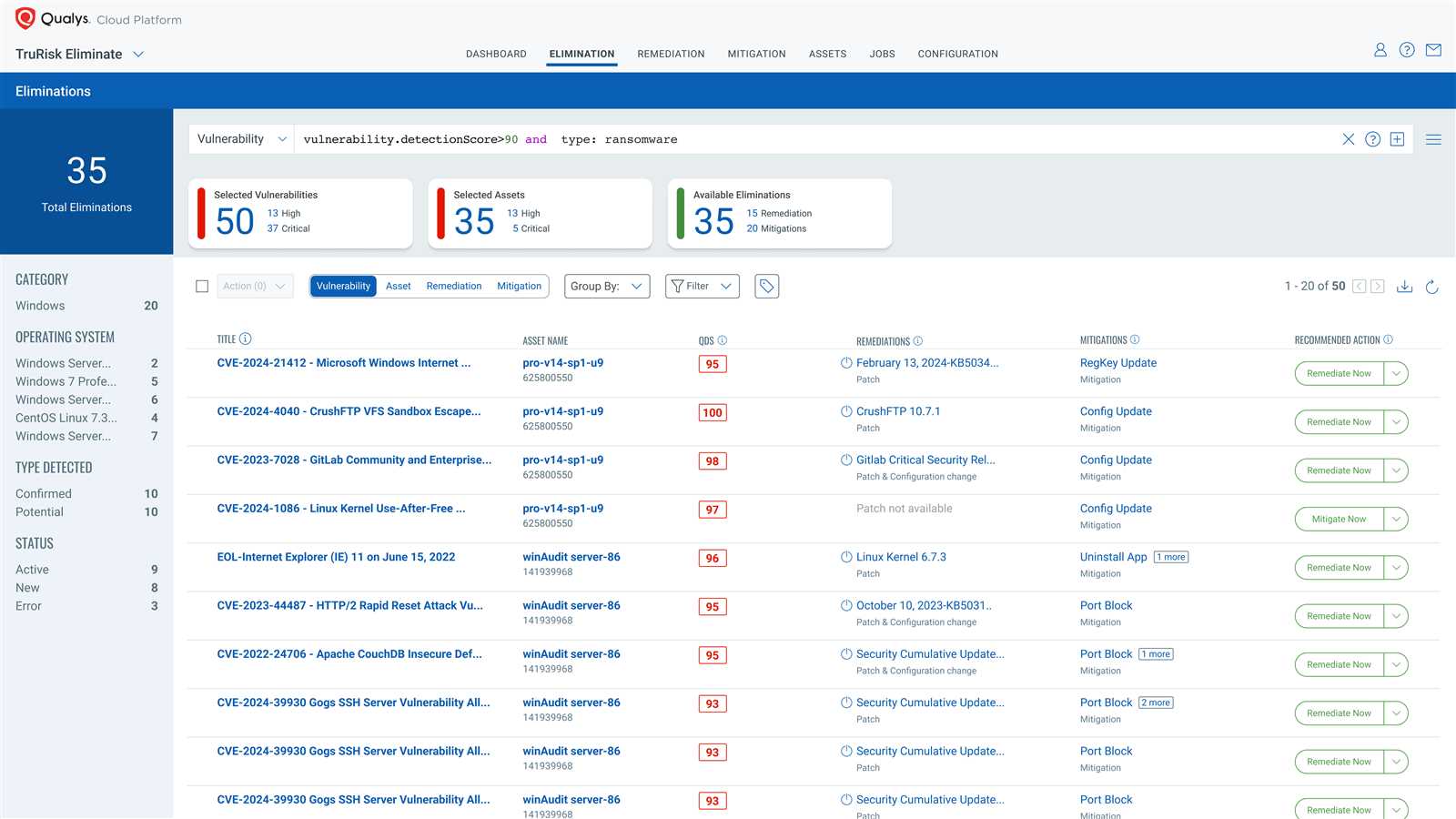
In today’s ever-evolving cybersecurity landscape, staying ahead of potential threats is critical. Understanding how to effectively identify, assess, and mitigate vulnerabilities within your network infrastructure is essential for any security professional. This knowledge can be tested through various certification assessments designed to evaluate one’s proficiency in security management systems and practices.
Preparing for such a certification requires not only mastering theoretical concepts but also gaining practical insights into how these systems work in real-world environments. With the right approach, you can navigate through the complex topics covered in the assessment, ensuring you are well-equipped to handle both the practical and theoretical challenges ahead.
Effective preparation involves understanding key concepts, tools, and strategies essential for securing a network. By focusing on the core principles and the most common scenarios, you can build a strong foundation to excel. This guide will help you understand how to approach these concepts, providing insights and resources to make your journey smoother and more effective.
Qualys VMDR 2.0 Exam Answers Overview
Preparing for certification related to security management and threat detection requires a solid understanding of key concepts, practices, and tools. This section provides an overview of what you can expect from assessments designed to test your knowledge in these areas. The focus is on recognizing the essential skills needed to successfully complete such evaluations, ensuring a clear understanding of the underlying principles.
These types of certifications assess not only your grasp of theoretical knowledge but also your ability to apply these concepts to real-world security challenges. You will encounter scenarios designed to test your proficiency in managing vulnerabilities, detecting potential risks, and responding effectively to security issues. A strong grasp of the core topics is crucial for tackling these questions with confidence.
In this overview, we will highlight key topics covered in the certification, including methods of vulnerability identification, risk assessment procedures, and the best practices for mitigating security threats. By gaining a thorough understanding of these areas, you can approach the certification process with a clear strategy and the tools necessary for success.
Understanding Qualys VMDR 2.0 Framework
The framework for vulnerability management and detection is designed to help organizations identify, assess, and respond to security risks in their networks. This approach integrates various tools and methodologies that streamline the process of safeguarding infrastructure, ensuring that any weaknesses are quickly addressed before they can be exploited. Understanding how this framework works is essential for anyone looking to effectively manage vulnerabilities in a complex security environment.
Key Components of the Framework
This framework is built around a few essential components that work together to detect, prioritize, and mitigate potential security risks. It combines automated scanning tools with a centralized management system, allowing teams to identify vulnerabilities across a range of systems. By categorizing risks based on their severity and potential impact, the framework enables security professionals to take swift, focused action to prevent breaches.
Process of Risk Detection and Mitigation
The process begins with identifying vulnerabilities through regular scans of networked systems. Once potential threats are detected, they are classified according to their risk level. Afterward, mitigation strategies are implemented based on the identified risks. The framework also incorporates continuous monitoring to ensure that any new vulnerabilities are promptly detected and addressed. This cyclical approach to risk management ensures that security remains robust and responsive to emerging threats.
Key Concepts of VMDR 2.0 Exam
In the realm of cybersecurity, it is crucial to understand the core principles that guide the identification and management of potential vulnerabilities within networked systems. Mastering these concepts ensures that security professionals can effectively assess risks, apply preventive measures, and respond to emerging threats. This section highlights the foundational elements that are essential for success in a certification focused on security risk management and threat detection.
One of the primary concepts to grasp is the process of vulnerability assessment, which involves identifying weaknesses in systems before they can be exploited. Understanding how to prioritize these vulnerabilities based on their risk level is key to effective mitigation. Another critical concept is continuous monitoring, which ensures that any new risks are quickly detected and addressed in real-time. Additionally, knowing the tools and technologies that aid in vulnerability scanning and remediation is vital for a comprehensive security strategy.
These concepts form the backbone of a structured approach to security management, empowering professionals to maintain secure systems, reduce the potential impact of security breaches, and ensure the ongoing protection of sensitive data. A deep understanding of these principles is vital for navigating complex security environments and making informed decisions when responding to vulnerabilities.
Preparation Tips for VMDR 2.0 Exam
Preparing for a certification focused on network security and vulnerability management requires a strategic approach. Effective preparation not only involves studying key concepts but also understanding the practical application of security tools and strategies. By focusing on specific areas and using the right resources, you can ensure that you are well-prepared for the challenges ahead.
- Understand the Core Concepts: Familiarize yourself with the fundamental principles of risk detection and system security. A solid grasp of how vulnerabilities are identified, assessed, and mitigated will be essential for navigating through the topics.
- Hands-On Practice: Practical experience is invaluable. Engage in real-world scenarios or virtual labs that allow you to apply the knowledge you’ve gained. This will help you understand how to use tools and systems effectively.
- Review Relevant Tools: Become proficient in the tools used for vulnerability scanning and remediation. Knowing how to configure and interpret scan results is crucial for solving security challenges.
- Focus on Risk Prioritization: Learn how to prioritize vulnerabilities based on their severity. Understanding risk levels and the appropriate response for each scenario is key for successful decision-making.
- Study Previous Case Studies: Reviewing past case studies and common vulnerability scenarios will help you anticipate the types of questions you may encounter and improve your analytical skills.
By integrating these strategies into your preparation, you can approach the certification process with confidence. With a mix of theory, practical application, and targeted practice, you will be well-equipped to tackle the key challenges in network security management.
Commonly Asked Questions in Qualys Exams
When preparing for certifications focused on vulnerability management and cybersecurity, understanding the most frequently asked questions can give you an edge. These questions are often designed to test your knowledge of core concepts and practical application. Knowing what to expect and how to approach these topics can help streamline your study efforts and improve your chances of success.
- What is the process of identifying vulnerabilities? This question typically asks you to explain the steps involved in scanning and discovering potential security risks within systems and applications.
- How do you prioritize vulnerabilities based on risk? You may be asked to demonstrate your ability to assess the severity of vulnerabilities and make decisions on how to address them based on their potential impact.
- What tools are used for vulnerability detection? Expect questions that focus on the tools and software commonly used for scanning and assessing system weaknesses. Familiarize yourself with popular tools and their capabilities.
- How do you handle newly discovered threats? Questions in this category typically test your understanding of response strategies and how to address emerging risks promptly.
- What is continuous monitoring, and why is it important? This question might assess your understanding of the importance of ongoing surveillance to detect and mitigate vulnerabilities as they arise.
- Can you explain patch management procedures? Be prepared to discuss the steps taken after vulnerabilities are identified, including how patches are applied to secure systems and prevent exploitation.
By familiarizing yourself with these key topics and questions, you can confidently approach the assessment process, knowing that you are prepared to tackle the most common challenges you will face.
How to Approach Qualys VMDR Topics
When studying for certifications in network security and risk management, it is essential to approach each topic methodically. Understanding how to break down complex subjects and focus on the most critical areas can significantly enhance your preparation. The key to success lies in recognizing the fundamental concepts, tools, and strategies, and knowing how to apply them in real-world situations.
To ensure you are well-prepared, start by organizing the topics into manageable sections. Focus on mastering the basics before diving into more advanced material. Understanding the relationships between different concepts will help you connect the dots and better retain information.
| Topic | Focus Area | Key Concepts |
|---|---|---|
| Vulnerability Identification | Scanning Systems | Tools, Detection Techniques |
| Risk Prioritization | Risk Analysis | Impact Assessment, Severity Levels |
| Mitigation Strategies | Patch Management | Fixing Vulnerabilities, Preventative Measures |
| Continuous Monitoring | Real-Time Detection | Monitoring Systems, Alerts |
| Security Best Practices | Protection Methods | Secure Configuration, Threat Response |
By focusing on these key areas, you can structure your study plan to ensure that you cover all the necessary concepts. Use practical examples and case studies to reinforce your understanding, and practice applying these principles through hands-on exercises. This approach will ensure that you are ready for the challenges ahead and can demonstrate a comprehensive understanding of the material during the assessment process.
Exploring Qualys VMDR 2.0 Features
Effective security management requires powerful tools that help detect vulnerabilities, assess risks, and mitigate threats. The features of modern security platforms are designed to integrate these functions seamlessly, providing a comprehensive solution to safeguard network infrastructures. This section explores the key features that make these tools invaluable for vulnerability management and real-time threat detection.
Comprehensive Vulnerability Scanning
One of the standout features is the ability to perform thorough vulnerability scans across multiple systems. These scans identify weaknesses in applications, networks, and devices, providing a comprehensive view of potential security risks. The tool uses automated methods to quickly detect vulnerabilities, making it easier for security professionals to focus on addressing high-priority issues.
Real-Time Risk Assessment and Prioritization

Another critical feature is the system’s ability to assess risk in real-time. Once vulnerabilities are detected, they are evaluated based on their potential impact, allowing for immediate action. This dynamic risk assessment enables teams to prioritize threats and address the most critical vulnerabilities first, reducing the likelihood of exploitation.
With these features, security teams are equipped to stay one step ahead of cyber threats, ensuring a proactive approach to network security. By providing fast, accurate insights and automating routine tasks, these tools help streamline vulnerability management processes and improve overall system protection.
Time Management Strategies for the Exam
Efficient time management is a crucial skill for success in any certification process. Properly allocating your time ensures that you can thoroughly answer each question without feeling rushed. By developing a strategic approach, you can maximize your performance and complete the assessment with confidence.
- Understand the Exam Structure: Before starting, take a few minutes to review the overall structure of the assessment. Knowing how many sections or questions there are will help you plan your time accordingly.
- Set a Time Limit for Each Section: Divide your total available time by the number of sections or questions. Allocate specific time slots for each area to avoid spending too long on any one section.
- Prioritize Easy Questions: Begin by answering questions you feel most confident about. This will build momentum and ensure that you secure easy points early on.
- Leave Difficult Questions for Later: If you encounter challenging questions, mark them and move on. Focus on answering all the easier ones first, then return to the more difficult ones with any remaining time.
- Practice Time Management: Before the actual assessment, take practice tests under timed conditions. This will help you get used to the pacing and identify areas where you might need to improve your speed.
- Stay Calm and Focused: It’s essential to stay calm during the assessment. If you feel yourself running out of time, take a deep breath and refocus. Staying composed will help you make better decisions and avoid unnecessary mistakes.
By following these strategies, you can efficiently manage your time and approach the certification process with a clear, focused mindset. Effective time management is key to ensuring that you perform your best and complete the assessment successfully.
Mastering Vulnerability Detection
Effective vulnerability detection is a cornerstone of any robust cybersecurity strategy. By mastering this process, professionals can proactively identify weaknesses in their systems before they become significant threats. The key to successful vulnerability detection lies in understanding both the tools and the methodologies that enable thorough scanning and risk assessment.
One of the fundamental aspects of vulnerability detection is the ability to scan various systems, including networks, applications, and databases, for potential security flaws. These scans typically leverage automated tools that can quickly and efficiently detect known vulnerabilities, providing a detailed list of risks that need attention. In addition to standard scans, deep dives into specific areas–such as critical infrastructure or outdated software–are essential for uncovering hidden vulnerabilities that may not be detected during routine assessments.
Mastery also involves understanding how to interpret the results of these scans. Identifying vulnerabilities is only the first step; evaluating the severity of each risk and prioritizing actions based on the potential impact is where expertise comes into play. This process allows security teams to focus their efforts on the most critical vulnerabilities, ensuring that resources are used effectively and that risks are mitigated in a timely manner.
In addition, continual learning and staying updated with the latest threats and vulnerabilities is crucial. New vulnerabilities emerge constantly, and the most effective detection systems must adapt to these changes. By incorporating these best practices into a security strategy, professionals can ensure comprehensive protection against a wide range of potential risks.
Important Security Features in VMDR
Effective security management requires a set of advanced features that ensure continuous protection, proactive risk mitigation, and rapid threat detection. These features are designed to address vulnerabilities across various systems, prioritize critical risks, and implement strategies to minimize potential damage from cyberattacks. In this section, we will explore the key security features that make modern vulnerability management platforms essential for maintaining a secure environment.
Real-Time Vulnerability Assessment
One of the most crucial features in any vulnerability management system is the ability to assess security risks in real-time. This feature allows organizations to detect vulnerabilities as soon as they appear, enabling immediate action to be taken. Real-time assessments ensure that no vulnerability goes unnoticed, allowing teams to address issues before they can be exploited by attackers.
Automated Risk Prioritization
Automating the risk prioritization process is essential for improving efficiency and ensuring that critical threats are dealt with first. By evaluating vulnerabilities based on their severity and potential impact, the system can automatically rank risks. This enables security teams to focus on the most pressing issues and allocate resources more effectively, reducing the risk of exploitation and ensuring a faster response time.
With these features, organizations can significantly enhance their security posture. By combining continuous scanning, real-time risk detection, and automated prioritization, security teams can act swiftly and strategically to protect their networks, applications, and data from evolving threats.
Essential Tools for Vulnerability Management

Effective vulnerability management relies heavily on the use of a variety of tools designed to identify, assess, and mitigate security risks. These tools play a pivotal role in helping security teams maintain a proactive stance by continuously monitoring and evaluating their network and systems for potential threats. Below, we explore the key tools that are integral to a comprehensive risk management strategy.
Automated Scanners are essential for identifying vulnerabilities across an organization’s IT infrastructure. These tools automatically scan systems, networks, and applications for known weaknesses, making it easier for security teams to detect risks early. Automation speeds up the process, ensuring that no vulnerability is overlooked, while also reducing human error.
Asset Discovery Tools help in identifying and cataloging all assets within the organization. Knowing what devices and systems are in place is crucial for understanding potential attack surfaces. These tools provide visibility into hardware, software, and services, ensuring that all assets are protected and properly managed.
Threat Intelligence Platforms offer real-time information about emerging vulnerabilities, exploit techniques, and threats. These tools integrate with vulnerability management systems to provide updated threat data, ensuring that teams can address the most recent and dangerous risks. Staying informed about evolving threats allows for quicker and more informed responses to potential attacks.
Patch Management Systems are crucial for addressing vulnerabilities identified during scans. Once a vulnerability is detected, these tools help automate the deployment of patches, ensuring that systems are updated without delay. Patch management systems help reduce the window of exposure and minimize the chances of exploitation.
Reporting and Analytics Tools provide insights into the effectiveness of vulnerability management efforts. These tools help generate detailed reports, track progress, and measure key metrics related to risk management. By analyzing trends, organizations can refine their security practices and focus on areas that require more attention.
By integrating these essential tools, organizations can create a robust vulnerability management program that not only detects and mitigates risks but also streamlines processes, ensures compliance, and enhances overall security posture.
Tips for Tackling Difficult Exam Questions
Facing challenging questions during an assessment can be overwhelming, but with the right approach, you can effectively navigate even the most complex problems. The key is to stay calm, strategically analyze each question, and apply techniques that help you identify the correct answer. This section provides useful strategies for handling difficult questions with confidence and accuracy.
Read the Question Carefully – When encountering a tough question, the first step is to carefully read and understand it. Make sure you grasp what is being asked before jumping to conclusions. Take your time to focus on key details such as keywords, phrases, and instructions that might indicate how the question should be approached.
Eliminate Clearly Wrong Answers – If the question is multiple choice, start by eliminating the most obviously incorrect answers. This can significantly increase your chances of choosing the correct option. Often, knowing what isn’t correct is just as valuable as knowing what is.
Break Down the Question – For particularly complex questions, break them down into smaller, more manageable parts. Look for clues in the question that can guide you to the correct answer. This method can help you focus on one element at a time, making the problem less intimidating.
Apply Your Knowledge – Draw from the knowledge you’ve accumulated during your preparation. Recall any relevant concepts, techniques, or methods that may apply to the question at hand. Sometimes, remembering similar examples or scenarios can help clarify the best approach to solving the problem.
Don’t Dwell Too Long on One Question – If a question proves too difficult, move on and come back to it later if time permits. Spending too much time on one question can cause unnecessary stress and eat up valuable time that could be used on easier questions.
Stay Calm and Confident – Keeping a positive mindset is essential. If you find yourself stuck, take a deep breath, refocus, and approach the question with a fresh perspective. Confidence plays a key role in overcoming difficult challenges during any assessment.
By following these strategies, you can improve your ability to tackle difficult questions, reducing stress and increasing your chances of success. The right preparation combined with effective exam techniques will empower you to handle even the most challenging scenarios with ease.
Study Resources for Qualys VMDR 2.0
To effectively prepare for an assessment on vulnerability management and detection systems, it’s crucial to access the right study materials. A combination of theoretical knowledge and practical resources will help reinforce your understanding and ensure you’re well-equipped to tackle any questions. In this section, we’ll explore some of the best resources for mastering the key topics and skills.
Official Documentation and Guides
One of the most reliable sources for studying is the official documentation provided by the platform. These guides offer detailed insights into the features, capabilities, and configuration options available in the system. Thoroughly reviewing these documents will help you understand the fundamental concepts and how they are applied in real-world scenarios.
Online Courses and Tutorials
Online courses are a great way to gain structured knowledge on various topics. Many platforms offer comprehensive courses that cover both theoretical foundations and practical applications. Look for tutorials that focus on the specific areas of vulnerability management, threat detection, and automated response strategies. These resources often include hands-on labs and practice tests to help you solidify your learning.
Books and eBooks – Books are another great study tool. Many authors have written detailed guides and textbooks on topics related to security management and vulnerability assessment. These books break down complex concepts into more digestible sections, providing a more in-depth understanding.
Practice Tests and Sample Questions – Simulating the testing environment with practice questions is essential for evaluating your readiness. Practice exams provide insight into the types of questions you may encounter and help you identify areas that need improvement. Regularly completing these tests will enhance your speed, confidence, and problem-solving skills.
Forums and Online Communities – Engaging with online communities and discussion forums can offer valuable insights from individuals who have gone through the same study process. Platforms such as Reddit, Stack Exchange, and dedicated security forums are ideal for asking questions, discussing complex topics, and sharing resources. These interactions can help you see different perspectives and learn from the experiences of others.
By using these study resources, you can develop a well-rounded understanding of vulnerability management systems. With the right mix of theoretical learning, hands-on practice, and community support, you’ll be better prepared to succeed in your assessment.
Practical Applications of VMDR Knowledge
Understanding the principles of vulnerability management and detection is not just about passing a test, but about applying that knowledge to real-world scenarios. Mastering these concepts enables professionals to identify, assess, and mitigate potential risks in dynamic environments. In this section, we will explore how this knowledge translates into practical solutions and everyday use cases for organizations.
Proactive Threat Detection
One of the most significant applications of this expertise is the ability to proactively detect threats before they become full-blown security breaches. By leveraging vulnerability scanning and risk assessment tools, professionals can identify weaknesses in their systems and prioritize them for remediation. This approach helps organizations stay ahead of potential attackers and reduce the likelihood of successful exploitation.
Incident Response and Remediation
In the event of a security incident, the ability to quickly identify the root cause and implement remediation steps is critical. Knowledge in vulnerability management allows professionals to pinpoint compromised areas, apply patches, and eliminate vulnerabilities swiftly. This quick response minimizes downtime and prevents further damage from occurring.
Security Compliance and Auditing
Many industries are governed by strict security standards and regulations that require regular vulnerability assessments. Professionals skilled in these areas are essential for ensuring that organizations stay compliant with industry regulations, such as GDPR, HIPAA, or PCI-DSS. Performing regular vulnerability audits and risk assessments is crucial for maintaining compliance and avoiding costly fines.
Optimizing IT Resources
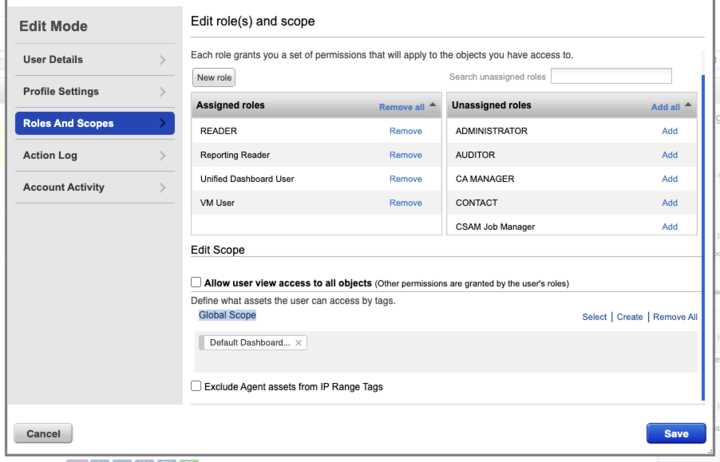
Effective vulnerability management also contributes to optimizing IT resources. By identifying and addressing security gaps, organizations can prioritize their resources more effectively. This not only strengthens security but also reduces wasted time and effort spent on addressing security issues that could have been avoided with proper planning and vulnerability detection.
Integration with Broader Security Frameworks
Another key application of this knowledge is in integrating vulnerability management processes with broader security frameworks. By aligning threat detection and response strategies with other security protocols, such as firewalls and intrusion detection systems, organizations can create a more comprehensive and robust defense against cyber threats.
Continuous Improvement and Adaptation
- Vulnerability management knowledge also contributes to the continuous improvement of an organization’s security posture.
- As new threats emerge and technology evolves, staying up to date with the latest vulnerability detection techniques allows security teams to adapt their strategies accordingly.
- This knowledge fosters a culture of continuous learning, ensuring that security measures remain effective in an ever-changing landscape.
By applying the knowledge gained in vulnerability management systems, professionals can improve not only the security of individual networks and devices but also the overall resilience of the entire organization. These practical applications are essential for safeguarding against evolving threats and ensuring long-term success in security management.
What to Expect on Exam Day
Preparing for an assessment can be a nerve-wracking experience, especially when you want to ensure you perform your best. Knowing what to expect on the day of the test can help ease anxiety and allow you to focus on showcasing your knowledge and skills. This section will guide you through what to anticipate during the process, from arriving at the testing center to completing the final step.
Before the Test
On the day of the test, make sure to arrive early to allow yourself time to settle in and familiarize yourself with the environment. If the assessment is online, ensure your computer and internet connection are functioning well before the test begins. It is advisable to double-check any required documentation or identification needed for verification purposes, as well as review any last-minute study materials to refresh your memory.
During the Test
Once the test begins, it is crucial to maintain focus and manage your time effectively. Most assessments are timed, so be mindful of the clock and pace yourself throughout the test. Questions will vary in complexity, so take your time to read each question thoroughly and ensure that you understand what is being asked. If you encounter a difficult question, don’t dwell on it for too long–move on and come back to it later if necessary. Many tests are designed to challenge your problem-solving abilities, so don’t be discouraged by tough questions.
Post-Test Process
Once you’ve completed the test, you will typically receive your results soon after submission, depending on the testing platform. If the results are not immediate, expect to receive feedback within a few hours to a few days. In some cases, there may be a review process where additional documentation or verification is needed. Remember to take time to reflect on the experience, regardless of the outcome, as each test provides valuable insights into your strengths and areas for improvement.
By understanding the process and expectations for the day, you’ll be able to approach the test with confidence and perform to the best of your ability. Preparation, practice, and a calm, focused mindset will all contribute to your success.
Key Mistakes to Avoid in the Assessment
In any testing situation, it’s important to be aware of common pitfalls that can undermine your performance. Avoiding these key mistakes can help you stay focused and maximize your chances of success. Whether you are facing a technical assessment or a more general evaluation, understanding what to steer clear of will improve your approach and boost your confidence.
One of the most frequent errors is failing to manage time effectively. Many tests are timed, and not allocating enough time to each section can result in rushed answers or incomplete responses. Another mistake is not reading the questions thoroughly before answering. Skimming over the question or rushing through can lead to misunderstandings, which may cause you to select the wrong answer. Take a moment to fully comprehend each question before making your choice.
Another critical mistake is neglecting to review your answers. If time permits, always go back and check your responses to ensure they are accurate. It’s easy to make simple mistakes under pressure, and a second look can often reveal overlooked details. Additionally, it’s important not to second-guess yourself too much. Trust the preparation and knowledge you’ve gained, and avoid overthinking when faced with tricky questions.
Finally, don’t underestimate the importance of staying calm and focused. Stress and anxiety can cloud your judgment, making it harder to recall key information or think clearly. It’s essential to maintain a positive mindset and keep your nerves in check, so you can approach each question with clarity and confidence.
By being mindful of these common mistakes, you can navigate the test more effectively and enhance your performance. Preparation, a clear strategy, and a calm demeanor are the keys to achieving your goals in any testing environment.
Post-Assessment: Next Steps in Cybersecurity
After completing a professional evaluation in the cybersecurity field, it’s important to reflect on the next logical steps to further advance your career and knowledge. Whether you achieved your desired results or are seeking areas of improvement, there are several strategies to take your skills to the next level. This is the perfect time to analyze your performance, continue your education, and explore practical applications of your knowledge.
1. Assess Your Results
Take time to carefully review your performance. Reflecting on the areas where you succeeded and where you faced challenges provides valuable insight into the strengths and weaknesses of your approach. Even if you passed the assessment, identifying areas for improvement will help you fine-tune your skills for future challenges. If you did not meet your goals, understanding why will guide your efforts in preparation for future assessments.
2. Continue Learning and Growing
Cybersecurity is a dynamic and rapidly evolving field, and continuing education is essential. With new threats emerging all the time, staying updated on the latest tools, techniques, and best practices will keep you at the forefront of the industry. Consider enrolling in advanced courses, attending webinars, or engaging in other learning opportunities to deepen your expertise. By expanding your knowledge in specialized areas, you will position yourself for more advanced roles and responsibilities.
3. Gain Practical Experience
Real-world experience is crucial for reinforcing the concepts and techniques learned during the assessment. Seek opportunities to apply your knowledge through internships, volunteer work, or hands-on projects. Practical experience allows you to tackle actual cybersecurity problems and gain valuable insight into the challenges faced by organizations. This can also improve your problem-solving abilities and enhance your resume.
4. Network with Professionals
Engaging with others in the cybersecurity community can significantly enhance your career. Networking with industry professionals, attending conferences, and joining forums will help you stay informed about the latest trends and best practices. This is also an excellent opportunity to exchange knowledge, collaborate on projects, and gain career advice from others who are more experienced in the field.
5. Explore Advanced Certifications
As your skills continue to develop, you may want to pursue additional certifications that will further enhance your qualifications. Advanced certifications demonstrate your expertise and can open doors to higher-level positions. Identify the certifications that are most relevant to your career goals and take steps to prepare for them. These certifications will help you remain competitive and show your commitment to staying ahead of industry changes.
Next Steps Summary
| Action | Details |
|---|---|
| Evaluate Your Performance | Reflect on your strengths and identify areas that need improvement. |
| Continue Education | Take advanced courses and attend learning opportunities to deepen your knowledge. |
| Get Practical Experience | Apply your skills in real-world scenarios through internships or projects. |
| Network with Others | Connect with industry professionals through conferences and forums. |
| Pursue Advanced Certifications | Look into higher-level certifications that align with your career goals. |
By following these steps, you can ensure continuous growth in the cybersecurity industry and continue building your expertise. Cybersecurity is a constantly changing landscape, and staying committed to learning and applying new concepts will help you thrive in this field.