
In the world of national security, ensuring that sensitive information is handled appropriately is of utmost importance. This section explores the critical process of evaluating and managing information that is restricted due to its potential impact on national safety. Those involved in this process must have a thorough understanding of various guidelines and rules to properly protect and categorize confidential data.
Successfully navigating this complex field requires an in-depth knowledge of the classification system, as well as the ability to apply it to specific situations. Individuals responsible for protecting such data must be prepared to identify what needs to be secured and follow the correct procedures. The process demands not only attention to detail but also a strong understanding of legal and ethical standards.
Preparation is key to performing well in this role. Familiarity with the core principles, relevant regulations, and real-life scenarios can significantly aid in making informed decisions. By mastering these concepts, professionals can ensure that information is safeguarded in accordance with the highest standards, maintaining the integrity of both the system and the nation’s security efforts.
Answers to Derivative Classification Exam
In the realm of national security, understanding how to properly handle and protect sensitive data is crucial. Individuals responsible for managing restricted information must demonstrate a clear comprehension of how to determine which materials need safeguarding and what guidelines should be followed to ensure their protection. This section delves into the fundamental concepts that are vital for excelling in this area of responsibility.
The process involves recognizing the types of information that are considered confidential and applying the correct protocols for securing them. A solid grasp of the various regulations and standards is essential to avoid errors that could compromise national security. Professionals in this field must also be able to make informed decisions based on a thorough understanding of both legal requirements and practical applications.
By focusing on the core principles of securing sensitive materials and adhering to established standards, those who manage confidential data contribute to the overall safety and integrity of governmental and organizational operations. Mastery of these practices is key to ensuring compliance and minimizing risks associated with improper handling of classified information.
Understanding the Derivative Classification Process
In the field of national security, safeguarding sensitive information is a critical responsibility. This process involves determining how certain materials should be treated based on their content and the potential impact of their release. Professionals in this area must be able to assess data and apply the appropriate standards to ensure that confidentiality is maintained throughout various stages of handling and dissemination.
Key Principles of Information Protection
The first step in the process is to evaluate the information carefully, identifying what makes it valuable or restricted. This involves understanding both the content and context of the material, as well as its relationship to other confidential data. Ensuring that the right level of protection is applied to each piece of information is essential for maintaining security across an organization or government entity.
Legal and Ethical Responsibilities
Alongside technical skills, individuals involved in this process must also be aware of the legal and ethical responsibilities tied to information management. Missteps in handling sensitive content can have serious consequences, both for national security and for individuals involved in the process. Therefore, it is vital to adhere to established guidelines and regulations, ensuring that all actions are transparent and compliant with relevant laws.
Key Concepts for the Exam
Successfully navigating the process of securing sensitive information requires a strong grasp of several fundamental principles. Professionals must understand how to assess and handle materials based on their content and security needs. A deep familiarity with the key concepts surrounding information protection will help ensure that all data is treated according to the highest standards and regulations.
One of the most important aspects of this process is the ability to identify what types of information require special protection. This involves understanding the classification systems, as well as the criteria used to determine whether a piece of data should be restricted or accessible. Additionally, individuals must be aware of the legal frameworks and policies that guide how information is categorized and handled within an organization or government entity.
Another critical concept is the distinction between different levels of protection. Not all sensitive information is equally restricted, and knowing how to apply the correct classification to various types of data is vital. Mastery of these principles ensures that individuals can effectively contribute to safeguarding national security and organizational confidentiality.
Common Mistakes to Avoid
When managing sensitive information, there are several pitfalls that can compromise both security and compliance. Being aware of these common errors is crucial for ensuring that all materials are handled properly and in accordance with the required standards. Missteps in the evaluation and protection of classified content can lead to serious consequences, so avoiding these mistakes is essential for anyone responsible for safeguarding confidential data.
Misunderstanding the Level of Protection
One of the most frequent mistakes is failing to correctly assess the level of protection needed for a piece of information. Not all sensitive data requires the same level of security, and misclassifying the protection level can either lead to over-restriction or inadequate safeguarding. Understanding the nuances of different levels of confidentiality is essential to ensuring the proper treatment of each piece of information.
Neglecting to Follow Established Guidelines
Another critical error is failing to adhere to the specific guidelines and protocols outlined by relevant regulations. These rules are designed to ensure that information is categorized, protected, and shared appropriately. Disregarding these standards, whether intentionally or due to oversight, can result in the mishandling of sensitive data and potentially cause harm to national security or organizational integrity.
How to Interpret Classification Guides
Effectively interpreting guidelines for managing confidential information is essential for maintaining security. These guides provide the necessary framework for determining how to categorize and safeguard sensitive data based on its content, potential risks, and impact. Understanding how to properly use these resources ensures that information is handled according to the highest standards, minimizing the chance of errors or unauthorized access.
When reviewing classification guides, it is important to focus on the key criteria that define the sensitivity of information. This includes understanding the terminology used, as well as the specific rules and procedures outlined for each level of protection. By following these instructions carefully, individuals can accurately assess what materials need to be restricted and apply the correct safeguards to prevent security breaches.
Additionally, interpreting these guides requires knowledge of the broader legal and regulatory framework. It is not just about recognizing the data that requires protection but also about understanding the implications of mishandling such information. By applying these guides properly, professionals can ensure compliance and protect both national security and organizational integrity.
Exam Structure and Question Types
Understanding the layout and types of questions in a knowledge assessment for managing sensitive materials is crucial for proper preparation. The format of the evaluation is designed to test an individual’s ability to apply regulations and guidelines effectively in various scenarios. Familiarity with the structure and types of questions can help participants feel more confident and perform better during the process.
Types of Questions
The questions are generally structured to assess both theoretical knowledge and practical application. Common question types include:
- Multiple Choice: These questions test knowledge of key concepts and require selecting the correct option based on a set of provided choices.
- Scenario-Based: These questions present hypothetical situations where the participant must apply the rules to make decisions regarding sensitive data handling.
- True/False: Simple statements are provided, and the participant must identify whether they are correct or incorrect based on established guidelines.
- Fill-in-the-Blank: These questions require participants to complete a statement by filling in the missing term or concept.
Structure of the Assessment

The overall structure of the assessment is designed to test both broad understanding and attention to detail. The evaluation typically includes:
- General Knowledge Section: Focuses on fundamental principles and concepts related to safeguarding confidential materials.
- Practical Application Section: Assesses how well participants can apply their knowledge in real-world situations.
- Regulatory Knowledge Section: Focuses on laws, rules, and procedures that govern the handling of sensitive information.
Importance of Information Protection
The protection of sensitive data is essential for maintaining national security, organizational integrity, and public trust. Proper handling and safeguarding of confidential materials ensure that critical information does not fall into the wrong hands, where it could potentially be misused. Understanding the significance of securing such data is key to preventing threats that could compromise safety or lead to severe consequences.
Impact on National Security
When classified materials are mishandled or exposed, it can have far-reaching implications on national security. Unauthorized access to sensitive information may lead to espionage, cyberattacks, or other forms of exploitation by adversaries. Protecting information ensures that those who wish to harm national interests are prevented from gaining crucial knowledge.
Preserving Organizational Integrity
Beyond national security, safeguarding confidential data also plays a critical role in maintaining the integrity of businesses, governments, and institutions. Data breaches can severely damage an organization’s reputation, erode public trust, and result in financial losses. Therefore, implementing strong information protection measures helps mitigate risks and preserve both the institution’s image and its ongoing operations.
Steps for Proper Derivative Classification
Effectively managing and protecting sensitive information requires a systematic approach to ensure that all materials are correctly categorized and handled according to established standards. The process of safeguarding data involves several crucial steps that help prevent unauthorized access and maintain security. Understanding these steps is essential for anyone responsible for securing confidential materials.
To classify information properly, the first step is to review the content carefully. This includes identifying the type of data, its relevance, and any potential security risks associated with its release. Once this assessment is complete, the next step is to apply the appropriate protective measures based on the sensitivity of the information.
The final steps in the process involve documenting the classification decision and ensuring that the data is stored and transmitted securely. Regular reviews of classification decisions and continuous training on updated guidelines are also essential to maintaining a strong security posture. By following these steps, individuals can effectively manage sensitive data while minimizing risks and ensuring compliance with relevant regulations.
Legal and Ethical Responsibilities in Classification

The management of confidential information comes with significant legal and ethical obligations. Individuals tasked with protecting sensitive data are not only responsible for following established guidelines but must also act with integrity and transparency in every decision they make. Understanding the legal framework and ethical standards governing the protection of information is essential for ensuring that data is handled appropriately and securely.
Legal responsibilities are rooted in national security laws, government regulations, and organizational policies. These rules are designed to prevent unauthorized access and ensure that sensitive materials are not misused or exposed. Alongside these legal duties, ethical considerations play a critical role in making sure that classified data is treated with the utmost care and respect for privacy and security.
| Legal Responsibilities | Ethical Responsibilities |
|---|---|
| Complying with national security laws and regulations. | Handling information with integrity and transparency. |
| Ensuring data is only accessed by authorized individuals. | Maintaining confidentiality and respect for privacy rights. |
| Adhering to institutional and government guidelines. | Promoting accountability and ethical decision-making in data handling. |
By upholding both legal and ethical standards, professionals can ensure that sensitive information is protected and that they contribute to the overall security of their organization and nation.
Tips for Studying for the Exam
Preparing for an assessment on handling sensitive information requires a focused and strategic approach. Success in such evaluations depends not only on understanding the concepts but also on being able to apply them effectively. To ensure a thorough understanding, it’s important to adopt a comprehensive study plan and use a variety of techniques that reinforce both theoretical knowledge and practical skills.
Effective Study Techniques
Here are some key strategies to help maximize your preparation:
- Review the Key Guidelines: Familiarize yourself with the core principles and regulations that govern the protection of sensitive materials. This foundational knowledge is essential for answering questions accurately.
- Practice with Sample Scenarios: Engage with practice questions or hypothetical situations that mirror real-life applications of the rules. This helps reinforce how to apply your knowledge in practical contexts.
- Take Regular Breaks: Studying for extended periods without breaks can reduce focus and retention. Break your study sessions into manageable chunks, and incorporate short breaks to recharge.
- Join a Study Group: Collaborating with others can help clarify difficult concepts and provide new perspectives. Group discussions often highlight areas that may need further attention.
Staying Organized
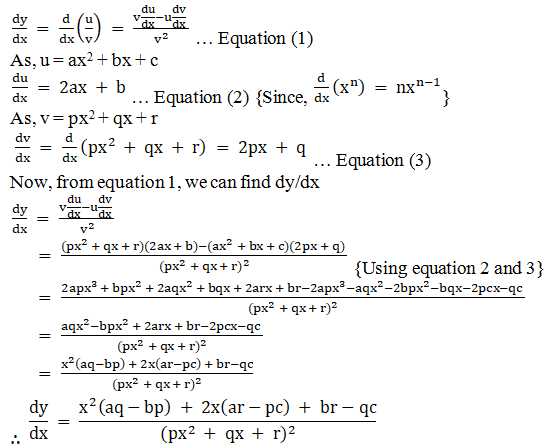
Being organized can improve the efficiency of your study sessions:
- Create a Study Schedule: Outline a clear plan with set goals for each study session. Prioritize topics based on their complexity and importance.
- Review and Revisit: Regularly review what you have studied to reinforce your memory. Revisiting key concepts will help solidify your understanding.
- Use Visual Aids: Diagrams, charts, and other visual tools can help break down complex information into more digestible parts.
Classifying Controlled Information Correctly
Properly categorizing sensitive materials is a critical responsibility that ensures secure handling of protected data. Whether it’s government documents or corporate records, applying the correct security measures prevents unauthorized access and maintains confidentiality. Ensuring that information is classified appropriately is not just about following rules; it’s about safeguarding interests and protecting national security or organizational integrity.
When handling controlled materials, it’s essential to follow a consistent and systematic approach. First, carefully assess the content of the information to determine its nature and sensitivity. Different types of data will require different levels of protection. Once identified, apply the necessary security classifications based on the established guidelines and protocols.
Accurate categorization of information reduces the risk of accidental exposure, and helps ensure that only authorized individuals are granted access. Following the proper procedures throughout the process strengthens both security and compliance, providing a reliable framework for managing confidential materials in any setting.
Impact of Errors on National Security
Even the smallest mistakes in handling sensitive information can have significant consequences for national security. Mismanagement or mishandling of protected materials can lead to unintended exposure, jeopardizing security efforts and potentially endangering lives. It’s crucial that those responsible for managing confidential data understand the far-reaching implications of their actions, as errors can lead to vulnerabilities that adversaries may exploit.
Consequences of Misclassification

Incorrectly categorizing sensitive information can create a variety of risks:
- Unauthorized Access: If information is classified at a lower level than necessary, it may be accessed by individuals who are not authorized to view it, leading to security breaches.
- Exposure of Critical Data: Mistakes in classification can result in the accidental release of data that could be vital to national defense or intelligence operations.
- Increased Vulnerability: Errors can open the door for external threats, as improperly secured materials may be intercepted or stolen by malicious actors.
Long-term Security Risks
Beyond immediate consequences, errors in handling sensitive materials can have lasting effects on the integrity of national security systems:
- Damage to Diplomatic Relations: Exposure of classified information can strain international relations and damage trust between nations.
- Compromise of Strategic Operations: Sensitive information that is leaked can interfere with military or intelligence strategies, undermining years of preparation and resources.
- Legal and Ethical Repercussions: Those responsible for mishandling data may face legal actions, reputational damage, and loss of career opportunities.
Understanding the consequences of errors in managing sensitive information is critical to protecting national interests and maintaining security. Strict adherence to guidelines and careful attention to detail is essential to safeguarding data from misuse or exposure.
Tools and Resources for Exam Preparation
To effectively prepare for assessments related to the handling and protection of sensitive information, it is essential to utilize a variety of study tools and resources. These materials not only provide important information but also help reinforce understanding and application of key concepts. Using the right resources can make a significant difference in your readiness for the evaluation.
Essential Study Materials
The following resources are useful for building a strong foundation of knowledge:
- Official Guidelines: Review the official manuals and guidelines related to information protection. These documents outline the standards and protocols you must follow.
- Sample Questions: Practicing with sample questions allows you to familiarize yourself with the format and types of scenarios you may encounter.
- Training Courses: Online or in-person training programs provide structured lessons and detailed explanations of key concepts.
Additional Support Tools
In addition to study materials, the following tools can enhance your preparation:
- Flashcards: These are great for memorizing important terms, definitions, and concepts quickly.
- Study Groups: Collaborative study sessions with peers help clarify doubts and reinforce concepts through discussion and mutual support.
- Practice Exams: Full-length practice exams simulate the actual testing environment and allow you to evaluate your preparedness.
By combining various study resources and using them strategically, you can significantly improve your chances of success in the assessment process.
Security Clearance and Derivative Classification
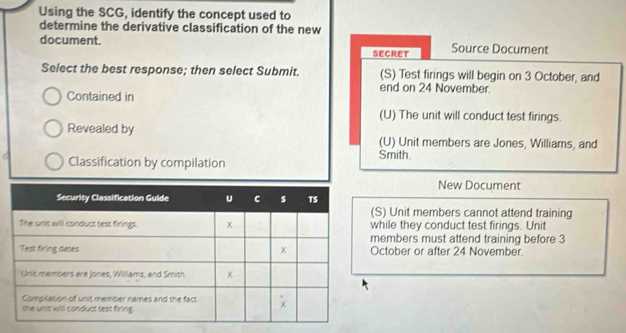
When dealing with sensitive information, individuals are required to obtain appropriate levels of access before handling materials that are considered confidential. Security clearance plays a crucial role in ensuring that only authorized personnel can access such information. Understanding the relationship between clearance levels and the handling of sensitive data is essential to maintaining national security and protecting critical assets.
Security clearance serves as a foundational element in the process of handling classified materials. It is granted based on an individual’s trustworthiness, reliability, and ability to maintain confidentiality. Those who hold security clearance are authorized to access, manage, and, in some cases, make decisions about the classification of sensitive materials.
Types of Security Clearance
The level of clearance granted determines the extent of access an individual has to confidential information. Below is an overview of the main types of security clearance:
| Clearance Level | Description |
|---|---|
| Confidential | Individuals with this level can access materials that, if disclosed, could harm national security. |
| Secret | This clearance level grants access to information that could cause significant damage to national security if revealed. |
| Top Secret | Holders of this clearance can access the most sensitive information, which could cause exceptional harm if exposed. |
Properly understanding security clearance and its role in safeguarding information ensures that sensitive data is handled by the right people, in the right way. Individuals working with classified materials must adhere to strict protocols and procedures to maintain the integrity and confidentiality of national security information.
Real-Life Scenarios in Derivative Classification
Understanding how to apply the principles of information handling in real-world situations is essential for those who manage sensitive materials. Various scenarios illustrate the challenges and complexities that arise when determining how certain data should be categorized or protected. These practical examples provide valuable insight into the decision-making processes involved in safeguarding national security.
In day-to-day operations, individuals with the proper clearance often face situations where they must make judgments about whether specific pieces of information should be kept confidential or shared with authorized personnel. These decisions are critical, as improper handling can result in the exposure of sensitive material and compromise national security.
Scenario 1: Analyzing Sensitive Data in Reports
Imagine a situation where an individual is reviewing a series of reports that include both classified and unclassified information. The task at hand is to determine which portions of the document need to be redacted or marked with a specific level of protection. The challenge lies in knowing how to assess the content and decide the appropriate actions based on the current classification guidelines.
| Situation | Action Taken |
|---|---|
| Sensitive technical specifications shared in a public presentation | Information needs to be reviewed to determine if it still falls under protected status or can be released with appropriate caveats. |
| Emails containing classified discussions mistakenly sent to unauthorized individuals | Immediate corrective action, including notification of the breach and an investigation to assess the potential impact on security. |
Scenario 2: Updating and Revising Classification Status
In another example, imagine a situation where the status of previously classified information is being revisited due to a change in its sensitivity or relevance. The decision-maker must weigh various factors to ensure that only the necessary individuals retain access to this material. Re-evaluating information and determining whether it can be downgraded or declassified is an important step in keeping the protection process up to date.
| Situation | Action Taken |
|---|---|
| Review of outdated intelligence reports | Reclassification of certain details that are no longer considered sensitive based on new intelligence findings. |
| Internal audit of classified documents | Thorough examination and potential updating of status or reassignment of access rights according to the latest policies. |
Real-life scenarios like these illustrate the complexities of handling sensitive information. By studying these situations, professionals in the field can better understand the nuances of classification decisions, ensuring that security measures are both effective and compliant with established guidelines.
Review of Key Exam Topics
When preparing for a test that assesses knowledge related to handling sensitive information, it’s essential to focus on the core concepts that govern the protection and management of classified materials. The key topics covered typically revolve around understanding the principles of safeguarding information, applying security protocols, and ensuring compliance with established policies. These areas are fundamental for anyone responsible for making decisions about what information should be protected and how it should be handled within the appropriate legal framework.
A comprehensive review of the critical topics helps ensure that individuals are well-prepared for any assessment related to these responsibilities. By focusing on the core principles and gaining a deeper understanding of how to implement them, individuals can enhance their ability to correctly interpret and apply security measures in real-world situations.
Understanding Information Sensitivity Levels

One of the most important topics covered in assessments is understanding the different levels of information sensitivity. This includes knowing how to assess and categorize data according to its potential impact on national security if disclosed. Information can range from unclassified to top secret, and it is crucial to know what qualifies each level and how to handle it accordingly.
Guidelines for Marking and Handling Data
Another vital topic is the correct way to mark and handle sensitive documents. This includes understanding the labeling requirements for various types of information, ensuring that access restrictions are properly applied, and knowing when and how information can be shared with authorized individuals. Proper handling ensures that sensitive materials are protected from unauthorized access while still being available to those who need it for legitimate purposes.
Familiarizing yourself with these core concepts is key to performing effectively in roles that involve handling classified information. Mastery of these topics ensures compliance with security protocols and minimizes the risk of breaches or unauthorized disclosures.
Maintaining Compliance with Regulations
Ensuring adherence to established security protocols is essential for protecting sensitive information and safeguarding national security. Individuals tasked with handling classified materials must be aware of and comply with the regulations that dictate how information is to be managed, stored, and shared. Compliance involves a combination of knowledge, vigilance, and consistent application of the rules to prevent accidental disclosure or unauthorized access to protected data.
To maintain compliance, it is necessary to stay updated on the latest guidelines and security measures. This includes understanding legal frameworks, following organizational policies, and being aware of any changes to classification and handling procedures. A proactive approach to compliance helps mitigate the risk of security breaches and ensures that all relevant standards are met.
Key Responsibilities in Compliance
Individuals responsible for handling sensitive data must be well-versed in the legal and ethical obligations that come with managing such information. This involves following proper procedures when accessing, marking, and disseminating data, ensuring that only authorized personnel have access to classified materials. Additionally, staff must undergo regular training to keep their knowledge current and remain vigilant in recognizing potential compliance violations.
Common Compliance Challenges
Even with the best intentions, maintaining compliance can be challenging. Common issues include inconsistent application of security measures, failure to properly update classification markings, or lapses in information handling protocols. Addressing these challenges requires continuous monitoring, regular audits, and a culture of accountability within the organization. By fostering an environment where compliance is prioritized, organizations can reduce the risk of errors and maintain the highest standards of information protection.
Post-Exam Steps and Certification
After completing the assessment process, it is important to understand the subsequent steps that ensure continued proficiency and compliance with security protocols. Successfully passing the test is just the beginning of an ongoing commitment to understanding and applying classification guidelines correctly. Following the evaluation, candidates must complete necessary administrative steps to receive their certification and fully integrate into the process of handling sensitive information.
Once the test is complete, individuals can expect to go through a verification process that includes reviewing their performance, receiving feedback, and finalizing any required documentation. After meeting all necessary criteria, candidates will be granted official certification that acknowledges their competence in managing classified materials.
Steps to Complete After the Test
- Review Feedback: After taking the assessment, candidates should carefully review any feedback provided to identify areas for improvement.
- Submit Final Documentation: Ensure all necessary forms and certifications are completed and submitted to the relevant authority for processing.
- Receive Certification: Once the requirements are met, individuals will receive official recognition of their qualifications to handle sensitive information.
- Participate in Ongoing Training: Certification is an ongoing process. To remain compliant, individuals should engage in regular training to stay updated on changes to protocols and regulations.
Maintaining Certification and Continuing Education
Obtaining certification is not the final step. To maintain certification, individuals must adhere to continuous learning and periodic recertification requirements. This ensures they remain informed about evolving security standards, updated protocols, and emerging risks. Regular training helps to reinforce knowledge and best practices, keeping all personnel in alignment with the latest classification procedures.