
In this section, we will explore the foundational concepts required to master key networking principles. A strong grasp of these topics will help you build the knowledge necessary to understand how networks communicate, how devices interact, and how data is routed through diverse systems.
Routing and addressing are among the core subjects covered here, and mastering these areas is essential for anyone pursuing a deeper understanding of network configurations and connectivity. You’ll also dive into how various devices are interconnected and how protocols enable smooth data transmission across multiple network layers.
This guide provides an overview of vital skills and techniques needed to effectively work with network topologies, understand data flow, and configure devices to ensure reliable communication in complex environments. Through careful study of these concepts, you’ll enhance your technical proficiency and readiness for real-world networking scenarios.
CCNA 2 Chapter 4 Exam Overview
This section focuses on key networking concepts that are fundamental for building a strong foundation in network configurations. You will encounter essential topics that involve the basic operations of routing and addressing, network communication, and the devices that make it all possible. Understanding these principles is crucial for anyone aiming to deepen their knowledge of how data moves through various systems.
Key areas of focus include routing protocols, subnetting, and IP addressing. By mastering these concepts, you will be able to understand the role of different network layers and how they contribute to overall network functionality. Additionally, this section will help you explore how different devices interact within a network, how they are configured, and how data is efficiently transmitted across these devices.
Overall, this section serves as a stepping stone to becoming proficient in network management, troubleshooting, and configuration. The knowledge gained here will prepare you for more advanced topics and practical scenarios, equipping you with the skills to tackle real-world networking challenges.
Key Concepts to Focus On
To succeed in mastering the core networking principles, it is essential to concentrate on several fundamental concepts. These concepts form the backbone of networking knowledge and play a crucial role in ensuring smooth communication within any networked environment. Gaining proficiency in these areas will provide the necessary skills to design, configure, and troubleshoot network systems effectively.
Routing and Addressing
Understanding how routing functions within a network is a critical skill. This includes how routing tables are built, how protocols determine the best path for data, and how network addresses are assigned. Additionally, knowledge of subnetting and IP address management is necessary for segmenting networks and optimizing the use of available addresses.
Network Devices and Configuration
Another important area is learning about various network devices and their configurations. From switches and routers to firewalls and hubs, each device plays a specific role in maintaining the network’s efficiency. Configuring these devices correctly ensures proper data flow and network security. Mastery of these configurations is key to managing a stable and secure network environment.
Understanding Network Protocols and Models
In networking, protocols and models are essential for ensuring that data is transmitted, received, and processed efficiently between devices. These protocols define the rules and conventions for communication, while models serve as structured frameworks that guide the design and functionality of networks. Understanding how these two components work together is fundamental for anyone looking to gain a deeper knowledge of network systems.
At the core of networking are the two most commonly used models: the OSI (Open Systems Interconnection) model and the TCP/IP model. Both provide a structured approach to understanding how different network layers interact to enable communication, with each layer focusing on a specific aspect of data transmission.
| OSI Model | TCP/IP Model |
|---|---|
| Layer 7 – Application | Application Layer |
| Layer 6 – Presentation | — |
| Layer 5 – Session | — |
| Layer 4 – Transport | Transport Layer |
| Layer 3 – Network | Internet Layer |
| Layer 2 – Data Link | Network Access Layer |
| Layer 1 – Physical | — |
Both models help to break down the complexities of networking by dividing it into manageable sections. The OSI model, for example, contains seven layers, each of which handles a different aspect of communication, from physical transmission to data encryption. The TCP/IP model, which is simpler, condenses some of the OSI layers into a smaller set that focuses on essential tasks like packet delivery and error handling.
Important IP Addressing Topics

IP addressing is a critical concept in networking, as it enables devices to identify and communicate with each other over a network. Understanding how to properly assign and manage IP addresses is essential for ensuring that a network operates efficiently and securely. This section highlights the key elements of IP addressing that every network professional should be familiar with.
Types of IP Addresses
There are several types of IP addresses that are used in different scenarios. Below are the most common types:
- Public IP Address: Assigned to devices that are directly accessible from the internet.
- Private IP Address: Used within a local network and not routed on the internet.
- Loopback Address: Used by a device to communicate with itself for testing purposes (e.g., 127.0.0.1).
- Multicast Address: Used to send data to a group of devices rather than just one.
Subnetting and Subnet Masks
Subnetting is the practice of dividing a larger network into smaller, more manageable segments. It is essential for optimizing network performance and security. The subnet mask defines which portion of an IP address refers to the network and which part refers to the host. Understanding how to calculate and apply subnet masks is key to efficient network management.
- Subnetting Basics: Dividing networks based on specific criteria to optimize address utilization.
- Subnet Masking: Identifying the network and host portions of an address by applying a subnet mask.
- CIDR Notation: A more flexible way to represent IP addresses and their associated routing prefixes.
By mastering these key topics, network professionals can ensure proper network addressing, reduce conflicts, and enhance performance across networked environments.
OSI Model and its Layers
The OSI model is a conceptual framework that helps understand how different layers of a network interact to enable communication between devices. It breaks down the complex process of data transmission into manageable stages, each responsible for a specific function. By learning how each layer operates, network professionals can better troubleshoot, configure, and optimize their systems.
Overview of the OSI Layers
The OSI model consists of seven layers, each performing distinct tasks. These layers work together to ensure the smooth flow of data from one device to another. The layers, from bottom to top, are as follows:
- Physical Layer: Responsible for transmitting raw bit streams over a physical medium, such as cables or wireless signals.
- Data Link Layer: Handles error detection and correction, as well as the flow of data over the physical link between devices.
- Network Layer: Manages routing and addressing, determining the best path for data to travel between devices across networks.
- Transport Layer: Ensures reliable data transfer by providing error recovery and flow control between devices.
- Session Layer: Manages sessions and controls the dialog between two devices, ensuring that data is properly synchronized.
- Presentation Layer: Responsible for data formatting, encryption, and compression to ensure that data is presented in a way that can be understood by the receiving system.
- Application Layer: The top layer where network services are directly accessed by end-users, including applications like web browsers and email clients.
Interacting Layers and Data Flow

When data is transmitted between two devices, it moves through each layer of the model in a process known as encapsulation. At each layer, specific protocols and services are applied to the data. As the data moves down the layers, it is wrapped in headers containing relevant information for that layer’s function. Upon reaching the destination, the layers reverse the process, known as de-encapsulation, to deliver the data in its original form.
TCP/IP and Routing Principles
The TCP/IP model is fundamental to modern networking, serving as the protocol suite that enables devices to communicate over the internet and local networks. It defines how data is packaged, addressed, transmitted, and routed from one device to another across diverse network environments. Routing principles build on this model, guiding how data packets are directed to their destination efficiently and reliably, depending on the network configuration and routing tables.
Key Elements of TCP/IP
The TCP/IP model consists of four layers, each handling different aspects of data transmission:
- Application Layer: Responsible for end-user applications, such as web browsers and email clients, interacting with the network.
- Transport Layer: Ensures reliable data transfer, using protocols like TCP and UDP to manage flow control and error correction.
- Internet Layer: Manages logical addressing (IP addresses) and routing, ensuring data packets are directed across networks correctly.
- Network Access Layer: Handles physical addressing (MAC addresses) and defines how data is transmitted over the physical medium.
Routing Fundamentals
Routing is the process of determining the best path for data to travel from its source to its destination. Routers play a crucial role in this process by using routing tables and protocols to analyze network traffic and direct packets accordingly. Key routing concepts include:
- Static Routing: Manually configured routes where network administrators define fixed paths for data transmission.
- Dynamic Routing: Uses routing protocols like OSPF or RIP to automatically update routing tables based on network changes, ensuring optimal path selection.
- Routing Tables: A set of rules stored in routers, used to determine the best route for forwarding packets based on destination IP addresses.
- Default Gateway: The route used when no specific match is found in the routing table for a packet’s destination address.
By understanding these principles, network professionals can configure efficient routing and ensure that data is transmitted with minimal delay and maximum reliability across networks.
Basic Networking Devices in Chapter 4
Networking devices are the building blocks of any communication network, each serving a specific role in the data transmission process. These devices ensure that data flows efficiently from one device to another, allowing networks to function properly. In this section, we will explore the basic devices commonly used in network configurations, focusing on their roles and how they interact with other components of the network.
| Device | Function | Typical Use |
|---|---|---|
| Router | Directs data packets between different networks based on IP addresses. They determine the best path for data. | Used to connect local networks to the internet or different network segments. |
| Switch | Connects devices within the same network, forwarding data based on MAC addresses. It works at the Data Link layer. | Used to connect computers, printers, and servers within a local area network (LAN). |
| Hub | Broadcasts data to all connected devices, operating at the physical layer. It does not filter or direct traffic. | Traditionally used in small networks, though it is largely replaced by switches. |
| Access Point (AP) | Provides wireless connectivity to devices, extending a wired network’s coverage area. | Used in wireless networks to allow devices to connect without physical cables. |
| Firewall | Filters traffic based on predefined security rules, preventing unauthorized access to the network. | Used to protect internal networks from external threats. |
Each of these devices plays a vital role in ensuring data flows smoothly and securely across the network. Understanding how they function individually and together is essential for building and maintaining efficient network systems.
Routing Tables and Their Functions
Routing tables are essential for directing data traffic across networks. They act as reference guides for routers, enabling them to determine the most efficient path for forwarding data packets. These tables store routing information, such as destination addresses and associated next-hop routes, which are used to ensure that data reaches its intended destination efficiently and securely. A clear understanding of how routing tables function is crucial for managing network traffic and maintaining a reliable network infrastructure.
Structure of a Routing Table
A typical routing table consists of several key components that help routers make routing decisions. These components include:
- Destination Network: The IP address of the network to which a packet is being sent.
- Next-Hop Address: The address of the next router or device that will forward the packet on its journey.
- Metric: A value that indicates the “cost” of reaching a destination, with lower values preferred for routing decisions.
- Interface: The network interface on the router that will be used to forward the packet.
- Routing Protocol: Indicates how the route was learned, such as through static configuration or dynamic protocols like RIP or OSPF.
Functions of Routing Tables

Routing tables serve several critical functions in network traffic management:
- Path Selection: Routing tables help routers determine the most efficient path for data to travel based on destination addresses and metrics.
- Traffic Optimization: By maintaining up-to-date routing information, routing tables ensure that data packets are directed along the best possible route, improving network performance.
- Load Balancing: In some cases, routing tables can be used to balance network load by distributing traffic across multiple paths.
- Redundancy and Failover: Routing tables provide backup routes in case the primary route fails, ensuring network reliability and uptime.
In summary, routing tables are essential for the proper functioning of network communication, guiding the flow of data between different segments of a network. Understanding how they work is vital for optimizing network performance and troubleshooting routing issues.
Subnets and Subnetting Explained
Subnetting is a critical concept in network design, allowing network administrators to divide large networks into smaller, more manageable segments. This process optimizes the use of IP address space and enhances network performance and security. By breaking down a network into subnets, organizations can better control traffic, reduce congestion, and efficiently allocate IP addresses to devices based on their needs.
What Are Subnets?
A subnet is essentially a smaller, more specific network within a larger network. It is created by partitioning an IP address space, using a subnet mask to identify which portion of the address refers to the network and which part refers to the host. This allows the network to support multiple devices or systems while maintaining structure and reducing wasted addresses.
- Network Portion: Identified by the subnet mask, this part of the address is used to define the network segment.
- Host Portion: This part of the address is used to identify individual devices or hosts within the subnet.
- Subnet Mask: A 32-bit number that separates the network and host portions of an IP address, guiding routing decisions within the subnet.
Subnetting Process
Subnetting involves modifying the default network mask to create additional subnets. The process includes the following key steps:
- Determine the required number of subnets: Based on the number of devices you plan to support, calculate how many subnets are necessary.
- Choose the right subnet mask: Adjust the subnet mask to create the needed subnets. This often involves borrowing bits from the host portion of the address.
- Divide the IP address space: Split the available address space into subnets, ensuring each subnet has its own range of usable addresses.
- Assign subnets to devices: Finally, allocate the appropriate subnet to each network segment, making sure that the devices within each segment can communicate effectively.
By using subnetting, network administrators can better manage IP addresses, enhance security by isolating network traffic, and ensure that each segment of the network operates efficiently.
Classless Inter-Domain Routing (CIDR)
Classless Inter-Domain Routing (CIDR) is a method used to allocate and specify IP addresses more efficiently, improving routing and address management across the internet. Unlike traditional IP addressing methods that relied on fixed class-based networks, CIDR allows for more flexible and precise distribution of address space. This flexibility helps prevent the exhaustion of IP addresses and optimizes the routing process by reducing the size of routing tables.
How CIDR Works
In CIDR, IP addresses are assigned with a prefix length that specifies how many bits in the address are allocated for the network portion. This method replaces the class-based system, where IP addresses were divided into fixed ranges (Class A, B, C, etc.). Instead, CIDR enables networks to have a variable number of host addresses, depending on the specific needs of the network.
- Network Prefix: The number of bits used to define the network portion of an address. It is written after the IP address in the format “IP address/Prefix length” (e.g., 192.168.1.0/24).
- Flexibility: CIDR allows networks to be divided into subnets of various sizes, making it easier to allocate address space efficiently without wasting addresses.
- Routing Efficiency: CIDR reduces the number of entries in the global routing table by aggregating routes, which helps speed up routing decisions and improve network performance.
Benefits of CIDR
Implementing CIDR provides several key benefits for network management and internet infrastructure:
- Better Address Utilization: CIDR allows for more precise allocation of IP addresses, which helps to avoid wasted address space that would otherwise occur in class-based allocation.
- Scalable Routing: By reducing the size of routing tables through route aggregation, CIDR helps scale the internet and makes routing more efficient across large networks.
- Reduces IP Address Shortage: The efficient use of IP address space through CIDR helps delay the exhaustion of IPv4 addresses, contributing to better address management as networks grow.
Overall, CIDR plays a vital role in optimizing the allocation and routing of IP addresses, providing network administrators with greater control over address assignments and improving the overall performance of the internet.
VLSM and Address Allocation Techniques
Variable Length Subnet Masking (VLSM) is an advanced technique that allows network administrators to allocate IP address space more efficiently by using different subnet masks for different segments of a network. This method provides greater flexibility compared to traditional subnetting, enabling a more precise distribution of addresses based on the actual needs of each network segment. By using VLSM, administrators can reduce address waste, optimize network performance, and make better use of limited IP address space.
When planning network address allocation, it is crucial to consider the varying requirements of different subnets. With VLSM, each subnet can be assigned a unique subnet mask, which ensures that address space is utilized in the most efficient manner possible. This technique not only helps conserve IP addresses but also improves the overall design and scalability of the network.
| Subnet | Subnet Mask | Number of Hosts |
|---|---|---|
| Subnet 1 | 255.255.255.192 | 62 |
| Subnet 2 | 255.255.255.224 | 30 |
| Subnet 3 | 255.255.255.248 | 6 |
The key to successful address allocation is to accurately determine the number of hosts required in each subnet. VLSM allows you to assign the smallest possible subnet mask that satisfies the host requirements for each segment, thereby maximizing the available address space. This flexibility also makes VLSM an essential tool for network expansion, ensuring that IP address allocations are adaptable to future growth.
By combining VLSM with proper network design practices, network administrators can achieve efficient, scalable, and cost-effective network architectures that support a growing number of devices and applications. Understanding and implementing VLSM is a crucial skill for managing modern IP networks and ensuring optimal address utilization.
Configuring Network Interfaces and Ports
Proper configuration of network interfaces and ports is a fundamental aspect of network management. These interfaces serve as the communication points between devices, allowing them to exchange data over a network. Configuring these interfaces correctly ensures reliable connectivity, efficient data transfer, and proper network segmentation. Understanding the settings associated with interfaces and ports, as well as how to adjust them to meet network requirements, is essential for network administrators.
Network interfaces can be either physical, such as Ethernet ports, or virtual, such as loopback interfaces. Each interface has specific settings, such as IP addresses, subnet masks, and link speeds, that must be configured correctly. Ports, on the other hand, control the flow of data between devices, and proper port configuration helps in managing access and improving network security.
Configuring Physical Network Interfaces
When configuring physical interfaces, it is important to define the parameters that allow devices to communicate effectively. Below are the key configuration steps:
- Assigning IP Addresses: Each interface must be given a unique IP address and subnet mask, allowing the device to communicate with other devices on the same network or across different networks.
- Enabling or Disabling Interfaces: Interfaces may be administratively shut down or brought up depending on network needs. This is typically done through commands such as “no shutdown” to enable and “shutdown” to disable an interface.
- Configuring Speed and Duplex: The speed (e.g., 100 Mbps or 1 Gbps) and duplex mode (half or full) should be configured to match the connected device’s capabilities to ensure optimal data transmission.
Port Configuration and Management
Port configuration focuses on managing data traffic between devices and controlling access to the network. Important tasks include:
- Assigning VLANs: Ports can be assigned to specific VLANs to segregate network traffic and ensure that devices within the same VLAN can communicate while remaining isolated from devices in other VLANs.
- Port Security: Port security settings can be applied to restrict access to network ports, preventing unauthorized devices from connecting to the network. Methods include MAC address filtering and limiting the number of devices that can connect to a single port.
- Configuring Trunk Ports: Trunk ports are used to carry traffic for multiple VLANs across switches. These ports must be configured to allow the transmission of VLAN tags, which help identify the VLAN to which the traffic belongs.
By configuring network interfaces and ports effectively, administrators can optimize network performance, enhance security, and ensure that devices communicate efficiently. Properly setting up these elements is critical for maintaining a stable and secure network infrastructure.
Analyzing Network Topologies and Design
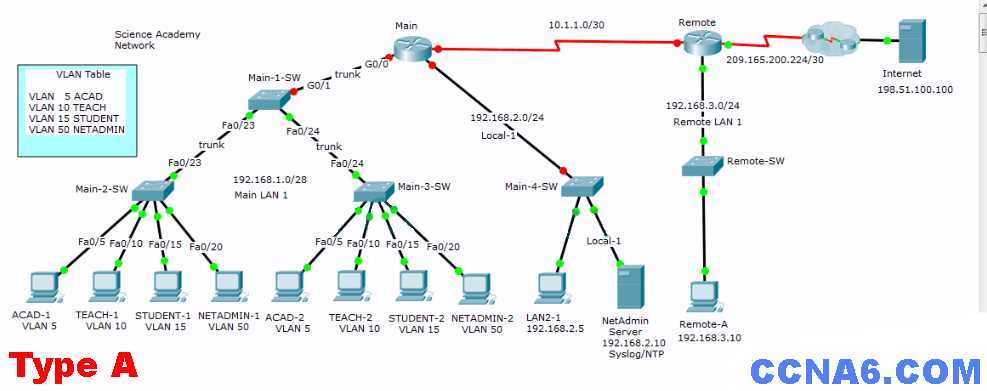
Network topology refers to the physical and logical arrangement of devices and their connections within a network. A well-designed network topology plays a crucial role in determining how data is transmitted, the efficiency of communication, and the overall scalability of the network. Analyzing different topologies and understanding their benefits and limitations is key to creating an optimized network infrastructure that meets the demands of an organization.
Effective network design requires careful consideration of factors such as performance, redundancy, cost, and security. Various network layouts can be employed, depending on the specific needs of the environment, from simple point-to-point connections to complex hierarchical structures. By evaluating and selecting the appropriate topology, administrators can ensure that their network supports future growth while maintaining high availability and reliability.
Common Network Topologies
There are several types of network topologies, each suited for different operational environments. The most commonly used are:
- Star Topology: In this setup, all devices are connected to a central hub or switch. This design is easy to manage and scalable but can suffer from a single point of failure if the central device goes down.
- Bus Topology: A single central cable connects all devices. It is cost-effective for smaller networks, but can become less efficient as more devices are added, leading to data collisions and reduced performance.
- Ring Topology: Devices are connected in a circular fashion, where each device has two neighbors. Data travels in one direction, passing through each device. While the ring is reliable, a failure in any device can disrupt the entire network.
- Mesh Topology: Every device is connected to every other device in the network. This topology provides high redundancy and fault tolerance but is complex and costly to implement.
Designing a Scalable and Resilient Network
When designing a network, it is important to focus on scalability and resilience to ensure the network can adapt to growing demands and remain operational even in the event of failures. Key aspects to consider include:
- Redundancy: Implementing redundant paths and devices can prevent network downtime. For example, using multiple routers or switches in critical areas ensures that data can be rerouted if a device fails.
- Load Balancing: Distributing traffic evenly across multiple links or devices improves network performance and helps prevent overloading any single point.
- Security: A well-designed network must also incorporate security measures, such as firewalls, access controls, and encryption, to protect sensitive data and prevent unauthorized access.
By thoroughly analyzing network topologies and applying best practices for design, network professionals can create robust, scalable, and high-performance networks that meet the needs of both current and future business operations.
Understanding Routing Protocols and Metrics
Routing protocols play a crucial role in enabling devices to communicate across networks, ensuring that data is directed along the most efficient paths. These protocols help determine the best route for data transmission, considering various factors that affect network performance. By using different types of metrics, routing protocols evaluate and choose optimal routes based on criteria like distance, bandwidth, and delay.
There are several key routing protocols that help define how networks exchange routing information, each with its own strengths and specific use cases. By understanding the workings of these protocols and the metrics they use, network administrators can better design, troubleshoot, and optimize network communications.
Types of Routing Protocols

Routing protocols are categorized into two main types: distance-vector and link-state. Each type uses different methods to determine the best path for data to travel.
- Distance-Vector Protocols: These protocols determine the best path based on distance metrics, typically the number of hops between devices. Examples include RIP (Routing Information Protocol) and IGRP (Interior Gateway Routing Protocol). While simple to implement, they can be less efficient and prone to routing loops.
- Link-State Protocols: Link-state protocols, such as OSPF (Open Shortest Path First), use a more advanced method of calculating the best path by considering the state of the network links. These protocols provide faster convergence and better scalability, but they require more resources for processing and memory.
Routing Metrics and Their Impact
Routing protocols use various metrics to evaluate the best possible path for data transmission. These metrics are essential in determining how data flows through a network and help avoid inefficiencies. Some of the most commonly used routing metrics include:
- Hop Count: The number of intermediate devices, such as routers, that a packet must pass through to reach its destination. This metric is often used in distance-vector protocols, though it is not always the most reliable indicator of the best path.
- Bandwidth: The available bandwidth of a link is a key factor in determining the most efficient path. A higher bandwidth path will generally be preferred over one with lower capacity.
- Latency: The time it takes for data to travel from the source to the destination. Lower latency is desirable, especially for real-time applications like voice and video conferencing.
- Cost: In some protocols, such as OSPF, the “cost” metric is used to represent the overhead of using a particular path, which may factor in variables like bandwidth, delay, and administrative preference.
Understanding how routing protocols use these metrics helps network engineers optimize their designs and ensure that data is transmitted efficiently across networks. By carefully considering the right routing protocols and metrics for specific scenarios, network professionals can build robust and scalable network infrastructures.
Best Practices for Preparation
Preparing for any certification or technical assessment requires a structured approach. It involves a combination of practical experience, theoretical knowledge, and strategic studying. While each learner has their own style, there are several key principles that can enhance your preparation process, making it both efficient and effective.
One of the most important practices is to focus on understanding core concepts thoroughly. Instead of memorizing facts, aim to grasp the underlying principles behind network configurations, protocols, and troubleshooting techniques. This will help you apply the knowledge in various scenarios and reinforce learning.
Another essential practice is to regularly practice hands-on exercises. Setting up and configuring network devices or creating virtual labs allows you to apply theory in real-world contexts. This practice enhances retention and boosts your problem-solving skills, especially in practical assessments.
Time management is also crucial. Allocate specific hours to study and avoid last-minute cramming. Break your study schedule into manageable chunks, tackling one topic at a time. Consistency over time often leads to better results than a single intensive study session.
Finally, practice tests and quizzes are a valuable tool to measure progress and identify areas of weakness. By simulating the test environment, you gain familiarity with the format and question types, while also reinforcing your knowledge. Don’t skip this step in your preparation journey.
Recommended Study Resources for Chapter 4
When preparing for a technical certification, using the right resources is essential for mastering the key concepts and skills required. Various materials can help reinforce your understanding and ensure you’re ready for both theoretical and practical aspects of the subject. Below are some of the most effective resources to consider as you study.
Books and Manuals
Books provide in-depth coverage of topics and are an excellent resource for foundational knowledge. Look for those that are highly regarded for their clarity and structured approach. Some recommended books include:
- Networking Basics – Covers fundamental networking concepts and configurations.
- Network Configuration and Management – A comprehensive guide with detailed configuration examples.
- Routing and Switching Explained – Focuses on routing protocols and network design principles.
Online Platforms and Courses
Interactive learning through online platforms is an efficient way to reinforce concepts and practice skills. Some top platforms include:
- Udemy – Offers video-based courses with hands-on labs and quizzes.
- LinkedIn Learning – Provides a variety of network-related courses, including practice tests and expert insights.
- Pluralsight – A great resource for in-depth technical content with practical demonstrations.
Practice Tests and Simulations
Using practice exams and simulators can give you a clear understanding of the test format and help identify areas for improvement. Some platforms to explore include:
- Boson Practice Tests – Renowned for their accuracy and detailed explanations of correct answers.
- ExamCompass – Free practice tests with a wide range of topics to help assess your knowledge.
- GNS3 – A network simulator for hands-on practice with real-world scenarios.