaining an efficient system. Without this, file management becomes confusing, and troubleshooting errors becomes more difficult.
- Misplacing important configuration files
- Overwriting system-critical files by mistake
- Failing to verify disk space before adding new data
Step-by-Step Guide to Preparation
Effective preparation is the key to mastering the material and ensuring success. This guide will walk you through a structured approach to studying, focusing on the most critical areas while providing practical tips to enhance your understanding and retention of key concepts. Following a clear plan will help you build confidence and ensure you’re ready for any challenge that may come your way.
The first step is to familiarize yourself with the essential topics, making sure you understand the foundational concepts. Once you’ve reviewed the core material, it’s important to practice regularly, applying your knowledge through real-world scenarios or simulations. This will help you reinforce what you’ve learned and identify any gaps in your understanding.
Finally, don’t forget to take time for review sessions. Going over your notes and test materials periodically will help solidify your knowledge and make you more comfortable with the material. With consistent practice, focus, and a well-rounded preparation plan, you’ll be fully equipped to tackle the tasks ahead.
Understanding File System Basics
Grasping the fundamentals of a system’s file structure is essential for effective management and troubleshooting. The file system dictates how data is stored, accessed, and organized, and understanding this structure helps in navigating, modifying, and protecting your data. This section will explore the key components that make up a typical file system, including directory structures and file types, and highlight their significance in system administration.
The file system structure can be viewed as a tree, where each directory can contain files or other directories. A strong understanding of this hierarchy allows system administrators to perform operations efficiently and securely.
| Directory | Description |
|---|---|
| / | The root directory, where all other directories branch from. |
| /home | Directory containing user-specific files and settings. |
| /etc | Contains system configuration files. |
| /var | Holds variable data such as logs and databases. |
| /tmp | Temporary files used by system processes. |
By understanding how directories are structured and what types of files are stored in each, administrators can perform tasks such as file manipulation, system configuration, and security management with greater ease and accuracy.
How to Interpret Questions Effectively
Understanding how to accurately interpret questions is a critical skill when preparing for any assessment. It’s essential to break down each question, identify the key concepts, and address what is being asked. By focusing on the language and structure, you can ensure that you answer clearly and comprehensively, avoiding common misunderstandings.
Breaking Down the Question
To properly address a question, start by breaking it into smaller parts. Look for keywords that highlight what is being asked, such as “explain,” “describe,” or “list.” Understanding the action required is key to crafting a focused response.
- Identify the main topic or concept
- Determine the type of response required (e.g., explanation, comparison, procedure)
- Look for any qualifiers that narrow down the scope (e.g., “only,” “most,” “first”)
Staying Focused on the Requirements
Once you’ve broken down the question, ensure that your response directly addresses the requirements. It’s easy to veer off-topic, but sticking to the main points will help you provide clear and relevant answers. If the question asks for specific details, make sure you cover them comprehensively.
- Avoid unnecessary information that does not directly relate to the question
- Ensure that all parts of the question are answered
- Structure your answer logically, following the flow of the question
Practice Questions for Chapter 2 Assessment
Practicing with sample questions is one of the most effective ways to reinforce your understanding and prepare for any test. By answering practice questions, you can familiarize yourself with the types of problems you may encounter, identify areas that need improvement, and refine your problem-solving skills. This section provides a selection of practice questions designed to help you assess your knowledge and improve your readiness.
Conceptual Understanding
Start by reviewing questions that test your grasp of core concepts. These questions focus on ensuring that you understand key principles and can apply them to various scenarios. Focus on clarity and accuracy in your answers.
- Explain the role of a specific system configuration file in managing resources.
- Describe the steps required to set up a basic file system structure.
- What are the key differences between user permissions and file ownership?
Practical Application
The next step is to practice with questions that test your ability to apply your knowledge in real-world situations. These questions require you to solve practical problems or execute specific tasks based on theoretical concepts.
- How would you set permissions for a directory that only allows read access to a specific user group?
- What commands would you use to check system disk usage and manage disk space?
- Given a list of files, how would you move them to a new directory while maintaining their original permissions?
Exploring User Management Topics
Effective user management is a key aspect of system administration, as it ensures that users have the appropriate permissions to access and modify system resources. Understanding how to create, manage, and secure user accounts is essential for maintaining a well-organized and secure environment. This section dives into the key concepts and practical steps needed to manage users efficiently, focusing on account creation, permissions, and security measures.
Creating and Managing User Accounts
Managing user accounts involves creating new users, modifying existing accounts, and deleting users when necessary. Proper configuration of user accounts ensures that only authorized individuals have access to system resources.
- Creating a new user using the useradd command
- Assigning passwords with the passwd command
- Removing a user account with the userdel command
- Modifying user details using usermod
Managing User Permissions and Groups
Permissions and groups control access to files and directories. Properly assigning user rights helps to ensure that sensitive information is protected and that system resources are used efficiently.
- Assigning user permissions using chmod and chown
- Adding users to groups with the usermod command
- Managing group permissions for shared resources
- Setting default user groups with the groupadd command
Security Considerations in User Management
Security is an essential part of user management, as it prevents unauthorized access and protects critical system files. Administrators should always implement strong security practices when managing users and their permissions.
- Enforcing strong password policies
- Locking or disabling inactive user accounts
- Regularly reviewing user permissions and access levels
- Using auditing tools to track user activity
Essential Networking Concepts for Chapter 2
Networking forms the backbone of modern systems, allowing communication between devices and users across various environments. Understanding the core principles of networking is essential for ensuring smooth connectivity, security, and data transfer. In this section, we will explore the fundamental networking concepts that are crucial for system administrators to manage and troubleshoot network connections effectively.
IP Addressing and Subnetting
One of the most important aspects of networking is understanding how devices are identified and communicate over the network. IP addresses assign unique identifiers to devices, while subnetting divides networks into smaller, manageable segments. This ensures efficient routing and better utilization of network resources.
- IPv4 and IPv6 address structures
- Subnet masks and their role in network segmentation
- Calculating subnets and network addresses
Routing and Network Configuration
Routing is the process of directing network traffic from one device to another across different network segments. Understanding the basics of routing, including static and dynamic routes, is essential for managing complex networks.
- Understanding routers and their role in traffic forwarding
- Configuring routing tables
- Common routing protocols (e.g., RIP, OSPF, BGP)
Network Services and Security
Network services such as DNS, DHCP, and HTTP ensure that devices can access resources and communicate effectively. Securing these services is equally important, as vulnerabilities in these areas can lead to unauthorized access and data breaches.
- Setting up and securing DHCP and DNS services
- Configuring firewalls and access control lists (ACLs)
- Ensuring secure communication through VPNs and encryption
How to Set Up Permissions
Setting up appropriate access permissions is critical for maintaining system security and ensuring that users can only access the resources they need. Permissions determine who can read, write, and execute files or directories, and they play an essential role in protecting sensitive data. This section explains the basic methods for setting and managing permissions to maintain a secure environment.
Understanding Permission Types
Permissions are granted at different levels and for different types of access. The three primary permission types are read, write, and execute, and they can be applied to files and directories for the owner, the group, and others.
| Permission | Symbol | Description |
|---|---|---|
| Read | r | Allows viewing the contents of a file or listing the contents of a directory. |
| Write | w | Allows modifying the contents of a file or adding/removing files in a directory. |
| Execute | x | Allows running a file as a program or accessing a directory. |
Setting Permissions Using Commands
The most common way to set permissions is by using the chmod command. This command allows you to modify permissions for files and directories using either symbolic or numeric modes.
- Symbolic Mode: Uses letters to specify the permissions. For example,
chmod u+x file.txtadds execute permission for the user. - Numeric Mode: Uses a three-digit number to set permissions. Each number corresponds to different permissions for the user, group, and others. For example,
chmod 755 file.txtgrants full permissions to the user and read-execute permissions to the group and others.
Understanding and using these commands effectively ensures that only the right users have the appropriate access to files and directories, which is crucial for system integrity and security.
Managing Processes and Services
Effectively managing processes and services is crucial for system administration. Processes are the running instances of programs, while services provide essential background functions for the system. Administrators need to understand how to monitor, control, and configure both to ensure the system runs efficiently and securely.
Understanding Process Management
Processes are fundamental units of execution within the system. They can be either foreground or background tasks, and managing them involves starting, stopping, and monitoring their status. Common commands such as ps, top, and kill are used to view running processes and control them as needed.
- ps: Displays information about running processes.
- top: Provides a dynamic, real-time view of processes and resource usage.
- kill: Sends signals to terminate or control processes.
Managing Services
Services, also known as daemons, run in the background and handle various system functions such as networking, logging, and scheduling tasks. Proper management of these services is essential for system stability and performance. Administrators can use tools like systemctl and service to start, stop, and check the status of services.
- systemctl: The primary command for managing system services on modern systems. It allows you to enable, disable, start, stop, and restart services.
- service: A legacy tool used to control services on older systems or distributions.
By mastering process and service management, system administrators can ensure the smooth operation of the system and troubleshoot performance issues efficiently.
System Logs and Troubleshooting Tips
System logs are essential tools for diagnosing issues and ensuring that the system is running smoothly. These logs provide detailed records of system activities, errors, and events that occur, enabling administrators to identify and troubleshoot problems. Understanding how to access and interpret logs is a vital skill for any system administrator.
Key Logs to Monitor
Several logs are critical for system management and troubleshooting. Key logs include system logs, application logs, and security logs. Each serves a distinct purpose, providing insights into the operation and health of the system.
- /var/log/syslog: Contains general system information and is useful for tracking events such as system start-up and shutdown.
- /var/log/auth.log: Records authentication events, including successful and failed login attempts, and is essential for security auditing.
- /var/log/dmesg: Displays kernel-related messages, including hardware and driver information, particularly useful for troubleshooting boot issues.
- /var/log/kern.log: Contains kernel-specific events, useful for diagnosing hardware-related or low-level system issues.
Troubleshooting Common Issues
When facing system issues, logs are often the first place to check. The following tips can help streamline the troubleshooting process:
- Check recent logs: Start by reviewing the most recent entries to spot any immediate errors or warnings that might indicate the cause of the problem.
- Use search tools: Commands like grep and less allow you to search through log files quickly to identify relevant entries.
- Check for repeated errors: Look for patterns of recurring errors that may point to persistent issues with hardware, software, or configurations.
By regularly reviewing system logs and using effective troubleshooting techniques, administrators can identify potential issues before they escalate and maintain a stable and secure environment.
Optimizing Time for Your Test Preparation
Effective time management is a key factor in successful test preparation. By allocating time wisely and focusing on high-priority areas, candidates can enhance their chances of achieving optimal results. The goal is to streamline study sessions and avoid unnecessary distractions, ensuring that every minute spent contributes meaningfully to overall performance.
To make the most of your study time, it’s crucial to break down the material into manageable sections. This approach allows you to focus on one topic at a time and build your understanding step by step. Setting clear goals for each study session will help you stay on track and avoid feeling overwhelmed.
Effective Study Strategies
Implementing structured strategies can drastically improve how efficiently you use your time. Consider the following techniques:
- Time Blocking: Dedicate specific blocks of time to particular topics or tasks, allowing you to concentrate fully without multitasking.
- Prioritize Key Areas: Focus on the most critical concepts or the ones you feel least confident about. This targeted approach ensures you cover essential material first.
- Practice Under Test Conditions: Simulate real test scenarios by practicing with timed quizzes or mock tests. This will help you manage your time during the actual assessment.
Minimizing Distractions
Eliminating distractions is vital to maintaining focus and maximizing productivity. Create a quiet, organized study space free of interruptions. Turn off notifications and consider using productivity tools or apps to block distracting websites during study periods.
By adopting these time optimization strategies, you can approach your preparation with confidence, ensuring that you are well-prepared and able to tackle each section effectively on the day of the test.
How to Stay Calm During the Test
Staying calm during a high-pressure situation is crucial for performing at your best. When faced with a challenging assessment, maintaining composure allows you to think clearly, process questions effectively, and manage time wisely. Stress and anxiety can cloud judgment, so it’s essential to use techniques that promote relaxation and focus.
It is important to prepare mentally as much as you prepare academically. Cultivating a calm mindset before and during the test can significantly improve your ability to respond to questions and handle tricky situations.
Pre-Test Relaxation Techniques
Before you start the assessment, employ strategies that help relax your mind and body:
- Deep Breathing: Practice slow, deep breathing to reduce anxiety. Inhale deeply for four counts, hold for four counts, and exhale for four counts to calm your nervous system.
- Positive Visualization: Imagine yourself navigating the test confidently. Visualizing success can help ease worries and boost self-assurance.
- Physical Movement: A short walk or stretching exercises can reduce physical tension and clear your mind before starting the test.
Staying Focused During the Test
During the test, staying calm and focused is key. Here are some strategies to keep your stress under control:
- Read Each Question Carefully: Take your time to fully understand each question before answering. Rushing through can lead to mistakes.
- Focus on One Question at a Time: Avoid worrying about the entire test. Concentrate on answering each question to the best of your ability.
- Take Short Breaks: If allowed, take a moment to stretch or close your eyes for a few seconds to reset your focus.
By incorporating these strategies, you’ll be better equipped to handle the pressures of the assessment and perform with confidence. Staying calm not only helps you think more clearly, but it also helps maintain a positive mindset throughout the process.
Resources for Further Learning
To deepen your understanding and continue developing your skills, utilizing the right resources is essential. Whether you’re looking to reinforce concepts, explore advanced topics, or get hands-on experience, there are many tools and platforms available. Expanding your knowledge beyond the basics will strengthen your overall expertise and keep you well-prepared for practical applications.
Here are some valuable resources to consider for continued learning:
| Resource Type | Description | Link |
|---|---|---|
| Books | Comprehensive textbooks provide in-depth theory and practical examples to help you master key concepts. | Learning the Shell |
| Online Courses | Interactive learning platforms offer structured courses with video lessons, quizzes, and hands-on exercises. | Coursera – System Administration |
| Community Forums | Participating in online communities lets you ask questions, exchange ideas, and learn from others’ experiences. | Ask Ubuntu |
| Documentation | Official manuals and guides are often the best way to learn the details of different tools and commands. | Linux Man Pages |
| Video Tutorials | Step-by-step video guides are great for visual learners and provide a practical, hands-on approach to problem-solving. | YouTube – Linux Tutorials |
These resources are just a few examples to help you continue your journey. Leveraging a combination of books, online platforms, and practical experience will enhance your learning and make the information more applicable in real-world scenarios. Keep exploring and practicing to stay current and develop a well-rounded understanding of the field.
What to Do After Completing the Exam
Once you have finished your assessment, it’s important to approach the next steps strategically. Rather than rushing through the end, take a moment to reflect on your performance, review your responses, and assess any areas that may need improvement. This period can also be used to focus on relaxation and recharge before awaiting the results.
Review Your Responses
Before submitting your work, it’s always wise to double-check your answers. Look for any missed questions or errors, and verify your reasoning if you had any doubts while answering. A fresh perspective can often help you spot mistakes you overlooked initially.
Evaluate Your Preparation Process
Afterward, take some time to assess how well your preparation aligned with the content of the assessment. Did you feel confident in the topics covered? Were there any surprises? Reflecting on these aspects can help you improve your approach for future challenges.
Relax and Unwind
Once you’ve submitted everything, allow yourself some time to relax. It’s essential to step back and not dwell on the assessment. Engage in activities that help you unwind, whether it’s exercising, spending time with friends, or simply taking a break from studying.
Plan for Future Learning
Regardless of the outcome, think about how you can continue building on the knowledge you’ve gained. Identify areas where you might need further practice or deeper understanding and begin planning for your next steps in your learning journey.