
Preparing for an important assessment on computer fundamentals requires a deep understanding of core principles. This section covers the most critical concepts and scenarios you may encounter, focusing on real-world applications and technical nuances.
As the study progresses, it’s essential to dive into key areas such as memory management, resource allocation, and security protocols. By strengthening your grasp of these concepts, you’ll be better equipped to address complex challenges during evaluations.
Practical exercises and theoretical frameworks form the backbone of most evaluations. Understanding the inner workings of a computer’s processing, storage, and network capabilities is crucial for mastering this subject area.
Key Concepts for Assessments in OS
When preparing for a comprehensive review in computer science, focusing on fundamental ideas is essential. Understanding the core principles provides a solid foundation for solving complex scenarios and challenges that may arise during evaluations.
The following areas are crucial for mastering the subject:
- Process Management: How tasks are scheduled, executed, and terminated within a computing environment.
- Memory Allocation: Techniques for efficiently distributing memory resources among different processes.
- File Handling: Methods for storing, retrieving, and organizing data in a structured manner.
- Security Protocols: Measures to protect information and resources from unauthorized access or attacks.
- Resource Management: Techniques for optimizing the use of hardware and software resources.
To perform well in assessments, one must grasp how these concepts interconnect and how they contribute to the overall functionality of a computing environment. Mastering these areas can significantly enhance performance in practical scenarios and theoretical discussions.
Additionally, it’s important to be familiar with real-world examples and case studies that showcase these principles in action. This practical approach will help reinforce the theoretical knowledge and prepare you for various situations that may arise in testing environments.
Essential Topics in OS Theory
Mastering core theoretical concepts is key to understanding how computing environments operate at a fundamental level. These principles provide the framework for handling tasks efficiently and ensuring smooth execution across various platforms.
Resource Management and Allocation
One of the primary focuses is the efficient distribution of resources such as memory, processing power, and storage. Resource management involves making decisions about how best to allocate these finite resources to processes and applications. Effective management ensures system stability and performance.
Security and Protection Mechanisms
Securing data and preventing unauthorized access are central to any computing environment. Theoretical knowledge of security models and access control ensures the integrity of the system and its resources. Understanding the importance of encryption and authentication can greatly enhance overall system security.
In addition to these, concepts such as process synchronization, file management, and inter-process communication also play an essential role in maintaining system functionality. By understanding these principles, one can develop a deep insight into the inner workings of complex environments.
Common Questions in OS Assessments
During an evaluation of computing principles, students are often tested on a variety of concepts that assess their understanding of how resources are managed and utilized. Certain topics consistently appear due to their fundamental importance in the field. Here are some of the most common types of challenges that arise in these types of evaluations.
Topics typically include memory management techniques, where candidates are required to explain different strategies for allocating memory resources. Another frequent question area concerns process synchronization, with an emphasis on how tasks coordinate to avoid conflicts and ensure smooth operation.
Additionally, questions may explore file systems and how data is stored, retrieved, and organized within a computer. Understanding how security protocols work to protect sensitive information is also a key area that is frequently tested.
Practical Scenarios for OS Assessments
In assessments, students are often tasked with solving real-world problems that reflect common challenges faced in computer environments. These scenarios test not only theoretical knowledge but also the ability to apply concepts to practical situations.
One common scenario involves memory allocation, where students might be asked to allocate resources for multiple running processes efficiently. Such problems assess understanding of dynamic memory management and the ability to optimize performance.
Another typical scenario focuses on process management, requiring students to determine the best scheduling algorithm for a given set of tasks. Understanding the trade-offs between shortest job first or round-robin scheduling can be crucial in solving these problems.
Additionally, security-related scenarios often appear, where candidates are asked to implement access control measures or secure communications between processes. These exercises test both the theoretical knowledge and the practical skills needed to protect system integrity.
Important OS Terms and Definitions
Understanding key terminology is essential for anyone studying the internal workings of a computing environment. These terms form the foundation for discussing complex concepts and solving related problems.
- Process: A running instance of a program, including its code, data, and state.
- Thread: A lightweight process that shares resources with other threads of the same process.
- Kernel: The core component responsible for managing hardware resources and providing essential services.
- Memory Management: Techniques used to allocate and manage memory resources effectively among running processes.
- File System: A method for organizing and storing data on a storage device.
- Scheduler: The part of the environment that decides which tasks or processes get executed and when.
- Deadlock: A situation where two or more processes are unable to proceed because they are each waiting on the other to release resources.
- Semaphore: A synchronization tool used to control access to shared resources in concurrent programming.
Familiarity with these terms allows for a deeper understanding of how resources are managed and tasks are executed within a computing environment. Mastery of these concepts is vital for navigating both theoretical and practical challenges in the field.
Understanding Process Management in OS

Effective task management is essential for the smooth functioning of any computing environment. This involves scheduling, execution, and termination of various programs running simultaneously. Understanding how tasks are handled helps ensure that each operation is prioritized and executed efficiently, without conflicts.
Process Creation and Scheduling
Every time a new program is launched, it is transformed into a process, which is assigned resources such as memory and processing power. Scheduling algorithms determine the order in which these processes are executed, aiming to optimize resource usage. Common scheduling methods include round-robin, first-come, first-served, and priority-based algorithms.
Process Synchronization and Termination
Once processes are running, managing their interaction becomes critical. Synchronization ensures that processes don’t interfere with each other while accessing shared resources. When a task finishes, it must be properly terminated to release resources. Efficient process management ensures that no resources are wasted, and the system remains responsive.
Memory Management and Allocation
Efficient use of memory resources is crucial for any environment where multiple programs are running concurrently. Proper management ensures that each task receives the necessary resources without interference from others, optimizing performance and preventing system overloads.
Memory allocation involves assigning portions of memory to active processes based on their requirements. Different strategies are used to allocate space effectively, such as contiguous allocation, where memory is assigned in continuous blocks, or paging, which breaks memory into fixed-size chunks to improve flexibility and reduce fragmentation.
Moreover, managing memory involves tracking usage and ensuring that allocated memory is properly deallocated once it is no longer needed. This prevents memory leaks and ensures that resources are available for new tasks, maintaining system efficiency.
File Systems and Storage Structures
Efficient data storage and retrieval are foundational elements of any computing environment. File organization and access methods ensure that data is structured in a way that allows for fast, secure, and reliable storage. These components are critical for optimizing system performance and ensuring data integrity.
File Organization Methods
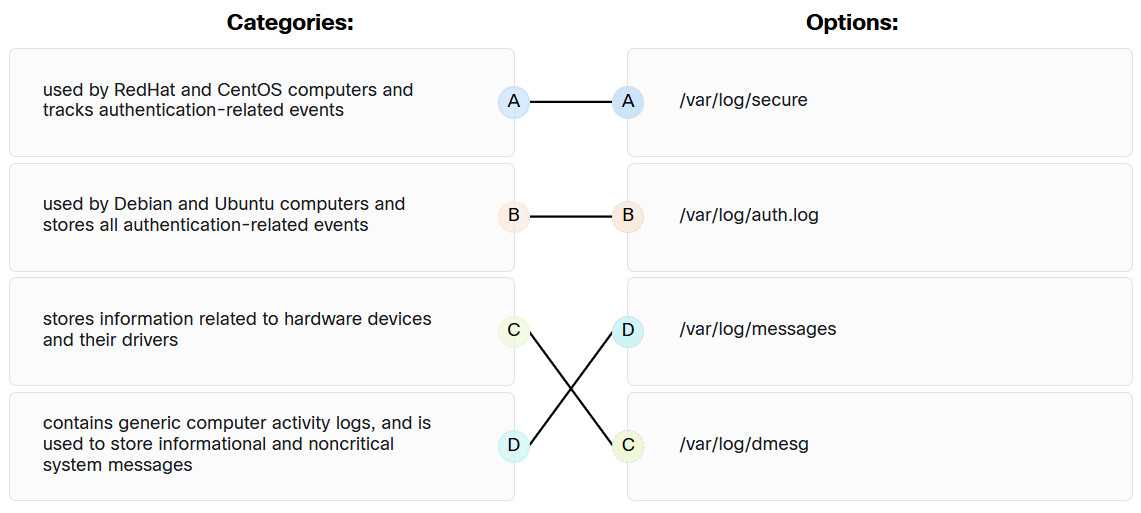
Data is typically stored in files, which are organized in a structured manner to make it easy to retrieve, update, and manage. Different file structures are used depending on the type of data and the needs of the environment. These structures include:
| File Structure | Description |
|---|---|
| Sequential | Data is stored in a linear sequence, allowing for simple but efficient reading of records one after another. |
| Indexed | Uses an index to keep track of where individual records are stored, allowing for faster access compared to sequential structures. |
| Hashed | Uses a hash function to directly access data, providing quick retrieval of information based on key values. |
Storage Allocation Methods
When it comes to storing data on physical devices, there are several ways in which memory space can be allocated to files. These methods determine how data is physically stored on the device and affect access times and efficiency:
- Contiguous Allocation: Files are stored in consecutive blocks, ensuring fast access but may lead to fragmentation.
- Linked Allocation: Data is scattered across various locations but each file segment contains a pointer to the next, reducing fragmentation.
- Indexed Allocation: Similar to linked allocation but using an index block to hold addresses for all file segments, offering better organization.
Understanding how files are structured and how data is allocated is key to optimizing storage performance and ensuring efficient management of resources.
Security Measures in Operating Systems

Ensuring the safety of data and processes is a fundamental aspect of any computing environment. Implementing strong protective mechanisms helps guard against unauthorized access, data corruption, and potential security breaches. These measures are designed to maintain the integrity and confidentiality of resources, while also ensuring availability and user privacy.
Various security techniques are employed to protect against both external and internal threats. Below are some of the most common security practices implemented in computing environments:
| Security Measure | Description |
|---|---|
| Access Control | Ensures that only authorized users can access specific resources. This is typically managed through user accounts and permissions. |
| Encryption | Transforms data into a coded format to prevent unauthorized access during storage or transmission. It’s essential for protecting sensitive information. |
| Authentication | Verifies the identity of users or processes through passwords, biometrics, or security tokens to prevent impersonation. |
| Firewalls | Monitors and controls incoming and outgoing network traffic based on predetermined security rules, protecting systems from external threats. |
These methods work together to create a layered defense that minimizes vulnerabilities and ensures the safe operation of a computing environment. Effective implementation of these measures is critical for both user safety and system stability.
Scheduling Algorithms and Techniques
Efficiently managing the execution of multiple tasks is a critical aspect of any computing environment. By organizing tasks in an optimal sequence, the system ensures that resources are utilized effectively, and processes are completed in a timely manner. Various scheduling techniques are designed to meet different operational needs, balancing factors like responsiveness, fairness, and resource usage.
Different scheduling strategies are used based on the type of workload and the goals of the system. Some focus on maximizing throughput, while others aim to minimize waiting times or ensure fairness among competing tasks.
Below are some of the most widely used techniques:
- First-Come, First-Served (FCFS): Processes are executed in the order they arrive. It’s simple but can lead to inefficiency, especially with long tasks blocking shorter ones.
- Shortest Job Next (SJN): This method prioritizes tasks with the shortest execution times. While it minimizes waiting time, it can suffer from starvation if short tasks keep arriving.
- Round Robin (RR): Each task is given an equal time slice, rotating between processes. It is fair but can lead to high turnaround times for long tasks.
- Priority Scheduling: Processes are assigned priority levels, with higher priority tasks being executed first. However, this method can also lead to starvation if low-priority tasks are continually preempted.
- Multilevel Queue Scheduling: Tasks are divided into multiple queues based on their characteristics, such as priority or CPU usage, allowing different algorithms to be applied to each queue.
By selecting an appropriate scheduling technique, systems can optimize performance, balance load, and ensure that all tasks are executed as efficiently as possible under varying conditions.
Kernel Functions in Modern OS
The core component of any computing environment manages crucial resources and facilitates communication between hardware and software. This central part is responsible for coordinating the execution of tasks, memory allocation, and ensuring smooth operation across all processes. It acts as an intermediary layer between the user applications and the physical components of the computer.
In modern environments, this central component performs a variety of essential functions to ensure efficiency, stability, and security. These functions help handle process management, system resources, and overall system performance.
Key Functions of the Kernel
The primary responsibilities of this core layer are vast and diverse, often divided into several specific roles:
- Process Management: It manages the execution of processes, including creation, scheduling, and termination. It ensures that processes run without conflict and optimally share system resources.
- Memory Management: The core is responsible for managing the system’s memory, allocating space to processes, and ensuring that memory is used efficiently while avoiding memory leaks or fragmentation.
- Device Management: It provides communication between hardware devices and software by managing drivers that control devices such as storage, network adapters, and input/output peripherals.
- Security and Protection: The core enforces security measures, such as access control and user authentication, to prevent unauthorized access and ensure the safe execution of tasks.
- File Management: It controls how data is stored, organized, and accessed on disk drives, implementing file systems and ensuring data integrity.
Interaction with User-Level Software
While users interact with applications, the core operates in the background, providing the necessary services to these applications. The system’s smooth operation relies on the efficient management of these critical tasks, ensuring that the computing environment remains stable, responsive, and secure.
By understanding the fundamental tasks handled by the core, users and developers can better appreciate how resources are allocated, tasks are scheduled, and security is maintained within a complex computing environment.
Virtualization Concepts and Practices
In today’s computing landscape, the ability to simulate hardware resources, creating multiple independent environments on a single physical machine, has become a cornerstone of efficiency and flexibility. This approach allows for better resource utilization, improved scalability, and easier management of various applications across different platforms.
Virtualization provides a layer that abstracts the underlying hardware from the software, enabling multiple virtual instances to coexist and operate independently. These virtual environments, often referred to as virtual machines, allow users to run different operating environments simultaneously on the same physical infrastructure.
The main benefits of virtualization are:
- Resource Optimization: By running multiple virtual instances on a single physical machine, hardware resources like CPU, memory, and storage are better utilized, reducing waste.
- Isolation: Virtual environments are isolated from each other, ensuring that problems in one instance do not affect others. This is particularly useful for testing and development purposes.
- Scalability: Virtualization enables easier scaling by creating additional virtual instances as needed, without requiring additional hardware resources.
- Cost Efficiency: By consolidating workloads onto fewer physical machines, organizations can save on hardware, power, and maintenance costs.
Different types of virtualization include:
- Full Virtualization: In this model, the virtual environment is entirely simulated, and the guest operating systems are unaware that they are running in a virtualized environment.
- Para-Virtualization: Here, the guest operating systems are aware of the virtualized environment and interact with the hypervisor to achieve greater efficiency.
- Hardware-Level Virtualization: This method uses specific hardware support (such as Intel VT or AMD-V) to improve the performance of virtual machines by directly managing the resources on the physical hardware.
Virtualization is not only beneficial for resource management, but it also plays a crucial role in cloud computing, disaster recovery, and high availability. As technology continues to evolve, virtualization will remain an essential practice for optimizing computing resources and supporting diverse workloads.
Interrupt Handling and Response
Interrupts are signals that inform the core component of a computing environment about events requiring immediate attention. These events can come from hardware devices, software routines, or even the system’s own internal processes. Interrupt handling is a critical mechanism, ensuring that high-priority tasks are addressed promptly while allowing other operations to continue without significant delays.
When an interrupt occurs, the system temporarily halts the execution of the current process and transfers control to a special routine, known as the interrupt service routine (ISR). This ensures that the event triggering the interrupt is dealt with in a timely manner, without interfering with the overall system operation.
The process of handling interrupts involves several key steps:
- Interrupt Detection: The system monitors the status of various devices or software to detect any events that may require attention.
- Context Saving: Before handling the interrupt, the current state of the system, including the values of registers and the program counter, is saved to ensure that the interrupted process can be resumed later.
- Interrupt Service Routine Execution: The system executes the ISR, which is designed to address the specific event that caused the interrupt, such as handling input from a keyboard or responding to a timer signal.
- Context Restoration: After the ISR has completed, the system restores the saved state, allowing the interrupted process to resume from where it was paused.
Effective interrupt handling improves the responsiveness of the environment, allowing for seamless operation even in the presence of numerous, potentially conflicting events. Different types of interrupts, such as hardware interrupts, software interrupts, and timers, are handled in specialized ways, ensuring that the system remains efficient and responsive to real-time events.
Interrupt management is particularly important in real-time environments, where the timely response to external events is critical. By managing interrupts efficiently, the system can prioritize tasks based on urgency, ensuring that time-sensitive operations are completed without delay.
Networking Features in OS
Networking capabilities are integral to modern computing environments, enabling devices to communicate over local or wide area networks. These features allow the sharing of resources, data, and services between computers, making it possible for users to access remote resources or connect to the internet. The management of network connections, protocols, and security is a core responsibility of the platform’s architecture, which must ensure seamless, secure, and efficient communication.
At the heart of network communication, various protocols and services are utilized to maintain the integrity and speed of data transmission. Network protocols such as TCP/IP, UDP, and HTTP are commonly supported, allowing devices to send and receive information in a structured manner. The system also needs to manage tasks such as addressing, routing, and ensuring reliable data transfer, which are all essential to maintaining a robust network environment.
The following features are key to networking in modern computing environments:
- IP Addressing: Each device on a network is assigned a unique address that helps route data packets to the correct destination.
- Packet Switching: Data is divided into small packets, each transmitted independently, to optimize routing and reduce congestion.
- Network Security: Features such as firewalls, encryption, and secure socket layers (SSL) are implemented to safeguard data and prevent unauthorized access.
- Connection Management: The platform manages the establishment, maintenance, and termination of network connections to ensure that data can be exchanged effectively.
Efficient networking is crucial for ensuring fast and reliable communication between devices, whether it is for local communication within an office or internet-based transactions. Additionally, the integration of networking services must be seamless to prevent data loss and minimize latency, ensuring that users experience minimal delays during communication.
As technology evolves, the platform continues to enhance its networking capabilities to support higher speeds, greater security, and new technologies like cloud computing, virtual private networks (VPNs), and IoT devices. The continuous development of networking features is critical for supporting the ever-expanding world of interconnected devices and online services.
Exam Tips for OS Students

Preparing for assessments in computing disciplines can be challenging, but with the right strategies, students can navigate through the complexity of key topics with greater ease. Success relies not only on understanding core concepts but also on effectively applying that knowledge to solve practical problems. Here are some practical tips for tackling assessments in this field.
Firstly, focusing on core concepts is essential. Understanding the fundamentals of process management, memory handling, and data storage will give you a solid foundation. These concepts often form the basis of many questions, so having a clear grasp of them will help you address various scenarios during the test.
Additionally, hands-on practice can make a significant difference. Work on practical examples and real-world applications related to the subject matter. Simulating tasks such as process scheduling, memory allocation, and file handling can provide valuable experience that will enhance your ability to tackle questions effectively.
- Review Key Terms: Make sure to memorize essential definitions and terminologies, such as “deadlock,” “paging,” and “context switching,” which are frequently referenced in assignments.
- Practice Problem-Solving: Solve as many practice problems as possible, focusing on both theoretical concepts and practical applications. This will help you become accustomed to the format and types of tasks that are commonly tested.
- Understand Theoretical Concepts: Don’t just memorize formulas or procedures–make sure you understand the theory behind them. This depth of knowledge will help you approach more complex or unexpected scenarios during the assessment.
- Manage Time Wisely: Time management is key during assessments. Read through all tasks carefully, allocate time based on difficulty, and avoid spending too much time on one question.
In addition, keep your study materials organized. Create summaries, diagrams, and flashcards for quick revision. Reviewing key concepts regularly will reinforce your understanding and help you retain information over time.
Finally, maintain a calm and focused approach during the assessment. Confidence in your preparation will allow you to approach each task methodically. Stay positive, and remember that understanding the underlying principles is more important than memorizing exact answers.
Preparing for OS Lab Practical Tests
Practical tests are a significant component of assessments in computing disciplines, where hands-on skills are just as important as theoretical knowledge. In these tests, you are often required to apply concepts learned in lectures to real-world scenarios. Proper preparation is essential to ensure that you can demonstrate your understanding effectively.
One of the first steps in preparing for practical lab assessments is familiarizing yourself with the tools and environment you’ll be working in. This includes understanding how to navigate the interface, use relevant software, and execute key commands. Mastery of the tools at your disposal will reduce the time spent figuring out technicalities during the test.
Key Areas to Focus On

When preparing for a lab practical, concentrate on areas that are frequently assessed. These typically include process management, file handling, memory allocation, and scheduling. Being comfortable with the practical application of these topics will significantly improve your performance. The following points are crucial:
- Process Management: Practice creating, managing, and terminating processes. Be familiar with process states and transitions, as well as commands to monitor and control processes.
- Memory Management: Understand how to allocate and free memory. Practice handling both contiguous and non-contiguous memory, as well as memory paging.
- File Systems: Learn how to create, read, write, and delete files. Practice working with directories and managing file permissions.
- Networking: Know how to set up network connections and configure relevant tools for communication between machines.
Effective Study Strategies
Preparation for practical tests should involve both theoretical review and hands-on practice. Some strategies to maximize your efficiency include:
- Hands-on Practice: Set aside time to work on lab exercises and past assignments. This will help you become comfortable with the tasks you might encounter during the test.
- Understand Common Commands: Ensure you know the most commonly used commands for managing processes, files, and memory. Being able to recall these quickly is essential during time-sensitive practical tests.
- Simulate Test Conditions: Recreate lab scenarios at home or in a study group to simulate real test conditions. This will help you become accustomed to performing under time constraints.
- Review Test Feedback: If previous tests or assignments have been returned, use the feedback to identify areas where you need to improve.
In addition, stay organized during the test. Plan your time carefully, allocate sufficient time to each task, and double-check your work before submission. While the tasks might be hands-on, efficiency and accuracy are critical to success.