Understanding how to configure and troubleshoot virtual networks is an essential skill for anyone learning about digital communication systems. Simulations provide an interactive way to practice and master these skills, offering real-world scenarios that enhance technical knowledge.
This guide focuses on practical steps to streamline your problem-solving process. By breaking down complex tasks into manageable actions, you can develop a clear understanding of core concepts and improve your proficiency in managing network configurations.
Whether you’re optimizing device settings, diagnosing connectivity issues, or learning how protocols interact, mastering these techniques will give you the confidence to tackle a variety of networking tasks. Explore this resource to gain valuable insights and tips for effective implementation.
Understanding Networking Concepts with Packet Tracer
Learning how communication occurs between different devices in a network is a fundamental aspect of mastering digital systems. By using virtual environments, you can explore how data travels, devices interact, and settings influence performance without needing physical hardware.
Here are key concepts to focus on when studying network structures and operations:
- Device Configuration: Understanding how to set up routers, switches, and other components is critical for ensuring smooth communication.
- Protocol Behavior: Observing how routing and switching protocols function helps in identifying their roles and importance.
- IP Addressing: Assigning and managing IPs ensures proper routing and connectivity within a network.
- Security Measures: Implementing firewalls, access control lists, and other methods protects data flow from unauthorized access.
By dissecting these elements in an interactive setting, you can enhance your understanding of both foundational and advanced principles, laying a solid groundwork for more complex configurations and designs.
Key Steps for Configuring Network Devices
Setting up equipment for digital communication requires a structured approach to ensure all components function seamlessly. Proper configuration not only enhances performance but also minimizes potential issues that could disrupt connectivity.
Preparing Devices for Setup
Before configuring, ensure all hardware is connected correctly and powered on. Check for any default settings that may need to be adjusted to fit the network’s requirements. Familiarize yourself with the interface of each device, whether it is accessed through a command-line tool or a graphical environment.
Executing the Configuration Process
The process often begins with assigning unique identifiers, such as IP addresses, to each component. Next, establish communication protocols, ensuring they align with the overall network design. Finally, activate security measures, such as enabling encryption or setting up access restrictions, to safeguard data.
By following these steps methodically, you can build a reliable network setup that supports efficient and secure operations.
Common Errors and Their Solutions
While configuring and managing virtual networks, users may encounter various mistakes that hinder performance or disrupt connections. Identifying these issues and resolving them effectively is key to maintaining a functional system.
Connectivity Issues
A frequent problem is the failure of devices to communicate. This is often caused by incorrect IP addressing or subnetting errors. Solution: Verify that all devices are on the same network or configured with proper routing protocols to enable communication between different segments.
Misconfigured Protocols
Another common challenge involves incorrect settings for routing or switching protocols. This can lead to inefficient data transfer or even complete communication breakdowns. Solution: Review the protocol configurations, ensuring that they match the requirements of your network’s design and enable smooth operation.
Addressing these common errors promptly will not only restore functionality but also enhance your understanding of network troubleshooting and optimization techniques.
How to Analyze Packet Flow Effectively
Understanding how data travels through a network is essential for optimizing performance and diagnosing issues. By examining the flow of information, you can identify bottlenecks, detect misconfigurations, and ensure seamless communication between devices.
Steps for Comprehensive Flow Analysis
- Observe the Path: Monitor the journey of data between source and destination devices. Ensure routing tables and pathways are correctly configured.
- Identify Delays: Check for latency in transmission and analyze potential causes, such as overloaded devices or inefficient routing.
- Inspect Protocols: Verify that communication protocols are functioning as intended and adhering to the established network design.
Tools for Detailed Inspection
- Simulation Logs: Use logs to review each step of the data transfer process and locate disruptions or errors.
- Traffic Filters: Apply filters to focus on specific types of data or devices, allowing a more targeted analysis.
By applying these techniques, you can gain deeper insights into your network’s operation and maintain a reliable and efficient communication system.
Using Simulation Tools for Learning
Virtual environments offer a hands-on approach to mastering networking concepts. They allow users to experiment with configurations, analyze behaviors, and build practical skills without requiring physical hardware.
Benefits of Interactive Simulations
By engaging with simulated scenarios, learners can explore a wide range of tasks, from basic device setup to complex protocol troubleshooting. This interactive experience helps bridge the gap between theoretical knowledge and real-world application.
Enhancing Skills Through Practice
Simulations provide a risk-free platform to test new ideas and refine troubleshooting techniques. They encourage users to repeat processes, improving accuracy and confidence in handling challenges.
Incorporating these tools into your studies not only accelerates learning but also ensures a deeper understanding of how network systems operate.
Best Practices for Troubleshooting Connections
Diagnosing connectivity problems requires a structured and methodical approach to identify and resolve issues effectively. By following proven techniques, you can ensure a stable and efficient network environment.
Verify Physical Connections: Begin by checking all cables, ports, and hardware for proper setup. Loose or faulty connections are a common source of communication failures.
Check Configuration Settings: Ensure that all devices have the correct parameters, such as IP addresses, subnet masks, and gateway settings, to align with the network’s design.
Use Diagnostic Tools: Employ tools like ping and traceroute to test pathways and pinpoint where disruptions occur. These utilities help determine whether the issue lies in the local network or beyond.
Monitor Logs: Review device logs for error messages or alerts that provide insights into misconfigurations or hardware issues. Logs often contain valuable clues for resolving problems.
By implementing these best practices, you can streamline the troubleshooting process and maintain a reliable network infrastructure.
Importance of VLANs in Network Design

Virtual Local Area Networks (VLANs) play a crucial role in modern network architecture by enhancing security, performance, and manageability. They allow network administrators to segment large networks into smaller, more efficient units without requiring additional physical hardware.
By grouping devices logically, VLANs help minimize broadcast traffic, improving the overall performance and efficiency of the network. This segmentation also helps isolate sensitive data, providing enhanced security by limiting access to certain users or devices.
Additionally, VLANs make network management easier. Administrators can quickly adjust configurations and isolate problems by targeting specific segments of the network. This flexibility is essential for adapting to changing organizational needs and optimizing network resources.
Incorporating VLANs into your network design ensures a more organized, scalable, and secure infrastructure that can handle growth and evolving requirements effectively.
Optimizing Routing Protocol Configuration
Effective routing protocol configuration is essential for ensuring fast, reliable, and efficient data transfer across networks. Optimizing these protocols helps reduce latency, prevent network congestion, and improve overall performance by making intelligent routing decisions based on network conditions.
Choose the Right Routing Protocol: Selecting the appropriate protocol for your network is critical. For larger networks, dynamic routing protocols like OSPF or EIGRP can offer scalability, while smaller networks may benefit from simpler static routing.
Adjust Metric Values: Fine-tuning metric values such as bandwidth, delay, or hop count helps optimize routing decisions. Properly configured metrics ensure that data packets take the most efficient path without unnecessary delays.
Implement Route Summarization: Reducing the number of routes advertised by summarizing multiple network addresses into a single route helps decrease the size of routing tables and improves the efficiency of route updates.
Enable Route Filtering: Filtering routes allows you to control the flow of routing information, blocking unwanted paths and ensuring that only the most relevant routes are used. This reduces unnecessary traffic and improves network stability.
By optimizing routing protocol configurations, you can ensure your network performs at its best, adapting to changing conditions and maintaining high levels of reliability and efficiency.
Exploring Switch Settings in Detail
Switch configuration plays a vital role in optimizing network performance and ensuring efficient data transfer between devices. By adjusting various settings, network administrators can enhance security, reduce network congestion, and ensure smooth communication across the network.
One key aspect of switch settings is the VLAN configuration, which allows administrators to segment the network into smaller, isolated groups. This improves network performance by limiting unnecessary traffic and improving security by controlling access between devices.
Another important feature is Port Security, which helps protect the network from unauthorized access by restricting which devices can connect to specific ports. This feature can prevent security breaches caused by malicious users or devices attempting to gain unauthorized access to the network.
Additionally, administrators can configure Spanning Tree Protocol (STP) settings to prevent network loops and ensure redundancy. Proper STP configuration helps maintain network stability by dynamically blocking or unblocking ports based on network topology changes.
By carefully managing these switch settings, administrators can optimize network performance, enhance security, and ensure the overall health of the network infrastructure.
Benefits of Using Packet Tracer Exercises
Utilizing network simulation exercises offers significant advantages for both beginners and experienced professionals. These exercises provide hands-on learning opportunities without the need for expensive hardware, allowing users to practice and refine their skills in a virtual environment.
One major benefit is the ability to simulate complex network configurations and scenarios. This enables users to explore a wide range of network setups, troubleshoot problems, and experiment with different protocols and settings without the risk of disrupting a live network.
Key Advantages
- Cost-effective learning: No need for physical devices, reducing the cost of training and experimentation.
- Safe experimentation: Users can safely test configurations and troubleshoot without the fear of causing real-world issues.
- Skill improvement: By practicing different scenarios, users gain deeper understanding and confidence in network management.
- Immediate feedback: Users can instantly see the effects of their actions, helping to quickly identify and correct mistakes.
Incorporating these exercises into learning pathways enhances the overall understanding of networking concepts and prepares individuals for real-world challenges.
Configuring IP Addresses for Stability
Setting up IP addresses correctly is crucial for maintaining a reliable and stable network. A well-planned IP addressing scheme ensures smooth communication between devices and prevents potential conflicts that can disrupt network operations. Proper configuration not only optimizes performance but also simplifies troubleshooting and network management.
When configuring IP addresses, it’s essential to account for factors such as subnetting, address allocation, and network size. A structured approach to assigning IP addresses helps in scaling the network and improves its efficiency.
Best Practices for IP Configuration
| Practice | Explanation |
|---|---|
| Static IP Assignment | Assigning fixed IP addresses to critical devices like servers or printers ensures they are always reachable at the same address. |
| Dynamic IP Assignment | Using DHCP (Dynamic Host Configuration Protocol) to assign IP addresses automatically is suitable for large networks where devices join and leave frequently. |
| Subnetting | Dividing a large network into smaller subnets can improve network performance and security by isolating traffic and limiting broadcast domains. |
| IP Address Planning | Planning the IP address range and structure in advance helps avoid conflicts and ensures efficient use of address space. |
Tips for Managing Bandwidth Efficiently
Effective bandwidth management is crucial to maintaining optimal network performance, especially as data demands increase. By prioritizing traffic and ensuring resources are allocated appropriately, network administrators can prevent bottlenecks and ensure seamless communication across devices. Proper bandwidth management helps avoid congestion, improves response times, and enhances overall user experience.
Strategies such as traffic shaping, bandwidth monitoring, and applying Quality of Service (QoS) policies can help in optimizing the usage of available bandwidth. These methods ensure critical applications receive the necessary resources while limiting non-essential traffic.
Best Practices for Efficient Bandwidth Management
- Traffic Prioritization: Prioritize essential services such as voice or video conferencing to ensure minimal disruption during peak usage times.
- Monitor Bandwidth Usage: Regularly monitor network traffic to identify which applications are consuming the most bandwidth and adjust accordingly.
- Implement QoS Policies: Quality of Service (QoS) allows you to define rules that allocate bandwidth to specific types of traffic, ensuring high-priority tasks are not affected by less important traffic.
- Limit Non-Essential Traffic: Restrict bandwidth usage for non-essential activities, such as large downloads or streaming, to prevent unnecessary congestion.
Tools for Bandwidth Management
- Network Monitoring Software: Use tools to keep track of bandwidth usage and identify any performance issues.
- Bandwidth Throttling: Implement throttling techniques to limit the maximum bandwidth available to less critical applications.
- Firewall Rules: Configure firewalls to block unnecessary traffic and prevent bandwidth wastage on unwanted connections.
Securing Your Network with Access Control
Network security is a critical aspect of maintaining a safe and efficient system. One of the most effective ways to safeguard your network is through access control, which ensures that only authorized individuals or devices can access sensitive resources. By defining who can access what data, and under which circumstances, you can prevent unauthorized access, reduce the risk of security breaches, and maintain the integrity of your network infrastructure.
Access control mechanisms, when properly implemented, play a vital role in protecting networked systems from potential threats. These measures can range from simple user authentication to more advanced multi-factor verification methods.
Key Components of Access Control
- Authentication: Verifying the identity of users or devices before granting access to the network.
- Authorization: Ensuring that authenticated users or devices are allowed to access specific resources based on predefined permissions.
- Auditing: Monitoring and logging access events to track who accessed the network, when, and what resources were accessed.
- Accountability: Ensuring users are held accountable for their actions within the network by implementing proper authentication and tracking systems.
Best Practices for Implementing Access Control
- Use Strong Passwords: Require users to create strong passwords to reduce the risk of unauthorized access.
- Implement Multi-Factor Authentication (MFA): Combine different methods of authentication, such as passwords and biometrics, to enhance security.
- Limit User Permissions: Grant users only the access they need to perform their tasks, applying the principle of least privilege.
- Regularly Update Access Policies: Periodically review and update access controls to adapt to new security threats and organizational changes.
- Monitor and Audit Access: Continuously monitor network access and regularly audit access logs to detect any unauthorized attempts or anomalies.
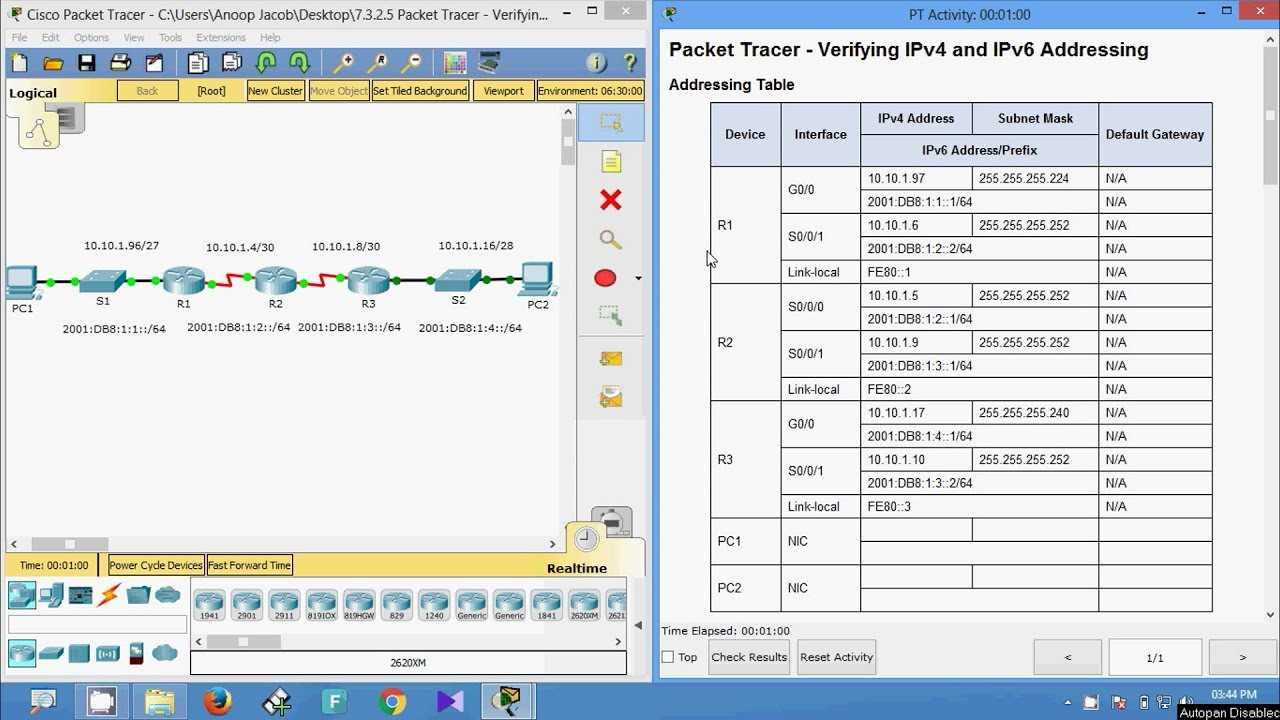
Understanding Dynamic and Static Routing
Routing is a crucial component in the management of network traffic. It determines how data packets travel between different network devices and reaches its destination. There are two main types of routing methods used in networking: static and dynamic routing. Each method has its advantages and applications, depending on the network’s complexity, size, and changing needs. Understanding the differences between these routing techniques can help in selecting the most suitable option for any given network scenario.
Static routing involves manually setting the paths for data to follow. This method provides more control over the routing process, but it requires maintenance and updates if the network topology changes. On the other hand, dynamic routing allows routers to automatically discover the best paths based on real-time information, adapting to network changes with minimal manual intervention.
Understanding Dynamic and Static Routing
Routing is a crucial component in the management of network traffic. It determines how data packets travel between different network devices and reaches its destination. There are two main types of routing methods used in networking: static and dynamic routing. Each method has its advantages and applications, depending on the network’s complexity, size, and changing needs. Understanding the differences between these routing techniques can help in selecting the most suitable option for any given network scenario.
Static routing involves manually setting the paths for data to follow. This method provides more control over the routing process, but it requires maintenance and updates if the network topology changes. On the other hand, dynamic routing allows routers to automatically discover the best paths based on real-time information, adapting to network changes with minimal manual intervention.
Understanding Dynamic and Static Routing
Routing is a crucial component in the management of network traffic. It determines how data packets travel between different network devices and reaches its destination. There are two main types of routing methods used in networking: static and dynamic routing. Each method has its advantages and applications, depending on the network’s complexity, size, and changing needs. Understanding the differences between these routing techniques can help in selecting the most suitable option for any given network scenario.
Static routing involves manually setting the paths for data to follow. This method provides more control over the routing process, but it requires maintenance and updates if the network topology changes. On the other hand, dynamic routing allows routers to automatically discover the best paths based on real-time information, adapting to network changes with minimal manual intervention.
Exploring Advanced Features of Network Simulation Tools
Network simulation tools offer a wide range of advanced features that enhance the learning and practical application of networking concepts. These features provide users with the ability to create complex network topologies, test configurations, and troubleshoot various network scenarios in a virtual environment. By utilizing these advanced capabilities, individuals can gain deeper insights into network design, configuration, and troubleshooting without the need for expensive physical equipment.
One of the most notable advanced features is the ability to simulate different types of network protocols and devices. This allows for comprehensive testing of network behaviors under different conditions. Additionally, users can explore features like network traffic analysis, real-time device configuration, and the ability to simulate faults and failures, helping them prepare for real-world network challenges.