
As you prepare to demonstrate your skills in managing computer systems, it’s essential to focus on the core topics and tasks that will be tested. The ability to navigate and configure system environments is crucial, and understanding how to solve common challenges will significantly improve your performance. Effective troubleshooting, resource management, and command-line proficiency are among the skills that will be key to your success.
Through a combination of theoretical knowledge and practical exercises, you’ll build a comprehensive understanding of system management techniques. Mastery of commands, permissions, networking tools, and system security will empower you to confidently handle various tasks. This section will guide you through these concepts and provide the necessary tools to succeed in a system administration assessment.
Key areas covered include managing user accounts, handling system processes, installing and updating software, and securing network connections. Each topic plays a vital role in ensuring a well-functioning environment and prepares you for real-world challenges in system administration. Whether you’re a beginner or looking to enhance your skills, this overview will help clarify essential topics and point you toward further learning opportunities.
Key Topics Covered in the Assessment
To prepare effectively for a system administration evaluation, it is essential to focus on a set of core subjects that test your understanding and practical skills. These topics cover a range of tasks, from managing system resources to troubleshooting issues and configuring networks. Each of these areas is fundamental for ensuring that the system runs smoothly and securely.
Core Areas of Focus
The following key topics are commonly addressed in the assessment, covering both theoretical concepts and practical applications. Mastery of these areas will ensure you’re well-equipped to manage and troubleshoot a variety of systems.
| Topic | Description |
|---|---|
| System Commands | Understanding essential commands for navigating and managing the system environment. |
| File Systems | Managing file structures and storage, including file permissions and directory hierarchy. |
| Process Management | Monitoring and controlling system processes, ensuring efficiency and resource optimization. |
| Networking | Configuring network settings, troubleshooting connectivity issues, and using network tools. |
| Security | Ensuring system security through user management, firewalls, and encryption techniques. |
Practical Skills Tested
Along with theoretical knowledge, practical proficiency in tasks such as installing software, managing users, and troubleshooting common errors is tested. Real-world scenarios may involve solving problems related to system performance, package management, or security breaches. Demonstrating your ability to respond to these challenges will play a key role in your success.
Essential Commands to Know
Familiarity with key commands is crucial for navigating and managing a system environment effectively. These commands serve as the building blocks for performing everyday tasks, such as managing files, monitoring system performance, and troubleshooting errors. Whether you’re working in a terminal or performing system administration tasks, mastering these commands will greatly enhance your efficiency.
Basic Navigation and File Management
Being able to move around the system and manipulate files is a fundamental skill for any system administrator. The following commands are commonly used for managing files and directories:
| Command | Description |
|---|---|
| cd | Changes the current directory. |
| ls | Lists files and directories in the current location. |
| cp | Copies files or directories from one location to another. |
| mv | Moves or renames files and directories. |
| rm | Deletes files or directories. |
System Monitoring and Performance
To ensure the system runs smoothly, monitoring its performance is essential. These commands help administrators track resources, processes, and network activity:
| Command | Description |
|---|---|
| top | Displays real-time system processes and resource usage. |
| df | Shows disk space usage across file systems. |
| ps | Displays information about active processes. |
| free | Displays available and used memory on the system. |
| netstat | Shows network connections and routing tables. |
Understanding File Systems and Directories
Efficient management of data storage relies on understanding how files and directories are organized within a system. Proper knowledge of file systems is essential for tasks like locating, accessing, and managing data, as well as maintaining system integrity. Each system has its own way of structuring information, which impacts how files are stored and retrieved.
File System Structure
At the core of any system is its file structure, which defines how data is stored on disk and accessed by users or applications. The file system is organized into directories, where each directory can contain files or other subdirectories. This hierarchical structure allows for efficient data organization and retrieval, ensuring that resources are easy to locate and manage.
| Directory | Description |
|---|---|
| / | The root directory, the starting point for all files and directories. |
| /home | Contains user-specific data and configurations. |
| /bin | Holds essential command binaries used by the system. |
| /etc | Contains system configuration files and scripts. |
| /var | Stores variable data, such as logs and databases. |
Managing Files and Directories
Understanding how to manage and navigate these directories is crucial for efficient system operation. You can create, delete, and move files or directories, which helps keep the system organized. Commands such as mkdir, rmdir, and ls allow users to interact with the file system and perform necessary tasks quickly and effectively.
Working with Permissions
Managing access rights is a critical aspect of system administration. By controlling who can read, write, or execute files and directories, administrators can maintain security and ensure proper system usage. Permissions help prevent unauthorized access to sensitive data while allowing users to perform necessary tasks on the system.
Permissions in most systems are granted through a combination of user types and specific access levels. These settings dictate what actions a user can take on a file or directory, whether it be viewing its content, modifying it, or executing programs. Understanding how to assign and modify these permissions ensures that each user or process operates within their designated boundaries.
There are three main types of permissions that can be set for files and directories:
- Read (r): Allows the user to view the contents of a file or directory.
- Write (w): Grants permission to modify or delete a file or directory.
- Execute (x): Allows the user to run a file or script as a program.
Permissions can be set using the chmod command, which allows users to change the access levels for files and directories. The command uses a symbolic or numeric representation to assign specific rights to the file owner, group, and others. By mastering the use of these commands, administrators can ensure that access to resources is appropriately restricted and managed.
Common Networking Commands
In any system environment, efficient network management is essential for ensuring smooth communication between devices and resources. Being able to quickly troubleshoot and configure network settings is a crucial skill for system administrators. A variety of commands are available to monitor network status, configure connections, and diagnose issues as they arise.
Network Configuration and Diagnostics
Several commands are used to configure network interfaces and check the status of network connections. These tools allow administrators to gather information about active connections, test connectivity, and resolve issues related to network communication.
| Command | Description |
|---|---|
| ifconfig | Displays or configures network interfaces, including IP addresses and network settings. |
| ping | Tests connectivity to a remote host by sending ICMP echo requests. |
| netstat | Shows network connections, routing tables, and network statistics. |
| traceroute | Tracks the route packets take to a destination, helping diagnose network latency issues. |
| nslookup | Resolves domain names to IP addresses and performs DNS queries. |
Managing Network Services
Beyond simply monitoring connections, managing network services and configurations is a key part of maintaining a system’s network functionality. These commands enable the setup and control of various services like DNS, DHCP, and HTTP.
| Command | Description |
|---|---|
| systemctl | Controls systemd services, allowing administrators to start, stop, or restart network-related services. |
| iptables | Manages firewall rules to control inbound and outbound network traffic. |
| curl | Transfers data from or to a server using various protocols, useful for testing API connections. |
| ssh | Provides secure remote login and command execution over the network. |
Mastering Shell Scripting Basics
Automating repetitive tasks and managing system operations efficiently requires an understanding of scripting. Shell scripts are used to execute a series of commands, allowing administrators to automate processes, perform batch operations, and create custom workflows. Mastery of basic scripting principles enhances productivity and ensures that common tasks can be performed with minimal manual intervention.
Key Elements of a Shell Script
At its core, a shell script is simply a text file containing a sequence of commands that can be executed by the shell. These scripts can be as simple as a series of commands or as complex as an interactive program. The fundamental components include variables, control structures, loops, and functions, which together allow for flexibility and power in automating tasks.
| Element | Description |
|---|---|
| Variables | Store data that can be used and manipulated throughout the script. |
| Loops | Repeat commands until a specific condition is met, allowing for automation of repetitive tasks. |
| Conditionals | Allow the script to make decisions based on logic, enabling branching and complex workflows. |
| Functions | Encapsulate blocks of code to be reused multiple times within a script. |
Writing and Executing a Simple Script
Writing a shell script begins with creating a file and marking it as executable. A simple script can be written using a text editor, with each line containing a command. After saving the script, you can give it execute permissions with the chmod command and run it directly from the terminal. Here is a basic example of a script:
#!/bin/bash
echo "Hello, world!"
This script, when executed, will print “Hello, world!” to the terminal. As you progress, you can build more complex scripts that include loops, conditionals, and error handling, significantly improving the automation of tasks.
Understanding Process Management
Efficient management of running tasks is a crucial aspect of system administration. Each task or program that runs on a computer is considered a process, and managing these processes effectively ensures optimal system performance. Administrators need to monitor, control, and troubleshoot processes to maintain a stable environment.
Process management involves keeping track of the processes running on the system, allocating resources, and controlling their execution. Understanding how processes are created, monitored, and terminated is essential for troubleshooting and system optimization. There are several tools and commands available to manage processes, allowing administrators to handle issues such as resource allocation and process termination efficiently.
Basic Process Management Commands
- ps – Displays information about the currently running processes, including their process IDs and resource usage.
- top – Provides real-time updates on system processes and resource usage, allowing for performance monitoring.
- kill – Terminates a process by sending a signal, typically used to stop misbehaving or unwanted processes.
- bg – Resumes a paused process in the background, freeing up the terminal for other tasks.
- fg – Brings a background process to the foreground, allowing for interaction with the process directly.
Managing Process States
Processes can be in different states depending on their current activity. Understanding these states is essential for effective troubleshooting and optimization. The most common process states include:
- Running (R): The process is currently executing or ready to execute.
- Sleeping (S): The process is waiting for an event or resource, such as input or I/O.
- Stopped (T): The process has been paused, either by a user or by the system.
- Zombie (Z): The process has completed execution, but its entry remains in the process table because the parent process has not yet read its exit status.
By regularly monitoring and managing processes, administrators can ensure that system resources are used efficiently, minimize downtime, and avoid potential conflicts or system crashes.
Package Management and Installation
Managing software packages efficiently is essential for system maintenance. The process of installing, updating, and removing software on a system is handled by package management tools. These tools ensure that all necessary dependencies are satisfied, and they allow users to easily manage installed applications and libraries.
Software packages are distributed in formats specific to the operating system, and the package management system helps automate the installation and maintenance process. These tools allow administrators to handle large volumes of software, from system utilities to third-party applications, with ease and consistency.
| Package Manager | Description |
|---|---|
| apt | Used on Debian-based systems for handling package installation, updates, and removal. |
| yum | Used in Red Hat-based systems to manage software packages and dependencies. |
| dnf | A more modern replacement for yum, offering improved performance and handling of software packages. |
| zypper | Package manager used in SUSE-based systems to manage software and updates. |
| pacman | Used in Arch Linux and its derivatives, providing a fast and flexible package management system. |
Package managers provide several key commands to manage software installation:
- install: Installs a specific package or set of packages from the repository.
- remove: Removes an installed package from the system.
- update: Updates the package list and installed packages to the latest available versions.
- upgrade: Upgrades all installed packages to their latest versions.
- search: Searches for available packages in the repository.
By using these commands effectively, administrators can ensure that their systems are kept up-to-date, secure, and efficient, with minimal effort required to manage software installations and updates.
Basic Troubleshooting Techniques for Linux
When systems encounter issues, it’s essential to approach the problem methodically to identify and resolve the root cause. Troubleshooting is a critical skill for maintaining stability and ensuring smooth operation. By following a structured approach, administrators can isolate problems, analyze error messages, and apply fixes efficiently.
Effective troubleshooting involves understanding the system’s behavior, using diagnostic tools, and leveraging logs to pinpoint issues. Identifying whether the problem is hardware-related, software-related, or due to configuration errors is key to finding the correct solution. This section covers common techniques and tools used in troubleshooting, empowering users to diagnose and resolve problems quickly.
Common Troubleshooting Steps
- Check System Logs: Logs provide valuable information about errors, crashes, and warnings that occur within the system. The
/var/logdirectory contains logs for system messages, kernel errors, and application-specific logs. - Verify System Resource Usage: Ensure the system has sufficient resources (CPU, RAM, and disk space). Use tools like
top,free, anddfto check resource utilization. - Test Network Connectivity: For issues related to network connections, tools like
ping,ifconfig, andnetstatcan help identify network failures or misconfigurations. - Restart Services: Sometimes, restarting a service or the entire system resolves temporary glitches. Use
systemctlorservicecommands to restart specific services.
Utilizing Diagnostic Tools
There are several tools available to help diagnose system problems. These tools provide detailed information and can assist in narrowing down the cause of the issue:
- journalctl: This command allows you to view logs for systemd services and applications, which can be crucial for diagnosing service-related problems.
- dmesg: Displays kernel ring buffer messages, often used to check for hardware-related issues.
- strace: A powerful tool for tracing system calls and signals of processes, useful for diagnosing application-level issues.
- lsof: Lists open files and processes using them, helpful in identifying issues related to file access or resource locking.
By using these methods and tools, administrators can address common issues such as system crashes, slow performance, and network connectivity problems effectively, ensuring that systems remain operational and responsive.
Configuration Files and System Settings
System settings and configuration files play a vital role in controlling how an operating system functions. These files are typically plain-text and contain settings that define system behavior, from network configurations to user preferences. Understanding how to edit and manage these files is essential for system administrators to tailor the environment to meet specific requirements.
Configuration files are usually located in the /etc directory and can govern various aspects of the system, such as user authentication, service management, and network interfaces. By modifying these files, administrators can adjust settings without needing to interact with the user interface, offering greater flexibility and control over system operations.
Key Configuration Files
- /etc/passwd – Contains essential user account information, such as usernames, home directories, and login shells.
- /etc/network/interfaces – Defines network interface settings, such as IP addresses, gateways, and DNS servers.
- /etc/fstab – Configures filesystem mount points and automatic mounting during system boot.
- /etc/hostname – Specifies the system’s hostname, which identifies the machine on a network.
- /etc/ssh/sshd_config – Contains configuration options for the SSH server, controlling how remote connections are handled.
Editing Configuration Files
Editing configuration files requires caution, as incorrect changes can lead to system instability or even make the system unbootable. Before making modifications, it’s important to back up the original configuration files. The most commonly used text editors for this task are:
- nano: A simple, user-friendly text editor that is easy to use for beginners.
- vim: A powerful editor suitable for more advanced users, offering a wide range of functionality for text manipulation.
- gedit: A graphical text editor available in some environments, ideal for users who prefer a more intuitive interface.
After editing configuration files, many changes will require restarting services or the system to take effect. To apply changes made to a service’s configuration, administrators can typically use the systemctl or service commands to restart or reload the affected service.
Linux User and Group Management
Managing users and groups is a fundamental task for maintaining an organized and secure system. Proper user management ensures that individuals have the right level of access to resources, while group management allows for easier administration of permissions. Understanding how to create, modify, and remove users and groups is essential for any system administrator.
User accounts define individual identities on the system, while groups provide a mechanism to group users together for easier management of permissions. This section will explore key commands and methods for effectively managing both users and groups, enabling administrators to maintain system security and streamline user-related operations.
Managing User Accounts
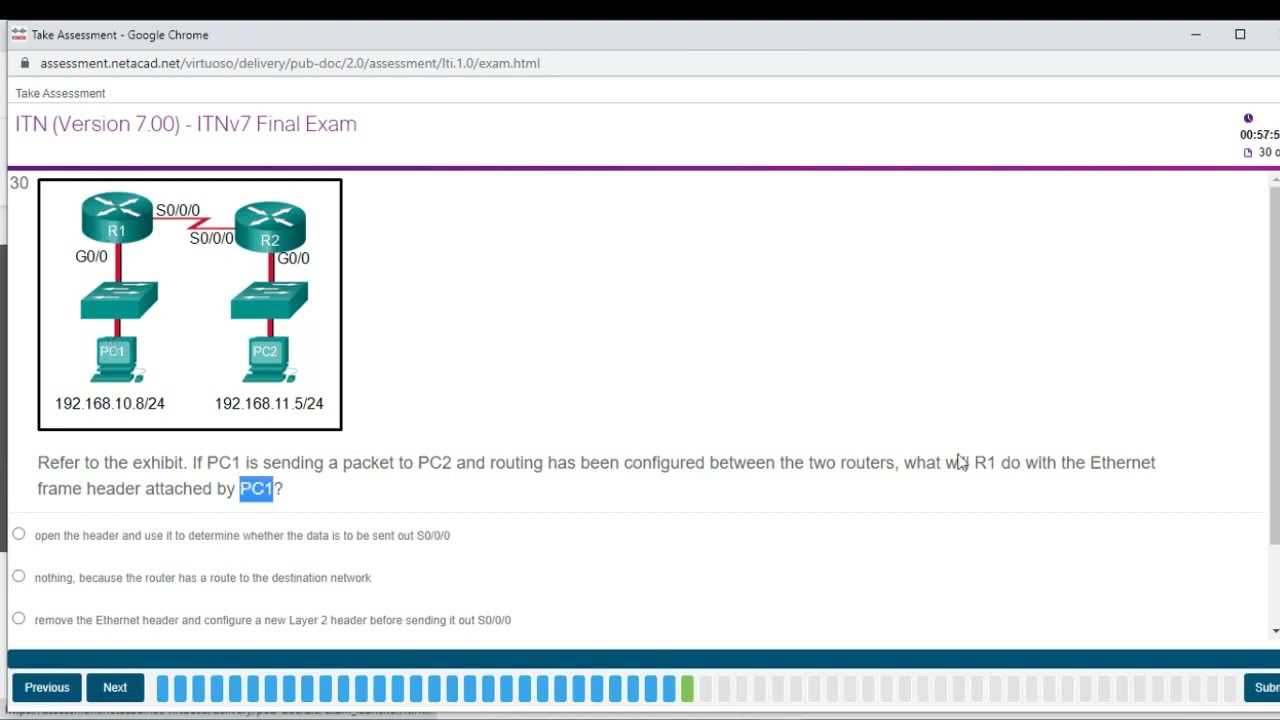
Users are the cornerstone of system access, and managing user accounts involves creating, modifying, and deleting them when necessary. The most common commands used for user management include:
- useradd: Used to create new user accounts. This command can specify details like the user’s home directory, login shell, and group memberships.
- usermod: Allows modification of an existing user account, including password changes, group membership modifications, or updating user details.
- userdel: Removes a user account from the system, along with any associated files if specified.
Managing Groups
Groups are used to manage sets of users with similar access requirements. By assigning users to the correct groups, administrators can efficiently manage permissions for shared resources. Key commands for group management include:
- groupadd: Creates a new group, which can then be assigned to users who need shared access.
- groupdel: Removes a group from the system. This command will not delete the users in the group but will disassociate them from it.
- gpasswd: Provides an easy way to modify group passwords and manage group administrators.
Properly managing users and groups ensures that access rights are correctly set, reducing the risk of unauthorized access and improving system security. Understanding the relationship between users, groups, and permissions is key to effective administration.
System Boot and Shutdown Procedures
The process of starting up and shutting down a system is critical for maintaining its integrity and ensuring that all services and resources are properly initialized or safely terminated. Understanding the boot and shutdown sequences allows administrators to troubleshoot issues, optimize performance, and maintain system stability.
When a system boots, it goes through a series of steps to load the necessary kernel, initialize hardware, and start essential services. Similarly, shutting down or rebooting the system involves carefully stopping services, unmounting file systems, and powering off hardware in a controlled manner. Both processes can be controlled via command-line tools and system management utilities.
System Boot Process
The boot process begins as soon as the system is powered on. Here’s an overview of the main steps involved:
- BIOS/UEFI: The system’s basic input/output system (BIOS) or unified extensible firmware interface (UEFI) initializes hardware components and performs a power-on self-test (POST) to ensure everything is functioning properly.
- Bootloader: The bootloader (such as GRUB) is responsible for loading the kernel into memory and starting the operating system. It provides options for booting into different kernels or recovery modes.
- Kernel Initialization: The kernel is loaded and takes control of the system. It detects and configures hardware components, sets up memory, and prepares the system for running applications.
- System Services: Once the kernel is running, essential system services and processes (e.g., network daemons, file systems) are started, completing the boot process.
System Shutdown Procedure
Shutting down a system is just as important as starting it up, ensuring that processes are safely stopped and data is not corrupted. The shutdown procedure typically involves the following stages:
- Graceful Shutdown: The system sends signals to running processes to terminate them gracefully. This helps to avoid data loss or file system corruption.
- Unmounting File Systems: All mounted file systems are unmounted, ensuring that no data is being written to disks before the system powers off.
- Power Off: After all processes have been terminated and file systems safely unmounted, the system is powered off or rebooted based on the shutdown command issued.
To initiate these procedures, system administrators commonly use commands like shutdown, reboot, or halt along with appropriate options to control the timing and nature of the process.
Managing System Resources Effectively
Effective management of system resources is crucial to ensuring optimal performance and stability. Resources such as CPU, memory, storage, and network bandwidth need to be monitored and allocated efficiently to avoid bottlenecks and ensure that all processes and services run smoothly. Proper resource management allows for better scalability, performance, and response times across the system.
This process involves tracking usage, adjusting limits, and optimizing configurations to make the best use of available hardware. System administrators need to be familiar with various tools and techniques for monitoring and managing resource utilization, troubleshooting potential issues, and making necessary adjustments to improve performance.
CPU and Memory Management
Effective CPU and memory management ensures that system processes are allocated the necessary resources while maintaining system responsiveness. Several tools and commands help monitor and manage CPU and memory usage:
- top: Provides a dynamic, real-time view of the system’s resource usage, showing CPU, memory, and process information.
- htop: An enhanced version of the
topcommand, offering a more user-friendly, interactive interface to monitor system resources. - free: Displays memory usage, including total, used, free, shared, and available memory.
- ps: Shows detailed information about active processes, allowing for investigation of CPU and memory usage by specific applications.
Disk Space and I/O Management
Storage management ensures that data is properly distributed across storage devices, preventing issues like disk overflows or performance degradation. Administrators can use various commands to monitor disk usage and optimize file system performance:
- df: Displays disk space usage across all mounted file systems, helping administrators identify potential issues with storage capacity.
- du: Provides disk usage for files and directories, allowing users to pinpoint which files or directories are taking up excessive space.
- iotop: Monitors and displays I/O usage by processes, helping identify processes that are consuming disproportionate amounts of disk I/O.
By continually monitoring these resources and making necessary adjustments, administrators can ensure that system performance remains high and that resources are used effectively across all running processes and applications.
Understanding Security in Linux
Maintaining a secure system is essential for safeguarding data, ensuring privacy, and preventing unauthorized access. A comprehensive security strategy involves several layers of defense, including proper configuration, regular monitoring, and the application of security policies. Ensuring that systems are protected from threats such as malware, unauthorized access, and data breaches is a fundamental part of system administration.
Security mechanisms within the operating environment help prevent attacks and minimize potential vulnerabilities. This includes the use of firewalls, encryption, access control, and auditing tools. System administrators need to continuously assess security practices to ensure they are up to date and effective in mitigating potential risks.
Access Control and User Management
Access control is one of the primary means of securing a system. By controlling who can access the system and what resources they can interact with, administrators can reduce the risk of unauthorized actions. Common tools for managing user access include:
- chmod: Used to modify file permissions, ensuring that only authorized users can access or modify sensitive data.
- chown: Changes ownership of files and directories, allowing system administrators to control which users or groups have specific access rights.
- usermod: Modifies user accounts, enabling the addition or removal of users from specific groups, or changing user permissions.
- sudo: Grants users administrative privileges for executing specific commands without giving full root access.
Network Security and Firewall Configuration
Network security is critical in preventing unauthorized access from external sources. Firewalls, both hardware and software-based, help filter out malicious traffic and restrict access to sensitive services. Common tools for enhancing network security include:
- iptables: A command-line utility used to configure and manage a system’s firewall, defining rules for incoming and outgoing traffic.
- ufw: An easier-to-use front-end for iptables, allowing users to configure basic firewall rules with a simplified interface.
- fail2ban: Protects against brute-force attacks by monitoring log files and blocking IP addresses that show malicious activity patterns.
By employing a combination of user management, network security tools, and access control, administrators can build a robust defense system, helping ensure that critical data and resources remain protected from unauthorized access.
Backup and Restore Linux Systems
Data protection and recovery are crucial for maintaining system integrity and ensuring business continuity. Regular backups ensure that, in the event of a failure or data loss, essential information can be restored without significant downtime. A reliable backup strategy involves automating the backup process, using tools to ensure that all critical files, configurations, and data are securely copied to a remote or external location.
Restoring a system from backup requires a methodical approach to recover files and settings in a way that minimizes disruption. It involves selecting the appropriate backup set, verifying its integrity, and applying it to bring the system back to a functional state. Without a reliable backup process in place, organizations risk significant data loss and the potential for extended downtime.
Common Backup Tools
There are several tools available for automating the backup process. These tools allow administrators to schedule backups, verify the success of backups, and restore data when necessary. Some of the most commonly used utilities include:
- rsync: A versatile command-line tool that enables the copying and synchronization of files and directories locally or to a remote location. It supports incremental backups, meaning only changes are saved, reducing storage space.
- tar: A tool used to create compressed archive files of directories and files. It’s commonly used for full-system backups and can be easily restored using the same command.
- dd: A disk copying tool that is used to create low-level backups, including entire disk images or partition copies. It’s particularly useful for creating full-system backups.
- rsnapshot: An rsync-based backup program that allows for incremental backups, making it efficient for both large systems and small-scale environments.
Restoration and Recovery Procedures
Once a system is backed up, the next critical step is ensuring that restoration procedures are well-defined and tested. The key to a successful restoration is having clear guidelines and knowing what to do when data loss occurs. Some key steps include:
- Identify the backup set: Always ensure that you’re selecting the correct backup set for restoration. Regularly test the integrity of backups to ensure they are reliable when needed.
- Restore system files: Begin by restoring key system configurations and files. This ensures that the operating environment is re-established before personal data is restored.
- Validate restored data: After restoring, it’s important to check the integrity of the system, ensuring that all files are present, and there is no corruption or missing data.
By employing a consistent backup strategy and understanding the recovery process, system administrators can significantly reduce the risk of data loss, minimizing downtime and ensuring the system’s reliability in the event of failure.
Linux Virtualization and Containers
Virtualization and containerization have revolutionized the way applications and services are deployed and managed. These technologies allow multiple isolated environments to run on a single physical machine, improving resource utilization and flexibility. Virtualization typically involves creating virtual machines (VMs), which emulate physical hardware, whereas containerization offers a lighter-weight approach by isolating applications at the operating system level.
Both technologies play an essential role in modern IT infrastructure, offering significant benefits such as simplified management, improved scalability, and increased security. While virtualization is often used for creating complete, isolated operating systems, containers provide a streamlined solution for running applications in self-contained environments with minimal overhead.
Key Differences Between Virtualization and Containers
Understanding the key distinctions between virtualization and containers is essential for choosing the right solution for your infrastructure needs. The following points outline the primary differences:
- Isolation level: Virtualization involves running entire operating systems, while containers isolate applications within the host OS, using shared resources.
- Resource efficiency: Containers are more lightweight as they share the host operating system’s kernel, whereas virtual machines require separate OS instances, resulting in higher resource consumption.
- Performance: Containers typically provide better performance due to lower overhead, while VMs may experience more latency due to the additional layer of virtualization.
- Use cases: Virtual machines are ideal for running multiple operating systems on a single server, while containers are better suited for deploying microservices and applications in a consistent, portable manner.
Popular Virtualization and Containerization Tools
Several tools are commonly used to implement virtualization and containerization. Below are some of the most popular ones:
- KVM (Kernel-based Virtual Machine): A full virtualization solution for Linux, allowing users to run multiple virtual machines on a single host. It provides strong isolation and support for multiple OS types.
- Docker: A widely-used containerization platform that allows developers to package applications and dependencies into portable containers. Docker makes it easier to build, deploy, and manage applications in a consistent environment.
- QEMU: An open-source machine emulator and virtualizer that provides system-level virtualization. It can be used alongside KVM to provide enhanced virtualization capabilities.
- Podman: A container management tool similar to Docker but without requiring a daemon. Podman is designed to run containers in rootless mode, offering a more secure option for container management.
By leveraging virtualization and containers, IT teams can optimize resource usage, enhance application portability, and create scalable, efficient environments that meet the demands of modern enterprise applications.
Preparing for Your Linux Exam
Successfully mastering the required material and achieving proficiency in a technical subject often demands careful planning and targeted study strategies. The key to excelling in any assessment is to focus on understanding core concepts, practicing hands-on exercises, and familiarizing yourself with common challenges and solutions. Preparation for this type of certification or assessment should not only involve theoretical knowledge but also practical application in real-world environments.
While the process may vary depending on individual learning styles, following a structured approach can help streamline your efforts and ensure comprehensive readiness. Whether you are learning key commands, understanding system architecture, or troubleshooting common issues, it is essential to prioritize the most crucial topics and refine your skills in those areas.
Study Tips for Effective Preparation
To approach your preparation systematically, here are some useful study tips:
- Review Key Concepts: Focus on understanding the basics such as file systems, user management, and network configurations. Mastering these areas will give you a strong foundation for more complex topics.
- Practice Hands-on: Theoretical knowledge alone may not be enough. Set up a virtual machine or use cloud services to simulate environments and practice commands and configurations.
- Utilize Study Guides: Seek out reputable guides or textbooks that cover the essential topics. These materials often include practice questions, case studies, and tips for troubleshooting.
- Join Online Communities: Engage with online forums and discussion groups where you can ask questions, share knowledge, and gain insights from others who have successfully completed similar assessments.
Common Mistakes to Avoid
When preparing for an assessment, it’s also important to avoid certain pitfalls that can hinder progress:
- Procrastination: Delaying your studies until the last minute can result in incomplete understanding and unnecessary stress. Start early and stick to a consistent study schedule.
- Overloading Information: Trying to memorize too many details without understanding the underlying principles can be counterproductive. Focus on grasping core concepts and how they interconnect.
- Neglecting Hands-on Practice: Theoretical knowledge is important, but practical experience is equally crucial. Make sure you are comfortable with executing commands, configuring systems, and solving issues in real environments.
By following these guidelines and approaching your preparation with dedication and focus, you can significantly improve your chances of success and gain the necessary skills to apply knowledge effectively in real-world scenarios.