Mastering networking concepts requires hands-on practice with simulations that allow you to test and troubleshoot various configurations. These exercises provide an excellent opportunity to enhance your understanding of network setups and problem-solving techniques.
In this guide, we will walk you through a series of networking tasks designed to test your skills. By working through these challenges, you’ll gain practical experience with device configuration, connectivity verification, and network troubleshooting.
Whether you’re a beginner or looking to improve your expertise, these exercises will help you sharpen your abilities and boost your confidence in real-world networking scenarios. With clear instructions and step-by-step guidance, you’ll be prepared to tackle any challenge and deepen your knowledge of network management.
Packet Tracer 8 4 1 2 Answers Guide
In this section, we will explore a comprehensive guide designed to help you navigate through the networking challenges and simulations. These tasks focus on real-world scenarios where network configuration, connectivity, and troubleshooting play a critical role in success. The goal is to enhance your ability to solve complex network issues while refining your skills in device setup and network management.
As you work through the challenges, you will gain valuable experience in configuring routers, switches, and other networking devices. The following guide offers detailed steps and insights to assist you in completing these tasks accurately. Each task provides a solution breakdown to ensure you fully understand the concepts and processes involved.
| Task Number | Network Configuration | Solution Overview |
|---|---|---|
| 1 | Router and Switch Configuration | Configuring basic device settings and establishing connectivity. |
| 2 | IP Address Assignment | Assigning static IP addresses and verifying communication between devices. |
| 3 | Routing Protocols | Implementing routing protocols and ensuring correct data flow across networks. |
| 4 | VLAN Configuration | Creating and managing Virtual LANs for segmented network traffic. |
| 5 | Security Configurations | Applying network security settings such as ACLs and encryption protocols. |
By the end of this guide, you will be well-equipped to manage networking tasks efficiently and troubleshoot any issues that may arise. Keep practicing to gain further proficiency in handling complex network configurations and simulations.
Understanding Packet Tracer Basics
This section introduces the essential concepts behind network simulation tools, focusing on their role in learning and practicing networking skills. These environments allow users to create and test network configurations without the need for physical equipment, making them a valuable resource for both beginners and experienced network professionals.
To begin, it is crucial to understand the basic components of the simulation environment. This includes setting up devices such as routers, switches, and computers, and configuring them to establish communication within a virtual network. These tools replicate real-world networking conditions, providing a hands-on approach to learning.
Through the use of visual interfaces, you can explore various network topologies, implement protocols, and troubleshoot connectivity issues. As you advance, you will also gain the ability to simulate different network scenarios, allowing for effective testing and evaluation of network designs before implementing them in real-world settings.
How to Navigate Packet Tracer
Mastering the navigation of network simulation tools is essential for efficiently building and testing network configurations. These tools provide an intuitive interface where you can drag and drop devices, connect them, and apply settings, making the learning process more hands-on and interactive.
To begin navigating, start by familiarizing yourself with the layout of the interface. The main workspace allows you to view and manipulate network devices, while the toolbar provides quick access to various features such as device selection, configuration options, and simulation controls. Understanding how to use the zoom function and the device toolbar will help you quickly adjust the view as needed.
Next, learn how to place and connect devices within the workspace. Each device can be configured by selecting it and applying the necessary settings, such as IP addresses or routing protocols. Familiarizing yourself with the different tabs for configuring network devices and running simulations will make the process more efficient.
Finally, take time to explore the simulation modes available in the tool. These modes allow you to test and troubleshoot network behavior in real-time, giving you the flexibility to observe how data flows through your network and identify any issues. Mastering these basic navigation techniques will set the foundation for more advanced configurations and simulations.
Steps to Solve Packet Tracer Tasks
Solving network simulation tasks requires a systematic approach to ensure that each step is completed correctly. By following a clear process, you can efficiently configure devices, test connectivity, and troubleshoot issues to meet the task requirements.
Here are the key steps to follow when working through these types of challenges:
- Read the Instructions Carefully – Before starting, thoroughly review the task details to understand the objectives and specific requirements. Make sure you know what the end goal is for the network setup.
- Set Up the Network Devices – Begin by placing the necessary devices, such as routers, switches, and computers, in the simulation environment. Ensure that each device is positioned correctly according to the instructions.
- Configure Device Settings – Assign IP addresses, routing protocols, and other settings to each device. Ensure that these configurations align with the task instructions to establish proper communication within the network.
- Connect Devices – Use appropriate cables and ports to connect the devices, ensuring all network links are correctly established. Pay attention to cable types (crossover, straight-through) based on the device connections.
- Test Connectivity – Once the devices are connected and configured, test the network to verify that data can flow properly. Use commands like “ping” or “traceroute” to check connectivity between devices.
- Troubleshoot and Fix Issues – If any devices fail to connect or data is not flowing correctly, use troubleshooting techniques to identify the problem. Check configurations, connections, and device statuses to resolve any issues.
- Verify the Solution – Once the network is functioning as expected, double-check the configurations and verify that all tasks have been completed according to the instructions.
By following these steps, you will be able to successfully complete network tasks, improve your problem-solving skills, and gain a deeper understanding of network management and troubleshooting techniques.
Common Mistakes in Packet Tracer
When working with network simulation tools, it’s easy to make mistakes that can hinder progress and lead to confusion. Understanding these common errors and how to avoid them will help improve your efficiency and accuracy when building and troubleshooting networks.
Here are some of the most frequent mistakes users encounter, along with tips to avoid them:
Incorrect Device Configuration
One of the most common issues arises from improper device configuration, such as incorrect IP addresses, subnet masks, or routing settings. These misconfigurations can prevent devices from communicating properly, leading to connectivity issues that are often difficult to identify without a detailed review.
Wrong Cable Types
Using the wrong cable type for connecting devices can result in errors. For example, using a straight-through cable instead of a crossover cable when connecting similar devices, or vice versa, can cause devices not to communicate as expected.
| Error Type | Cause | Solution |
|---|---|---|
| IP Addressing | Incorrect subnet mask or address assignment | Double-check IP configurations and ensure proper subnetting. |
| Device Connections | Incorrect cable type used | Use the correct cables for each device connection (straight-through or crossover). |
| Routing Protocols | Improper routing configurations | Ensure routing protocols match across devices and networks. |
By staying mindful of these common mistakes and taking time to review each step carefully, you can avoid frustrating errors and improve the overall quality of your network simulations.
Packet Tracer 8 4 1 2 Challenge Overview
This section provides an overview of a specific network configuration challenge, aimed at testing your ability to configure, troubleshoot, and manage network devices effectively. The task requires you to set up various network components and ensure proper communication between them, mimicking real-world networking scenarios.
The challenge focuses on configuring routers, switches, and computers to meet specified requirements. You will need to address different aspects of network management, including IP addressing, routing protocols, and security settings. The goal is to evaluate your understanding of key concepts while allowing you to develop practical problem-solving skills as you troubleshoot and adjust configurations.
Completing this challenge successfully will give you the confidence and expertise needed to handle more complex network tasks and strengthen your overall networking proficiency.
Configuring Devices in Packet Tracer
Configuring devices is a fundamental step in building and managing networks. In this section, we will explore how to set up various network components, such as routers, switches, and computers, to ensure they work together seamlessly. Proper configuration of these devices is essential for establishing connectivity, optimizing performance, and troubleshooting network issues.
To begin, you will need to access each device’s configuration mode and apply the necessary settings. For routers, this typically includes assigning IP addresses to interfaces, configuring routing protocols, and setting up security features. Switches require VLAN configurations, port assignments, and sometimes access control lists (ACLs) to manage network traffic.
After configuring the basic settings, it is important to test the devices for connectivity and ensure they communicate effectively within the network. This involves using commands such as “ping” or “show” to verify that the configuration is correct and that devices are interacting as expected.
In summary, successful device configuration requires attention to detail, a solid understanding of networking principles, and the ability to troubleshoot when issues arise. Mastering these steps will enhance your networking skills and prepare you for more complex scenarios in the future.
Testing Network Connectivity in Packet Tracer
Once the devices in your network are properly configured, it’s essential to test the connectivity to ensure that everything is functioning as expected. Testing network connectivity helps identify potential issues such as misconfigurations, connectivity failures, or device errors. In this section, we will explore various methods to test and verify network connections in a simulation environment.
To begin testing, you can use a range of commands and tools to check if devices can communicate with each other. The following methods are commonly used:
- Ping Command: This is one of the simplest and most effective ways to test connectivity between devices. By sending small data packets to a target device, the “ping” command can quickly verify whether a device is reachable over the network.
- Traceroute Command: This tool helps track the path that data takes between devices, revealing any network delays or routing issues that might be affecting performance.
- Device Status Indicators: Many network devices, such as switches and routers, provide status indicators that show the operational state of their interfaces. Ensuring these indicators are green or active confirms proper device functionality.
- Simulation Mode: This mode allows you to visually track data packets as they travel through the network. It helps to identify where packets are getting lost or delayed.
By systematically testing and troubleshooting network connections using these methods, you can quickly detect and resolve issues to maintain optimal network performance. These tools also help simulate real-world scenarios, improving your troubleshooting skills for future network setups.
Analyzing Routing and Switching Tasks
In network design and management, routing and switching play critical roles in ensuring proper communication between devices. These tasks require understanding how data is transmitted across different network segments and how devices make decisions about forwarding that data. Analyzing these tasks involves evaluating how data flows through the network and ensuring that the correct paths are chosen for efficient and secure communication.
When analyzing routing and switching tasks, it’s important to focus on the configuration of routers and switches, as well as the protocols and algorithms used for routing and forwarding data. This includes examining routing tables, VLAN configurations, and the application of security measures such as access control lists (ACLs).
For routers, the analysis will often involve reviewing the routing protocols in use, such as RIP, OSPF, or EIGRP. These protocols determine how routers share information about network topology and decide the best path for data to travel. For switches, tasks may include configuring VLANs, trunking, and spanning tree protocols (STP) to prevent loops and ensure network stability.
Effective analysis of these tasks requires careful attention to both configuration details and network behavior. By thoroughly evaluating routing and switching operations, you can identify potential issues and ensure optimal network performance.
Understanding IP Addressing in Simulations
IP addressing is a fundamental concept in network simulations, as it determines how devices communicate within a network. In this section, we will explore the importance of properly assigning and managing IP addresses in simulated environments, ensuring that devices can reach each other effectively.
Each device on a network requires a unique identifier, known as an IP address, to communicate with other devices. In simulations, configuring these addresses accurately is crucial for establishing connectivity between devices. This includes understanding the structure of an IP address, the role of subnet masks, and the purpose of network and host portions.
Subnetting is an essential aspect of IP addressing, allowing network administrators to divide a larger network into smaller, manageable segments. By understanding how to create subnets, you can efficiently allocate addresses and optimize the network’s performance.
Proper IP addressing not only ensures that devices can communicate within their own networks but also across different networks, especially when routing is involved. In simulations, it’s vital to verify that addresses are correctly configured to avoid common connectivity issues and ensure smooth operation.
How to Troubleshoot Network Issues
Network issues can arise due to a variety of reasons, ranging from hardware failures to misconfigurations. Troubleshooting network problems requires a systematic approach to identify and resolve the root cause of the issue. This section will guide you through the essential steps and tools needed to efficiently troubleshoot network connectivity problems.
The first step in troubleshooting is to gather information about the issue. This involves identifying which devices are affected and understanding the symptoms, such as slow performance, lost connections, or complete network failure. Once the issue is identified, you can begin the diagnostic process.
Steps to Troubleshoot Network Problems
- Verify Physical Connections: Ensure that all cables, switches, and routers are properly connected and powered on. Check for loose or damaged cables that may cause interruptions in service.
- Check IP Address Configurations: Incorrect IP addressing is a common cause of connectivity issues. Verify that devices have the correct IP address, subnet mask, and default gateway settings.
- Ping Test: Use the ping command to test connectivity between devices. This helps determine whether the devices can communicate with each other and identifies potential routing issues.
- Check Routing Tables: If the issue involves inter-network communication, ensure that routing protocols are properly configured and that the routing tables contain the correct paths for data transmission.
Advanced Troubleshooting Techniques
- Traceroute: Use the traceroute tool to track the path of data as it travels through the network. This can help identify where packets are being delayed or lost.
- Examine Device Logs: Network devices often log errors or unusual activities. Reviewing the logs can provide valuable insights into what is causing the problem.
- Test Different Devices: Isolate the issue by testing other devices on the network. This can help determine if the problem lies with a specific device or a broader network issue.
By following these troubleshooting steps, you can effectively identify and resolve network issues. Patience and a methodical approach are key to ensuring smooth network operations and minimizing downtime.
Using Command-Line Interface in Packet Tracer
The Command-Line Interface (CLI) is a powerful tool for configuring and managing network devices in simulated environments. It allows users to interact directly with devices, providing a more granular level of control compared to graphical user interfaces. In this section, we will explore how to effectively use the CLI to configure various network devices and troubleshoot network issues.
Understanding the basics of CLI usage is essential for anyone working with network simulations. The CLI offers a text-based interface where commands are entered to execute specific tasks such as configuring interfaces, routing protocols, or even testing connectivity. While the CLI may seem intimidating at first, it is a versatile tool that provides advanced configuration options and troubleshooting capabilities.
Getting Started with the CLI
- Accessing the CLI: To access the command-line interface, click on a network device (e.g., router or switch) in the simulation workspace, then select the CLI tab. You will be presented with a prompt where commands can be entered.
- Basic Commands: Familiarize yourself with essential commands like
enable, which grants privileged access, andshow, which displays information about the device’s configuration and status. - Configuration Mode: Enter configuration mode by typing
configure terminal. This mode allows you to modify the device’s settings, such as interface configurations and routing protocols.
Practical Examples of CLI Usage
- Setting IP Addresses: To configure an IP address on an interface, use the command
ip address [address] [subnet mask]followed byno shutdownto enable the interface. - Routing Configuration: To enable routing on a device, use commands like
router ospf [process ID]to configure OSPF routing protocol orrouter eigrp [autonomous system]for EIGRP. - Testing Connectivity: Use the
pingcommand to test connectivity between devices and diagnose potential network issues.
By mastering the CLI, users can gain full control over the configuration and troubleshooting of network devices in simulations. Whether you’re setting up a network, analyzing traffic, or diagnosing problems, the CLI is an indispensable tool in network management.
Implementing Network Security Measures

In the modern network landscape, ensuring robust security is essential to protect against unauthorized access, data breaches, and other threats. By implementing various security measures, network administrators can safeguard their infrastructure and data from malicious attacks. Effective network security not only protects sensitive information but also maintains the integrity and availability of network services.
Security measures can be applied at different layers of the network, from physical security to software-based protections. Key aspects of securing a network involve controlling access, monitoring traffic, encrypting communications, and implementing policies that mitigate risks. This section will explore several strategies for enhancing network security, focusing on both preventative and detective measures.
Key Security Measures
- Firewalls: A firewall acts as a barrier between trusted internal networks and untrusted external networks. It monitors and controls incoming and outgoing network traffic based on security rules.
- Encryption: Encrypting data ensures that even if traffic is intercepted, the information remains unreadable without the appropriate decryption key. Common encryption methods include SSL/TLS for web traffic and IPsec for secure IP communications.
- Access Control: Limiting access to network resources is critical. Using technologies such as VPNs (Virtual Private Networks) and 802.1X authentication helps control which devices and users are allowed to connect to the network.
- Intrusion Detection and Prevention Systems (IDPS): These systems monitor network traffic for signs of suspicious activity or potential breaches. They help detect and, in some cases, prevent attacks in real-time.
Implementing Secure Protocols
- SSH (Secure Shell): SSH provides a secure channel for remote management of network devices. Unlike older protocols like Telnet, SSH encrypts communication, making it resistant to eavesdropping and man-in-the-middle attacks.
- HTTPS (Hypertext Transfer Protocol Secure): HTTPS encrypts data transmitted between a web server and a browser, ensuring that sensitive information, such as login credentials and payment details, are protected during transit.
- VPN (Virtual Private Network): A VPN allows remote users to securely access the network by tunneling encrypted data through the public internet. It ensures that sensitive information remains protected, even over unsecured networks.
By implementing a multi-layered security approach, network administrators can significantly reduce the risk of cyber threats. Continuous monitoring and updates to security measures are also crucial in adapting to emerging threats and maintaining a secure network environment.
Verifying Solutions in Packet Tracer
When building and configuring network simulations, it’s essential to verify that each step has been correctly implemented. The process of verification ensures that all devices are functioning as expected, connections are properly established, and the network behaves according to the design specifications. This section will explore methods for testing, troubleshooting, and confirming that network solutions are correctly implemented.
Verification involves both automated tools and manual checks to ensure that everything from IP configurations to routing protocols is correctly set up. By systematically testing various aspects of the network, network engineers can identify any issues early and address them efficiently. This practice is essential for achieving a reliable and secure network environment.
Testing Connectivity
One of the first steps in verifying network functionality is testing the connectivity between devices. This can be done using various commands and tools available within the simulation environment. Key techniques include:
- Pinging Devices: Use the
pingcommand to test if devices can communicate with one another over the network. A successful ping indicates that the device is reachable and responding correctly. - Traceroute: The
traceroutecommand helps track the path taken by data packets as they travel through the network. It can help identify where a connection fails or experiences delays. - Checking Routing Tables: Review the routing tables of routers and other network devices to ensure that correct paths are established for data flow.
Validating Configurations
After performing basic connectivity tests, it’s important to validate the configurations of each device within the network. This involves reviewing device settings and verifying that all network parameters match the intended design. Key validation checks include:
- IP Addressing: Ensure that all devices have correct and unique IP addresses, and verify that subnet masks and gateways are properly configured to ensure communication between networks.
- VLAN Configuration: Check that VLANs are set up correctly, ensuring that devices are segmented into the appropriate groups and that inter-VLAN routing is functioning as needed.
- Routing Protocols: Confirm that routing protocols (such as OSPF, EIGRP, or static routes) are correctly configured and that devices can exchange routing information efficiently.
Verifying solutions is a crucial part of network simulation and implementation. By testing all aspects of the network thoroughly, including device configurations, connectivity, and routing paths, users can ensure the network operates smoothly and efficiently. Regular verification throughout the simulation process helps prevent issues and guarantees a successful network deployment.
Best Practices for Networking Simulations
When working with network simulations, it is essential to follow best practices to ensure accurate results, efficient performance, and a smooth learning experience. Implementing these guidelines will help you optimize your network designs, reduce errors, and enhance the reliability of your simulations. Whether you’re building a simple topology or testing complex configurations, these practices are crucial for effective and successful network simulation projects.
Planning and Design
One of the first steps in creating any simulation is planning the network design. A well-thought-out design helps ensure that all aspects of the network function correctly and allows for smoother troubleshooting later. The following tips can guide your design process:
- Define Objectives: Clearly outline what you want to achieve with the simulation. Whether it’s testing connectivity, configuring routing protocols, or analyzing security measures, knowing your goals will help shape the design.
- Use Logical Topology: Build a logical network topology that mirrors real-world scenarios. Ensure that devices are placed logically and connections reflect the network’s intended flow of data.
- Plan for Scalability: While your simulation may start small, it should be scalable. Consider potential future needs and ensure that the network can easily be expanded or modified as required.
Optimizing Performance and Accuracy
To get the most out of your network simulations, it’s important to optimize both performance and accuracy. Below are some practices that can improve the effectiveness of your simulation:
- Minimize Unnecessary Devices: Avoid adding excess devices or components that aren’t needed for your specific test. This reduces simulation complexity and enhances performance.
- Validate Configurations: Ensure that each device’s settings, such as IP addressing, routing protocols, and security policies, are correctly configured before running the simulation. Small errors can lead to inaccurate results and wasted time.
- Use Debugging Tools: Utilize built-in debugging tools to identify and resolve issues during the simulation. Tools like packet capture and trace route can help diagnose where problems occur in the network.
Following these best practices will ensure that your network simulations are efficient, accurate, and valuable learning experiences. By planning ahead, validating configurations, and optimizing performance, you can build networks that closely mirror real-world environments and effectively test network behavior in a simulated setting.
Learning from Networking Challenges
Engaging with networking challenges offers a valuable opportunity to deepen your understanding of network design, troubleshooting, and configuration. These exercises are designed to push your knowledge and skills to their limits, providing practical, hands-on experience. By solving real-world problems in a simulated environment, you not only test your knowledge but also learn to apply theoretical concepts in dynamic, real-time scenarios.
Overcoming Obstacles and Gaining Insights
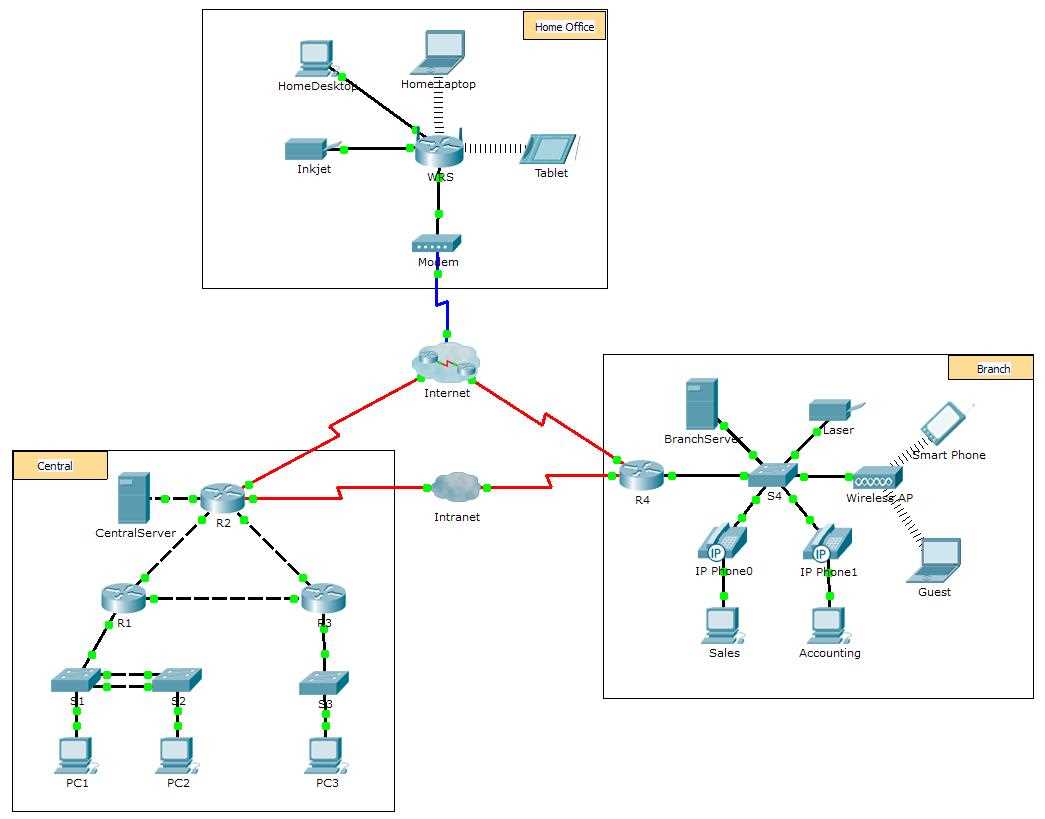
Networking challenges often involve complex scenarios that require you to think critically and systematically. These tasks typically present a series of problems that you must diagnose and resolve. As you work through the challenges, several key learning outcomes can be achieved:
- Problem-Solving Skills: Networking tasks help sharpen your ability to troubleshoot and resolve issues efficiently. Each challenge provides an opportunity to learn how to identify the root cause of a problem, test solutions, and verify results.
- Understanding Configurations: Many challenges require configuring network devices, adjusting settings, and optimizing the network for specific needs. This hands-on experience improves your understanding of configuration syntax and network protocols.
- Critical Thinking: By navigating complex networks and systems, you enhance your ability to think critically and approach problems from multiple angles, which is a crucial skill for any network professional.
Applying Lessons to Real-World Scenarios
Once you’ve successfully completed several challenges, the next step is applying your new skills to real-world situations. The experience gained from these tasks allows you to better understand how networks function under different conditions, preparing you for more advanced network management and troubleshooting tasks. The key takeaways from these exercises are:
- Real-World Applications: The problems encountered in these challenges reflect those found in actual network environments. By simulating these conditions, you prepare yourself to handle similar issues on live networks.
- Improved Efficiency: With each challenge completed, you learn techniques that allow you to work faster and more efficiently, improving your overall productivity in network management.
- Enhanced Confidence: As you solve more challenges, your confidence grows. This confidence translates into the ability to tackle more complex network issues with ease, making you a more capable network engineer.
Ultimately, learning from networking challenges is not just about solving the problems at hand; it’s about building a deeper understanding of how networks operate, which will be invaluable in your professional development and in tackling future challenges. Every task provides insights that help you grow and refine your technical abilities.