Efficient communication between diverse segments of a network is crucial for maintaining optimal performance and scalability. By implementing strategies that support structured data flow, organizations can ensure seamless operations across interconnected systems.
This article delves into techniques for establishing routing frameworks that enhance both reliability and functionality. The focus is on creating solutions designed to simplify complex infrastructures while maintaining flexibility for future expansion.
Key insights include identifying appropriate tools, understanding how distinct components interact, and applying best practices to optimize routing processes. By mastering these concepts, network administrators can effectively manage and monitor dynamic environments.
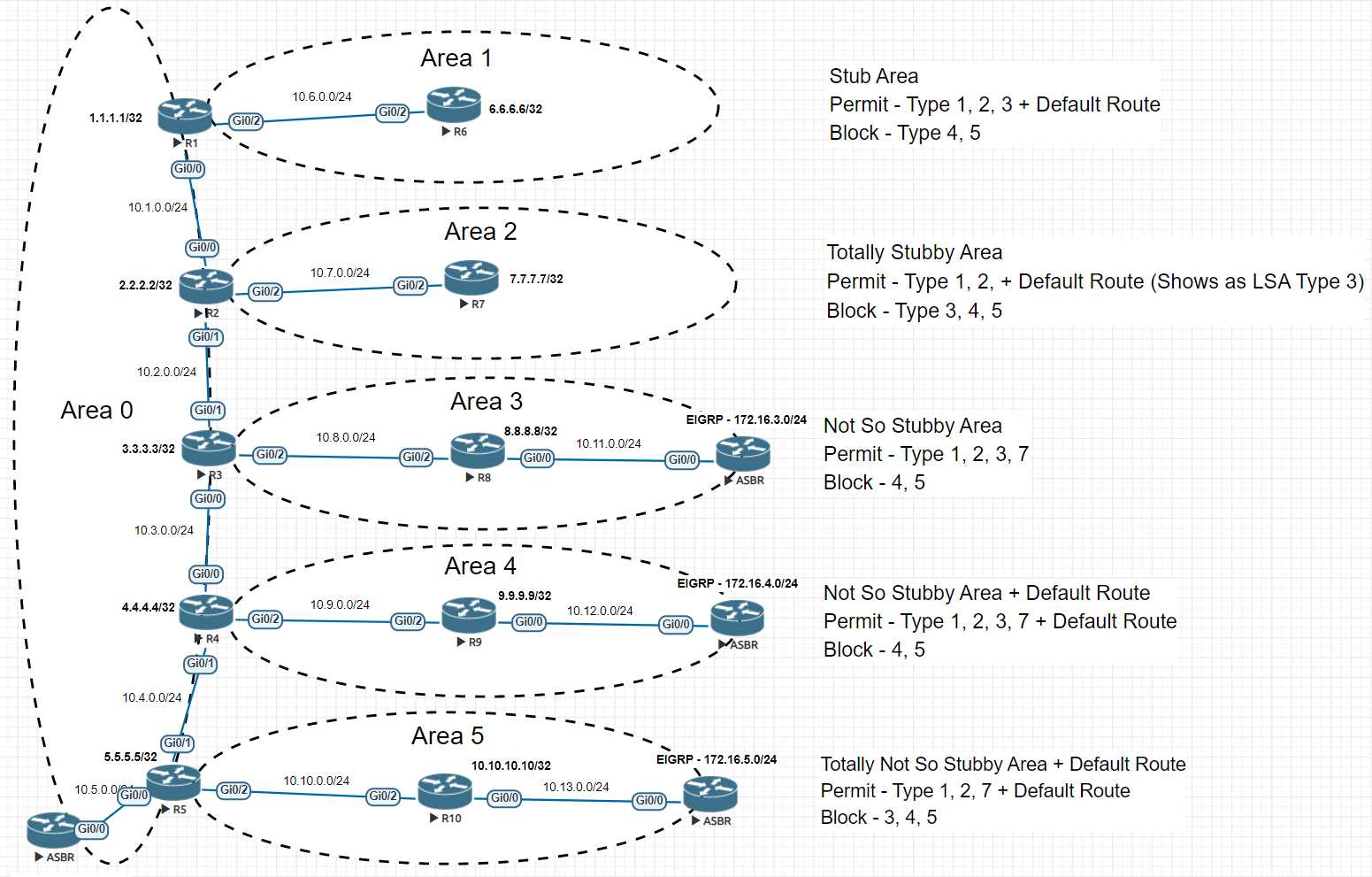
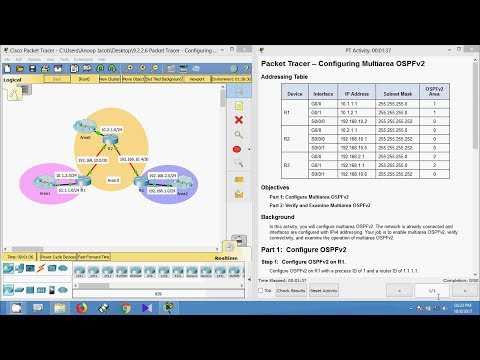
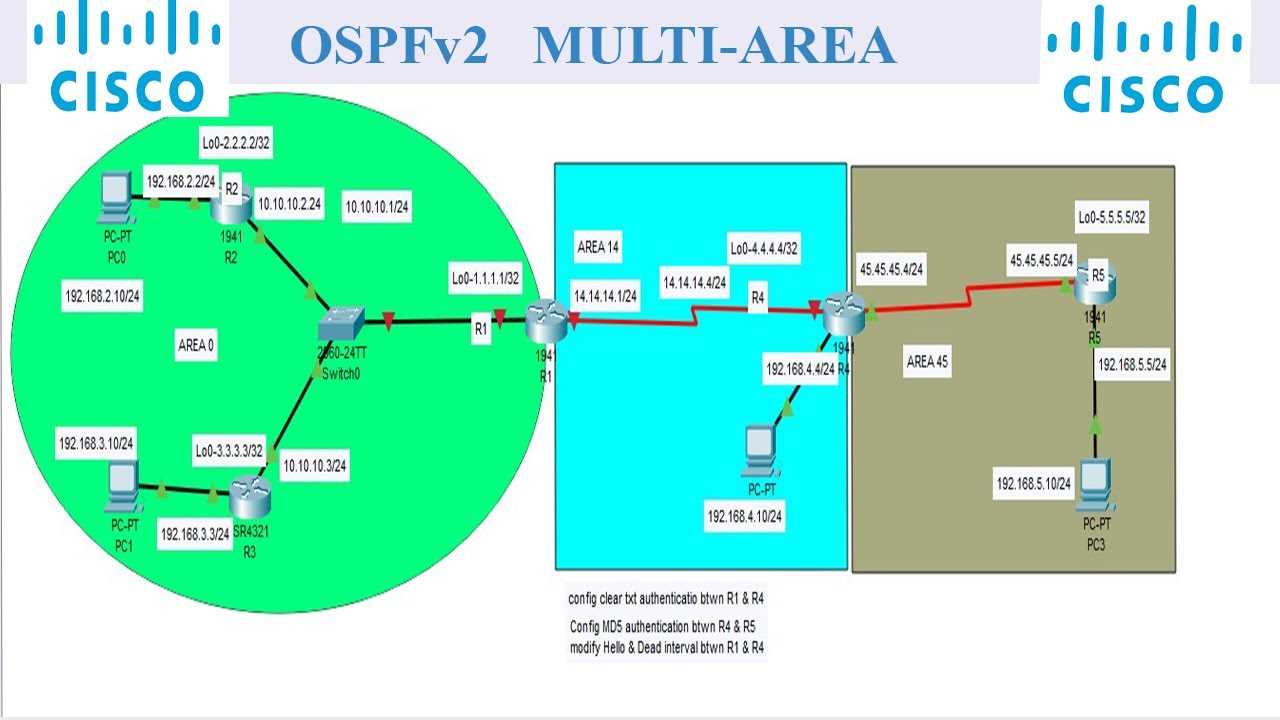
Understanding OSPFv2 Multi-Area Architecture
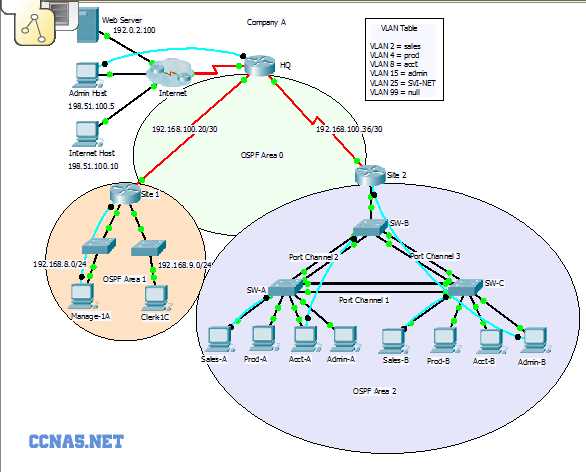
Effective network routing requires a structured approach to segmenting large systems into manageable units. This method enhances scalability, reduces overhead, and improves the overall efficiency of data transmission.
The architectural design involves creating distinct zones within the network, each with its own specific responsibilities. This organization minimizes redundancy and ensures seamless communication between different parts of the system. By isolating traffic to smaller areas, administrators can better control resources and optimize performance.
- Reduced complexity: Segmenting the system allows for simpler troubleshooting and configuration adjustments.
- Improved performance: Smaller zones result in faster convergence and streamlined data processing.
- Enhanced stability: By isolating disruptions to individual sections, the overall system remains unaffected.
Implementing this approach involves defining clear boundaries, assigning unique identifiers, and ensuring smooth transitions between zones. The ultimate goal is to achieve a balanced and efficient routing environment that meets the needs of dynamic networks.
Key Benefits of Multi-Area Configuration
Dividing complex networks into smaller, well-defined segments brings a range of advantages for maintaining stability and enhancing performance. This structured approach allows for better management of resources and simplifies routing processes across diverse environments.
Optimized Resource Utilization
Breaking down the system into distinct sections ensures that each part handles only the information relevant to its operation. This minimizes processing demands on individual devices and reduces overall system strain, leading to improved efficiency and responsiveness.
Enhanced Scalability and Maintenance
Smaller, independent sections are easier to expand and adapt as network requirements evolve. This setup simplifies maintenance tasks, enabling administrators to make changes without impacting the entire system. The modular design also facilitates faster troubleshooting and minimizes downtime.
By implementing this configuration, organizations can achieve a more reliable, scalable, and efficient networking environment that supports their long-term operational goals.
OSPFv2 Packet Types and Their Roles
Effective communication in routing protocols relies on specific message types that coordinate operations, share information, and ensure the accuracy of data exchange. These message formats each serve unique functions to maintain a consistent and reliable network environment.
- Hello Packets: These messages are used to establish and maintain connections between devices. They verify availability and form relationships with neighboring systems.
- Database Description Packets: These summarize the content of routing tables, enabling devices to exchange knowledge about network structures without transferring excessive data.
- Link State Request Packets: When additional details are needed about specific routes, these messages request the necessary information from other devices.
- Link State Update Packets: Used to share routing information across the network, ensuring all devices have up-to-date and accurate data.
- Link State Acknowledgment Packets: These confirm receipt of routing updates, reducing the risk of data loss or miscommunication.
Each of these message types plays a crucial role in maintaining synchronization and efficiency, ensuring that all connected systems function as a cohesive unit in even the most complex network environments.
Initial Setup for OSPFv2 Lab Practice
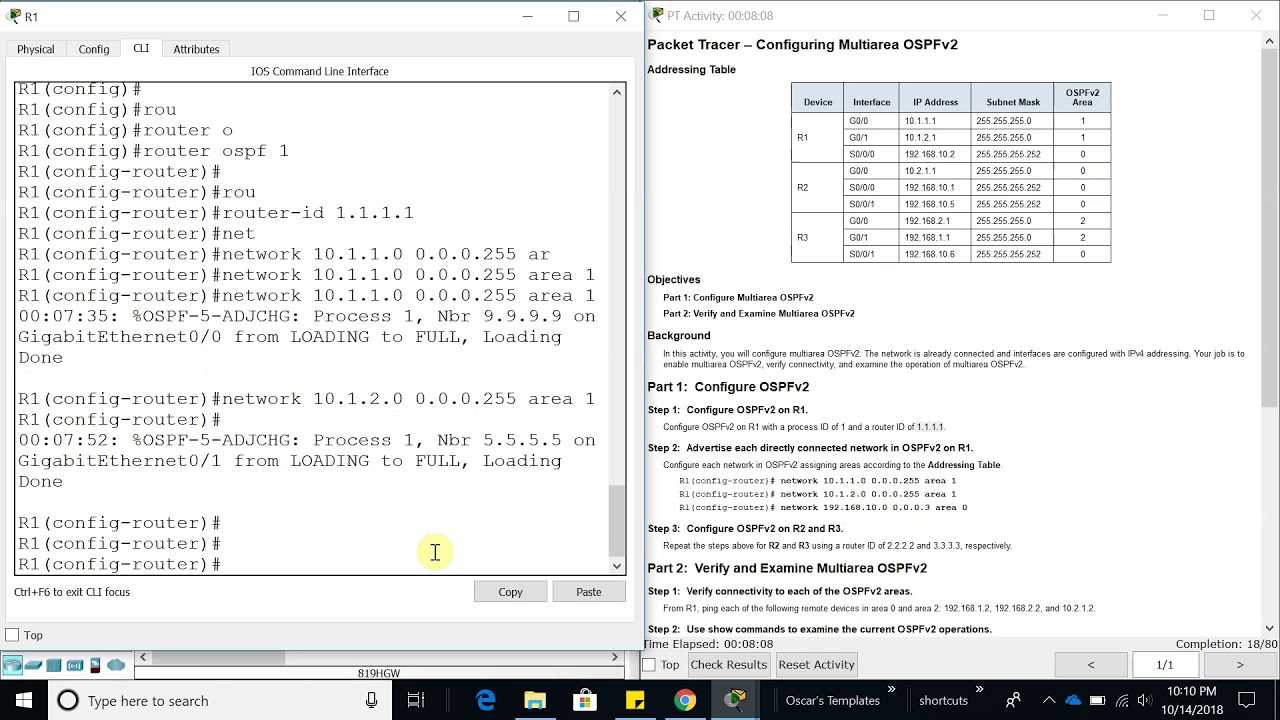
Preparing a simulated environment for network routing involves careful planning and a systematic approach. This ensures the accuracy of configurations and provides a solid foundation for testing and learning advanced techniques.
Essential Components and Their Roles
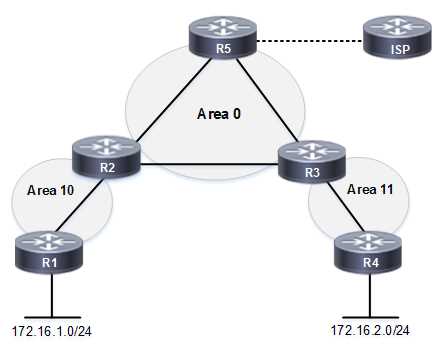
Before beginning, it’s vital to identify the necessary elements for the setup. These include physical or virtual devices, appropriate software, and clearly defined addressing schemes to facilitate seamless communication.
| Component | Description |
|---|---|
| Routers | Devices responsible for determining the best path for data transmission. |
| Switches | Used to connect and manage multiple devices within the network. |
| IP Addressing Scheme | A structured plan for assigning unique identifiers to devices. |
| Routing Protocol Software | Ensures proper communication and path selection across the network. |
Step-by-Step Preparation
Once the components are in place, the next step is to define connectivity between devices, assign addresses, and verify their communication. This process involves configuring each device with the correct settings and ensuring compatibility to avoid errors during operation.
By starting with a well-organized setup, network administrators can ensure accurate simulations and streamline the process of implementing advanced features later in the practice environment.
Configuring Area Borders in OSPFv2
Defining boundaries within a network is essential for managing routing efficiency and maintaining control over data distribution. These borders help isolate regions of the system while ensuring seamless communication between them.
Purpose of Defined Borders
Boundaries allow the network to be divided into manageable sections, reducing processing overhead and simplifying troubleshooting. Each boundary acts as a transition point, ensuring that information flows efficiently without unnecessary duplication.
- Localized traffic: Restricts data to specific regions, reducing congestion.
- Efficient updates: Ensures changes are propagated only where needed.
- Improved scalability: Simplifies the addition of new sections to the network.
Steps to Establish Boundaries
- Identify the devices that will serve as transition points between different sections.
- Assign appropriate identifiers to these devices to differentiate their roles within the system.
- Define rules for data exchange, specifying which information should cross boundaries and how it should be handled.
- Test the setup to ensure smooth interaction between sections and resolve any discrepancies.
By carefully designing and implementing boundaries, administrators can enhance the efficiency and reliability of their routing systems, enabling better resource utilization and simpler management.
Router ID Selection and Best Practices
Choosing the correct identifier for routing devices is a critical task in network configuration. The router identifier ensures proper communication between systems, distinguishing each device uniquely within the network and simplifying troubleshooting and management.
Factors in Router ID Selection
Selecting the right identifier is influenced by several factors, each contributing to the reliability and scalability of the network. The identifier needs to be unique, easy to manage, and resilient to network changes.
- Uniqueness: Each device in the network must have a distinct identifier to prevent conflicts and ensure seamless communication.
- Static Assignment: Assigning a static ID prevents the router from automatically choosing a different ID in the event of a reboot, ensuring consistency.
- Logical Structure: Consider assigning IDs based on network hierarchy or geographic locations for easier management.
Best Practices for Router ID Management
Following best practices when selecting and maintaining router identifiers can greatly improve network stability and prevent future configuration issues.
- Always ensure the router ID is unique within the entire network to avoid any potential conflicts.
- Use a manual configuration method to assign the router ID, especially in large-scale environments where automatic assignment might lead to unpredictable results.
- Incorporate clear naming conventions based on your network design to make identifying devices easier for future network administrators.
- Regularly review and update router IDs as necessary when network expansions or modifications occur.
By following these guidelines, network administrators can ensure that the router IDs contribute to the overall efficiency and reliability of the network infrastructure.
Addressing and Subnetting for OSPF Networks
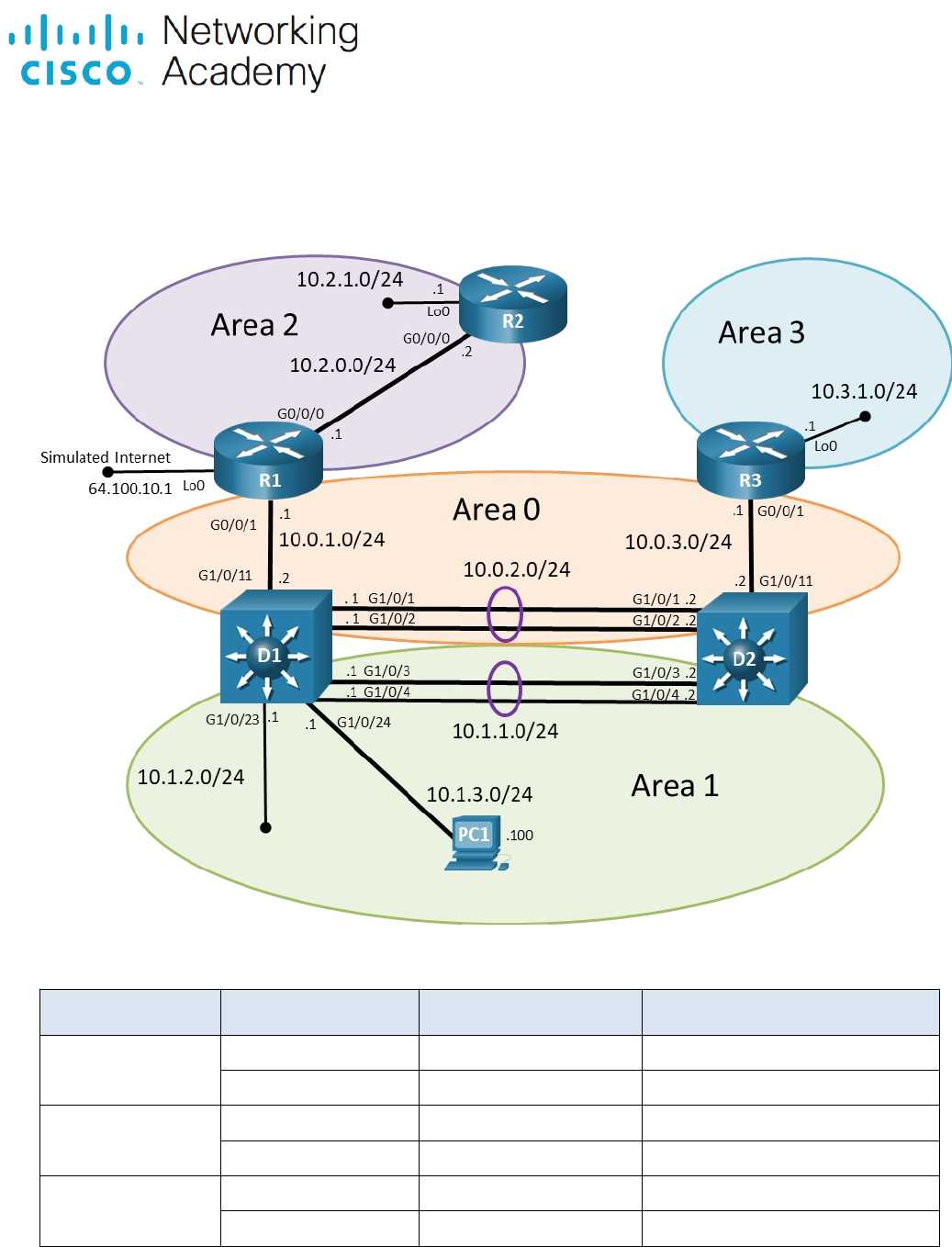
Effective addressing and subnetting are crucial in optimizing network design and ensuring efficient data routing. Properly divided address spaces allow for scalable, manageable, and stable communication between devices within a system.
Key Principles of Addressing
Addressing within a network allows devices to identify and communicate with one another. The main goal is to structure the addresses in a way that makes it easy to scale and organize the network while minimizing unnecessary broadcast traffic.
- Unique Network Addresses: Ensure each network segment is given a unique address to avoid conflicts.
- Hierarchical Addressing: Use logical address groupings based on network design to facilitate easier management and routing.
- Conservation of Address Space: Plan address usage carefully to maximize the utilization of available address blocks.
Subnetting for Scalability and Efficiency
Subnetting allows a large network to be divided into smaller, more manageable segments. This technique reduces network congestion and improves overall performance by isolating traffic within each subnet.
- Subnet Mask Calculation: Understand how subnet masks define network boundaries and segment address space efficiently.
- Classless Inter-Domain Routing (CIDR): Use CIDR to allow more flexible and efficient allocation of IP addresses, enabling better scalability.
- Minimizing Broadcast Domains: Create smaller subnets to reduce broadcast traffic and enhance network performance.
By following addressing and subnetting best practices, administrators can create a more robust and easily scalable network infrastructure that supports efficient communication and performance.
Authentication Methods in OSPFv2
Securing communication within a network is essential for protecting the integrity of routing information. Authentication mechanisms ensure that only authorized devices can participate in the routing process, preventing unauthorized access and potential security risks.
Types of Authentication
There are two main methods to authenticate routing exchanges between devices: simple password-based and cryptographic authentication. Both methods aim to verify the identity of routers involved in the network exchange.
- Simple Authentication: This method relies on a shared password for authenticating the router. While simple, it offers basic protection against unauthorized devices joining the network.
- Cryptographic Authentication: A more secure approach, it uses hashing techniques to ensure the integrity of the routing messages and verify the authenticity of the sender. This method is more robust but requires additional resources.
Best Practices for Authentication
To maintain a secure routing environment, it is important to implement best practices when configuring authentication methods. Proper selection and management of authentication mechanisms can significantly reduce the risk of unauthorized access.
- Use Strong Passwords: Ensure that passwords used for simple authentication are complex enough to withstand brute force attempts.
- Apply Cryptographic Authentication: For increased security, use cryptographic methods over simple passwords, especially in larger or more sensitive networks.
- Consistent Configuration: Ensure that all routers in the network use the same authentication method and credentials to avoid communication breakdowns.
By implementing these authentication techniques, networks can maintain secure and reliable routing protocols, safeguarding the flow of data and preventing malicious activities.
LSA Types in OSPF and Their Functions
Link-state advertisements (LSAs) are essential components in the operation of routing protocols, providing critical information about network topology. Each type of LSA serves a specific function, enabling routers to share details about network changes and maintain an accurate routing table. These advertisements allow routers to make informed decisions on the best paths to forward data.
Overview of LSA Types
In a network that uses link-state protocols, multiple types of LSAs are generated to communicate different pieces of information. Each LSA type plays a distinct role in maintaining the efficiency and stability of the network.
- Type 1 (Router LSA): This type describes the state of the router’s links to its directly connected neighbors. It provides fundamental routing information within the local network.
- Type 2 (Network LSA): Generated by the designated router, this LSA describes the relationships between routers on broadcast or non-broadcast networks, summarizing the routers connected to a specific network segment.
- Type 3 (Summary LSA): Used by area border routers to summarize routes from other areas and send them to different regions, reducing the size of routing tables.
- Type 4 (ASBR Summary LSA): This type is generated by area border routers to provide information about external routes originating from an autonomous system boundary router (ASBR).
- Type 5 (External LSA): Used to propagate external routes into the network, informing routers about paths to destinations outside the autonomous system.
Function and Importance of LSAs
LSAs are crucial for building and maintaining the link-state database, which each router uses to calculate the best path to every destination. Each LSA type contains vital information that helps to ensure that routers have an up-to-date and complete view of the network topology.
- Network Stability: By continuously exchanging LSAs, routers ensure that all devices have the latest information on network topology changes, enhancing stability.
- Efficiency in Routing: LSAs help routers make decisions based on current and accurate information, resulting in more efficient routing of data packets.
- Optimized Network Performance: Proper use of LSAs helps in minimizing network overhead and improving overall routing performance by limiting the amount of information exchanged between routers.
In summary, LSAs are vital for the smooth functioning of a network using link-state routing protocols, ensuring accurate and efficient routing by distributing key network information. The correct understanding and usage of different LSA types contribute significantly to optimizing network performance.
Route Summarization Techniques in OSPFv2
Route summarization is an essential technique used to optimize routing in large networks by consolidating multiple IP addresses into a single, summarized route. This reduces the size of routing tables, enhances network performance, and improves the overall efficiency of routing decisions. By summarizing routes, a network can reduce the number of entries that routers need to process, thus speeding up convergence and minimizing network overhead.
In networks using link-state protocols, such as OSPF, summarization is typically implemented at the boundary between areas. This allows for the aggregation of routes from one area into a more compact representation for use in another area, reducing the complexity and size of the routing table.
The benefits of route summarization include:
- Reduced routing table size, which improves memory and processing efficiency.
- Faster convergence times, as routers can more easily update and exchange information.
- Minimized routing overhead, as fewer routes are exchanged between routers, leading to less bandwidth usage.
To summarize routes effectively, administrators must carefully plan and implement proper boundary configurations. This involves identifying logical groupings of addresses that can be represented with a single summary route. In practice, summarization is commonly applied in area border routers, where multiple network prefixes from one area are grouped into a single route advertisement for other areas.
Troubleshooting Common OSPFv2 Issues
Network issues can arise in environments using dynamic routing protocols, resulting in problems such as connectivity failures, slow network performance, or incorrect routing paths. Identifying and resolving these problems requires a structured approach, as various factors can influence the behavior of the network. Understanding common causes and the methods to diagnose them is key to maintaining a healthy routing system.
Typical Problems
There are several issues that frequently occur in dynamic routing environments. These include:
- Failure to Establish Neighbor Relationships: Routers may fail to establish proper communication due to mismatched configuration settings, such as different hello and dead intervals, authentication issues, or incorrect area definitions.
- Routing Loops: Misconfigurations in the network, such as improper summarization or incorrect path selection, can cause routing loops, where data circulates endlessly without reaching the destination.
- Slow Convergence: Network topology changes, excessive flooding, or delays in processing updates can result in slower convergence times, where routers take longer to adjust to new paths.
- Missing Routes: If a router does not learn or advertise certain routes, the issue may lie in the network segmentation, improper interface setup, or a failure in exchanging routing information.
Troubleshooting Methodology
To address these issues, a methodical approach is essential. Key steps in troubleshooting include:
- Check Neighbor Relationships: Use diagnostic tools to verify if neighbor relationships are correctly formed. Commands like show ip ospf neighbor can help identify any communication failures.
- Verify Interface and Configuration: Inspect the router’s interfaces to ensure that the correct IP addresses and network types are assigned, which are essential for proper packet exchange.
- Examine LSAs: Investigate the link-state advertisements to ensure they are generated and propagated correctly across the network, which is critical for accurate routing.
- Review Routing Table: Use commands like show ip route to check for missing or incorrect routes, and verify that they are properly received and advertised.
By carefully following these steps, administrators can effectively identify the root cause of issues, leading to faster resolution and improved network stability.
Optimizing Performance in Multi-Area Networks
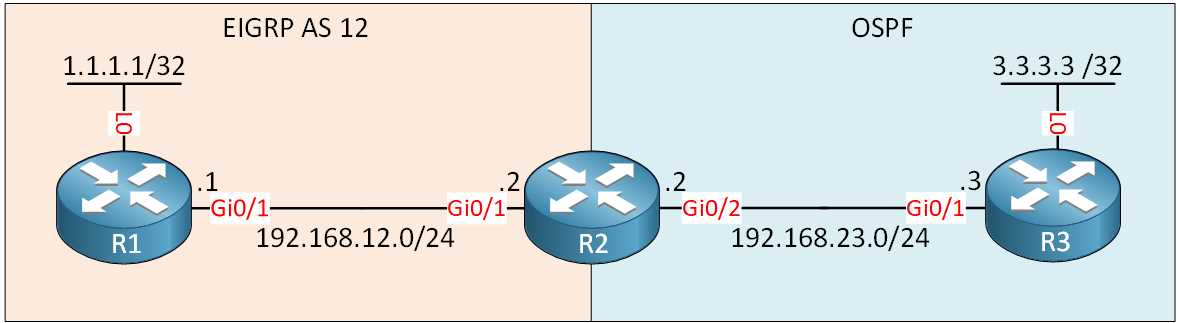
In complex network environments, performance optimization is crucial to ensure that communication remains fast and efficient. When dealing with multiple segments, proper planning and configuration are essential for minimizing congestion and reducing unnecessary traffic. The following strategies focus on enhancing the overall performance of networks with segmented architectures, ensuring stability, faster convergence, and minimal resource consumption.
Key Strategies for Performance Optimization
Several best practices can significantly improve network performance. These strategies focus on reducing overhead, optimizing resource use, and ensuring effective data routing.
| Strategy | Benefit | Implementation Tips |
|---|---|---|
| Use of Area Borders | Reduces unnecessary inter-area traffic and limits the propagation of routing information. | Assign appropriate boundaries and avoid excessive area overlap. |
| Route Summarization | Decreases the size of routing tables and reduces protocol overhead. | Implement summarization at borders between areas to minimize route advertisement. |
| Optimizing Hello and Dead Timers | Improves stability and speed of neighbor relationships. | Ensure uniform timer configurations across routers within the same area. |
| Efficient Link-State Advertisement (LSA) Flooding | Reduces the impact of frequent topology changes and improves convergence. | Limit the frequency of LSAs and manage flood intervals. |
By following these strategies, network operators can enhance the performance of their infrastructure, ensuring better scalability and responsiveness in larger systems. Efficient planning and attention to these details can significantly reduce network strain and increase overall reliability.
Configuring Stub and Totally Stubby Areas
In large-scale networks, it is often necessary to limit the types of routing information exchanged between network areas to improve efficiency and reduce overhead. By designating certain areas as stub or totally stubby, network administrators can control the propagation of routing updates and optimize the flow of routing information. These configurations ensure that routers in specific areas only receive essential route information, minimizing unnecessary data processing.
Understanding Stub Areas
A stub area is a type of network segment where external routes are not advertised. Instead, a default route is typically used to route packets destined for outside the area. This setup reduces the size of routing tables and enhances performance by preventing the need to maintain detailed routing information for external destinations.
Benefits of Totally Stubby Areas
In a totally stubby area, even the summary routes from other areas are filtered, leaving only a default route for outbound traffic. This extreme form of simplification results in even smaller routing tables, significantly reducing the processing load on routers within the area. This is particularly useful in smaller branches or remote offices where only internal routing is required.
Key Benefits:
- Improved performance by reducing the number of routes.
- Lower memory and CPU usage on routers within stub areas.
- Faster convergence and simplified routing decisions.
Implementation Considerations:
- Stub areas should only be used where external routes are unnecessary.
- Be cautious when applying totally stubby areas, as they remove all external and inter-area routing information.
Network Design Considerations for OSPFv2
When designing large-scale networks, careful planning is essential to ensure optimal performance, scalability, and efficient management of routing information. The design of the network should address factors such as topology, area structure, traffic patterns, and redundancy. A well-thought-out approach can help mitigate potential issues like routing loops, slow convergence, and excessive resource usage.
Factors to Consider in Network Design
- Area Structure: Define the appropriate number of areas and determine whether they should be stub, totally stubby, or normal. Each area serves a specific purpose, such as reducing the size of the routing tables or limiting the propagation of external routes.
- Scalability: As the network grows, ensure that the design accommodates additional routers and areas without causing performance degradation. Hierarchical structuring can help achieve this by breaking down the network into manageable parts.
- Redundancy and Fault Tolerance: Ensure high availability by implementing redundancy at both the link and router levels. Redundant paths should be established to minimize network downtime in case of link or router failure.
- Traffic Engineering: Analyze traffic patterns to optimize routing and prevent congestion. Design the network to handle expected traffic loads, and consider traffic shaping and load balancing where appropriate.
Best Practices for Effective Design
- Limit the Number of Areas: Keep the number of areas to a reasonable level to avoid complexity and excessive resource usage. Too many areas can lead to routing inefficiencies.
- Optimize Router Placement: Place routers in strategic locations to ensure efficient path selection and minimal latency. Consider the role of each router in the network when determining placement.
- Use of Backbone Area: The backbone area should connect all other areas in the network. Ensure proper connectivity between backbone and other areas to maintain proper routing functionality.
OSPFv2 Interaction with Other Protocols
Routing protocols must be able to interact effectively within complex networks that often involve multiple technologies. The ability of one protocol to work alongside or exchange information with others is essential for creating a seamless routing environment. This collaboration ensures that data can flow efficiently across diverse systems and that the routing table remains accurate and up-to-date, even in multi-protocol environments.
When integrating with other protocols, considerations such as compatibility, route redistribution, and policy-based routing play a significant role. These interactions enable routers to exchange information and select optimal paths based on various routing requirements and conditions.
Redistribution Between Protocols
Redistribution allows for the sharing of routing information between different routing protocols. For instance, when integrating a link-state protocol with a distance-vector protocol, routes can be redistributed from one protocol’s routing table to another. However, it’s crucial to handle redistribution carefully to avoid issues like routing loops and inconsistencies. Proper filtering and route tagging are often used to manage these interactions.
OSPFv2 and BGP
The Border Gateway Protocol (BGP) and OSPFv2 can interact through redistribution, but their operational models differ significantly. OSPFv2, being an interior gateway protocol (IGP), is designed for efficient routing within an autonomous system, while BGP is an exterior gateway protocol (EGP) that manages routing between different autonomous systems. When both protocols are present in a network, they are often used to handle internal and external routing separately. Proper configuration of redistribution points ensures that routes are accurately passed between the two protocols, allowing the network to function cohesively.
OSPFv2 and EIGRP
Enhanced Interior Gateway Routing Protocol (EIGRP) is another IGP that can interact with OSPFv2 in larger networks. Similar to OSPFv2, EIGRP uses an advanced method to compute the best path, but it is a hybrid protocol. Redistribution between OSPFv2 and EIGRP must be handled with care to avoid route conflicts and ensure smooth route exchange. In some cases, administrative distances are adjusted to control which protocol’s routes are preferred.
Advanced Commands for OSPFv2 Analysis
Effective analysis of routing protocols often requires the use of advanced commands that provide in-depth insights into network performance and troubleshooting. These commands are essential for network engineers to diagnose issues, verify configurations, and ensure optimal operation of routing processes. By leveraging these commands, administrators can monitor network behavior, examine the state of routing tables, and fine-tune the protocol for enhanced efficiency.
When analyzing routing behavior, it’s crucial to focus on parameters such as the status of neighbors, route advertisements, and database contents. These factors directly impact the flow of data across a network, making it necessary to use the appropriate commands for effective monitoring and debugging.
Viewing Neighbor Status
One of the primary tasks in diagnosing network issues is to check the status of neighboring devices. The following command helps identify the state of OSPFv2 neighbors, displaying essential details about their connections:
| Command | Purpose |
|---|---|
| show ip ospf neighbor | Displays the status of OSPFv2 neighbors, including the state of the relationship, the IP addresses, and other relevant metrics. |
| show ip ospf interface | Provides detailed information about the interfaces on which OSPFv2 is running, including their state and other interface-related settings. |
Examining Routing Tables
For a deeper understanding of how OSPFv2 is influencing routing decisions, examining the routing table is essential. The following command displays the routing table, including all routes learned through OSPFv2:
| Command | Purpose |
|---|---|
| show ip route ospf | Shows all routes learned through OSPFv2, including details about route types and their associated metrics. |
| show ip ospf database | Displays the OSPFv2 link-state database, providing a complete view of all known routes and their state information. |
By using these commands, network engineers can gain comprehensive visibility into the health of their OSPFv2 network, enabling them to quickly identify issues and make informed adjustments to improve performance and reliability.
Monitoring and Verifying OSPFv2 Configurations
Ensuring that routing protocols are correctly set up and functioning properly is a critical aspect of maintaining a reliable network. Monitoring and verifying configurations help network administrators confirm that the routing process is running as expected and identify any potential issues before they affect network performance. Regular checks provide insights into the health of the network, allowing for prompt detection and troubleshooting of problems.
By leveraging various monitoring commands, administrators can examine the operational state of routers, verify the status of neighbors, and review the correctness of routing tables. It is crucial to ensure that each configuration aligns with the intended design and that all devices are participating correctly in the routing process.
Verifying Router Interfaces and Neighbors
To verify that a router is properly communicating with its neighbors and that its interfaces are correctly configured, the following commands can be used:
| Command | Purpose |
|---|---|
| show ip ospf interface | Displays detailed information about the interfaces running the protocol, including status, IP addresses, and metrics. |
| show ip ospf neighbor | Shows the status of neighboring devices, helping administrators confirm that all expected routers are visible and in the correct state. |
Checking Routing Table and Database
Another key verification step is ensuring that the routing table reflects the expected routes and that all link-state information is up-to-date. These commands provide valuable insights into the routes learned through the protocol and the state of the routing database:
| Command | Purpose |
|---|---|
| show ip route | Displays the network routes known to the router, including those learned through the routing protocol. |
| show ip ospf database | Shows the router’s link-state database, revealing detailed information about each OSPFv2 router’s view of the network. |
By using these tools to monitor and verify configurations, network engineers can ensure the smooth operation of the routing protocol and detect any inconsistencies or misconfigurations that may lead to connectivity issues.
Real-World Scenarios for OSPF Multi-Area Setup
In large-scale networks, breaking up a single routing domain into multiple areas can enhance efficiency, improve network performance, and simplify management. By segmenting the network, routing information can be better controlled, and overhead reduced, leading to faster convergence and optimized resource usage. This setup is especially beneficial in enterprise environments with complex topologies, where scalability and reliability are essential for smooth operation.
Scenario 1: Large Enterprise Network
Consider a large corporation with multiple regional offices spread across different cities or countries. Each region requires local routing information to be exchanged efficiently, but it is not necessary for routers in one region to have complete knowledge of the entire global network. In this case, dividing the network into several areas reduces the amount of routing information that needs to be processed by each router, while still allowing inter-area communication through area border routers (ABRs). This setup allows for effective routing within each region, without overwhelming the routers with excessive details from other regions.
Scenario 2: Data Center Network Optimization
In a data center, the network is often divided into several logical zones, each representing a different function or service, such as storage, compute, and network management. To optimize performance and ensure that routing updates are processed efficiently, dividing the data center network into areas can prevent the network’s backbone from being overwhelmed. Each zone communicates with the backbone area, while reducing unnecessary flooding of routing updates across the entire network, which helps improve scalability and resource allocation.
In both these scenarios, segmenting the network into multiple areas provides clear benefits in terms of performance, control, and scalability. Properly designing the network’s area structure based on these principles ensures optimal use of network resources while maintaining efficient routing operations.